- Cisco Community
- Technology and Support
- Networking
- Routing
- Home Lab Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 11:33 AM
I'm currently studying for my CCNA and have a lab that I like to build scenarios on and tinker with. It is connected to my Home Network (Comcast). Everything works great until i try to remote/ping computers connected to the 3750v2 switch from computers on the home network (Comcast). Clients on 3750V2 can ping comcast computers without problems but not the opposite direction (comcast to cisco lab). Is this because Comcast Modems do not have a route pointing back to my Cisco router? For instance i have the Arch Linux box setup as a DHCP server for the lab but it's connected to the comcast network, I can see requests for IP's coming from the Cisco Network and getting to the DHCP server but they don't seem to be getting back to the clients plugged into the Cisco switch and I can't ping the vlan interface either from comcast computer. Any Ideas? Is this because there is no access list set to allow return dhcp offers? My gut is saying it's because there's no route in Comcast modem directing packets back to the Cisco router, but then again if that's true how can I achieve internet access but then again the router has an IP Address that is in the same subnet as the Comcast Router. I'm lost and have googled for hours on this subject with no luck.
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Other Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 01:06 PM
Comcast router not aware of where to send this packet coming from "10.0.1.1 255.255.255.0"
So you need route entry from Comcast router point to cisco Router.
if you looking 10.0.1.1 255.255.255.0 to get internet, then you NATing for these subnet.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 12:23 PM - edited 07-07-2019 12:24 PM
Here are the config.
I have very basic configs on these.
Router Config
Router-1841#show run
Building configuration...
Current configuration : 3100 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname Router-1841
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
clock timezone cst -6
dot11 syslog
ip cef
!
!
!
!
ip domain name CISCO-LAB
multilink bundle-name authenticated
!
!
!
!
!
archive
log config
hidekeys
!
!
ip ssh version 2
!
!
!
interface Loopback1
ip address 10.10.10.10 255.255.255.0
!
interface FastEthernet0/0
ip address 10.0.0.41 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 10.0.1.1 255.255.255.0
ip helper-address 10.0.0.200
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface Serial0/0/0
no ip address
shutdown
service-module t1 clock source internal
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 10.0.0.1
!
!
no ip http server
no ip http secure-server
ip nat inside source list 1 interface FastEthernet0/0 overload
!
access-list 1 permit 10.0.1.0 0.0.0.255
!
!
control-plane
!
line con 0
exec-timeout 0 0
logging synchronous
login local
line aux 0
line vty 0 4
login local
transport input ssh
!
scheduler allocate 20000 1000
end
Switch Config
Switch-1-3750v2>en
Password:
Switch-1-3750v2#show run
Building configuration...
Current configuration : 7208 bytes
!
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname Switch-1-3750v2
!
boot-start-marker
boot-end-marker
!
!
enable secret
!
username
no aaa new-model
clock timezone cst -6 0
switch 1 provision ws-c3750v2-48ps
system mtu routing 1500
ip domain-name lab.com
!
!
!
!
!
crypto pki trustpoint TP-self-signed-1615185664
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1615185664
revocation-check none
rsakeypair TP-self-signed-1615185664
!
!
crypto pki certificate chain TP-self-signed-1615185664
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31363135 31383536 3634301E 170D3933 30333031 30303032
35365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 36313531
38353636 3430819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100DCCB A565EC4F F28092DB 4C010691 149AA2B9 85F930A9 EDC2A358 A8B5663A
044ED36C 1948CCC3 D4CBBEFF B93C7F6A EB06B363 FC6BD718 0FAD692F 873D0FCE
455498CB 04ACECCF FF6E752E 606E1411 F3CA664A EBE3501B CD72A007 BEFA3D29
F8B62629 08D42134 577D95AE B910F327 1A67DE60 C3D6E4DC 74506533 F9AC54D1
0AE10203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 14E59706 D515D072 ABD91F36 5119AB84 4DA88E01 60301D06
03551D0E 04160414 E59706D5 15D072AB D91F3651 19AB844D A88E0160 300D0609
2A864886 F70D0101 05050003 818100BE 3893EAB5 884647C3 9CE00624 2215AA88
726192F4 19856D5C DE2CC3B1 B851C77D 851D6588 3654D245 2597DE91 ADD54D90
E066F571 AE5C3149 2CCCC35E 519B52E5 0EF13CFC 873AF868 797E9671 4CDE9C41
0AA10A3E 55BC7DE5 980515D0 11E06599 C9A2B3D6 6A5E59A3 48809E62 77BCA535
C5D3E8EB 6130AB1F DEEF6EC8 275AB1
quit
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet1/0/1
switchport mode access
!
interface FastEthernet1/0/2
switchport mode access
!
interface FastEthernet1/0/3
switchport mode access
!
interface FastEthernet1/0/4
switchport mode access
!
interface FastEthernet1/0/5
switchport mode access
!
interface FastEthernet1/0/6
switchport mode access
!
interface FastEthernet1/0/7
switchport mode access
!
interface FastEthernet1/0/8
switchport mode access
!
interface FastEthernet1/0/9
switchport mode access
!
interface FastEthernet1/0/10
switchport mode access
!
interface FastEthernet1/0/11
switchport mode access
!
interface FastEthernet1/0/12
switchport mode access
!
interface FastEthernet1/0/13
switchport mode access
!
interface FastEthernet1/0/14
switchport mode access
!
interface FastEthernet1/0/15
switchport mode access
!
interface FastEthernet1/0/16
switchport mode access
!
interface FastEthernet1/0/17
switchport mode access
!
interface FastEthernet1/0/18
switchport mode access
!
interface FastEthernet1/0/19
switchport mode access
!
interface FastEthernet1/0/20
switchport mode access
!
interface FastEthernet1/0/21
switchport mode access
!
interface FastEthernet1/0/22
switchport mode access
!
interface FastEthernet1/0/23
switchport mode access
!
interface FastEthernet1/0/24
switchport mode access
!
interface FastEthernet1/0/25
switchport mode access
!
interface FastEthernet1/0/26
switchport mode access
!
interface FastEthernet1/0/27
switchport mode access
!
interface FastEthernet1/0/28
switchport mode access
!
interface FastEthernet1/0/29
switchport mode access
!
interface FastEthernet1/0/30
switchport mode access
!
interface FastEthernet1/0/31
switchport mode access
!
interface FastEthernet1/0/32
switchport mode access
!
interface FastEthernet1/0/33
switchport mode access
!
interface FastEthernet1/0/34
switchport mode access
!
interface FastEthernet1/0/35
switchport mode access
!
interface FastEthernet1/0/36
switchport mode access
!
interface FastEthernet1/0/37
switchport mode access
!
interface FastEthernet1/0/38
switchport mode access
!
interface FastEthernet1/0/39
switchport mode access
!
interface FastEthernet1/0/40
switchport mode access
!
interface FastEthernet1/0/41
switchport mode access
!
interface FastEthernet1/0/42
switchport mode access
!
interface FastEthernet1/0/43
switchport mode access
!
interface FastEthernet1/0/44
switchport mode access
!
interface FastEthernet1/0/45
switchport mode access
!
interface FastEthernet1/0/46
switchport mode access
!
interface FastEthernet1/0/47
switchport mode access
!
interface FastEthernet1/0/48
switchport mode access
!
interface GigabitEthernet1/0/1
switchport mode access
!
interface GigabitEthernet1/0/2
switchport mode access
!
interface GigabitEthernet1/0/3
switchport mode access
!
interface GigabitEthernet1/0/4
switchport mode access
!
interface Vlan1
ip address 10.0.1.2 255.255.255.0
!
ip default-gateway 10.0.1.1
no ip http server
no ip http secure-server
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
login local
line vty 0 4
exec-timeout 0 0
logging synchronous
login local
transport input ssh
line vty 5 15
exec-timeout 0 0
logging synchronous
login local
transport input ssh
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 12:30 PM
Hello,
we need to know how your devices are connected. Post a brief schematic drawing of your topology...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
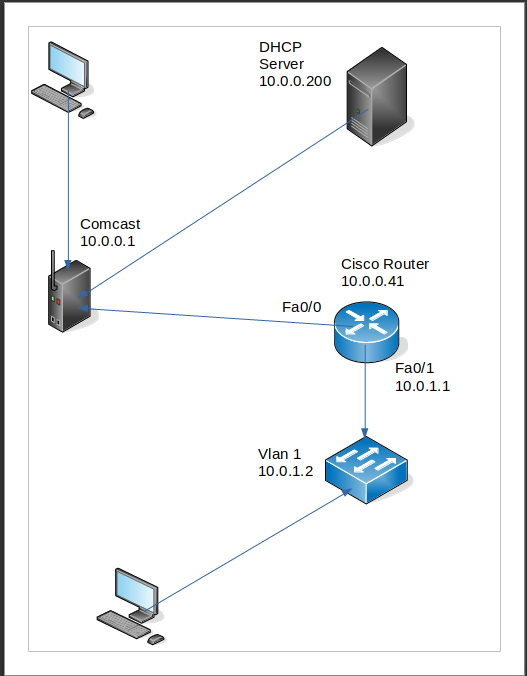
07-07-2019 01:00 PM
Attached is a Topology I just made with Libre Office Draw
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 01:02 PM
I really believe that the comcast modem just doesn't know how to get to the 10.0.1.2 subnet without a static route, I may be wrong but that's why I'm asking the pros! lol
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 01:06 PM
Comcast router not aware of where to send this packet coming from "10.0.1.1 255.255.255.0"
So you need route entry from Comcast router point to cisco Router.
if you looking 10.0.1.1 255.255.255.0 to get internet, then you NATing for these subnet.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2019 01:20 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide