- Cisco Community
- Technology and Support
- Networking
- Routing
- Access DMZ systems from either default gateways
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Access DMZ systems from either default gateways
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2019 12:45 PM
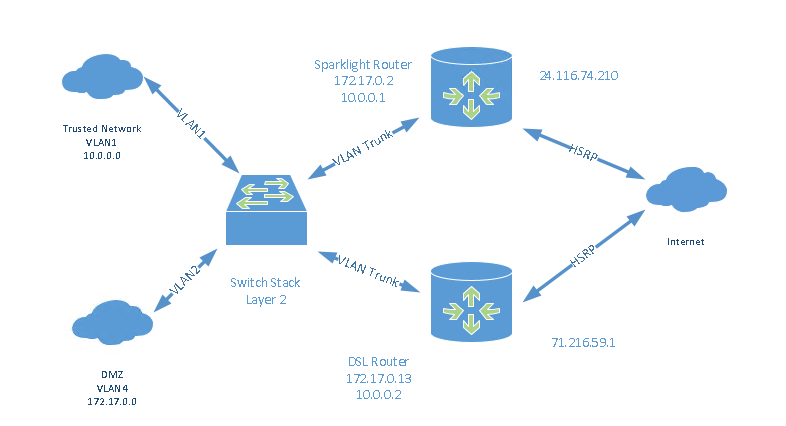
Hi, I have two routers set up with HSRP connected to two ISPs, one cable and one DSL, so customers can always access our DMZ should one ISP go down. The routers are connected to our trusted network, VLAN1, and our DMZ, VLAN4.
But trusted network PCs going out the default gateway of the Cable Router, can’t connect to the DMZ servers with a default gateway of DSL router, or vice-a-versa . I would like to find a solution for this, so I can balance network load between the two ISPs. I think that we might be able to do this with source routing or route maps. Do you have any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2019 01:57 PM
Hello,
post a drawing of your topology. Policy based routing could work, post the running configs of both routers as well so we can help with the details...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 02:01 AM
Hello
With the topology you have highlighted I would expect the routing between vlan 1 and vlan 4 users will be done via the L3 switch that interconnects to two rtrs facing your ISP’s
Is this correct if so can you post the configuration of the L3 switch?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 08:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 08:37 AM
Hello
Looks like you will need to route leak on the two rtrs to allow inter vrf comunication.
Are you using any dynamic routing on those two rtrs - if possiblle post the configuration of those two rtrs please
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 08:52 AM
Hi Paul, The only routing protocol I have running on these routers is BGP, for a IPSEC GRE VPN tunnel.
-Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2019 08:46 AM
Hi Guys, for simplicity, posting just what might be applicable. Let me know if I am missing anything, or you want config from other router - configured pretty much the same:
version 16.9
no service pad
no service dhcp
hostname Sparklight
boot-start-marker
boot system bootflash:isr4300-universalk9.16.09.04.SPA.bin
boot-end-marker
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
no ip source-route
track 10 ip sla 10 reachability
!
no cdp run
!
class-map type inspect match-all Inside-DMZ-Class
match access-group name Inside-DMZ
class-map type inspect match-all Outside-Inside-Class
match access-group name Outside-Inside
class-map type inspect match-all Outside-DMZ-Class
match access-group name Outside-DMZ
class-map type inspect match-any All-Protocols-Class
match protocol tcp
match protocol udp
match protocol icmp
!
policy-map type inspect Outside-Inside-Policy
class type inspect Outside-Inside-Class
inspect
class class-default
drop
policy-map type inspect All-Protocols-Policy
class type inspect All-Protocols-Class
inspect
class class-default
drop
policy-map type inspect Outside-DMZ-Policy
class type inspect Outside-DMZ-Class
inspect
class class-default
drop log
policy-map type inspect Inside-DMZ-Policy
class type inspect Inside-DMZ-Class
inspect
class class-default
drop
!
zone security DMZ
zone security Inside
zone security Outside
zone security Snort
zone-pair security DMZ-Inside source DMZ destination Inside
service-policy type inspect All-Protocols-Policy
zone-pair security DMZ-Outside source DMZ destination Outside
service-policy type inspect All-Protocols-Policy
zone-pair security Inside-DMZ source Inside destination DMZ
service-policy type inspect Inside-DMZ-Policy
zone-pair security Inside-Outside source Inside destination Outside
!
interface GigabitEthernet0/0/0
no ip address
ip nat inside
zone-member security Inside
negotiation auto
spanning-tree portfast disable
!
service-policy type inspect All-Protocols-Policy
zone-pair security Outside-DMZ source Outside destination DMZ
service-policy type inspect Outside-DMZ-Policy
zone-pair security Outside-Inside source Outside destination Inside
service-policy type inspect Outside-Inside-Policy
zone-pair security Snort-Outside source Snort destination Outside
service-policy type inspect All-Protocols-Policy
!
interface GigabitEthernet0/0/0.1
encapsulation dot1Q 1 native
ip address 10.0.0.1 255.255.0.0
ip nat inside
zone-member security Inside
!
interface GigabitEthernet0/0/0.4
encapsulation dot1Q 4
ip address 172.17.0.2 255.255.0.0
ip nat inside
zone-member security DMZ
standby version 2
standby 1 ip 172.17.0.20
standby 1 preempt
standby 1 track 10 decrement 10
!
interface GigabitEthernet0/0/1
ip flow monitor FlowMonitor input
ip flow monitor FlowMonitor output
ip address 24.116.74.210 255.255.255.240
ip nat outside
zone-member security Outside
negotiation auto
spanning-tree portfast disable
ip forward-protocol nd
ip tcp synwait-time 10
no ip http server
ip http access-class ipv4 RouterAccess
ip http authentication local
ip http secure-server
ip http session-idle-timeout 1200
ip tftp source-interface GigabitEthernet0/0/0.1
ip nat inside source static x
xxx
xxx
ip route 0.0.0.0 0.0.0.0 24.116.74.209
ip access-list standard ovrld
permit 172.17.0.0 0.0.255.255
permit 10.0.0.0 0.255.255.255
ip access-list extended Inside-DMZ
permit tcp any any eq www
permit tcp any any eq 443
ip access-list extended Outside-DMZ
permit tcp any host 172.17.0.xxx eq 30175
xxx
xxx
ip sla 10
icmp-echo 8.8.8.8
frequency 5
ip sla schedule 10 life forever start-time now
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide