- Cisco Community
- Technology and Support
- Networking
- Routing
- NAT a specific host outbound to a specific public IP, not the NAT pool
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
09:06 AM
- last edited on
08-26-2022
02:33 AM
by
Translator
![]()
I have a NAT issue that has been nagging me forever.
My Internet router has nat overload pool configured for PAT outbound from the internal RFC-1918 network. This works fine. I have inside source nat configured for inbound NAT of a public IP to a host inside RFC-1918 IP. This too works fine.
But..... I want that same inside host when going outbound to the internet to nat outbound using the same public as the inside uses. When the inside host goes outbound right now, its public IP is shown as the router's interface IP in the PAT pool and not the static NAT.
IP fudged to protect security.
router outside interface: 1.1.1.1
host IP: 172.16.14.14
static inside source NAT: 172.16.14.14 NATs to 1.1.1.10 for inbound traffic
Can this be done so host's outbound traffic flow shows coming from 1.1.1.10 instead of the 1.1.1.1 PAT pool?
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
12:39 PM
- last edited on
08-26-2022
02:35 AM
by
Translator
![]()
Hello
@jbankstonps wrote:
static inside source NAT: 172.16.14.14 NATs to 1.1.1.10 for inbound traffic
Can this be done so host's outbound traffic flow shows coming from 1.1.1.10 instead of the 1.1.1.1 PAT pool?
Deny that inside host from your dynamic pat acl and then create a static nat statement.
Example:
access-list 100 deny host 172.16.14.14 any
access-list 100 permit ip 172.16.14.0 0.0.0.255 any
ip nat inside source-list 100 interface <wan> overload
ip nat inside source static 172.16.14.14 1.1.1.10
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022 09:11 AM
small lab and share result soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
09:40 AM
- last edited on
08-26-2022
02:34 AM
by
Translator
![]()
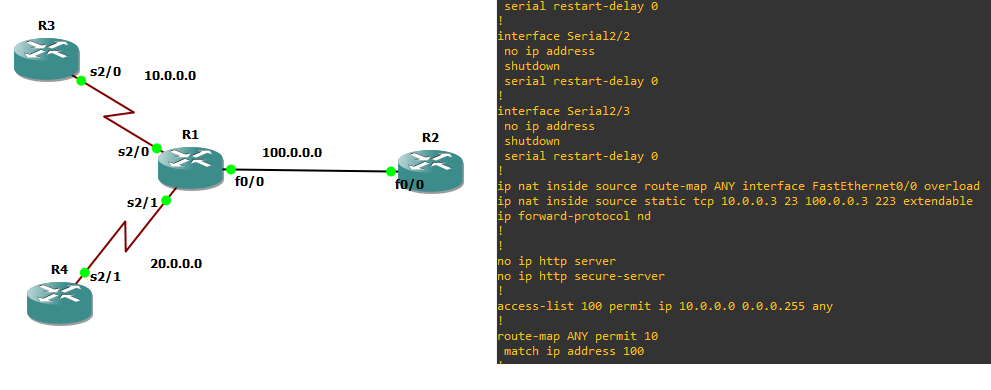
I do small lab and success
in dynamic NAT instead of use list use
route-map
as following
ip nat inside source
route-map
ANY interface X/X overload
!
route-map ANY permit 10
match ip address 100
!
ip access-list extended 100
permit ip <LAN><LAN MASK> any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
10:14 AM
- last edited on
08-26-2022
02:38 AM
by
Translator
![]()
not what I was looking for.
all other inside hosts go outbound using the PAT interface nat but I need the one host to go outbound using a static nat so that the public internet sees the host's public IP as the 1.1.1.10 while the other inside hosts' will be shown as coming from the 1.1.1.1 interface PAT IP. I tried a
route-map
to force the host's nat that way and it didn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022 10:34 AM


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
12:39 PM
- last edited on
08-26-2022
02:35 AM
by
Translator
![]()
Hello
@jbankstonps wrote:
static inside source NAT: 172.16.14.14 NATs to 1.1.1.10 for inbound traffic
Can this be done so host's outbound traffic flow shows coming from 1.1.1.10 instead of the 1.1.1.1 PAT pool?
Deny that inside host from your dynamic pat acl and then create a static nat statement.
Example:
access-list 100 deny host 172.16.14.14 any
access-list 100 permit ip 172.16.14.0 0.0.0.255 any
ip nat inside source-list 100 interface <wan> overload
ip nat inside source static 172.16.14.14 1.1.1.10
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022
12:54 PM
- last edited on
08-26-2022
02:36 AM
by
Translator
![]()
with a slight twist...... I had to remove the static nats being used at the port level and then put in one single nat IP to IP, without any extendable port nats
ip nat inside source static tcp 172.16.14.14 25 1.1.1.10 25 extendable
and all the other ports nats were replaced with a single
ip nat inside source static 172.16.14.14 1.1.1.10
and it works now!
very cool, thank you, just some additional feedback as the port nats were part of the complication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022 01:17 PM
it work what, can you ping now from 172.16.14.14 to 8.8.8.8 ? or it work can you access from Out to 172.16.14.14 using port 25 ?
can you elaborate?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide