- Cisco Community
- Technology and Support
- Networking
- Routing
- how can i deny access in one direction, but not the other? (pkt)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
how can i deny access in one direction, but not the other? (pkt)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 02:33 AM - edited 12-02-2023 05:43 PM
Hi,
I'm sorry to bother you all, but I'm having some issues with the network I'm building in CISCO Packet Tracer.
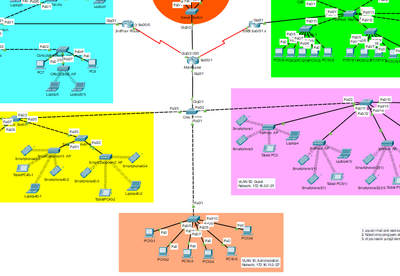
In my network, I need to deny access from one direction but not the other. For instance, in my network, I need the VLAN 20 (172.16.8.0 /24), VLAN 30 (172.16.9.0 /24), VLAN 40 (172.16.10.0 /24) and VLAN 50 (172.16.0.0 /21) to be blocked from accessing the VLAN 10 (172.16.11.0 /27), but not vice versa; 172.16.11.0 /27 must still be able to ping those networks, but those networks must not be able to ping 172.16.11.0 /27.
I initially tried doing this using ACLs on the MainRouter, but that did not work at all as packets were able to ping in both directions even when I added ACL to a particular interface.
Does anyone know what my issue might be, and what should I do in order to fix it? Should i use other network security protocol? Any help would be much appreciated.
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 03:17 AM
For icmp
Allow icmp reply and deny all other traffic
Apply this acl with IN direction.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 03:49 AM - edited 12-02-2023 04:34 AM
If you want to deny access only in one direction...you should configure Extended acl. Standard acl blocks two-way communication and Extended acl blocks one way communication...
Here is the sample configuration....
ip access-list 101 deny icmp any 172.16.11.0 0.0.0.31 eq echo
ip access-list 101 permit ip any any
ip access-group 101 in
Best regards
******* If This Helps, Please Rate *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 05:19 AM
in what interface should i put the ACL? is it in interface g0/1.10? the one who handles the VLAN 10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 05:49 AM
Apply to interface that direct connect to subnet you want to protect.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:00 AM
I tried that but it is still pinging in both direction.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:02 AM
Share config I will check
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:26 AM - edited 12-02-2023 06:27 AM
here:
!
!
!
!
!
ip dhcp pool Administration
network 172.16.11.0 255.255.255.224
default-router 172.16.11.1
dns-server 172.16.12.3
ip dhcp pool 4thFloor
network 172.16.10.0 255.255.255.0
default-router 172.16.10.1
dns-server 172.16.12.3
ip dhcp pool Guest
network 172.16.0.0 255.255.248.0
default-router 172.16.0.1
dns-server 172.16.12.3
!
!
!
no ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2911/K9 sn FTX1524R5DB-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/1
no ip address
ip access-group FILTER-ADMINISTRATION-VLAN-ACCESS in
duplex auto
speed auto
!
interface GigabitEthernet0/1.10
encapsulation dot1Q 10
ip address 172.16.11.1 255.255.255.224
ip helper-address 172.16.11.1
ip access-group FILTER-ADMINISTRATION-VLAN-ACCESS in
!
interface GigabitEthernet0/1.40
encapsulation dot1Q 40
ip address 172.16.10.1 255.255.255.0
ip helper-address 172.16.10.1
!
interface GigabitEthernet0/1.50
encapsulation dot1Q 50
ip address 172.16.0.1 255.255.248.0
ip helper-address 172.16.0.1
!
interface GigabitEthernet0/2
ip address 172.16.12.1 255.255.255.0
ip access-group DENY-OTHER-VLANS-TO-ACCESS-THE-FILE-SERVER out
duplex auto
speed auto
!
interface Serial0/0/0
description Link to 2ndFloor_Router
ip address 172.16.11.34 255.255.255.252
!
interface Serial0/0/1
description Link to 3rdFloor_Router
ip address 172.16.11.38 255.255.255.252
!
interface Vlan1
no ip address
shutdown
!
interface Vlan50
mac-address 0060.70e5.0a01
no ip address
!
router rip
version 2
network 172.16.0.0
!
ip classless
!
ip flow-export version 9
!
!
ip access-list extended ONLY-ALLOW-VLAN-20-TO-ACCESS-THE-FILE-SERVER
permit ip 172.16.8.0 0.0.0.255 host 172.16.12.2
ip access-list extended DENY-OTHER-VLANS-TO-ACCESS-THE-FILE-SERVER
deny ip 172.16.0.0 0.0.7.255 host 172.16.12.2
deny ip 172.16.9.0 0.0.0.255 host 172.16.12.2
deny ip 172.16.10.0 0.0.0.255 host 172.16.12.2
deny ip 172.16.11.0 0.0.0.31 host 172.16.12.2
permit ip any any
ip access-list extended FILTER-ADMINISTRATION-VLAN-ACCESS
deny ip 172.16.0.0 0.0.7.255 172.16.11.0 0.0.0.31
deny ip 172.16.8.0 0.0.0.255 172.16.11.0 0.0.0.31
deny ip 172.16.9.0 0.0.0.255 172.16.11.0 0.0.0.31
deny ip 172.16.10.0 0.0.0.255 172.16.11.0 0.0.0.31
permit ip 172.16.11.0 0.0.0.31 172.16.0.0 0.0.7.255
permit ip 172.16.11.0 0.0.0.31 172.16.8.0 0.0.0.255
permit ip 172.16.11.0 0.0.0.31 172.16.9.0 0.0.0.255
permit ip 172.16.11.0 0.0.0.31 172.16.10.0 0.0.0.255
deny ip any any
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:32 AM
I think I get issue here
Change direction to be
OUT not IN
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:34 AM - edited 12-02-2023 06:39 AM
to the int g0/1.10, right? it fails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:57 AM
the interface where traffic from source entering to the router...
Best regards
******* If This Helps, Please Rate *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:22 AM - edited 12-02-2023 06:28 AM
Extended ACL's should be configured on closer to source...and apply on interface g0/1.10 in bound direction...
if sources(vlan 20,30,40,& 50) are available/connected on two different routers(2nd floor and 3rd floor)....you should configure two extended acl's... one... acl on each router....
Please post the configuration...it might be helpful....
Best regards
******* If This Helps, Please Rate *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 06:31 AM
here's the configuration for the main router:
ip dhcp pool Administration
network 172.16.11.0 255.255.255.224
default-router 172.16.11.1
dns-server 172.16.12.3
ip dhcp pool 4thFloor
network 172.16.10.0 255.255.255.0
default-router 172.16.10.1
dns-server 172.16.12.3
ip dhcp pool Guest
network 172.16.0.0 255.255.248.0
default-router 172.16.0.1
dns-server 172.16.12.3
!
!
!
no ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2911/K9 sn FTX1524R5DB-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/1
no ip address
ip access-group FILTER-ADMINISTRATION-VLAN-ACCESS in
duplex auto
speed auto
!
interface GigabitEthernet0/1.10
encapsulation dot1Q 10
ip address 172.16.11.1 255.255.255.224
ip helper-address 172.16.11.1
ip access-group FILTER-ADMINISTRATION-VLAN-ACCESS in
!
interface GigabitEthernet0/1.40
encapsulation dot1Q 40
ip address 172.16.10.1 255.255.255.0
ip helper-address 172.16.10.1
!
interface GigabitEthernet0/1.50
encapsulation dot1Q 50
ip address 172.16.0.1 255.255.248.0
ip helper-address 172.16.0.1
!
interface GigabitEthernet0/2
ip address 172.16.12.1 255.255.255.0
ip access-group DENY-OTHER-VLANS-TO-ACCESS-THE-FILE-SERVER out
duplex auto
speed auto
!
interface Serial0/0/0
description Link to 2ndFloor_Router
ip address 172.16.11.34 255.255.255.252
!
interface Serial0/0/1
description Link to 3rdFloor_Router
ip address 172.16.11.38 255.255.255.252
!
interface Vlan1
no ip address
shutdown
!
interface Vlan50
mac-address 0060.70e5.0a01
no ip address
!
router rip
version 2
network 172.16.0.0
!
ip classless
!
ip flow-export version 9
!
!
ip access-list extended ONLY-ALLOW-VLAN-20-TO-ACCESS-THE-FILE-SERVER
permit ip 172.16.8.0 0.0.0.255 host 172.16.12.2
ip access-list extended DENY-OTHER-VLANS-TO-ACCESS-THE-FILE-SERVER
deny ip 172.16.0.0 0.0.7.255 host 172.16.12.2
deny ip 172.16.9.0 0.0.0.255 host 172.16.12.2
deny ip 172.16.10.0 0.0.0.255 host 172.16.12.2
deny ip 172.16.11.0 0.0.0.31 host 172.16.12.2
permit ip any any
ip access-list extended FILTER-ADMINISTRATION-VLAN-ACCESS
deny ip 172.16.0.0 0.0.7.255 172.16.11.0 0.0.0.31
deny ip 172.16.8.0 0.0.0.255 172.16.11.0 0.0.0.31
deny ip 172.16.9.0 0.0.0.255 172.16.11.0 0.0.0.31
deny ip 172.16.10.0 0.0.0.255 172.16.11.0 0.0.0.31
permit ip 172.16.11.0 0.0.0.31 172.16.0.0 0.0.7.255
permit ip 172.16.11.0 0.0.0.31 172.16.8.0 0.0.0.255
permit ip 172.16.11.0 0.0.0.31 172.16.9.0 0.0.0.255
permit ip 172.16.11.0 0.0.0.31 172.16.10.0 0.0.0.255
deny ip any any
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 07:55 AM - edited 12-02-2023 08:10 AM
Remove all acl's if you configured any other routers...for example..
Router(config)# no access-list 101
Router(config-if)# no ip access-group 101 in|out
implement following acl in 2nd Floor router....
ip access-list 101 deny icmp 172.16.8.0 0.0.0.255 172.16.9.0 0.0.0.31 eq icmp
ip access-list 101 permit ip any any
Interface Gig0/1
ip access-group 101 in
Note: There is no difference applying ACL on physical or sub interface as ACL is layer 3 and 4, not lower layer, hence doesn't make any diffrence applying it on the physical or sub interface.
after that try to ping from vlan 20 pc to vlan 10 pc you shouldn't see the communication...
but when you try to ping from vlan 10 pc to vlan 20 you should see successful communiation....
if you achive this for one vlan same way we can implement other vlans...
Best regards
******* If This Helps, Please Rate *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 08:39 AM
the ping were still successful in both direction
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide