- Cisco Community
- Technology and Support
- Networking
- Routing
- Dual WAN failover with limited ports
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 07:09 AM - edited 03-05-2019 08:17 AM
Hello
I have a 1841 router which i am using as firewall/NAT/routing between vlans etc. Currently i have the router on a stick setup. I have two interfaces, one Fa 0/0 is connected to my ISP's VDSL modem and i am using Dialer1 to do the PPP authentication. Dialer1 is my outside facing interface and is therefore firewalled. I am also using NAT overload.
Fa 0/1 is connected to my switchs trunk port and is split into subinterfaces to allow me to route between vlans on the switch.
I currently have a static route pointing to Dialer1 to route all WAN bound traffic.
I wish to add a second WAN link via a 4g/LTE device to use as a failover should my VDSL go down. I ONLY want to use this when my VDSL line goes down. I dont want to load-balance or anything like that.
I was looking at the following device (Netgear LB1111) and was wondering is it possible to create a new VLAN on my switch and appropriate subinterface on my router to connect the LTE device to and then add a second static route with a greater administrative distance to point all WAN bound traffic as the IP address of my LTE device?
If i do this then in theory I can use something like IP SLA to have Fa 0/0 ping an external IP (like 8.8.8.8) every 30 seconds and if there is no ICMP response then have the traffic use the second route to the LTE device? I'm not sure how to configure this yet, im still trying to understand if my theory will work. I'm guessing that should my primary route become available again (i.e. Fa 0/0 starts receiving ICMP responses from 8.8.8.8 again), that the traffic will swing over to my VDSL route again?
My topology would look something like this (i added the new vlan 10 to a separate line for ease of reading, it will all go through the same cable to a trunk port on my switch).
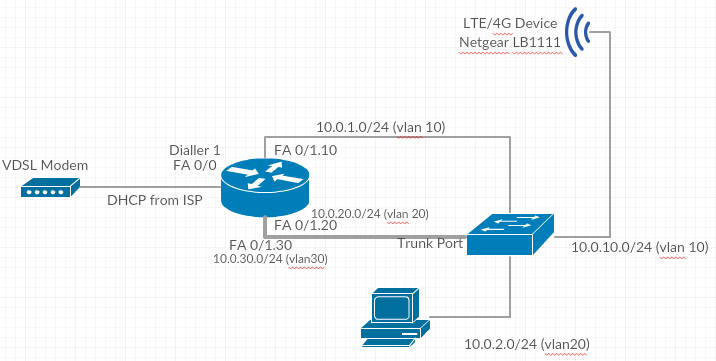
Any advice much appreciated
Matt
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:14 AM
Hello,
From physical point of view, there is no other way than one you already posted unless you add an ethernet module to your router. Personally, I do not like having both LAN and WAN on one trunk interface but it works.
There is something that you need to pay attention. If Your LTE device is going to do NAT, there is no issue; however, if your router is translating for both links, you need to do extra configuration for NAT.
My configuration is kind of pseudo. I did not test it. Check the syntax and replace yours.
For IP SLA, something like this:
You check 8.8.8.8 with your VDSL source interface. Create a track and add a track to the route toward your VDSL. If IP SLA fails, the route will be removed from the routing table.
ip sla 1 [ You can tweak the parameters]
icmp-echo 8.8.8.8 source-interface [VDSL interface]
timeout 5000
frequency 30
threshold 500
ip sla schedule 1 start-time now life forever
track 1 ip sla 1 reachability
ip route 0.0.0.0 0.0.0.0 [your dialer] track 1
ip route 0.0.0.0 0.0.0.0 [ your LTE] 100. 100 is an administrative distance. This default route will be placed into routing tabling when the VDSL route is removed.
Now NAT.
If LTE device is doing NAT, you do not need to change your NAT configuration. If your router is doing NAT for both, you need to tell your router how to translate the packets based on the exit interfaces. Something like this
ip nat inside source route-map MYVDSL [VDSL interface] overload
ip nat inside source route-map MYLTE [LTE interface] overload
route-map MYVDSL permit 10
match ip address 1
match interface [VDSL interface]
!
route-map MYLTE permit 10
match ip address 1
match interface [LTE interface]
access-list 1 permit [Lan IP] 0.0.0.255
Interface Dialer
IP NAT outside
Interface LTE
IP NAT outside
Interface LAN
IP NAT inside
Hope it helps,
Masoud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:14 AM
Hello,
From physical point of view, there is no other way than one you already posted unless you add an ethernet module to your router. Personally, I do not like having both LAN and WAN on one trunk interface but it works.
There is something that you need to pay attention. If Your LTE device is going to do NAT, there is no issue; however, if your router is translating for both links, you need to do extra configuration for NAT.
My configuration is kind of pseudo. I did not test it. Check the syntax and replace yours.
For IP SLA, something like this:
You check 8.8.8.8 with your VDSL source interface. Create a track and add a track to the route toward your VDSL. If IP SLA fails, the route will be removed from the routing table.
ip sla 1 [ You can tweak the parameters]
icmp-echo 8.8.8.8 source-interface [VDSL interface]
timeout 5000
frequency 30
threshold 500
ip sla schedule 1 start-time now life forever
track 1 ip sla 1 reachability
ip route 0.0.0.0 0.0.0.0 [your dialer] track 1
ip route 0.0.0.0 0.0.0.0 [ your LTE] 100. 100 is an administrative distance. This default route will be placed into routing tabling when the VDSL route is removed.
Now NAT.
If LTE device is doing NAT, you do not need to change your NAT configuration. If your router is doing NAT for both, you need to tell your router how to translate the packets based on the exit interfaces. Something like this
ip nat inside source route-map MYVDSL [VDSL interface] overload
ip nat inside source route-map MYLTE [LTE interface] overload
route-map MYVDSL permit 10
match ip address 1
match interface [VDSL interface]
!
route-map MYLTE permit 10
match ip address 1
match interface [LTE interface]
access-list 1 permit [Lan IP] 0.0.0.255
Interface Dialer
IP NAT outside
Interface LTE
IP NAT outside
Interface LAN
IP NAT inside
Hope it helps,
Masoud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:21 AM
Thanks Masoud
Thanks a great help.
Could I ask why you don't like having LAN and WAN on the same trunk? Is it a security issue?
The LTE device does do NAT so thats one less thing for me to do.
Would adding a module such as HWIC-4ESW be an option? I've never configured these so dont know if its possible to make them a routable WAN port?
Thanks again
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:40 AM
One of the reason is security. You have connected your LTE to your LAN switch even though in different VLAN, it still can impose a threat.
If we want to go through threat and security, we need to talk about firewall, port security and so on and so force so I do not want to make a big deal out of it. I have done something similar for some ISPs.
Second, your network is not a complex network, but the new design adds a little complexity and change and troubleshooting become more difficult.
Masoud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:45 AM
Yes,
You can use HWIC-4ESW. It is a 4-switchport card. You put your IP address on the VLAN interface.
Masoud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 08:47 AM
great stuff thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2017 10:07 AM
Happy to help,
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide