- Cisco Community
- Technology and Support
- Security
- Physical Security
- Yup. As indicated, you can
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VSM 7.7 SSL Certificate error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2016 02:13 AM
Hi,
Any thoughts on solving this error when using the CameraControls api
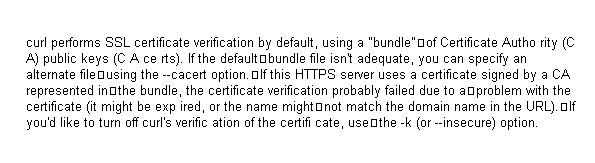
and using the -k option the server returns
Missing SessionId header or security information.
- Labels:
-
Physical Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2016 05:22 AM
Yup. As indicated, you can tell curl to disregard the certificate issues with the -k switch. This works, but as you indicated, exposes another underlying issue. The camera is still expecting the request to be from an authenticated session containing a valid *sessionID*. There are a couple ways one could try to overcome this challenge;
1) Disable SessionID in the camera firmware so that a valid session
2) Add the authentication functionality to your script and acquire a legitimate SessionID from the camera that can then be passed to the curl utility.
Hope this helps.
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2016 06:23 AM
Thanks for the pointers.
Wouldn't it be easier if the server produced a valid Certificate rather than disabling a security feature and exposing all clients to risk?
So i need to use the same session id in the html header of the request that i used to generate the required token?
This surely makes the token useless if you have to send both anyway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2016 07:22 AM
Yes. Instead of disregarding the warnings concerning the SSL certificate, you could certainly address them. There are two ways to go about that and I suppose it would depend on the scope of your project which would make the most sense;
- Add the presented certificate from the Camera (or VSOM/VSMS server instance in this case?) to the Trusted Certificate store on the machine making the curl request.
- Re-cert the Camera/VSOM/VSMS server with certificate information signed by a CA that is already trusted (public CA, or enterprise PKI potentially?).
As for the SessionID, if that is being communicated via SSL (and not subject to
The -k option isn't causing all TLS/SSL encryption to be dropped... it's just telling curl to disregard that the certificate *authenticity* might not be up to scratch (signed by a trusted CA, proper date ranges, etc. etc...), but its cryptographic material can still be used to pin up an encrypted connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2016 08:58 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide