- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Inside-Inside NAT On ISR4451?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Inside-Inside NAT On ISR4451?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 07:03 PM
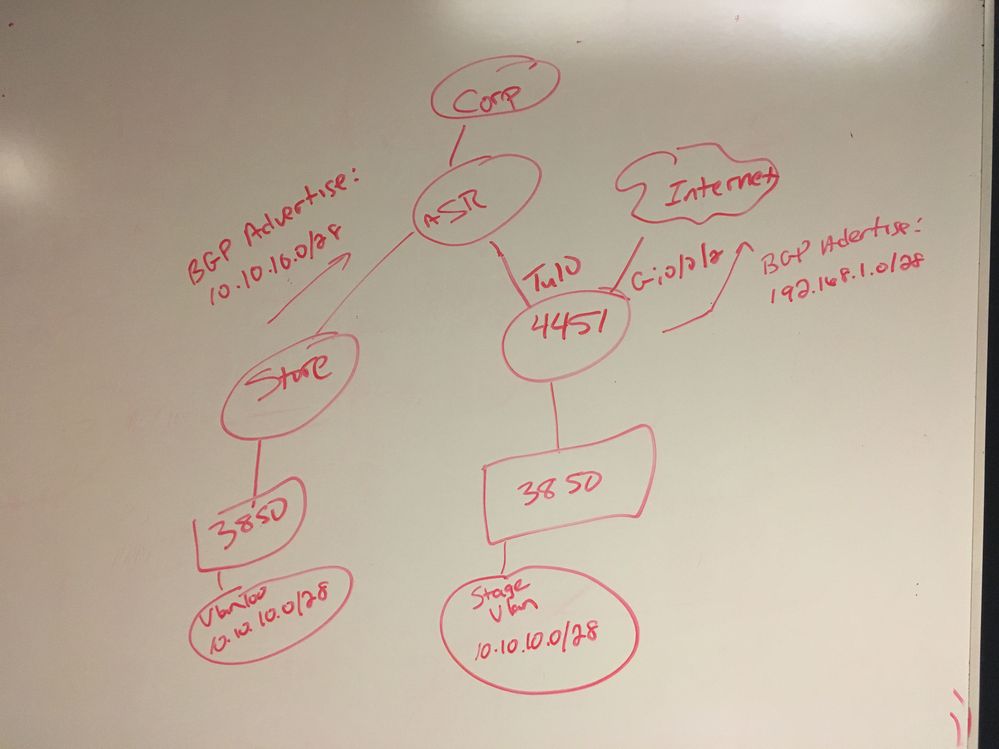
I am trying to build some server infrastructure at my staging location which will be shipped to another store location. We want to build the clusters with the store IP so that it build correctly and we do not have to re-IP the server cluster.
I built a vlan that uses the same store IP at my staging facility. I need to NAT these store IPs to an IP block from my staging facility so that it can route to my corpnet and then come back to my staging facility rather than the store. Is there a way to do NAT from inside to inside?
Store IP block: 10.10.10.0/28
Staging IP block: 192.168.1.0/28
I need to NAT from 10.10.10.0 to 192.168.1.0. I need 1:1 NAT. It needs to NAT over my VPN tunnel which is an inside zone. I do not want to route over the internet since I am trying to hit my corpnet resources via the tunnel.
Any ideas? Thanks
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 07:20 PM
Can you share a quick drawing on how everything is connected together with this isr?
You should probably be able to do Nat but before sharing some configs i would prefer checking how the connection is done between your staging site and corporate office
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 07:46 PM
As you can see, I am already advertising the 10.10.10.0/28 from my store. I want to nat the 10.10.10.0/28 IP space at my staging facility to a local staging subnet 192.168.1.0/28 so it can route to my corpnet resources and return back to my staging facility where it will have the static NAT mapping and route back to the 10.10.10.0/28 IP at my staging facility after it returns from corpnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 09:01 PM - edited 08-09-2018 09:02 PM
Your staging 10.10.10.0/28 access the Corp network through a tunnel interface going to ASR. But you've written bgp advertise your local 192.168.1.0/28 over internet?
Is this subnet 192.168.1.0/28 existing on your ISR? This is what's not clear.
If not existing, you can do nat inside isr interface facing your switch and nat outside on your tunnel interface.
You can simply configure ip nat enable on both interfaces and then user the command:
Ip nat source static network 10.10.10.0 192.168.1.0 28
Ip nat source static network 192.168.1.0 10.10.10.0 28
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 08:47 AM
Hi Francesco,
Actually. BGP is advertising the 192.168.1.0 to the ASR not the internet. Sorry for the misrepresentation in the drawing. I tried putting ip nat outside on the Tu10 interface but it breaks the rest of the network at my staging site when I do this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2018 08:44 PM
Can you use another subnet?
When you say it breaks everything else, can you share the config you've tried?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 03:08 AM - edited 08-10-2018 03:10 AM
Hello
@jmperlewitz wrote:
I need to NAT these store IPs to an IP block from my staging facility so that it can route to my corpnet and then come back to my staging facility rather than the store. Is there a way to do NAT from inside to inside?
Store IP block: 10.10.10.0/28Staging IP block: 192.168.1.0/28
I need to NAT from 10.10.10.0 to 192.168.1.0. I need 1:1 NAT. It needs to NAT over my VPN tunnel which is an inside zone. I do not want to route over the internet since I am trying to hit my corpnet resources via the tunnel.
1:1 nat is indeed applicable however you dont mention what subnet is being used between these to sites so as to be able to nat between them -
Example for 1:1 nat
Store IP block: 10.10.10.0/28
ip access-list 10 permit 10.10.10.0 0.0.0.7
ip nat pool Store-IP x.x.x.1 x.x.x.6 prefix-length 28 type match-host
ip nat inside source list 10 pool Store-IP
Staging IP block: 192.168.1.0/28
ip access-list 10 permit 192.168.1.0 0.0.0.7
ip nat pool Staging-IP x.x.x.1 x.x.x.6 prefix-length 28 type match-host
ip nat inside source list 10 pool Staging-IP
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 08:52 AM
Hi Paul:
1:1 nat is indeed applicable however you dont mention what subnet is being used between these to sites so as to be able to nat between them
I'm not sure what you mean here. Per my drawing, I have a 10.10.10.0/28 subnet being advertised from my store. I need to use this same subnet at my staging site so I can stage my server cluster using the store IPs.
I want to nat from 10.10.10.0/28 to 192.168.1.0/28 (which is IP space at my staging facility). I need to NAT to my Staging facility IP space so that I can route correctly from the staging facility to my Corpnet.
It routes over Tu10, which is configured for NAT Inside
I hope this is more clear. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 12:01 PM - edited 08-10-2018 12:09 PM
Hello
Unfortunately no it isn't clear , well for me at least.
Your nat inside local addressing would be the two /28 subnets of storage and staging blocks correct?
Your OP requests 1:1 nat - Meaning any nat outside global address is mapped to its relevant the inside local address.
So to nat between these two areas what is connecting them? - You need some physical outside path / interface to nat towards from either area however what I can see is both these subnets reside on the single ASR rtr locally
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 12:18 PM
I want my 10.x inside local to translate to the 192.x outside global and route over my VPN to the ASR. When the packet comes into the ASR, it needs to have a source IP of 192.x rather than 10.x or else it will route back to the Store instead of the staging facility.
The problem I am having is the only outside NAT interface I have setup is the gi0/0/2 which goes to the internet. I do not want to go to the internet. I need to go to VPN but I cant make my VPN interface NAT Outside. Hence why I cant really get traditional NAT to work.
I am trying to think of a clever solution to get it to work but it looks like that will not be possible.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide