- Cisco Community
- Technology and Support
- Networking
- Routing
- Natting a server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 01:52 PM - edited 03-04-2019 10:22 PM
I've a Nat problem that is confounding me.
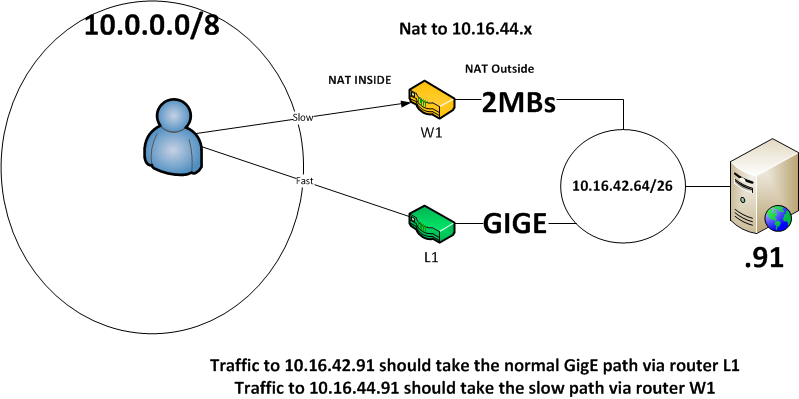
Today .. in our lab I have a video server that sits on subnet 10.16.42.91/26
This subnet is run by a L3 switch with L3 routing back to the rest of the network.
I need to test this server over an emulated WAN access to validate branch office performance.
The WAn Emulator is all setup and works fine
Now I'd like to extend this slow acess outside the lab, so that any one can test the slow path from their desk.
Do do this I've added a 2nd router between the video server subnet and the rest of the network
I'd like to NAT the 10.16.42.91 address to 10.16.44.91,
Such that .. anyone referencing 10.16.44.91 goes via the slow path, and anyone using 10.16.42.91 goes via the GigE
The NAting router is an 881 running 15.3
It would need to do hide-nat so return traffic would flow via the NAT router
I've tried several nat configs, but remain confounded.
Diagram below .. would appreciate any suggestion
Thanks in advance
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 02:30 PM
Wes
You need two things -
1) for the return traffic to go back to the 881 you need to NAT overload all the user IPs to the 10.16.42.x interface IP on the 881. You have the inside facing the users which makes it a lot easier so -
access-list 101 permit ip 10.0.0.0 0.0.0.255 host 10.16.44.91
ip nat inside source list 101 interface
Note i'm not entirely sure the exact order of processing in terms of the two NAT statements so in the acl above where you have the host 10.16.44.91 you might need to change it to the real IP of the server. Try the above first.
2) a NAT for the server -
ip nat outside source static 10.16.42.91 10.16.44.91 netmask 255.255.255.255
Edit - i'm assuing you have already assigned "ip nat inside" to the interface on the 881 facing the users and "ip nat outside" on the interface facing the server.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 03:01 PM
Hi Wes,
Also to add to Jon's post, you may need to add a static route on the 881 that routes 10.16.44.91 out of the interface facing the server. Something like
ip route 10.16.44.91 255.255.255.255
This is required as inside to outside NAT needs to make a routing desicion first before packets will be translated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 02:30 PM
Wes
You need two things -
1) for the return traffic to go back to the 881 you need to NAT overload all the user IPs to the 10.16.42.x interface IP on the 881. You have the inside facing the users which makes it a lot easier so -
access-list 101 permit ip 10.0.0.0 0.0.0.255 host 10.16.44.91
ip nat inside source list 101 interface
Note i'm not entirely sure the exact order of processing in terms of the two NAT statements so in the acl above where you have the host 10.16.44.91 you might need to change it to the real IP of the server. Try the above first.
2) a NAT for the server -
ip nat outside source static 10.16.42.91 10.16.44.91 netmask 255.255.255.255
Edit - i'm assuing you have already assigned "ip nat inside" to the interface on the 881 facing the users and "ip nat outside" on the interface facing the server.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 03:01 PM
Hi Wes,
Also to add to Jon's post, you may need to add a static route on the 881 that routes 10.16.44.91 out of the interface facing the server. Something like
ip route 10.16.44.91 255.255.255.255
This is required as inside to outside NAT needs to make a routing desicion first before packets will be translated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 03:03 PM
Will
Good spot. For some reason i always forget the route when doing that particular NAT
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 05:58 PM
Thanks Guys
I didn't think to combine the interface hide-nat along with the static source nat.
The NAT ACL had to be the inside IP vs the actual server ip
works like a charm now
ip nat inside source list 102 interface FastEthernet4 overload << hide-nat behind the router outside addr
ip nat outside source static 10.16.42.95 10.16.226.95 extendable add-route << static nats per host
ip nat outside source static 10.16.42.94 10.16.226.94 extendable add-route
access-list 102 permit ip any host 10.16.226.95 <<<< had to be the inside address
access-list 102 permit ip any host 10.16.226.94
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
