- Cisco Community
- Technology and Support
- Networking
- Routing
- Cisco 2921, ISA, Cisco 3750 routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 2921, ISA, Cisco 3750 routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2013 11:36 AM - edited 03-04-2019 08:08 PM
Hello!
I'm designing a new topology to access to the Internet using Cisco2921 NAT and MS ISA Firewall. In brief my topology looks like this.
I'm going to use ISA as a proxy to public some internal services and to provide
internet access for my users. ISA won’t use NAT. It will route traffic. Cisco 2921 will handle NAT, ISP Failover and IPSec VPN to datacenters.
Cisco 3750 will route outbound internal traffic.
My routing for internal users on Cisco 3750 will look like this:
10.10.200.0 255.255.255.0 192.168.200.1 (outbound traffic to datacenter goes directly to Cisco 2921)
0.0.0.0 0.0.0.0 192.168.201.1. (other outbound traffic goes to ISA server then to Cisco2921)
My question is about route from Cisco 2921 to my local network 192.168.0.0/22.
Can I write it like this?
192.168.0.0 255.255.252.0 192.168.200.2 (traffic goes directly to Cisco 3750)
Traffic will flow like this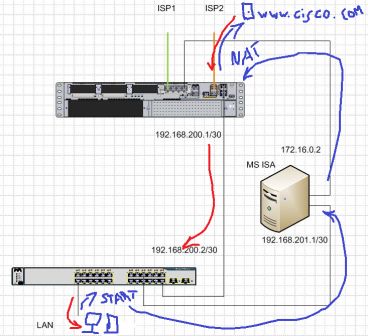
If I use this route, I'll restrict my traffic from datacenter to go through ISA server BUT all responses from the Internet will go directly to 3750 too.
I doubt about security and functionality of such solution. Or it is good enough?
Of course I will public my internal resources to internet that way. It is on Cisco 2921
ip nat inside source static tcp 172.16.0.2 80 (my external IP) 80
I could use PBR to divide my traffic from datacenter and other traffic, but I don't know how to use PBR with IPSec VPN traffic.
Could you advice how to make it better way?
Thank you very much!
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2013 02:47 AM
Hi.
I've decided to make NAT on ISA and second NAT on Cisco2921. So, I can control traffic flow and I don't have to do heavy configuration.
Everything works fine now!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide