- Cisco Community
- Technology and Support
- Networking
- Routing
- IOS Remote Access VPN (AnyConnect) Troubleshooting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 06:29 AM
Experts,
I am looking for some assistance with configuring/troubleshooting IOS to do AnyConnect remote access, allowing remote users to access local resources, as well as traverse other L2L tunnels on the 1921.
What is not working:
I am not able to get remote users connected to the hub 1921 via AnyConnect to be able to access internal resources, or resources over a L2L tunnel to an ASA5520.
What is working:
- Internal hosts on the 1921 can access internet hosts, and hosts on the other end of the L2L tunnel with an ASA5520. From what I can tell, the L2L tunnel with the ASA is fine.
- Remote access hosts can ping/access the 1921 (loopback interface).
What I believe is correct:
- I believe crypto-map ACLs and NAT statements are correct on both sides. (Also, internal hosts on the 1921 can access resources over the tunnel)
Possible issues:
- Zone based firewall not configured correctly?
- Do remote hosts (172.20.52.0/29) need a zone pair from outside to inside?
- How would you mark the other policy based tunnels as inside if so?
- What debug command would show me if firewall rules are blocking 172.20.52.0/29 hosts from going to 172.20.48.0/24 or 192.168.0.0/24 hosts?
- Do remote hosts (172.20.52.0/29) need a zone pair from outside to inside?
- Webvpn context missing something?
- I've tried adding an ACL here like some examples have shown, it didn't work.
- Virtual Interface config?
- I'm not very familiar with the 'interface virtual-template' config the cisco guides dictated
- I added it as an inside zone member trying to troubleshoot firewall issues.
I can't find anymore configuration examples to follow for this.
This was the guide I used to get this partially setup: https://www.cisco.com/c/en/us/support/docs/security/anyconnect-secure-mobility-client/200533-AnyConnect-Configure-Basic-SSLVPN-for-I.html#anc13
Lastly, this router is a hub for other ASAs to dynamically connect to. Since the ASA5500 series doesn't do VTIs, I had to create a policy based dynamic map on this 1921 to avoid creating a bunch of individual L2Ls. It works, I've already tested that a 5505 could connect and traffic flowed. I kept the ASA5520 being used for this testing static for more clarity.
Can anyone offer more guidance?
Our topology:
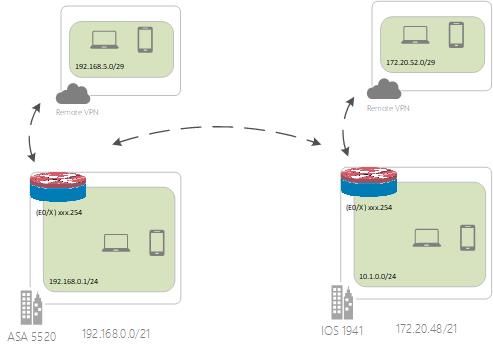 Topology
Topology
Config:
Cisco 2941 HUB Router
Current configuration : 21224 bytes
!
! Last configuration change at 10:03:23 EDT Fri May 10 2019 by [REDACTED]
!
version 15.7
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname [REDACTED]
!
boot-start-marker
boot system flash:c1900-universalk9-mz.SPA.157-3.M3.bin
boot system flash:c1900-universalk9-mz.SPA.154-3.M2.bin
boot-end-marker
!
!
logging buffered 4096
enable secret 5 [REDACTED]
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication login local_access local
aaa authentication login AAA_ANYCONNECT local
aaa authorization exec default local
!
!
!
!
!
!
aaa session-id common
clock timezone EST -5 0
clock summer-time EDT recurring
!
!
!
!
!
!
!
!
!
!
ip dhcp pool DHCP-POOL_INTERNAL
network 172.20.48.0 255.255.255.0
domain-name [REDACTED]
default-router 172.20.48.254
dns-server 192.168.0.1 172.20.0.6 8.8.8.8
!
!
!
no ip bootp server
ip domain lookup source-interface GigabitEthernet0/0
ip domain name [REDACTED]
ip name-server 192.168.0.1
ip name-server 192.168.0.2
ip name-server 172.20.0.6
ip cef
no ipv6 cef
!
!
flow record nbar-appmon
match ipv4 source address
match ipv4 destination address
match application name
collect interface output
collect counter bytes
collect counter packets
collect timestamp absolute first
collect timestamp absolute last
!
!
flow monitor application-mon
cache timeout active 60
record nbar-appmon
!
parameter-map type inspect global
max-incomplete low 18000
max-incomplete high 20000
nbar-classify
multilink bundle-name authenticated
!
cts logging verbose
!
crypto pki trustpoint selfsigned
enrollment selfsigned
revocation-check crl
!
crypto pki trustpoint test_trustpoint_config_created_for_sdm
subject-name e=sdmtest@sdmtest.com
revocation-check crl
!
crypto pki trustpoint [REDACTED]
enrollment terminal
usage ike
usage ssl-server
usage ssl-client
fqdn [REDACTED]
subject-name [REDACTED]
revocation-check crl
!
!
crypto pki certificate chain selfsigned
crypto pki certificate chain test_trustpoint_config_created_for_sdm
crypto pki certificate chain [REDACTED]
certificate [REDACTED]
quit
certificate ca [REDACTED]
quit
license udi pid CISCO1921/K9 sn [REDACTED]
!
!
!
redundancy
!
crypto ikev2 proposal IKEV2-PROPOSAL_1
encryption aes-cbc-256
integrity sha512
group 24
crypto ikev2 proposal IKEV2-PROPOSAL_2
encryption aes-cbc-256
integrity sha256
group 24
!
crypto ikev2 policy IKEV2-POLICY
proposal IKEV2-PROPOSAL_1
proposal IKEV2-PROPOSAL_2
!
!
crypto ikev2 profile IKEV2-PROFILE_S2S_ASA5520
match identity remote address [REDACTED]
identity local key-id ASA5520
authentication remote pre-share key [REDACTED]
authentication local pre-share key [REDACTED]
!
crypto ikev2 profile IKEV2-PROFILE_S2S_DYNAMIC
description ** Allows dynamic tunnels **
match identity remote any
authentication remote pre-share key [REDACTED]
authentication local pre-share key [REDACTED]
!
no crypto ikev2 http-url cert
!
!
!
class-map match-any CM_VOICE
match ip dscp ef
class-map type inspect match-any INTERNAL_DOMAIN_FILTER
match protocol msnmsgr
match protocol ymsgr
class-map type inspect match-all CLASSMAP_INSPECTION-VPN-IN
match access-group name ACL_VPN-IN
class-map type inspect match-any CLASSMAP_INSPECTION-OUTBOUND
match protocol tcp
match protocol udp
match protocol icmp
match protocol dns
match protocol http
match protocol https
!
policy-map type inspect POLICYMAP_INSPECTION-OUTBOUND
class type inspect CLASSMAP_INSPECTION-OUTBOUND
inspect
class class-default
drop log
policy-map PM_QOS
class CM_VOICE
priority
class class-default
fair-queue
policy-map PM_OUTSIDE_OUTBOUND
class class-default
shape average 12000000
service-policy PM_QOS
policy-map type inspect POLICYMAP_INSPECTION-VPN-IN
class type inspect CLASSMAP_INSPECTION-VPN-IN
inspect
class class-default
drop
!
zone security INTERNET
zone security INSIDE
zone-pair security ZP_INSIDE-to-OUTSIDE source INSIDE destination INTERNET
service-policy type inspect POLICYMAP_INSPECTION-OUTBOUND
zone-pair security ZP_OUTSIDE-to-INSIDE source INTERNET destination INSIDE
!
!
crypto vpn anyconnect usbflash0:/webvpn/anyconnect-win-4.4.00243-webdeploy-k9.pkg sequence 1
!
crypto isakmp policy 1
!
crypto isakmp policy 2
encr aes 256
hash sha256
group 2
!
!
crypto ipsec transform-set TRANSFORMSET-IPSEC_S2S-ASA esp-aes 256 esp-sha-hmac
mode tunnel
crypto ipsec transform-set TRANSFORMSET-IPSEC_S2S-DYNAMIC esp-aes 256 esp-sha-hmac
mode tunnel
!
!
!
crypto dynamic-map CRYPTOMAP-DYNAMIC_S2S-DYNAMIC 1
description ** DYNAMIC TUNNELS **
set transform-set TRANSFORMSET-IPSEC_S2S-DYNAMIC
set pfs group24
set ikev2-profile IKEV2-PROFILE_S2S_DYNAMIC
!
!
crypto map CRYPTOMAP_OUTSITE 1 ipsec-isakmp
set peer [REDACTED]
set transform-set TRANSFORMSET-IPSEC_S2S-ASA
set pfs group24
set ikev2-profile IKEV2-PROFILE_S2S_ASA5520
match address ACL_CRYPTOMAP-S2S-ASA
crypto map CRYPTOMAP_OUTSITE 65001 ipsec-isakmp dynamic CRYPTOMAP-DYNAMIC_S2S-DYNAMIC
!
!
!
!
!
interface Loopback0
ip address 172.20.55.254 255.255.255.255
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description **Inside Interface**
mtu 1400
ip address 172.20.48.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
zone-member security INSIDE
duplex auto
speed auto
!
interface GigabitEthernet0/1
description ** OUTSIDE INTERNET **
ip address dhcp
no ip proxy-arp
ip nat outside
ip virtual-reassembly in
zone-member security INTERNET
duplex auto
speed auto
no cdp enable
crypto map CRYPTOMAP_OUTSITE
!
interface Virtual-Template1
ip unnumbered Loopback0
zone-member security INSIDE
!
ip local pool ADDRESSPOOL_ANYCONNECT 172.20.52.1 172.20.52.6
ip forward-protocol nd
!
ip http server
ip http upload enable path flash:
ip http upload overwrite
ip http access-class 23
ip http authentication local
ip http secure-server
ip http secure-trustpoint [REDACTED]
!
ip tftp source-interface Loopback0
ip nat inside source route-map ROUTEMAP_NAT interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 dhcp
ip ssh source-interface GigabitEthernet0/0
ip ssh version 2
ip scp server enable
!
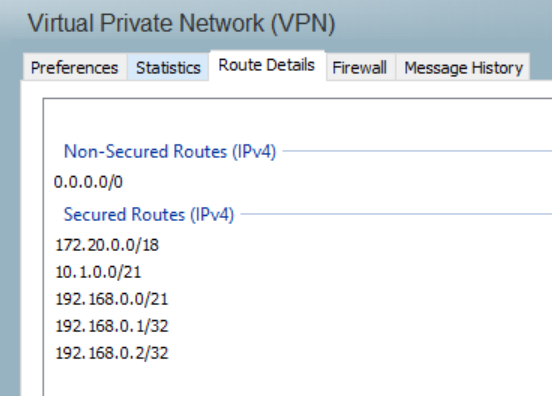
ip access-list standard ACL_ANYCONNECT-SPLITTUNNEL
permit 172.20.0.0 0.0.63.255
permit 10.1.0.0 0.0.7.255
permit 192.168.0.0 0.0.7.255
!
ip access-list extended ACL_CRYPTOMAP-S2S-ASA
permit ip 172.20.48.0 0.0.7.255 192.168.0.0 0.0.7.255
permit ip 172.20.48.0 0.0.7.255 10.1.0.0 0.0.7.255
permit ip 172.20.48.0 0.0.7.255 172.20.32.0 0.0.7.255
ip access-list extended ACL_NAT
deny ip 172.20.48.0 0.0.7.255 172.20.0.0 0.0.63.255
deny ip 172.20.48.0 0.0.7.255 192.168.0.0 0.0.7.255
deny ip 172.20.48.0 0.0.7.255 10.1.0.0 0.0.7.255
permit ip 172.20.48.0 0.0.0.255 any
ip access-list extended ACL_VPN-IN
permit esp any any
permit udp any any eq isakmp
!
!
route-map ROUTEMAP_NAT permit 10
match ip address ACL_NAT
match interface GigabitEthernet0/1
!
!
access-list 23 permit 172.20.0.0 0.0.63.255
access-list 23 permit 192.168.0.0 0.0.7.255
access-list 23 permit 10.1.0.0 0.0.7.255
!
!
!
control-plane
!
!
vstack
!
line con 0
session-timeout 60
exec-timeout 60 0
session-disconnect-warning 300
logging synchronous
login authentication local_access
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
session-timeout 60
access-class 23 in
exec-timeout 60 0
privilege level 15
session-disconnect-warning 300
logging synchronous
login authentication local_access
transport input telnet ssh
line vty 5 15
session-timeout 60
session-disconnect-warning 300
logging synchronous
transport input none
!
scheduler allocate 20000 1000
ntp server 192.168.3.5 source GigabitEthernet0/0
!
!
webvpn gateway WEBVPN-GATEWAY_ANYCONNECT
ip interface GigabitEthernet0/1 port 1025
ssl trustpoint [REDACTED]
inservice
dtls port 1025
!
webvpn context WEBVPN-CONTEXT_ANYCONNECT
aaa authentication list AAA_ANYCONNECT
gateway WEBVPN-GATEWAY_ANYCONNECT
!
ssl authenticate verify all
inservice
!
policy group GROUPPOLICY_ANYCONNECT-SPLIT
functions svc-enabled
svc address-pool "ADDRESSPOOL_ANYCONNECT" netmask 255.255.255.248
svc keep-client-installed
svc split include acl ACL_ANYCONNECT-SPLITTUNNEL
svc dns-server primary 192.168.0.1
svc dns-server secondary 192.168.0.2
!
policy group GROUPPOLICY-ANYCONNECT-FULL
functions svc-enabled
svc address-pool "ADDRESSPOOL_ANYCONNECT" netmask 255.255.255.248
svc dns-server primary 192.168.0.1
svc dns-server secondary 192.168.0.2
default-group-policy GROUPPOLICY_ANYCONNECT-SPLIT
!
end
Solved! Go to Solution.
- Labels:
-
ISR G2
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 10:31 AM
Hello,
the subnet you included in the ACL, 172.20.52.0/18, includes all hosts in the range 172.20.0.1 - 172.20.63.254, which includes the entire inside network.
To be on the safe side, and to avoid making mistakes with access lists, I would always use an IP address range that is completely different from the local LAN (your NAT inside). So instead of 172.120.x.x, use something in the 10.x.x.x or 192.168.x.x range for the address pools...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 09:15 AM
Hello,
your local address pool (172.20.52.1 172.20.52.6) and your inside network appear to be in the same subnet that is included in the split ACL. Try to make the changes in bold:
ip access-list standard ACL_ANYCONNECT-SPLITTUNNEL
permit 172.20.52.0 0.0.0.255
permit 10.1.0.0 0.0.7.255
permit 192.168.0.0 0.0.7.255
webvpn context WEBVPN-CONTEXT_ANYCONNECT
aaa authentication list AAA_ANYCONNECT
gateway WEBVPN-GATEWAY_ANYCONNECT
ssl authenticate verify all
inservice
policy group GROUPPOLICY_ANYCONNECT-SPLIT
functions svc-enabled
svc address-pool "ADDRESSPOOL_ANYCONNECT" netmask 255.255.255.0
svc keep-client-installed
svc split include acl ACL_ANYCONNECT-SPLITTUNNEL
svc dns-server primary 192.168.0.1
svc dns-server secondary 192.168.0.2
virtual-template 1
default-group-policy GROUPPOLICY_ANYCONNECT-SPLIT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 10:13 AM - edited 05-11-2019 10:22 AM
Georg,
Thanks for reviewing my issue.
I believe the inside network should be 172.20.48.0/24.
interface GigabitEthernet0/0 description **Inside Interface** mtu 1400 ip address 172.20.48.254 255.255.255.0 ip nat inside ip virtual-reassembly in zone-member security INSIDE duplex auto speed auto
ip dhcp pool DHCP-POOL_INTERNAL network 172.20.48.0 255.255.255.0 domain-name [REDACTED] default-router 172.20.48.254 dns-server 192.168.0.1 172.20.0.6 8.8.8.8
There are four other sites (each site is assigned a /20) which is why I used a /18 in the split tunnel ACL.
I could break that out and only include the blocks for the other sites and the local block (172.20.48.0/24) if you think that should be tested.
Am I missing something else?
I'll start testing those changes once I get back to the device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 10:20 AM
Here's something else that's weird:
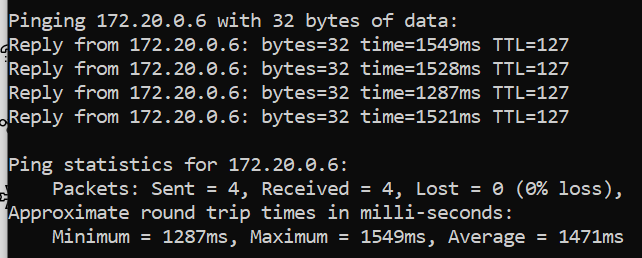
The remote client can ping the 1921's loopback interface (Loopback 0, 172.20.55.254), which is included in the current split tunnel ACL
ip access-list standard ACL_ANYCONNECT-SPLITTUNNEL permit 172.20.0.0 0.0.63.255 (loopback is in here, works) permit 10.1.0.0 0.0.7.255 permit 192.168.0.0 0.0.7.255 (doesn't work)
Remote clients can ping this guy:
interface Loopback0 ip address 172.20.55.254 255.255.255.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 10:31 AM
Hello,
the subnet you included in the ACL, 172.20.52.0/18, includes all hosts in the range 172.20.0.1 - 172.20.63.254, which includes the entire inside network.
To be on the safe side, and to avoid making mistakes with access lists, I would always use an IP address range that is completely different from the local LAN (your NAT inside). So instead of 172.120.x.x, use something in the 10.x.x.x or 192.168.x.x range for the address pools...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2019 07:50 AM
@Georg Pauwen wrote:...To be on the safe side, and to avoid making mistakes with access lists, I would always use an IP address range that is completely different from the local LAN (your NAT inside)...
I think that was the key. I didn't change the subnet I was using, but I changed the NAT ACL based on what you said about not overlapping:
ip access-list extended ACL_NAT deny ip 172.20.48.0 0.0.3.255 172.20.55.0 0.0.0.7 (added for AnyConnect) deny ip 172.20.48.0 0.0.7.255 172.20.0.0 0.0.63.255 (Sites 1-4 including this one) deny ip 172.20.48.0 0.0.7.255 192.168.0.0 0.0.7.255 (5th site) deny ip 172.20.48.0 0.0.7.255 10.1.0.0 0.0.7.255 (6th site) permit ip 172.20.48.0 0.0.0.255 any
(The remote subnet doesn't actually overlap the local LAN, local LAN is a /24 and remote is a /29 in two different subnets, but do the site to site tunnels using blocks /21 so one statement covers all the subnets at that site)
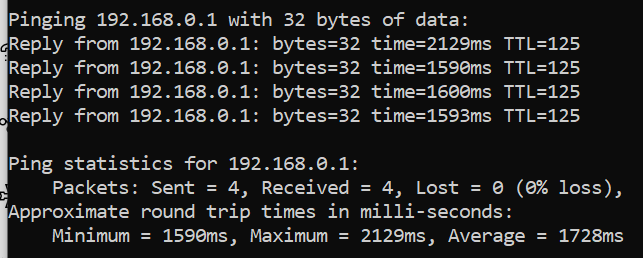
Results from remote AnyConnect client on 172.20.52.0/29:
Hitting other sites while remoted in using AnyConnect 172.20.52.2 going to:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide