- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- i cannot establish VPN connection with rv120w to shrew soft client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2014 12:05 AM
1. I bought 2 rv120w router and install one direct to WAN and one behind router-hub.
2. one behind router is set DMZ, and each are conneted Site to Site vpn
3. I need to connect each site with my mobile devices(1 notebook, 2 Win8 tablets, 2 android devices )
4. i use wibro mobile router, win8 devices're behind router, and their fort is fowarded(DMZ)
5. I'll take care of Android devices later, here now, my trouble is Win8 devices
6. i installed cisco QuickVPN software. frankly,that software is shit. i don't know why but it even cannot reach router, no log generated on rv120w. and i dont want PPTP connection. sorry for criticism but I'm sure many of QuickVPN users(and people who fail to be a user) agree with me. it's 2014. not 1998.
Cisco should be shamed for that software. it looks like a second grade collage student's 2nd semester project(Many of them're batter nowadays.) and doesn't work.
more amazing fact is that's only software that RV series provides officialy. What the...so in conclusion, Cisco does not provide any IPSec client connection tool at all. does that makes any sense?
7. i tried 10 or more hours to make IPSec client connection with many vpn client soft ware, this is my closest shot.
RV120W log :
2014-10-02 15:03:05: [rv120w][IKE] INFO: Configuration found for 175.xxx.xxx.xxx[500].
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received request for new phase 1 negotiation: 11x.xxx.xxx.xxx[500]<=>175.xxx.xxx.xxx[500]
2014-10-02 15:03:05: [rv120w][IKE] INFO: Beginning Aggressive mode.
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: draft-ietf-ipsra-isakmp-xauth-06.txt
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: RFC 3947
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: DPD
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: DPD
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received Vendor ID: CISCO-UNITY
2014-10-02 15:03:05: [rv120w][IKE] INFO: Received unknown Vendor ID
2014-10-02 15:03:05: [rv120w][IKE] INFO: For 175.xxx.xxx.xxx[500], Selected NAT-T version: RFC 39472014-10-02 15:03:06: [rv120w][IKE] INFO: Floating ports for NAT-T with peer 175.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] INFO: NAT-D payload does not match for 11x.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] INFO: NAT-D payload does not match for 175.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] INFO: NAT detected: Local is behind a NAT device. and alsoPeer is behind a NAT device
2014-10-02 15:03:06: [rv120w][IKE] INFO: Sending Xauth request to 175.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] INFO: ISAKMP-SA established for 11x.xxx.xxx.xxx[4500]-175.xxx.xxx.xxx[4500] with spi:90dd9f6bf4d51d95:70f7c62456edef9e
2014-10-02 15:03:06: [rv120w][IKE] INFO: Received attribute type "ISAKMP_CFG_REPLY" from 175.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] INFO: Login succeeded for user "fxxxxxxxxX1"
2014-10-02 15:03:06: [rv120w][IKE] INFO: Received attribute type "ISAKMP_CFG_REQUEST" from 175.xxx.xxx.xxx[4500]
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] WARNING: Ignored attribute 5
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] WARNING: Ignored attribute 28678
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] ERROR: Local configuration for 175.xxx.xxx.xxx[4500] does not have mode config
2014-10-02 15:03:06: [rv120w][IKE] INFO: Purged ISAKMP-SA with proto_id=ISAKMP and spi=90dd9f6bf4d51d95:70f7c62456edef9e.
2014-10-02 15:03:07: [rv120w][IKE] INFO: ISAKMP-SA deleted for 11x.xxx.xxx.xxx[4500]-175.xxx.xxx.xxx[4500] with spi:90dd9f6bf4d51d95:70f7c62456edef9e
Phase 1 Setting
| Selected IKE Policy View | ||
| General | ||
| Policy Name | FDCStD | |
| Direction / Type | Responder | |
| Exchange Mode | Aggresive | |
| Enable XAUTH Client | ||
| Local Identification | ||
| Identifier Type | Local Wan IP | |
| FQDN | 112.167.xxx.xxx | |
| Peer IKE Identification | ||
| Identifier Type | Remote Wan IP | |
| FQDN | 175.xxx.xxx.xxx | |
| IKE SA Parameters | ||
| Encryption Algorithm | 3DES | |
| Authentication Algorithm | SHA-1 | |
| Authentication Method | Pre-Shared Key | |
| Pre-Shared Key | qpwoeiruty | |
| Diffie-Hellman (DH) Group | Group 2 (1024bit ) | |
| SA-Lifetime | 28800 Seconds | |
Phase2 setting
| Add / Edit VPN Policy Configuration | ||
| Policy Name | ||
| Policy Type | ||
| NETBIOS | Enable | |
| Local Traffic Selection | ||
| Local IP | ||
| Start Address | ||
| End Address | ||
| Subnet Mask | ||
| Remote Traffic Selection | ||
| Start Address | ||
| End Address | ||
| Subnet Mask | ||
| Split DNS | ||
| Split DNS | Enable | |
| Domain Name Server 1 | ||
| Domain Name Server 2 | (Optional) | |
| Domain Name 1 | ||
| Domain Name 2 | (Optional) | |
| Manual Policy Parameters | ||
| SPI-Incoming | ||
| SPI-Outgoing | ||
| Encryption Algorithm | ||
| Key-In | ||
| Key-Out | ||
| Integrity Algorithm | ||
| Key-In | ||
| Key-Out | ||
| Auto Policy Parameters | ||
| SA-Lifetime | ||
| Encryption Algorithm | ||
| Integrity Algorithm | ||
Enable | ||
| Select IKE Policy | ||
Shres client setting

Phase 1 Setting
| Selected IKE Policy View | ||
| General | ||
| Policy Name | FDCStD | |
| Direction / Type | Responder | |
| Exchange Mode | Aggresive | |
| Enable XAUTH Client | ||
| Local Identification | ||
| Identifier Type | Local Wan IP | |
| FQDN | 112.167.xxx.xxx | |
| Peer IKE Identification | ||
| Identifier Type | Remote Wan IP | |
| FQDN | 175.xxx.xxx.xxx | |
| IKE SA Parameters | ||
| Encryption Algorithm | 3DES | |
| Authentication Algorithm | SHA-1 | |
| Authentication Method | Pre-Shared Key | |
| Pre-Shared Key | qpwoeiruty | |
| Diffie-Hellman (DH) Group | Group 2 (1024bit ) | |
| SA-Lifetime | 28800 Seconds | |
Phase2 setting
| Add / Edit VPN Policy Configuration | ||
| Policy Name | ||
| Policy Type | ||
| NETBIOS | Enable | |
| Local Traffic Selection | ||
| Local IP | ||
| Start Address | ||
| End Address | ||
| Subnet Mask | ||
| Remote Traffic Selection | ||
| Start Address | ||
| End Address | ||
| Subnet Mask | ||
| Split DNS | ||
| Split DNS | Enable | |
| Domain Name Server 1 | ||
| Domain Name Server 2 | (Optional) | |
| Domain Name 1 | ||
| Domain Name 2 | (Optional) | |
| Manual Policy Parameters | ||
| SPI-Incoming | ||
| SPI-Outgoing | ||
| Encryption Algorithm | ||
| Key-In | ||
| Key-Out | ||
| Integrity Algorithm | ||
| Key-In | ||
| Key-Out | ||
| Auto Policy Parameters | ||
| SA-Lifetime | ||
| Encryption Algorithm | ||
| Integrity Algorithm | ||
Enable | ||
| Select IKE Policy | ||
Shres client setting








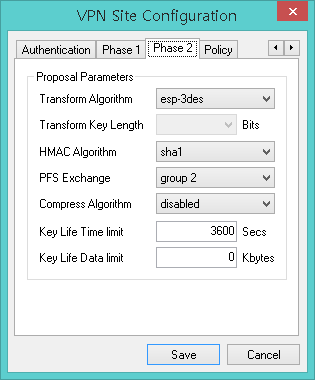

8. in rv120w setting for advanced seup> Policy Type>
there's two option FQDN and IP Adress
when I'm in none static IP Adress environment, how should I set that field?
RV120w do not support none static IP Adress?
Solved! Go to Solution.
- Labels:
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2014 01:39 AM
Hi kastwf001,
My name is Mehdi from Cisco Technical Support, just want to inform you regarding QuickVPN is an light software using IPsec service of windows, so here it depend of windows and firewall ... IPsec setting on windows, encryption ...
anyhow for RV120W it's open for 3rd party software as ShrewVPN , TheGreenBow ... and working as expected since those software are using their ip sec services ..
Please follow configuration steps on RV120W and ShrewVPN (screenshots taken from you post) :


Please let me know if you have any question
Please rate the post or mark as answered to help other Cisco Customers
Regards
Mehdi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2014 01:39 AM
Hi kastwf001,
My name is Mehdi from Cisco Technical Support, just want to inform you regarding QuickVPN is an light software using IPsec service of windows, so here it depend of windows and firewall ... IPsec setting on windows, encryption ...
anyhow for RV120W it's open for 3rd party software as ShrewVPN , TheGreenBow ... and working as expected since those software are using their ip sec services ..
Please follow configuration steps on RV120W and ShrewVPN (screenshots taken from you post) :


Please let me know if you have any question
Please rate the post or mark as answered to help other Cisco Customers
Regards
Mehdi
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide