- Cisco Community
- Technology and Support
- Networking
- Routing
- Help with basic config ISR 1111-8PLTEE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Help with basic config ISR 1111-8PLTEE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2020 09:10 PM
Hey all, recently got a Cisco ISR 1111-8PLTE to mess around with for our home connection and we're having some trouble getting DDNS to work correctly. I've scoured the web looking for answers but everything seems so generic. Currently running a Minecraft server, Space Engineers server (On the same VM), and a NextCloud server, on 2 separate VM's hosted on 1 box (though each VM has its own IP) Trying to figure out how to get the Dynamic DNS to work again (it was working flawlessly with consumer grade Netgear router prior to the ISR). My DDNS is through dyndns.org.
Right now, if we try to ping the DDNS address, the router returns the host being pinged from's address, regardless of host. (for example my pc is 192.168.1.23, if I ping the ddns name it returns 192.168.1.23, same for other computers on the LAN) So I feel like we are missing something with NAT from internal to external etc.
Additionally, I seem to be able to reach the Minecraft server externally with our public IP but not DDNS hostname, however cannot reach the space engineers server with the IP or DDNS name, even though the port forwards are setup the same. And nothing I do makes the NextCloud server work externally, I can only reach internally with its LAN IP, I cant do port forwards for it because it by default uses ports 80 and 443 as it's intended to be public facing and you cant generate a cert for it using letsencrypt, unless it stays on those ports.
So with that complicated mess in mind, here is a sanitized (for privacy) version of the config, maybe someone could help us figure out what we're missing? I'm sure its something dumb, but we're both still learning.
Building configuration...
Current configuration : 10248 bytes
!
! Last configuration change at 06:43:43 UTC Mon Jul 27 2020 by **********
!
version 16.8
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
!
hostname ************
!
boot-start-marker
boot system flash bootflash:c1100-universalk9_ias.16.08.03.SPA.bin
boot-end-marker
!
!
logging buffered informational
logging persistent
enable secret *********
!
no aaa new-model
clock timezone UTC -7 0
!
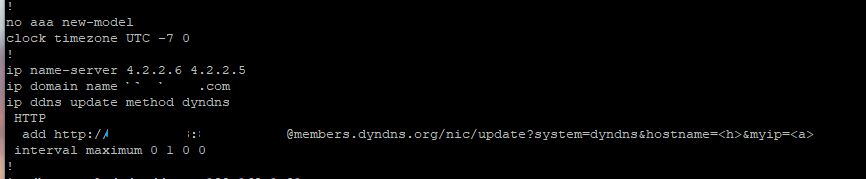
ip name-server 4.2.2.6 4.2.2.5
ip domain name *
ip ddns update method dyndns
HTTP
add http://*******:**********@members.dyndns.org/nic/updatesystem=dyndns&hostname=<h>&myip=<a>
interval maximum 0 1 0 0
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
multilink bundle-name authenticated
!
!
!
crypto pki trustpoint TP-self-signed-1426224979
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1426224979
revocation-check none
rsakeypair TP-self-signed-1426224979
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-1426224979
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31343236 32323439 3739301E 170D3230 30373139 30363138
34385A17 0D333030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 34323632
32343937 39308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 01008BBA BF6A7B5E A2662986 BC00629C FCCF1974 28A1D2BA 15E9D870
E98375FF 55B3C566 C1C2B9DA 87722080 7E902842 37D1FFAA 5F0FBE12 F25719E4
BEFA9539 752809E1 25A9E7CC 6F4F54FB C0FEC9C7 0C0E2F8B 2E602093 722BAC2F
174424ED 7ED92464 21354249 C5123709 EB2B581D 5F79972D AA957925 809E18EA
E0AB6FB8 36625948 51A0DB1A FE56CF00 B2D2F20E 47937775 99F41282 1ECD8EFE
5034B221 90731DB8 7A787AAA BBB1D16D 17A376CF 2FD889AD 4EF03E8B FC0E9B9A
EB890478 42C71FD1 5E9147FB FBFF7ECD 42BF9150 ABA96F88 D0E43ABA F23B28E2
902318B8 81D36B31 E76E0B74 E0B3EA08 7AD07B1C 9EF7752D 89D09771 5DFD47D4
F6C7489D A7EF0203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF
301F0603 551D2304 18301680 14414B2E 324EC090 369034D3 E7A29415 DC8B1593
87301D06 03551D0E 04160414 414B2E32 4EC09036 9034D3E7 A29415DC 8B159387
300D0609 2A864886 F70D0101 05050003 82010100 504C32E1 D778D68F 09D12752
A854816E F68E4B83 DC66D003 72B8AC99 1B47A510 08F81512 5073FF79 FC1BCAA5
76C8284E 98582745 21708615 9B0CF9FC 1FA75991 CF377E11 4F0BAF34 E66A4204
04AB22D4 446F1A00 E9420868 588446B9 9C6B4C19 2E04747F 54F885D2 1F6E72AE
D680CB88 3592A183 4180C51C 3193726A 6C416C96 B9548D34 863AD9BC 0DF0370B
DD75F34C 84381797 0046DE15 3D8A51BA E2658AA3 92001375 81C8E04A 496A47FA
CD6A112A E4B6701C D2AB337C 3B05729B 8F0B56DA AD8E3CE6 958D9CDF CC9A0CE0
C62369E3 CFC71EF8 34D7D31E C232DD4C 06E76306 E6FE6D20 F58A5F90 EF2EFE63
4A097DAD FD6F07AF 75940A66 346A662E 68AE055A
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
license udi pid C1111-8PLTEEA sn ***********
no license smart enable
memory free low-watermark processor 70177
!
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
!
username ***********
!
redundancy
mode none
!
controller Cellular 0/2/0
lte modem link-recovery rssi onset-threshold -110
lte modem link-recovery monitor-timer 20
lte modem link-recovery wait-timer 10
lte modem link-recovery debounce-count 6
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet0/0/0
description Modem Interface WAN
ip ddns update hostname *******.dyndns.org
ip ddns update dyndns
ip address dhcp
ip nat outside
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
duplex full
!
interface GigabitEthernet0/1/1
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/2
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/3
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/4
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/5
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/6
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface GigabitEthernet0/1/7
switchport access vlan 10
switchport trunk native vlan 10
switchport mode access
!
interface Cellular0/2/0
ip address negotiated
shutdown
!
interface Cellular0/2/1
no ip address
shutdown
!
interface Vlan1
no ip address
!
interface Vlan10
description LAN
ip dhcp relay source-interface Vlan10
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip nat inside
!
interface Dialer0
!
ip nat inside source static tcp 192.168.1.22 25566 interface GigabitEthernet0/0/0 25566
ip nat inside source static tcp 192.168.1.22 27016 interface GigabitEthernet0/0/0 27016
ip nat inside source static tcp 192.168.1.22 25565 interface GigabitEthernet0/0/0 25565
ip nat inside source list NAT interface GigabitEthernet0/0/0 overload
ip forward-protocol nd
ip http server
ip http access-class ipv4 InternalSSH
ip http authentication local
ip http secure-server
ip dns server
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0/0 dhcp
ip ssh version 2
!
!
ip access-list standard InternalSSH
permit 192.168.1.0 0.0.0.255
ip access-list standard NAT
permit 192.168.1.0 0.0.0.255
!
!
!
!
!
control-plane
!
!
line con 0
logging synchronous
login local
transport input none
stopbits 1
line vty 0 4
access-class InternalSSH in
login local
transport input ssh
!
wsma agent exec
!
wsma agent config
!
wsma agent filesys
!
wsma agent notify
!
!
end
- Labels:
-
ISR 1000 Series
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 01:17 AM
Hello,
it looks like you are missing the '?'in your under your http:
http://*******:**********@members.dyndns.org/nic/update?system=dyndns&hostname=<h>&myip=<a>
In order to get that in there, press Ctrl+V first, then enter the '?'...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 09:12 AM - edited 08-08-2020 09:22 AM
Thanks Georg,
I feel silly now, that was originally in the config, but I have re-done it so many times that I must have missed it the 3rd or 4th time.
I entered that string in. In any case, I put it back and its now correct, but still not working :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 10:07 AM
Hello,
I now remember that DDNS possibly does not work at all on the ISR1111 running XE software. Can you run 'debug ip ddns update' ?
Have a look at the discussion below (never mind the warning you might get, it is a link to a discussion on CCO):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 10:20 AM
Whenever I run that command, I get "Dynamic DNS debugging is on" but it will never output any results. Even though all logging is turned on and available. Thats a huge bummer if it truly is not functional on the ISR 1100's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 11:28 AM
Hello,
no debug output at all is a bad sign. You could try and upgrade to the latest XE version Gibraltar-16.12.4 MD, it might be supported on this one. I have no idea why they would drop DDNS support on that platform...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2020 08:19 AM
The only issue with updating to Gibraltar is that it would require me to enable Smart Licensing, and as this is for home use, I don't think I have license to use, and cant really afford enterprise pricing to use the router. Or do you know if Cisco has a smart license that's aimed at home users of their equipment? Otherwise I am stuck on 16.9.0 or below for right-to-use licenses. Thank you for all your help thus far though, I really appreciate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2020 09:18 AM
Hello,
actually, I wouldn't bother with the Gibraltar update. I checked the release notes, and there is no mention of anything DDNS related. So far, the discussion link I sent you earlier has been the only source I could find that addresses this issue. I will try to find something more 'official' from Cisco...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 12:04 PM
Thanks! Look forward to seeing if they have an answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2020 07:28 PM
Hi Georg,
Just checking in, its been a while, did you hear anything from Cisco officially about the DDNS?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2020 12:05 AM - edited 09-04-2020 12:08 AM
Hello,
the only thing I could find is the below from the Cisco ISR 1K FAQ:
Q: Does the 1000 Series ISRs support Dynamic DNS?
A: Yes, Cisco IOS XE does support Dynamic DNS.
So according to this document (linked below) it is supported. Which doesn't help at all, since it is not working on your router.
https://www.router-switch.com/media/upload/faq-pdf/cisco-1000-series-integrated-routers-faq.pdf
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide