- Cisco Community
- Technology and Support
- Networking
- Routing
- Network Design for Integration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 06:54 PM
Dear all,
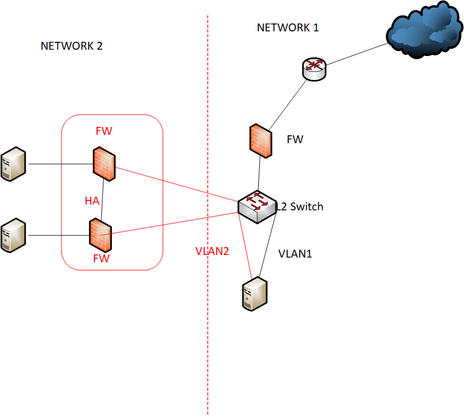
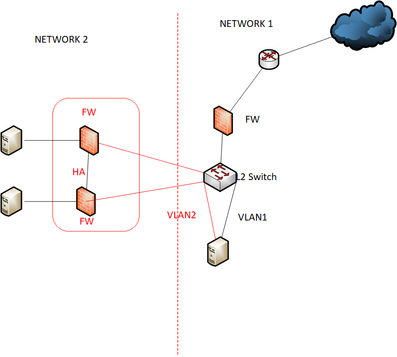
I have concern the existing network design and i would like to change.On our existing design ,we two network.
Network 1 is primary.we have other network,network 2, that network need to access our server.
So previous design is we use L2 switch and create two vlan(one for network 1 ,one for network 2).
our server have two network interface and one interface connect to vlan1 and one interface connect to vlan2.
server guy run persistence route in server for two network.Please see below diagram.
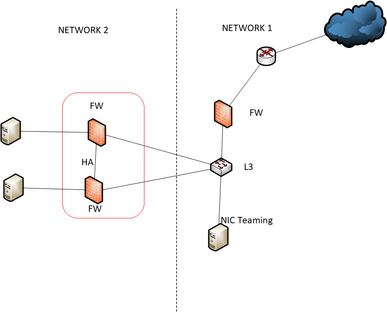
I would like to change below design.But i also concern my new design.i consider to use L3 swithch to integrate network 2 and run static route to network 2.
So please help me which one is the best practice in design ?
What kind of protocol should i need to use to integrate Network 2 Firewall links ,Ether-channel?
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 10:58 PM
Hi @Leo Laohoo
I am looking for benefits for avoiding asymmetric routing.
As I understand his question, he is facing issue with routing between both Networks because he installed second ASA (which are in HA) in Routed mode. so whenever network 2 want's to communicate with Network 1's server reply packet's are getting drops due to asymmetric routing.
Why is it happening:
Network 2's server is sending a packet to Network 1 server then as per normal "AND" rule server will reply to the default gateway and main ASA is getting a drop because he is not configured for asymmetric routing. So he found another way and added routes on the server itself.
There is also a solution to allow asymmetric routing on the main ASA but he already designed the network so we would go with layer 3 switch. It will resolve his asymmetric routing issue.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 08:32 PM
Hi,
So please help me which one is the best practice in design ?
I suggest going with your network design option 3 with the Layer 3 network.
No, AS Single cable is connected between per ASA to switch so you do not require EtherChannel. Configure the ports in Access port if you are moving with Layer network.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 08:17 AM
Hello
How is network 2 getting out to the internet at present and if it isnt t does the OP require network 2 to access the internet?
We dont see where the correlation /routing at present between vlan1-2 being performed (if any), is the server doing this?
Even if you turn that L2 switch into a L3 what is the advantage of this?
I would say there isnt not enough information at present to provide a definitive answer, unless i am missing something which is highly likely!
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 06:04 PM
Hi ,
I forgot to give some information.Network 1 is our branch site,it need to access our DC.
Network 2 is other network and it isn't under control. They need to access my server to get some data.
Last time we run persistence route in server,default rout to network 2 and static route to our DC.
I thought it is not proper way so we change to L2 to L3.
If i use NIC teaming i need to run LACP in switch side,correct ? or Which design is the best practice ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 07:20 PM
Hi,
Now the design has changed. As network 1 is your branch site. How to connected both sides? Are you using Site to Site VPN, MPLS etc? Why did you show us that it is connected on switch directly? Do you have two ISP connections one like the Internet and another as a site to site VPN or MPLS?
Know we are looking for more information on the same.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 08:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 10:47 PM
Hi,
How many users are working on Site-A?
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2019 01:34 AM
Hi,
Not too much ,this server is retrieve some data from DC and Network 2 pull this data only.Why ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 04:00 AM
Hi,
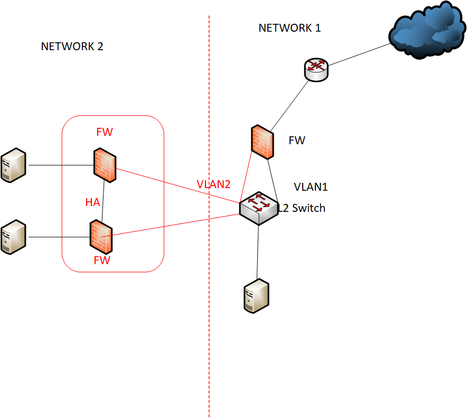
I asked you to figure out do you really required a Layer 3 switch. If you asking me, I am happy with Layer 2 switch in Network 1 and a port-channel between ASA to Existing Layer 2 switch. Create Two VLAN's on Cisco Switch and same on ASA. Now One VLAN will keep as LAN and one keeps as DMZ.
It will save your money and provide you an aditional level of security between Server and Clients. Why you configured routes on your server? I don't think it will require in this case because all data will travel to Gateway (ASA) and ASA will take action as per configuration of ACL, NAT etc.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 02:28 PM - edited 04-03-2019 02:38 PM
Hi,
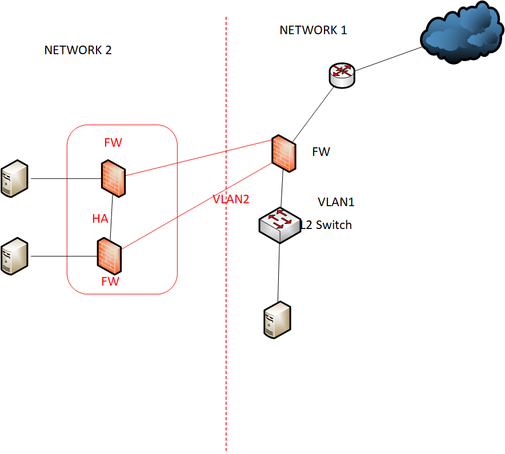
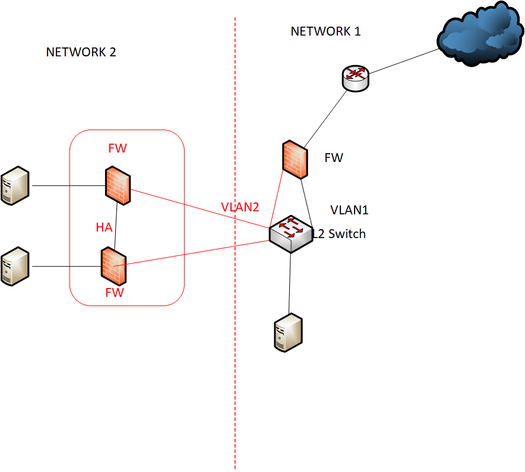
Do you mean below design ? Network 2 firewall link connect to our switch is 2x 10 G fiber.
Let me know if I am using ASA 5512 .5512 support SFP +. can connect their firewall to my firewall .But i have only one firewall.Can i do as below design ? and let me know ASA can do link aggregation because i need more bandwidth.their firewall links is 2 x 10 G to our network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2019 02:31 AM - edited 03-28-2019 02:34 AM
Hello
Looks like you have a security issue regards your server you don't mention if this is running some fw application so i am assuming it isn't, Anyway it has presence in both networks as such any breach on that device could leave both networks open to each other.
One possible solution could be to have your network 1 fw provide L3 for vlan 1-2, Add an additional physical into this fw for vlan 2, Team you server nics for vlan 1 between the L2 switch and lastly DMZ vlan2 so only specific hosts can leak into vlan1 for that server
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 02:20 AM
Hi,
the another problem is my firewall cannot support sfp+. Network 2 firewall will use 2 x 10 G fiber.
so i consider L3 switches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 02:11 AM
Hi,
Again we came to the same point. How to both sites are connected? Are you using VPN (As you said), or Direct Fiber cables, or MPLS connection or secondary internet connection for VPN?
If it is VPN connection then why are you thinking that Network 2 is using fiber cable and you can't do this because of the port not available on the firewall? You havan e Internet connection and VPN will make over the existing internet connection. It is software configuration but a part of the hardware.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 01:58 AM - edited 04-08-2019 01:58 AM
Hi Deepak kuma,
Network 2 is not my network.i cannot control and cannot say them don't use fiber.
My network is direct fiber network.They don't need to integrate our existion network.They only need to access my server that specifically create for them.my server pull some data from my DC and they will retrieve data from my server.they cannot access directly our DC.So i consider for integration design. The below design is previous design proposed and i don't know what is the best practice.
Some friends advise to use below design .Network 2 is in DMZ zone.
Network 2 firewall is using 2x 10 G firber.(it is their requirement). I need to propose their requirement.
i want to propose cost effective simple design. and i would like to know their firewall link 2x 10 G can directly connect to my firewall. my ASA firewall is 5512.so my firewall support SFP+.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 10:48 PM
I really don't see any benefits of turning the Layer 2 switch to do Layer 3 in a simple network like that.
NIC teaming, however, is a good idea.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide