- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- RV340 - Block A List Of IP Addresses - How To?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 - Block A List Of IP Addresses - How To?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 01:19 PM
Hello,
There are several comprehensive lists of known bad actor IP addresses.
How to create a blacklist of IP addresses on the RV34x?
I have checked all available options in the admin GUI, plus all available documentation and it seems there is no way to do this.
If there is no way, that is a very regrettable limitation.
Perhaps Cisco wants to force license subscriptions of their version of such security?
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 03:09 PM
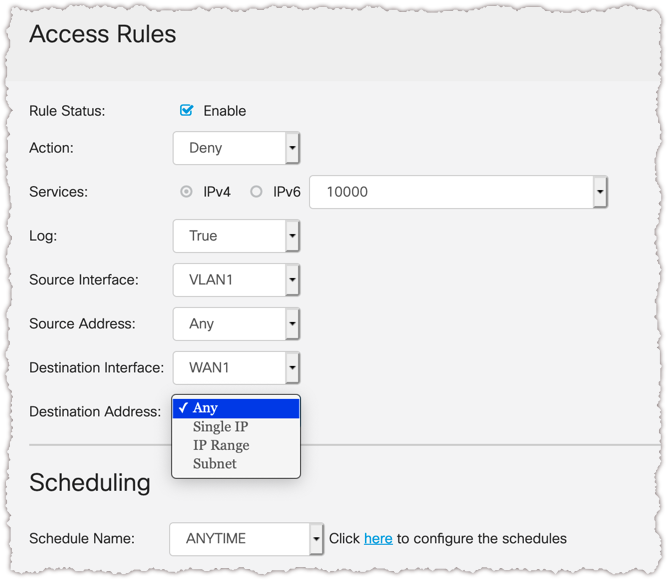
You can use ACL to block IPs. If you network the list of IPs then you can block them as a network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 04:25 PM - edited 05-23-2019 04:28 PM
That is not a solution unfortunately. Your suggestion to use ACLs would require entering hundreds or thousands of single IP addresses. Entering IP address ranges would block too many unintended websites/servers - although I don't know what you mean exactly by networking the list of IPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 12:12 AM - edited 05-24-2019 12:23 AM
I superscope my IP blocks into networks. It is the way I work. Using a Class A block would block a lot more IPs than I would want to make a list of. Lists to me are small scale.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 06:36 AM
You cannot use network/object groups in the access rules on the RV340.
So you would have to list every single IP, IP range or sub-net with a separate rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 07:42 AM
Hi, please let me know which lists you a referring to.
IP Reputation and Webreputation is typically a professional service which costs money. Generating, Verifying, and Managing these lists is a lot of effort. Especially adding IP addresses is best done as a cloud service.
Webreputation can be done very easily and for free with Cisco Umbrella.
But you are correct, the add-on security licnese will enable a set of advanced security features, like web reputation. It will block automatically dangerous web addresses.
Another way is to block and allow specific apps. The Rv340 inspects and identifies more than 500 different internet apps which you can use to allow or block.
Hope this helps.
Jo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2019 12:58 PM
It is possible on Windows with etc\hosts file but that is not possible on IOS or IOT devices or easily on Android or Linux or devices and of course each would have to be managed separately.
It really would be optimum to block IP Addresses on the router instead of each device.
Apparently there is a way on Ubiquiti routers - may be the only option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2019 02:42 AM
Hi, how many IP addresses to you want to block ? You can block single or a range or a subnet.
Do you want to import a list of IP addresses?
You can set up different rules for different local IP Groups or device types.
Hope you can help me better understand the requirement.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2019 05:55 PM - edited 05-27-2019 05:56 PM
OK, you should have read the thread to understand the requirement.
The intent is to block many individual IP addresses.
Blocking ranges it not option, that would block too many unintended sites.
Blocking individual IP addresses is not an option there are way too many.
Access Control Rules wont work for those reasons.
Further, Rutgers University CS Dept. has comprehensive telemetry and provides tremendous insight into attacker IP Addresses:
report.cs.rutgers.edu/mrtg/drop/dropstat.cgi?start=-1w
They supply lists of hundreds if not thousands of individual addresses:
report.cs.rutgers.edu/DROP/attackers
There are many such lists:
badips.com
blacklists.co/download/mysql.txt
malwaredomainlist.com/mdl.php?sort=IP&
The benefit for blocking many discreet addresses with one rule should be obvious.
This could be done with Access Control Lists.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2019 11:08 PM - edited 05-27-2019 11:09 PM
I block big ranges with ACLs. If I need access to an IP address or range then I modify my ACL lists. I think you are thinking about this too hard. As far as testing rules it is going to be the same. Using ranges and class address blocking is going to make you router faster. I would rather block a class b than a 1000 IP addresses. It is more efficient. Over laps can be fixed if you need it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2019 03:30 AM
Sorry if I ask too many questions. I just want to understand better what your requirements are and how many IP addresses you want to block and also how you want to manage these IP addresses.
For an SMB firewall it is much better from a perfromance point of view to follow what @leecoxhouse1 recommends.
Form a security point of view you can add this by using a dynamic IP reputation service maintained by a Threatintelligence company. These provide in almost realtime IP reputations for web addresses and can block dangerous websites based on several rules ( who owns them, how many webaddresses do they have ,are they brand new ). They can identify Spammers and Threats very quickly.
( Of course i recommend Cisco Umbrella or OpenDNS it is run by Cisco)
You do not want to get your hosts to dangerous IP addresses use a threat intelligence service. You do want to block specific addresses use the ACL or the content filter. You can also block your hosts from using internet applications on the RV340, like torrents etc.
If you want to block advertisements check out https://en.wikipedia.org/wiki/Pi-hole.
Best
Jo
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide