- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA blocked PCs from accessing outside of network.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2022
03:26 AM
- last edited on
11-15-2022
08:43 PM
by
Translator
![]()
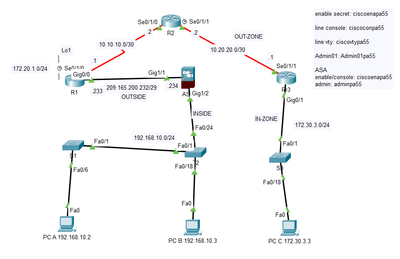
Hello, I was doing a sample skills test and I have issue with ASA firewall blocking PCs to access outside of ASA firewall.
In this scenario, I am trying to ping from PC-B to R1's Loopback (172.20.1.1). Meaning, Inside Network go to Outside Network.
Unfortunately, PC-B only able to ping its default gateway (192.168.10.1). The moment I tried to ping to ASA Interface Gig 1/1 (209.165.200.234), it shows request timeout. This means, it blocks at ASA firewall and prevent PC-B from going outside of the network.
I have use the following configuration:
ASA Firewall Config
CCNAS-ASA#sh run
: Saved
:
ASA Version 9.6(1)
!
hostname CCNAS-ASA
domain-name ccnasecurity.com
enable password [deleted to prevent marked as spam] encrypted
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 209.165.200.234 255.255.255.248
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.10.1 255.255.255.0
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
shutdown
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
shutdown
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
object network inside-net
subnet 192.168.10.0 255.255.255.0
nat (inside,outside) dynamic interface
!
route outside 0.0.0.0 0.0.0.0 209.165.200.233 1
!
!
!
aaa authentication ssh console LOCAL
!
username admin password [deleted to prevent marked as spam] encrypted
!
class-map inspection_default
match default-inspection-traffic
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect tftp
!
service-policy global_policy global
!
telnet timeout 5
ssh 172.30.3.3 255.255.255.255 outside
ssh timeout 10
!
dhcpd address 192.168.10.6-192.168.10.30 inside
dhcpd enable inside
=== END ===
I have provided the pkt and the pdf file under this post.
Much appreciated for your help
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2022 06:48 AM - edited 11-25-2022 01:43 AM
After several hours researching, I have found the answer. It turns out I need to configure access-list on ASA firewall, in order to allow INSIDE network to OUTSIDE network.
The following is the configuration added:
CCNAS-ASA(config)#access-list IN-OUT extended permit ip 192.168.10.0 255.255.255.0 any
CCNAS-ASA(config)#access-group IN-OUT in interface inside
Hopefully, this will find helpful for those who seek it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2022 06:48 AM - edited 11-25-2022 01:43 AM
After several hours researching, I have found the answer. It turns out I need to configure access-list on ASA firewall, in order to allow INSIDE network to OUTSIDE network.
The following is the configuration added:
CCNAS-ASA(config)#access-list IN-OUT extended permit ip 192.168.10.0 255.255.255.0 any
CCNAS-ASA(config)#access-group IN-OUT in interface inside
Hopefully, this will find helpful for those who seek it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide