- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Re: Cyberark_DUO integration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 01:12 AM
We have intergrated CyberArk with DUO. We are using ldap for first level authentication.
When we connect to ldap directly from CyberArk on 636 SSL port, it is working fine. But when we replace the hostname with DUO server name, it gives bellow error.
Failed to connect to host, Reason: Failed to connect to LDAP host “xx.xx.xx.xxx” with user “CN=xxxxxxxxx”. Code(21, 81) (21)
Summary:
LDAP verify check ended with errors (-1)
What could be the issue?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 05:58 AM
It seems like this issue is beyond what can be reasonably explored in a community forum. Please contact Duo Support to receive interactive 1:1 troubleshooting assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 06:59 AM
If CyberArk is reporting standard LDAP error codes, 21 is LDAP_INVALID_SYNTAX.
First, you should double-check that you completed all deployment steps in our documentation and verify that your authproxy.cfg contents are correct and that you supplied the necessary SSL certificate and key file for LDAPS.
Next, enable debug logging on the Duo proxy server and try again. Examine the debug output to help you find the issue.
You mention you’re using LDAP but not specifically Active Directory. If you are using OpenLDAP or another dir you may need to change the username_attribute parameter as it defaults to sAMAccountName for AD.
If you’re still having issues, contact Duo Support for assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 07:21 AM
Hi,
We have checked the documentation and created the auth[proxy.cfg and provided necessary SSL certificate and key file for ldaps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 07:24 AM
Hi Kristina,
We have checked the DUO documentation and configured the authproxy.cfg. We gave the SSL cert and key file for ldap.
Debug is enabled but we don’t see any logs for the error in duo logs. Only error we could see is in CyberArk event viewer logs as I mentioned in my previous mail.
We are using Active Directory.
Regards,
Lavanya G
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 07:44 AM
Any incoming connection and bind should get captured in the Duo log. If you don’t see any events in the Duo proxy debug output, then it sounds like your CyberArk PAS can’t contact the Duo server.
Focus on possible networking or name resolution issues. Observing packet captures from the CyberArk server may help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 08:12 AM
With 389 it is working perfectly. Only, with 636 is the problem. In Cyberark server, we see below error in windows event viewer log.
*** The certificate received from the remote server does not contain the expected name. It is therefore not possible to determine whether we are connecting to the correct server. The server name we were expecting is . The SSL connection request has failed. The attached data contains the server certificate.***
A fatal alert was generated and sent to the remote endpoint. This may result in termination of the connection. The TLS protocol defined fatal error code is 43. The Windows SChannel error state is 552.
We have updated AD certificate in pem format in Authproxy.cfg. But, the error shows it is looking for cert with DUO Proxy hostname where ideally it should take the AD certificate details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 09:33 AM
It sounds like you may have specified the wrong certificate for the incoming LDAP connection.
In this configuration it’s important to understand when the Duo Authentication proxy is acting as an LDAP server and when it is acting as an LDAP client. It’s a server to CyberArk, and a client to AD.
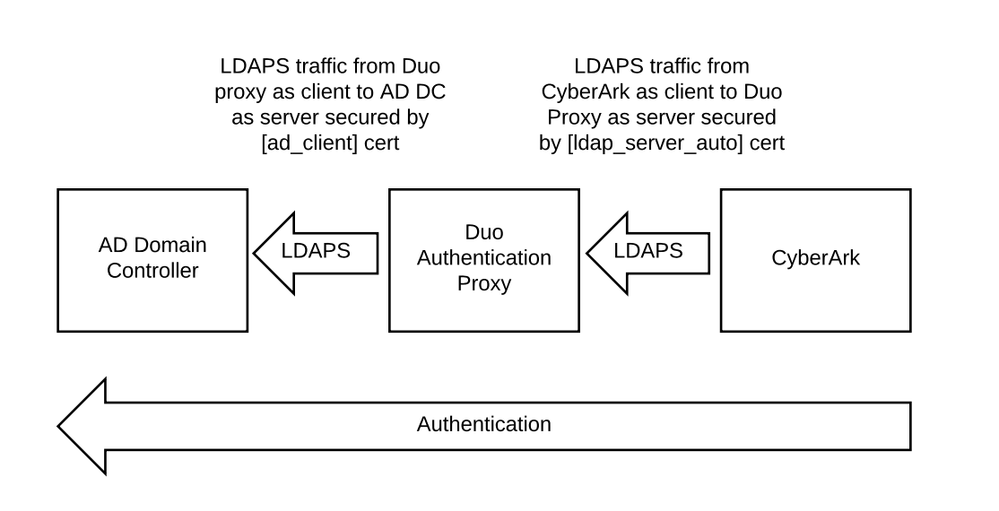
The certificate you specify in [ldap_server_auto] should be distinct from the one used by your AD server. The certificate is used only for the incoming LDAP connection from the downstream service (CyberArk, in this case). You need to use a certificate and key pair issued to your Duo Authentication Proxy, with the Duo proxy server hostname as the subject or subject alternate name. If your Duo Proxy’s hostname is duo.example.com and your DC is dc.example.com, and you are using a cert issued to dc.example.com for the Duo Proxy as LDAP server, and CyberArk is trying to match the cert’s hostname to the server’s, then the connection will fail (as you saw).
If you want the Duo Authentication Proxy server to contact your AD server using LDAPS, then you would add the DC’s certificate in the [ad_client] section.
Finally, make sure that the KEY file doesn’t require a password! If you are issuing the cert from a Windows CA you’ll need to split the PFX and also use openssl or an online tool like SSL Shopper to remove the password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 01:21 AM
Hi Kristina,
We got certificate and key issued for duo server with the Duo proxy server hostname as the subject or subject alternate name. Added the cert (ssl_cert_path ) and key(ssl_key_path) details in .pem format under [ldap_server_auto]section. Key doesn’t have password, removed using ssl
When we mention the duo server details in cyberark and mention 636 port and SSL as Yes, still facing below error.
*** Failed to connect to host, Reason: Failed to connect to LDAP host “xx.xx.xx.xxx” with user “CN=xxxxxxxxx”. Code(21, 81) (21) Summary: LDAP verify check ended with errors (-1)***
Regards,
Lavanya G
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 05:58 AM
It seems like this issue is beyond what can be reasonably explored in a community forum. Please contact Duo Support to receive interactive 1:1 troubleshooting assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2018 05:36 AM
Thanks for your response. It’s very clear and helpful. Will implement in our environment accordingly.
Thank you so much.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide