- Cisco Community
- Technology and Support
- Networking
- Routing
- Help please, how to configure properly from cisco ASA cluster to external routers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Help please, how to configure properly from cisco ASA cluster to external routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2019 11:23 PM
Hi Everybody;
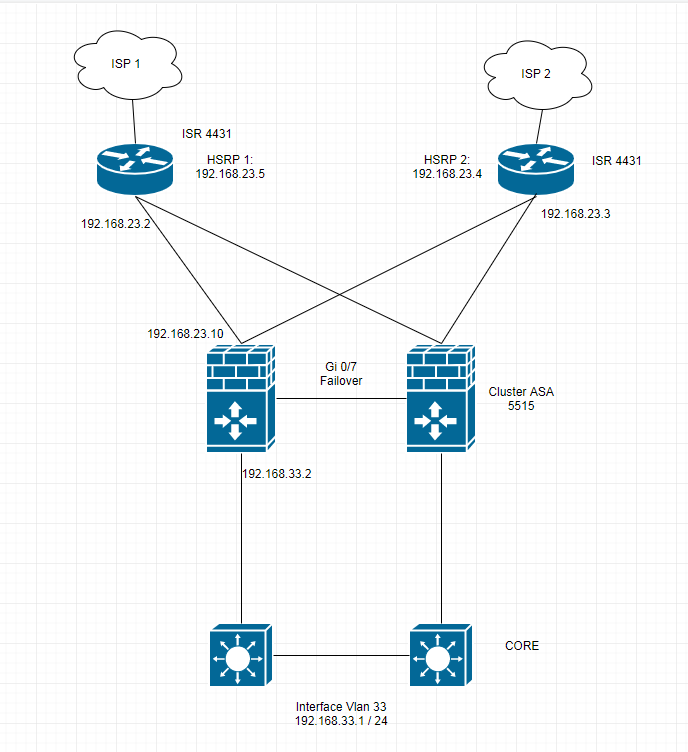
I am thinking in the implementation of a ASA cluster (active-standby), between my aggr core to the external router (which balance the traffic according IP's through route-maps) due to the company is growing fast and we need a extra security. The problem is to balance the traffic through route-maps in Cisco ASA to router 1 or router 2 depending on the source of the IP address, how can I configure the ASA and Router interfaces for full connectivity? I was thinking of configuring the routers with a BVI interface as a portchannel to have 2 interfaces in each router with an IP, but how can I configure the Firewall to achieve the same? With a simple Portchannel? Would a portchannel converge well to a BVI interface? I need help because I have never done anything similar and the environment is very delicate.
See the proposed topology below:
- Labels:
-
ISR 4000 Series
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 04:12 AM
First, don't call it a cluster. Cluster is a different implementation nowadays. You are implementing a Failover-system.
For your setup, I would add two external switches. One switch connects ISP1 on VLAN 101, the other switch connects ISP2 on VLAN 102.
The ASAs are configured with redundant interfaces to both switches and use subinterfaces (with VLANs 101 and 102) for both ISPs. Now the ASA sees two ways to the internet and you can control which traffic to send to which ISP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2019 12:48 AM
Hello,
in addition to Karsten's remarks: do you actually already have the hardware in place ? Looking at your topology, in order to gain maximum leverage, I would use VRRP for LAN redundancy between the core switches, and an active/active stateful failover setup between your ASAs. On the ASAs, you can indeed use PBR (provided you are running 9.4.1 or later) to send traffic to the respective ISP based on the source address
There are certain caveats to an active/active failover setup (such as the requirement for multiple context mode), but in general, having one device just sit there in standby mode, doing nothing, should be avoided if possible...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide