- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Issue with Guest Access and dACL?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Issue with Guest Access and dACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2018 12:02 PM - edited 02-21-2020 10:52 AM
Hello All,
Cisco ISE v2.3
Cisco WLC-2504 v8.3
I am testing a new Guest setup on ISE and I am having some trouble with the dACL assigned in the Authorization Profile.
The guest client connects to the guest Wi-Fi and gets an IP Address. The client then receives the ISE_REDIRECT and gets redirected to the Guest Wi-Fi login page, and authenticates successfully.
After the client authenticates successfully, they receive the Wireless_Guest_Internet Authorization Profile. In that profile I specify the Guest Vlan as well as a dACL. The live log detail for the client shows:
15016 Selected Authorization Profile - Wireless_Guest_Internet
11022 Added the dACL specified in the Authorization Profile
11002 Returned RADIUS Access-Accept
It doesn't appear as though the dACL is getting applied to the Guest endpoint pc, because the client can access all internal resources even though the dACL specifically denies such access. Below is the dACL:
permit udp any eq bootpc any eq bootps
permit udp any any eq domain
permit ip any host <Primary-ISE-IP>
permit ip any host <Secondary-ISE-IP>
deny ip any 192.168.0.0 0.0.255.255
deny ip any 10.0.0.0 0.255.255.255
permit ip any any
Is there anything wrong with the dACL shown above? I'm not sure why the Guest can access everything..?
Any thoughts or suggestions would be greatly appreciated!
Thanks in Advance,
Matt
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2018 10:27 PM
Hi Matthew Martin
I think it may sound stupid for me to say this but all of us make mistakes.
Are you sure you are specifying an Airespace ACL and not just DACL under authorization results like below
the same ACL name has to be defined exactly in the WLC with the same name (case-sensitive) under Security tab and if you are using flexconnect Wireless Design you need to also Flexconnect ACL with the same name to work perfectly fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2018 10:55 AM
Hey Mohamed, thanks for the reply.
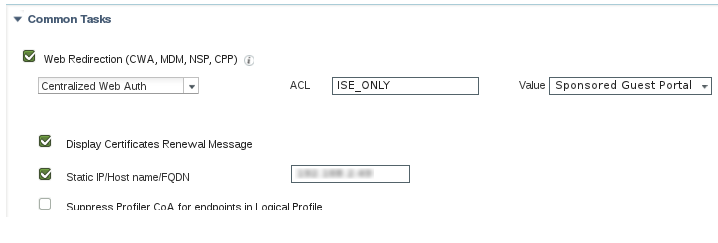
We have another Authorization Profile called "Wireless_ISE_Redirect". In that profile I've selected the following:
*I don't remember why we selected the Display Cert Renewal Message option... Is this something you think is needed??
On the Wireless Controller > Wireless > FlexConnect Groups > Group-Name > ACL Mapping > Policies: I have a FlexConnect ACL under Policy Access Control Lists called "ISE_ONLY".
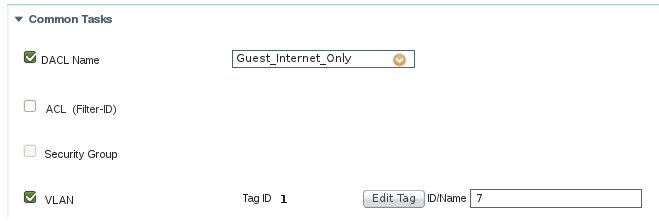
So after the client connects to Guest Wi-Fi, they get the Wireless_ISE_Redirect profile shown above. Then, after they authenticate successfully through the login page, they get the 2nd Auth Profile (*Wireless_Guest_Internet) which has the dACL checked as well as the Vlan assignment. See below:
So are you saying the dACLs are for Wired connections only, and what I would need to do is create the same ACL on the WLC and add a 2nd Policy Access Control List in the FlexConnect Group and give it whatever name I use under the Airespace ACL Name..?
*FYI, our original configuration was to just assign the Vlan for the Guest (*no dACL assignment) and then just allow the NAD (*Switches) to decide what Vlan7 can access. The NADs have a Zone-Based Firewall which sets access. I had another forum post for assistance on how to get Vlan7 the correct access. But, I never got ANY replies, so I thought to try this method above with the dACL...
Thanks Again,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 02:22 AM
Hi Matthew Martin
Sorry for late reply I had long nights at Data Centers :)
So are you saying the dACLs are for Wired connections only, and what I would need to do is create the same ACL on the WLC and add a 2nd Policy Access Control List in the FlexConnect Group and give it whatever name I use under the Airespace ACL Name..?
Yes, dACLs would be ignored by WLC and only Airespace ACL would be processed, you can configure both dACL and Airespace ACL and use the same Authorization profile for both wired and wireless and the NAD will accept the corresponding ACL and ignore the other (Switch will download dACL, WLC will process Airespace ACL (wACL)).
Difference here is that Switch download the dACL from the Authentication server (ISE) where in WLC you need to define the Airespace ACL locally inside the WLC.
Now where to configure this Airespace ACL depends on your Wireless design architecture (Local vs Flexconnect)
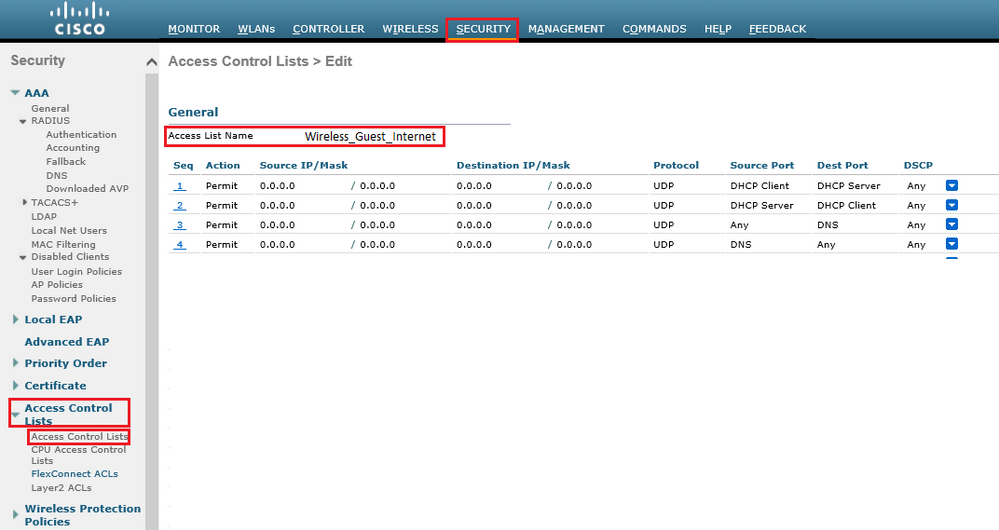
In Locally Switched WLAN, You need to define the Airespace ACL under Security --> Access Control Lists --> Access Control Lists (This is for AireOS WLCs).
There should be Two ACLs: Redirect ACL (for Redirection) and Airespace ACL (for final Access).
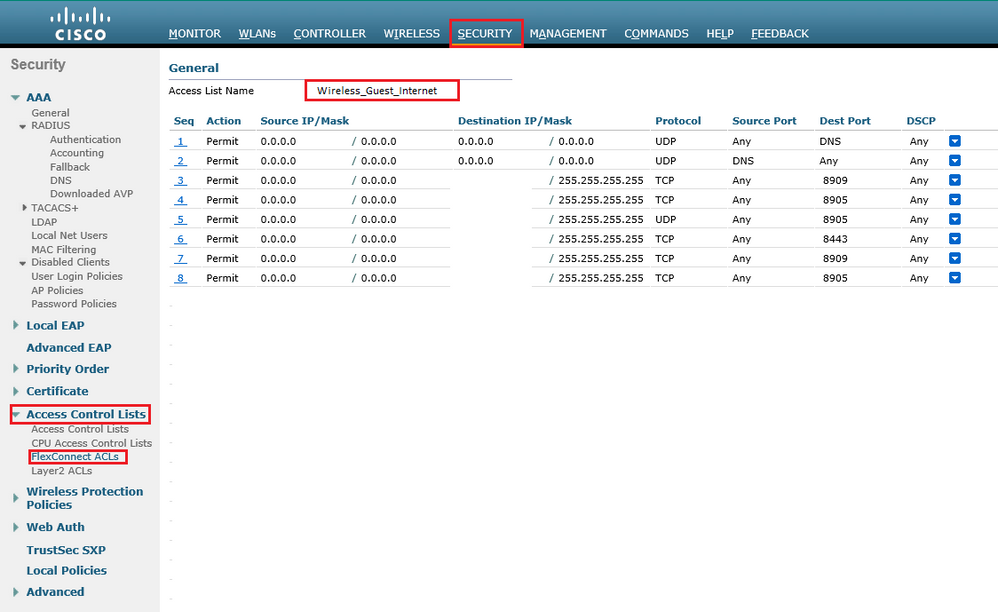
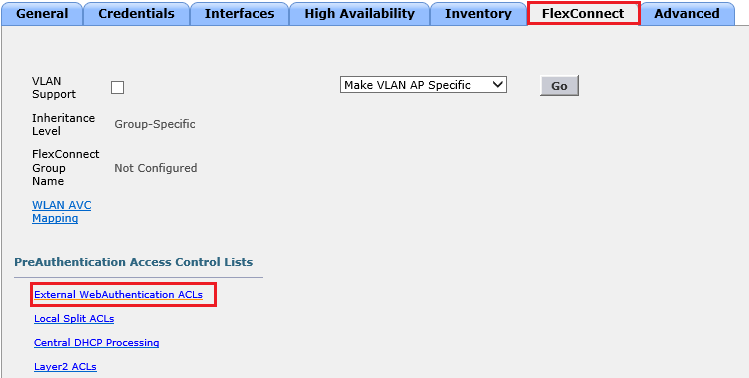
In Flexonnect WLAN, You need to define the Airespace ACL under Security --> Access Control Lists --> Flexconnect Lists (This is for AireOS WLCs)
There should be Two ACLs: Redirect ACL (for Redirection) and Airespace ACL (for final Access).
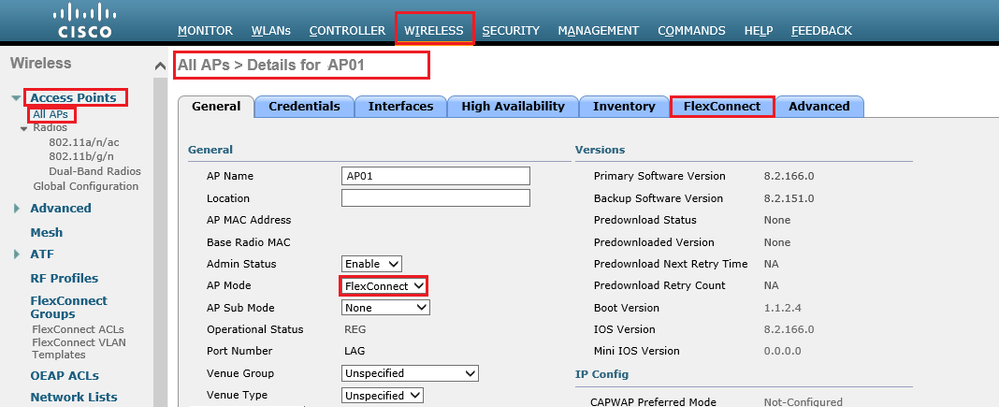
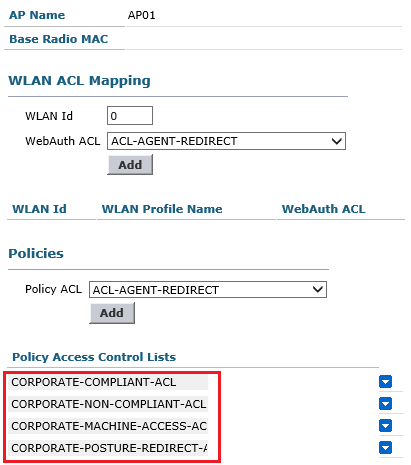
The Same ACLs in Flexconnect design should be mapped under the FlexConnect Groups or under manually under the AP itself depending on your environment. for one customer i have have to manually assign these ACL manually under each Flexconnect AP as shown below.
Now modify your ISE authorization profile to include Airespace ACL under common task and put the same name you defined in WLC. (You can keep the dACL if you are going to use this profile for wired connection also but if not you can safely remove it ).
I hope this helps
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide