- Cisco Community
- Technology and Support
- Networking
- Routing
- ASA 5520 to 5505 ipsec tunnel help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 12:56 PM
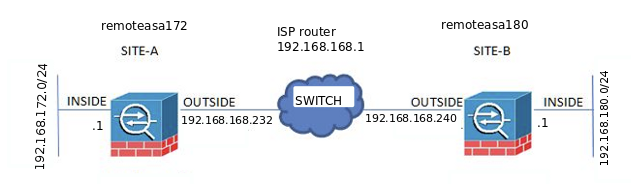
How to configure a ipsec tunnel between a Cisco ASA 5520 and a Cisco ASA 5505?
============================---------------------------remoteasa172-------------------------------=================================
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
: ASA Version 9.1(7)32
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 182.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.180.0 255.255.255.0 192.168.168.240 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map enable interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.172.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.172.3-192.168.172.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa172#
============================---------------------------remoteasa180-------------------------------=================================
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
: ASA Version 9.2(4)5
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
dhcpd dns 192.168.168.1
dhcpd ping_timeout 20
dhcpd domain myudomain.com
dhcpd auto_config outside
dhcpd option 3 ip 192.168.180.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.180.3-192.168.180.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa180#
Solved! Go to Solution.
- Labels:
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 05:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 06:24 AM
The posted config for 171-233 does not have the n
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 06:29 AM
Apologies - I hit post too soon. I was saying that the nat suggested by Antonin does not show up in the posted config for 171-233. Put it in and test again. I would prefer a test from a PC connected in one LAN to a PC connected in the remote LAN. And follow the ping attempt with show crypto ipsec sa on both ASAs.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 08:46 AM - edited 02-25-2019 09:06 AM
I have two standing pings running from 192.168.171.3 to 192.168.172.1 (ping 192.168.171.1 is good) and from 192.168.171.3 from 192.168.172.1 (ping 192.168.171.1 is good)
I CAN'T GET RID OF THIS NAT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
I'm having a hard time getting rid of a nat....
I'm trying to clear it but I can't find it.
asa171-233(config)# clear Xlate interface inside
INFO: 0 xlate deleted
asa171-233(config)#
asa171-233# clear Xlate interface outside
INFO: 0 xlate deleted
asa171-233# conf t
asa171-233(config)# sh run | i nat
nat (inside,outside) static interface service tcp www 8080
asa171-233(config)# no nat (inside,outside) static interface service tcp www 8$
no nat (inside,outside) static interface service tcp www 8080
^
ERROR: % Invalid input detected at '^' marker.
asa171-233(config)#
asa171-233(config)# sh run | i nat
nat (inside,outside) static interface service tcp www 8080
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)# no nat (inside,outside) static interface service tcp www 8$
no nat (inside,outside) static interface service tcp www 8080
^
ERROR: % Invalid input detected at '^' marker.
asa171-233(config)# no nat (inside,outside) ?
configure mode commands/options:
<1-2147483647> Position of NAT rule within before auto section
after-auto Insert NAT rule after auto section
source Source NAT parameters
asa171-233(config)# no nat (inside,outside) a
asa171-233(config)# no nat (inside,outside) after-auto ?
configure mode commands/options:
<1-2147483647> Position of NAT rule within after auto section
source Source NAT parameters
asa171-233(config)# no nat (inside,outside) after-auto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 09:09 AM - edited 02-25-2019 09:12 AM
Got rid of the nat :-) Ping still not working......
asa171-233(config)# sh run | i nat
nat (inside,outside) source static 192.168.171.0_24 192.168.171.0_24 destination static 192.168.172.0_24 192.168.172.0_24 no-proxy-arp route-lookup
nat (inside,outside) static interface service tcp www 8080
asa171-233(config)# no object network HTTP_ALLAN_OBJ
asa171-233(config)# sh run | i nat
nat (inside,outside) source static 192.168.171.0_24 192.168.171.0_24 destination static 192.168.172.0_24 192.168.172.0_24 no-proxy-arp route-lookup
asa171-233(config)#
CONFIG CONFIG CONFIG CONFIG CONFIG CONFIG CONFIG CONFIG
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)# sh run
: Saved
:
: Serial Number: JMX1510L0T6
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
:
ASA Version 9.1(7)23
!
hostname asa171-233
domain-name mydomain.com
enable password N7HlIItY8AVJppkQ encrypted
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.233 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.171.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif mngt
security-level 0
ip address 10.10.10.13 255.255.255.224
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name mydomain.com
object network 192.168.172.0_24
subnet 192.168.172.0 255.255.255.0
object network 192.168.171.0_24
subnet 192.168.171.0 255.255.255.0
access-list OUTSIDE-IN extended permit ip any any
access-list OUTSIDE-IN extended permit icmp any any
access-list OUTSIDE-IN extended permit tcp any any
access-list OUTSIDE-IN extended permit tcp any any eq www log errors
access-list OUTSIDE-OUT extended permit ip any any
access-list OUTSIDE-OUT extended permit icmp any any
access-list OUTSIDE-OUT extended permit tcp any any
access-list INSIDE-IN extended permit ip any any
access-list INSIDE-IN extended permit icmp any any
access-list INSIDE-IN extended permit tcp any any
access-list INSIDE-OUT extended permit ip any any
access-list INSIDE-OUT extended permit icmp any any
access-list INSIDE-OUT extended permit tcp any any
access-list LAN_Traffic_172_232 extended permit ip object 192.168.171.0_24 object 192.168.172.0_24
pager lines 24
logging enable
logging monitor debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu mngt 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any echo inside
icmp permit any echo-reply inside
icmp permit any mngt
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static 192.168.171.0_24 192.168.171.0_24 destination static 192.168.172.0_24 192.168.172.0_24 no-proxy-arp route-lookup
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 5
route outside 192.168.172.0 255.255.255.0 192.168.168.232 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic_172_232
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.168.0 255.255.255.0 outside
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.171.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.171.3-192.168.171.63 inside
dhcpd enable inside
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 73ozQQQ.JMBHDyQz encrypted
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:040fce9ba2f272f19df2b381639e1c51
: end
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
asa171-233(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 09:11 AM
Your problem with this is that you are looking at this statement
nat (inside,outside) static interface service tcp www 8080
as something in global config. And the output of your show command sort of makes it look like that. But it is really part of the configuration of the network object
object network HTTP_ALLAN_OBJ
so in config mode try this
object network HTTP_ALLAN_OBJ
no nat (inside,outside) static interface service tcp www 8080
that should take care of that nat.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 09:24 AM
The config that you just posted looks good to me. Looks like you got rid of the nat that you were trying to remove
nat (inside,outside) static interface service tcp www 8080
And even if you have not removed it I do not think that it was causing the issue. What caused the issue was the dynamic nat for everything going inside to outside. That nat no longer shows up. So I think you should be good. In fact if you have removed those nat statements then you really do not need the static nat which you have in the config.
So you are trying to ping and it is not working. What do you get in show crypto ipsec sa on both ASA?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:43 AM
I removed the nat (no nats left). Here is the SA.
asa171-233# sh cry isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.168.168.232
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
asa171-233#
asa171-233# sh cry ipsec sa
interface: outside
Crypto map tag: CMAP, seq num: 72, local addr: 192.168.168.233
access-list LAN_Traffic_172_232 extended permit ip 192.168.171.0 255.255.255.0 192.168.172.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.171.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.172.0/255.255.255.0/0/0)
current_peer: 192.168.168.232
#pkts encaps: 492, #pkts encrypt: 492, #pkts digest: 492
#pkts decaps: 2107, #pkts decrypt: 2107, #pkts verify: 2107
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 492, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.168.233/0, remote crypto endpt.: 192.168.168.232/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: EF3725F7
current inbound spi : 26FE6696
inbound esp sas:
spi: 0x26FE6696 (654206614)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: CMAP
sa timing: remaining key lifetime (kB/sec): (4373876/18235)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xEF3725F7 (4013368823)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: CMAP
sa timing: remaining key lifetime (kB/sec): (4373971/18235)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
asa171-233#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:35 AM
Thanks Rick, got it. I still have some dhcp stuff I can get rid of...
I've been thinking that there may be a conflict between the ((crypto map CMAP)) commands and the ((crypto ikev1/tunnel-group)) commands....
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic_172_232
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
policy 1
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:42 AM
what do you get in show crypto ipsec sa from both ASAs?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:44 AM
Deleted all nat and dchp.
asa171-233# sh cry isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.168.168.232
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
asa171-233# sh cry ips sa
asa171-233# sh cry i[sec
asa171-233# sh cry ipsec
asa171-233# sh cry ipsec sa
interface: outside
Crypto map tag: CMAP, seq num: 72, local addr: 192.168.168.233
access-list LAN_Traffic_172_232 extended permit ip 192.168.171.0 255.255.255.0 192.168.172.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.171.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.172.0/255.255.255.0/0/0)
current_peer: 192.168.168.232
#pkts encaps: 492, #pkts encrypt: 492, #pkts digest: 492
#pkts decaps: 2107, #pkts decrypt: 2107, #pkts verify: 2107
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 492, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.168.233/0, remote crypto endpt.: 192.168.168.232/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: EF3725F7
current inbound spi : 26FE6696
inbound esp sas:
spi: 0x26FE6696 (654206614)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: CMAP
sa timing: remaining key lifetime (kB/sec): (4373876/18235)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xEF3725F7 (4013368823)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: CMAP
sa timing: remaining key lifetime (kB/sec): (4373971/18235)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
asa171-233#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:48 AM
These lines demonstrate that the vpn is working and is passing traffic in both directions.
#pkts encaps: 492, #pkts encrypt: 492, #pkts digest: 492
#pkts decaps: 2107, #pkts decrypt: 2107, #pkts verify: 2107
If something is not working I do not believe that the issue involves the vpn. What is your current assessment of the situation? What is working and what is not working?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:55 AM
Holy S*** I restarted the ping and now it works :-) You're the best.
Which one of your answers should I select for the solution?
It was the NATs? Remember how hard you worked to get a NAT to the inside to outside and a PAT to the outside to inside? Do you think that I can put them back?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:57 AM
I was wrong, I up arrowed to the local network ping...not the tunnel ping. The laptops are still not pinging and the router is not pinging....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:51 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide