tomasa180(config)#
tomasa180(config)# clear access-list OUTSIDE-IN counters
tomasa180(config)# clear access-list OUTSIDE-OUT counters
tomasa180(config)# clear access-list INSIDE-IN counters
tomasa180(config)# clear access-list INSIDE-OUT counters
tomasa180(config)#
tomasa180(config)#
tomasa180(config)#
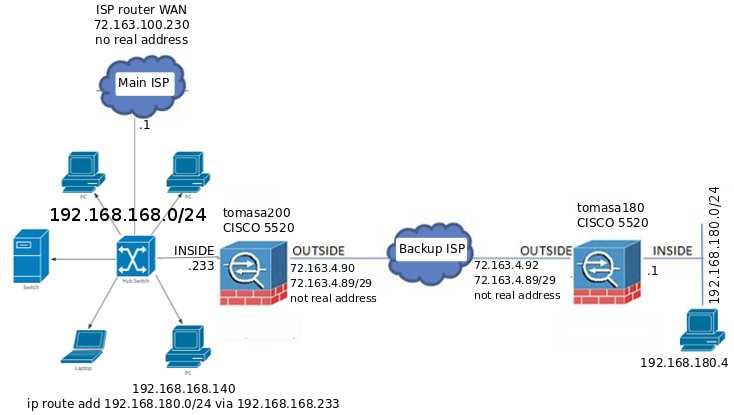
tomasa180(config)# PING RECEIVED FROM 192.168.168.140 TO SERVER AT 192.168.180.4
tomasa180(config)# ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=1 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=1 len=56
ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=2 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=2 len=56
ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=3 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=3 len=56
ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=4 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=4 len=56
ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=5 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=5 len=56
ICMP echo request from outside:192.168.168.140 to inside:192.168.180.4 ID=10856 seq=6 len=56
ICMP echo reply from inside:192.168.180.4 to outside:192.168.168.140 ID=10856 seq=6 len=56
tomasa180(config)# sh acc
tomasa180(config)# sh access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list OUTSIDE-IN; 8 elements; name hash: 0x9ccc1a31
access-list OUTSIDE-IN line 1 extended permit icmp any any echo (hitcnt=0) 0x250e6fd2
access-list OUTSIDE-IN line 2 extended permit icmp any any echo-reply (hitcnt=0) 0x2687e947
access-list OUTSIDE-IN line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x5be3a224
access-list OUTSIDE-IN line 4 extended permit icmp any any unreachable (hitcnt=0) 0x25d8467a
access-list OUTSIDE-IN line 5 extended permit icmp any any source-quench (hitcnt=0) 0x9fab9a16
access-list OUTSIDE-IN line 6 extended permit icmp any any (hitcnt=0) 0x2d9fa831
access-list OUTSIDE-IN line 7 extended permit tcp any any (hitcnt=0) 0x988e8549
access-list OUTSIDE-IN line 8 extended permit ip any any (hitcnt=0) 0x03aa8b7f
access-list OUTSIDE-OUT; 8 elements; name hash: 0x2fb3cebb
access-list OUTSIDE-OUT line 1 extended permit icmp any any echo (hitcnt=0) 0xb0cdcb44
access-list OUTSIDE-OUT line 2 extended permit icmp any any echo-reply (hitcnt=1) 0xe6e17f86
access-list OUTSIDE-OUT line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x43b2e4a3
access-list OUTSIDE-OUT line 4 extended permit icmp any any unreachable (hitcnt=0) 0x71200251
access-list OUTSIDE-OUT line 5 extended permit icmp any any source-quench (hitcnt=0) 0xb8197876
access-list OUTSIDE-OUT line 6 extended permit icmp any any (hitcnt=0) 0xf4c12f3b
access-list OUTSIDE-OUT line 7 extended permit ip any any (hitcnt=13) 0x85562ffc
access-list OUTSIDE-OUT line 8 extended permit tcp any any (hitcnt=0) 0xdb94916e
access-list INSIDE-IN; 8 elements; name hash: 0xf1656621
access-list INSIDE-IN line 1 extended permit icmp any any (hitcnt=1) 0x5cfc8e4a
access-list INSIDE-IN line 2 extended permit icmp any any echo (hitcnt=0) 0x9c95fbfd
access-list INSIDE-IN line 3 extended permit icmp any any echo-reply (hitcnt=0) 0x9d795e65
access-list INSIDE-IN line 4 extended permit icmp any any time-exceeded (hitcnt=0) 0x27cfbb1c
access-list INSIDE-IN line 5 extended permit icmp any any unreachable (hitcnt=0) 0xb7cbe6d3
access-list INSIDE-IN line 6 extended permit icmp any any source-quench (hitcnt=0) 0x14c4a592
access-list INSIDE-IN line 7 extended permit ip any any (hitcnt=13) 0xece2599d
access-list INSIDE-IN line 8 extended permit tcp any any (hitcnt=0) 0x8be220e6
access-list INSIDE-OUT; 8 elements; name hash: 0x55692ef1
access-list INSIDE-OUT line 1 extended permit icmp any any echo (hitcnt=0) 0x8675fd2a
access-list INSIDE-OUT line 2 extended permit icmp any any echo-reply (hitcnt=0) 0x601c23e7
access-list INSIDE-OUT line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x1ea93d27
access-list INSIDE-OUT line 4 extended permit icmp any any unreachable (hitcnt=0) 0x4b244f07
access-list INSIDE-OUT line 5 extended permit icmp any any source-quench (hitcnt=0) 0xa4ebb397
access-list INSIDE-OUT line 6 extended permit icmp any any (hitcnt=0) 0x121fd7eb
access-list INSIDE-OUT line 7 extended permit ip any any (hitcnt=0) 0x91f5358c
access-list INSIDE-OUT line 8 extended permit tcp any any (hitcnt=0) 0x19534f9c
access-list LAN_Traffic_200; 1 elements; name hash: 0xe8cacd0c
access-list LAN_Traffic_200 line 1 extended permit ip object 192.168.180.0_24 object 192.168.168.0_24 (hitcnt=14) 0xd6eace25
access-list LAN_Traffic_200 line 1 extended permit ip 192.168.180.0 255.255.255.0 192.168.168.0 255.255.255.0 (hitcnt=14) 0xd6eace25
tomasa180(config)#
tomasa180(config)# clear access-list OUTSIDE-IN counters
tomasa180(config)# clear access-list OUTSIDE-OUT counters
tomasa180(config)# clear access-list INSIDE-IN counters
tomasa180(config)# clear access-list INSIDE-OUT counters
tomasa180(config)#
tomasa180(config)# PING RECEIVED FROM 192.168.168.140 TO ASA AT 192.168.180.1
tomasa180(config)# ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=1 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=2 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=3 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=4 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=5 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=6 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=7 len=56
ICMP echo request from 192.168.168.140 to 192.168.180.1 ID=10861 seq=8 len=56
tomasa180(config)#
tomasa180(config)# sh access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list OUTSIDE-IN; 8 elements; name hash: 0x9ccc1a31
access-list OUTSIDE-IN line 1 extended permit icmp any any echo (hitcnt=0) 0x250e6fd2
access-list OUTSIDE-IN line 2 extended permit icmp any any echo-reply (hitcnt=0) 0x2687e947
access-list OUTSIDE-IN line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x5be3a224
access-list OUTSIDE-IN line 4 extended permit icmp any any unreachable (hitcnt=0) 0x25d8467a
access-list OUTSIDE-IN line 5 extended permit icmp any any source-quench (hitcnt=0) 0x9fab9a16
access-list OUTSIDE-IN line 6 extended permit icmp any any (hitcnt=0) 0x2d9fa831
access-list OUTSIDE-IN line 7 extended permit tcp any any (hitcnt=0) 0x988e8549
access-list OUTSIDE-IN line 8 extended permit ip any any (hitcnt=0) 0x03aa8b7f
access-list OUTSIDE-OUT; 8 elements; name hash: 0x2fb3cebb
access-list OUTSIDE-OUT line 1 extended permit icmp any any echo (hitcnt=0) 0xb0cdcb44
access-list OUTSIDE-OUT line 2 extended permit icmp any any echo-reply (hitcnt=0) 0xe6e17f86
access-list OUTSIDE-OUT line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x43b2e4a3
access-list OUTSIDE-OUT line 4 extended permit icmp any any unreachable (hitcnt=0) 0x71200251
access-list OUTSIDE-OUT line 5 extended permit icmp any any source-quench (hitcnt=0) 0xb8197876
access-list OUTSIDE-OUT line 6 extended permit icmp any any (hitcnt=0) 0xf4c12f3b
access-list OUTSIDE-OUT line 7 extended permit ip any any (hitcnt=2) 0x85562ffc
access-list OUTSIDE-OUT line 8 extended permit tcp any any (hitcnt=0) 0xdb94916e
access-list INSIDE-IN; 8 elements; name hash: 0xf1656621
access-list INSIDE-IN line 1 extended permit icmp any any (hitcnt=0) 0x5cfc8e4a
access-list INSIDE-IN line 2 extended permit icmp any any echo (hitcnt=0) 0x9c95fbfd
access-list INSIDE-IN line 3 extended permit icmp any any echo-reply (hitcnt=0) 0x9d795e65
access-list INSIDE-IN line 4 extended permit icmp any any time-exceeded (hitcnt=0) 0x27cfbb1c
access-list INSIDE-IN line 5 extended permit icmp any any unreachable (hitcnt=0) 0xb7cbe6d3
access-list INSIDE-IN line 6 extended permit icmp any any source-quench (hitcnt=0) 0x14c4a592
access-list INSIDE-IN line 7 extended permit ip any any (hitcnt=2) 0xece2599d
access-list INSIDE-IN line 8 extended permit tcp any any (hitcnt=0) 0x8be220e6
access-list INSIDE-OUT; 8 elements; name hash: 0x55692ef1
access-list INSIDE-OUT line 1 extended permit icmp any any echo (hitcnt=0) 0x8675fd2a
access-list INSIDE-OUT line 2 extended permit icmp any any echo-reply (hitcnt=0) 0x601c23e7
access-list INSIDE-OUT line 3 extended permit icmp any any time-exceeded (hitcnt=0) 0x1ea93d27
access-list INSIDE-OUT line 4 extended permit icmp any any unreachable (hitcnt=0) 0x4b244f07
access-list INSIDE-OUT line 5 extended permit icmp any any source-quench (hitcnt=0) 0xa4ebb397
access-list INSIDE-OUT line 6 extended permit icmp any any (hitcnt=0) 0x121fd7eb
access-list INSIDE-OUT line 7 extended permit ip any any (hitcnt=0) 0x91f5358c
access-list INSIDE-OUT line 8 extended permit tcp any any (hitcnt=0) 0x19534f9c
access-list LAN_Traffic_200; 1 elements; name hash: 0xe8cacd0c
access-list LAN_Traffic_200 line 1 extended permit ip object 192.168.180.0_24 object 192.168.168.0_24 (hitcnt=14) 0xd6eace25
access-list LAN_Traffic_200 line 1 extended permit ip 192.168.180.0 255.255.255.0 192.168.168.0 255.255.255.0 (hitcnt=14) 0xd6eace25
tomasa180(config)#
tomasa180(config)#
tomasa180(config)#