- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2015 01:15 PM
Hi,
I've been trying to set up my Cisco RV180W Router as an IPSec VPN client but have run into an issue which I'm hoping someone can help me with. I've managed to get the configuration working so that the Cisco IPSec VPN client successfully authenticates against the XAUTH user I have set on the router, however during negotiation, the client terminates with the following error message repeatedly appearing on the router: "Tue Oct 20 19:41:53 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<IP OF CLIENT>>[34360] does not have mode config".
I've read around the internet and a number of people seem to be saying that the Cisco VPN Client isn't compatible with the router, however the same happens for my iPhone VPN client.
Is there any way that this can be made to work? Below I've attached the full configuration files and log files. Thank you very much in advance.
Log file from router (I've changed the IPs to <<Client and Router IP>> respectively as well as refs to MAC addresses)
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: Floating ports for NAT-T with peer <<CLIENT IP>>[44074]
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] WARNING: Ignore INITIAL-CONTACT notification from <<CLIENT IP>>[44074] because it is only accepted after phase1.
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: NAT-D payload does not match for <<ROUTER IP>>[4500]
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: NAT-D payload does not match for <<CLIENT IP>>[44074]
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: Received unknown Vendor ID
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: Received Vendor ID: CISCO-UNITY
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: NAT detected: Local is behind a NAT device. and alsoPeer is behind a NAT device
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: Sending Xauth request to <<CLIENT IP>>[44074]
Tue Oct 20 20:03:10 2015 (GMT +0000): [r1] [IKE] INFO: ISAKMP-SA established for <<ROUTER IP>>[4500]-<<CLIENT IP>>[44074] with spi=<<XXXXX>>.
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: Received attribute type "ISAKMP_CFG_REPLY" from <<CLIENT IP>>[44074]
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: Login succeeded for user "myusername"
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: XAuthUser myusername Logged In from IP Address <<CLIENT IP>>
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: Sending Informational Exchange: notify payload[10381]
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: Received attribute type "ISAKMP_CFG_REQUEST" from <<CLIENT IP>>[44074]
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] WARNING: Ignored attribute 5
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] WARNING: Ignored attribute 28683
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] WARNING: Ignored attribute 28684
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: Local configuration for <<CLIENT IP>>[44074] does not have mode config
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] ERROR: delete payload with invalid doi:0.
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: Purged ISAKMP-SA with proto_id=ISAKMP and spi=<<XXXXX>>.
Tue Oct 20 20:03:15 2015 (GMT +0000): [r1] [IKE] INFO: XAuthUser myusername Logged Out from IP Address <<CLIENT IP>>
Tue Oct 20 20:03:16 2015 (GMT +0000): [r1] [IKE] INFO: ISAKMP-SA deleted for <<ROUTER IP>>[4500]-<<CLIENT IP>>[44074] with spi=<<XXXXX>>
Router configuration
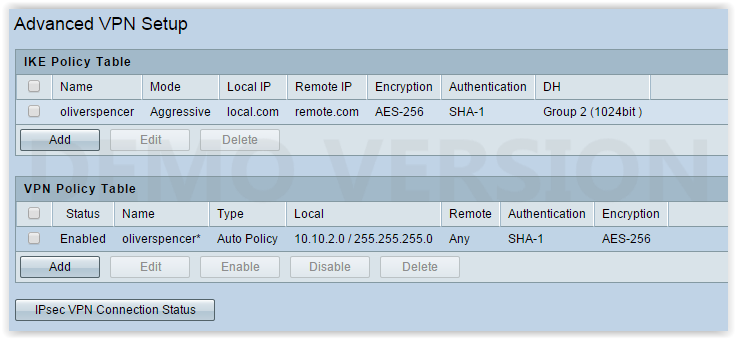
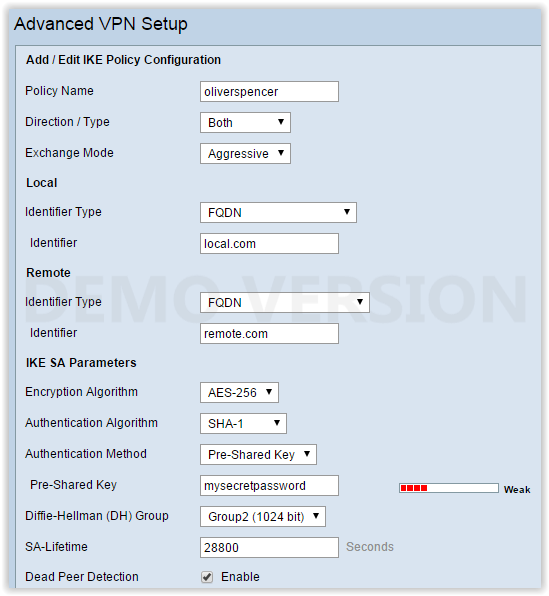
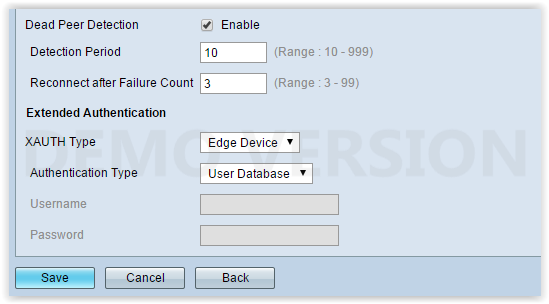
IKE Policy
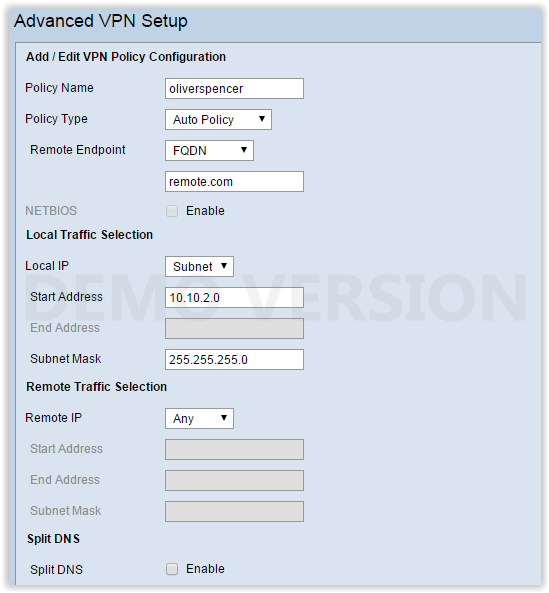
VPN Policy
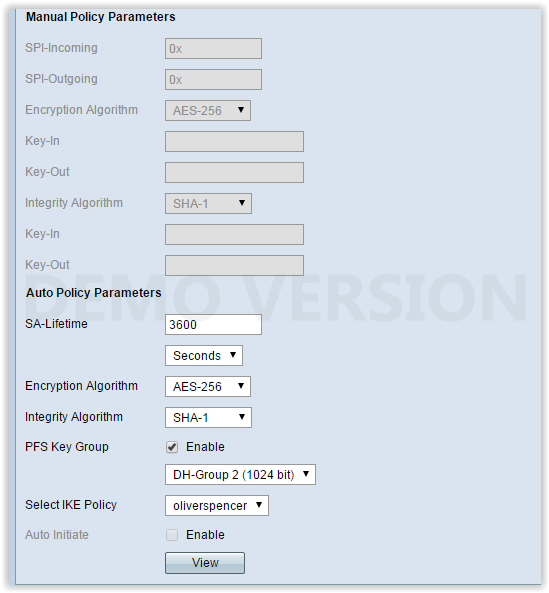
Client config
Host: << ROUTER IP>>
Group Authentication Name: remote.com
Group Authentication Password: mysecretpassword
Transport: Enable Transparent Tunneling; IPSec over UDP (NAT/PAT)
Username: myusername
Password: mypassword
Solved! Go to Solution.
- Labels:
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2015 07:11 AM
Thank you for contacting Cisco.
Correct, the RV180 is not compatible with the Cisco VPN Client. The Iphone uses the Cisco VPN Client.
You could use the PPTP server on the RV180 to connect a PPTP Client.
Also, he RV180 will allow an IPsec connection to 3rd party clients. Greenbow and Shrew Soft are 2 clients commonly used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2015 07:11 AM
Thank you for contacting Cisco.
Correct, the RV180 is not compatible with the Cisco VPN Client. The Iphone uses the Cisco VPN Client.
You could use the PPTP server on the RV180 to connect a PPTP Client.
Also, he RV180 will allow an IPsec connection to 3rd party clients. Greenbow and Shrew Soft are 2 clients commonly used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2015 07:54 AM
Thanks for your note. Can you advise which Cisco routers are able to support the Cisco VPN Client, as I'd prefer to steer clear of PPTP due to security concerns.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2016 09:59 AM
did you manage to get shewsoft working?
will be grateful for any help
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2016 02:50 PM
Hi Saleemarchd1:
What problems did you have here? I have someone on my team who actually installed it as a solution, and should be able to help. I will have them respond to this post if you can tell me what problems you're having..
Thanks
Glenn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2016 03:20 PM
Hi Glenn
see my reply to your teammates post.. 2 posts above.. describes my problem with the VPN client and images with the settings on shrewsoft client.
thanks
Hello Michael
I have the exact same problem. Im trying to use shrewsoft to connect to this but no avail
I have configured the IKE Policy etc in the server as shown in the above screenshot.
pre-shared key configured
bringing up tunnel ...
negotiation timout occurred
tunnel disabled
detached from key daemon
I get a error everytime i connect.
what should i set on the shrewsoft program
I set the host ip address correctly, for local identity used key identifier as well as fqdn and swapped the remote.com and local.com with the local and remote id. as well as set the pre share key.. but still struggling. :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2016 08:02 AM
Hi Glen
Any help willbe appreciated. hope you have seen my reply. look forward to your post back
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2016 09:56 AM
Hello Michael
I have the exact same problem. Im trying to use shrewsoft to connect to this but no avail
I have configured the IKE Policy etc in the server as shown in the above screenshot.
pre-shared key configured
bringing up tunnel ...
negotiation timout occurred
tunnel disabled
detached from key daemon
I get a error everytime i connect.
what should i set on the shrewsoft program
I set the host ip address correctly, for local identity used key identifier as well as fqdn and swapped the remote.com and local.com with the local and remote id. as well as set the pre share key.. but still struggling. :(
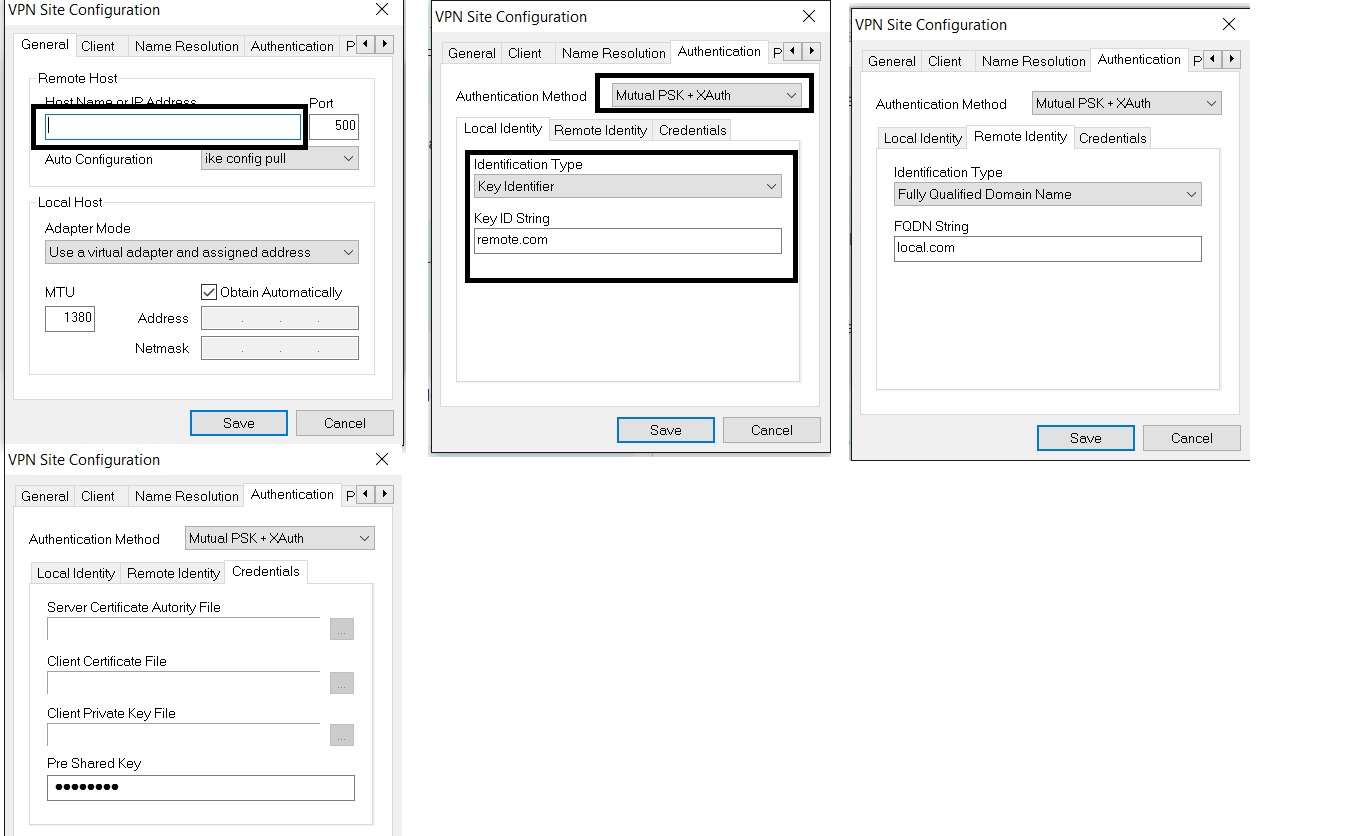
Your help will be greatly appreciated.
thanks
Saleem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2015 08:11 AM
Unfortunately the Cisco VPN Client is EOL. See link below.
http://www.cisco.com/c/en/us/products/collateral/security/vpn-client/end_of_life_c51-680819.html
The only options currently in the Small Business router would be a PPTP or 3rd party IPsec client.
The Cisco ASA5500 series support the Cisco Anyconnect VPN Client.