- Cisco Community
- Technology and Support
- Networking
- Routing
- NAT-ing on a specific ASA port
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAT-ing on a specific ASA port
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2011 03:09 AM - edited 03-04-2019 01:21 PM
Hi everyone...
Trying to configure the cisco ASA to perform NAT-ing. The scenario is such.
Currently, we have a network topology as such

The link to the outside world is a IPSEC. The Ip addresses going through the IPSec are the 172.31.xx.xx ones.
however, there is a requiment that one specific customer does not want the 172.31.xx.xx addresses to sip into the IPSec. They would like a public ip address.
My option, is to do NAtting at the port of the ASA. So, i placed another redundant GE cable from the switch to the router, as shown below.
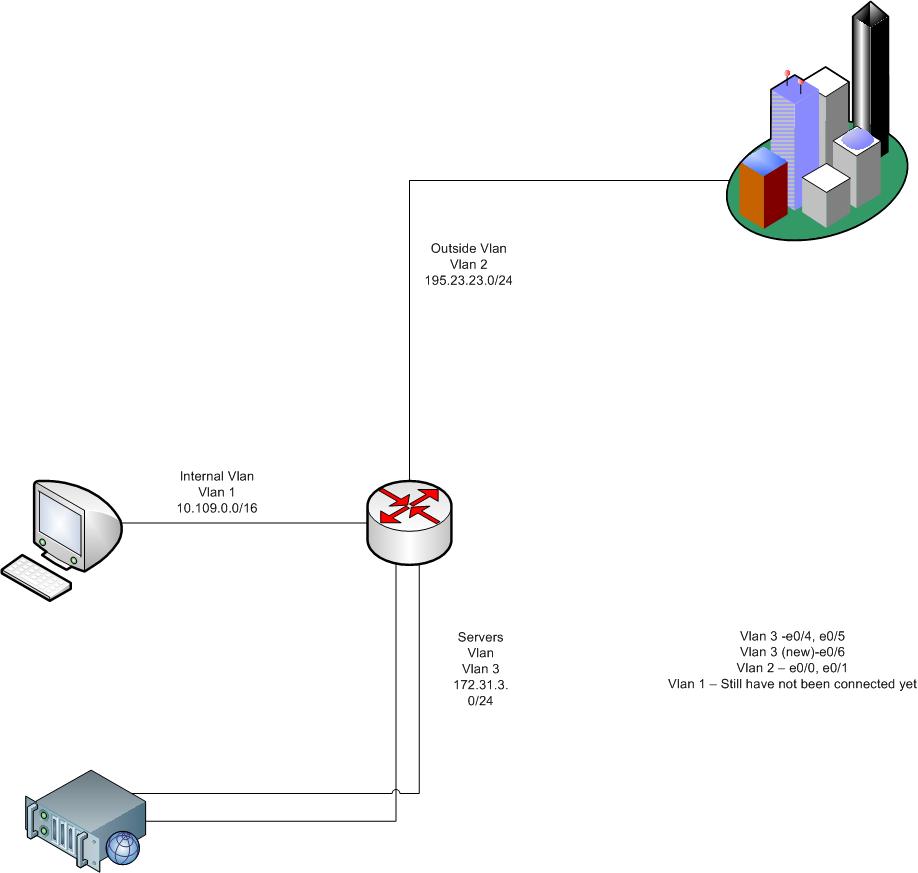
Say, i place it in port e0/6. And assign it to vlan 3.
How can i make a NAT for this specific port (PAT)? I am seeing that ASA can only produce NAT for a collective output...
eg : #nat (inside) xx.xx.xx.xx yy.yy.yy.yy
example :#global (outside)1 10.21.67.40-10.21.67.45 netmask 255.255.255.240
1. How can i make only e0/6 to perform nat and not the rest?
from what i see, and did
#e0/0
#nat (inside) nat id access list netmask outside ...
Is this applicable?
2. Is there any way to just perform NAT on a specific destination address?
3. any other method to accomplish this?
Configuration:
interface Vlan1
nameif inside
security-level 100
ip address 10.xxx.xx.xx 255.255.0.0
!
interface Vlan2
nameif outside
security-level 0
ip address 195.xx.xx.xx 255.255.255.0
!
interface Vlan3
no forward interface Vlan1
nameif application
security-level 50
ip address 172.31.xx.xx 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 2
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
switchport access vlan 3
!
interface Ethernet0/5
switchport access vlan 3
!
interface Ethernet0/6
!
interface Ethernet0/7
Help.....
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2011 05:24 AM
Hi,
you can have static nat or port redirection. if static nat in place your server can access internet directly. if port redirection in place it will respond only to the request what it will receive from outside world. pick your option and do the config accordingly.
example : with static nat your server can access internet and fresh traffic to this server should be allowed in access list.
static (application,outside) 195.x.x.x 172.31.x.x netmask 255.255.255.255
or you can do port redirection from outside world to specific ip address or outside interface itself.
example: With this statment server will not have access to internet and you need allow redirected port in access list to have access to the same from internet.
static (application,outside) tcp 195.x.x.x 22 172.31.x.x 22 netmask 255.255.255.255
static (application,outside) tcp 195.x.x.x 80 172.31.x.x 80 netmask 255.255.255.255
static (application,outside) tcp 195.x.x.x 443 172.31.x.x 443 netmask 255.255.255.255
static (application,outside) tcp interface 172.31.x.x 443 netmask 255.255.255.255
if you know which source is sending traffic ( customer public ip address )to these servers you can have access list outside to permit the same or else you need to open for entire public.
Rgds
Rama
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide