- Cisco Community
- Technology and Support
- Networking
- Routing
- Cannot ping a laptop
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 12:19 PM - edited 03-05-2019 10:59 AM
I have two Cisco Catalyst 3560 switches connected to a Juniper SRX 550 Firewall. I have a laptop connected to each switch, and I'm getting the correct DHCP and default gateways. I can ping everything from the 172.16.64.2 switch, but from the 172.16.128.2 switch, I'm not able to ping the laptop connected to the 172.16.64.2 switch.
Config from the 172.16.64.2/18 switch
=====================================
hostname SW1
!
!
no aaa new-model
ip subnet-zero
no ip domain-lookup
!
!
!
!
no file verify auto
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface FastEthernet0/1
!
....
!
interface FastEthernet0/24
switchport trunk encapsulation dot1q
switchport trunk native vlan 10
switchport mode trunk
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
ip address 172.16.64.2 255.255.192.0
!
ip default-gateway 172.16.64.1
ip classless
ip http server
!
!
control-plane
!
!
line con 0
line vty 0 4
login
line vty 5 15
no login
!
!
end
Config from the 172.16.128.2/18 switch
=====================================
hostname SW2
!
!
no aaa new-model
vtp domain SCOTTSDALE
vtp mode transparent
ip subnet-zero
no ip domain-lookup
!
!
!
!
no file verify auto
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
vlan 128
name Dev
!
interface FastEthernet0/1
.......
!
interface FastEthernet0/23
!
interface FastEthernet0/24
switchport trunk encapsulation dot1q
switchport trunk native vlan 10
switchport mode trunk
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
ip address 172.16.128.2 255.255.192.0
no ip route-cache
!
ip default-gateway 172.16.128.1
ip classless
ip http server
!
!
control-plane
!
!
line con 0
line vty 0 4
login
line vty 5 15
no login
!
!
end
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 06:21 AM
Glad you got it working. Please mark this thread as solved. :)
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 12:27 PM
I noticed that for the 172.16.128.2 switch, under VLAN 1 IP address, it says "no ip route-cache". It doesn't say it on the other switch's VLAN 1 IP address. I'm not sure if that's the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 12:39 PM
Hi there,
On the SRX CLI, what is the output of:
show security zones
show security policies
...possible that the IRBs (aka, SVIs) on the SRX are in different zones and the traffic in one direction is not permitted by policy.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 12:57 PM
I tested this in Packet Tracer since I'm using the same exact switch. It works in PT, but not sure why it doesn't work on the real switch.
https://drive.google.com/open?id=1NhLqlv0C5bI7WwaIEx68Q2QnX3Vg4Qt_
SRX CLI:
## Last changed: 2018-10-15 07:42:35 EDT
version 12.3X48-D70.3;
system {
host-name gw-test;
time-zone EST;
root-authentication {
encrypted-password "$1$UY4VWVSu$m8f1FUDTxLXVPUxlFVGA9/";
}
name-server {
208.67.222.222;
208.67.220.220;
}
name-resolution {
no-resolve-on-input;
}
services {
web-management {
https {
system-generated-certificate;
interface [ ge-0/0/2.0 ge-0/0/3.0 ];
}
session {
idle-timeout 60;
}
}
dhcp {
pool 172.16.64.0/18 {
address-range low 172.16.101.1 high 172.16.101.254;
router {
172.16.64.1;
}
}
pool 172.16.128.0/18 {
address-range low 172.16.151.1 high 172.16.151.254;
router {
172.16.128.1;
}
}
}
}
syslog {
archive size 100k files 3;
user * {
any emergency;
}
file messages {
any critical;
authorization info;
}
file interactive-commands {
interactive-commands error;
}
}
max-configurations-on-flash 5;
max-configuration-rollbacks 5;
license {
autoupdate {
url https://ae1.juniper.net/junos/key_retrieval;
}
}
ntp {
server 172.16.64.254;
}
}
security {
screen {
ids-option untrust-screen {
icmp {
ping-death;
}
ip {
source-route-option;
tear-drop;
}
tcp {
syn-flood {
alarm-threshold 1024;
attack-threshold 200;
source-threshold 1024;
destination-threshold 2048;
timeout 20;
}
land;
}
}
}
nat {
source {
rule-set nsw_srcnat {
from zone [ DEV DNDO ];
to zone Internet;
rule nsw-src-interface {
match {
source-address 0.0.0.0/0;
destination-address 0.0.0.0/0;
}
then {
source-nat {
interface;
}
}
}
}
}
}
policies {
from-zone DNDO to-zone Internet {
policy All_DNDO_Internet {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone Internet to-zone DNDO {
policy All_DNDO_Internet {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone DEV to-zone Internet {
policy All_DEV_Internet {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone Internet to-zone DEV {
policy All_DEV_Internet {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone DNDO to-zone DEV {
policy All_DNDO_DEV {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone DEV to-zone DNDO {
policy All_DNDO_DEV {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone DNDO {
interfaces {
ge-0/0/2.0 {
host-inbound-traffic {
system-services {
ping;
dhcp;
https;
}
}
}
}
}
security-zone DEV {
interfaces {
ge-0/0/3.0 {
host-inbound-traffic {
system-services {
ping;
dhcp;
https;
}
}
}
}
}
security-zone Internet {
interfaces {
ge-0/0/0.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 10.1.10.3/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.16.64.1/18;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
address 172.16.128.1/18;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 10.1.10.1;
}
}
protocols {
stp;
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:12 PM
hmmm zones DEV and DNDO do permit all inter-zone traffic.
From a device connected to switch2 with an IP in the 172.16.128.0/18 subnet can you ping the ge-0/0/2 interface IP 172.16.64.1 ?
With a device connected to switch2 and the laptop connected to switch1, is there a software firewall enabled on the laptop which blocks ICMP from non-local subnets?
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:16 PM
No, I'm not able to ping 172.16.64.1 from a laptop connected to the 172.16.128.2 switch. Also, just noticed that from a 172.16.64.2 switch laptop, I'm not able to ping 172.16.128.1
No software blocking ICMP on either laptops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:21 PM
Basically, I'm copying and pasting from the Packet Tracer since it works in Packet Tracer. Everything looks identical to Packet Tracer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:27 PM
Correction............
From a laptop connected to 172.16.64.2 switch, I can ping 172.16.64.1 and 172.16.128.2
From a laptop connected to 172.16.128.2 switch, I can ping 172.16.64.1 and 172.16.128.2
Sorry about that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:30 PM
So I'm back to my original situation. From the a laptop connected to 172.16.128.2 switch, I'm not able to ping a laptop connected to the 172.16.64.2 switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:35 PM
With you two laptops on separate switches, if you run tcpdump/wireshark on the ping target, do you see the ping request and reply?
If so, then add the following to the SRX:
set security flow traceoptions file ICMP_TEST set security flow traceoptions flag basic-datapath set security flow traceoptions packet-filter ICMP_TEST source-prefix <laptop_A_ip>/32 set security flow traceoptions packet-filter ICMP_TEST destination-prefix <laptop_B_ip>/32
....attempt a ping. Then run show log ICMP_TEST, attach the output to this thread.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 01:42 PM
ok. I need to install Wireshark, and I'm not too familiar with it. I'll try that.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 06:15 AM
Thank you. I turned off windows defender on Windows 10, now I can ping both laptops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 06:21 AM
Glad you got it working. Please mark this thread as solved. :)
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
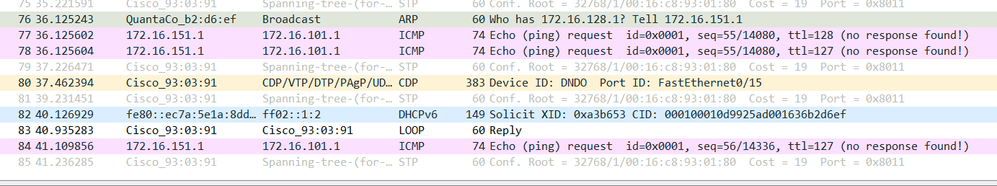
10-15-2018 01:56 PM
I see the ping request coming to the 172.16.101 laptop from 172.16.15 .laptop. This is the laptop that I cannot ping.
Does it matter where I add the commands to the SRX?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 11:51 PM
OK, so your capture shows no reply to the incoming request. This narrows it down to the machine itself and not the network equipment.
I am guessing it is windows laptop that you are using. Have you tried disabling the windows firewall service?
Regarding the SRX commands, enter configuration mode and paste them. However at this stage they are not necessary as it looks to be an issue with the laptop.
cheers,
Seb.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide