- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Problem in DMVPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem in DMVPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2021 04:51 AM
As, i am trying to do DMVPN using OSPF. But OSPF neighbor does not created. And R1(HO) router also get some notification such as %CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC packet. (ip) vrf/dest_addr= /192.168.1.1, src_addr= 192.168.1.30, prot= 47
Any Help!!
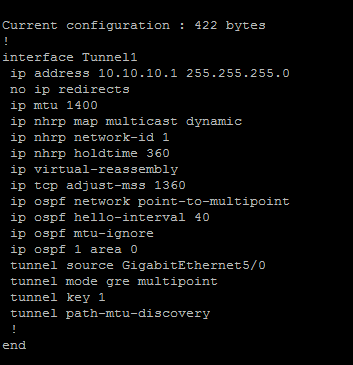
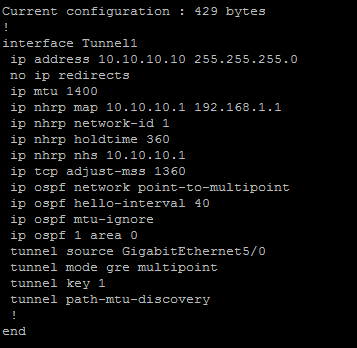
I have also uploaded my config files here
- Labels:
-
ASR 1000 Series
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2021 07:32 AM
Hello ,
see the following document
you may need a statement like the folowing on Branch router on each mGRE tunnel pojnting to external HUB address in each mGRE cloud
ip nhrp map multicast 192.168.1.1
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2021 07:49 AM
Thank you but in my lab, OSPF neighbor does not created. I don't know why??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 06:32 AM
Hello,
as already noted you are missing the commands to make the mGRE tunnel protected by IPSec
follow the document I have provided in my previous post
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 07:42 AM
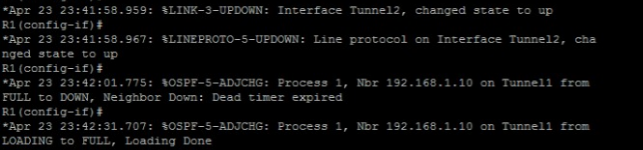
Thank you for your response. As i have mention my problem was (OSPF neighbor is not formed). When I use 'ip ospf network point-to-multipoint' command the OSPF neighbor is formed. But some errors comes after it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 08:51 AM
Hello
it looks like you have recursive routing error causing the OSPF to flap
external networks used as tunnel source must not be advertised over the tunnel
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 09:12 AM
Hello,
Thank you.
I remove advertising external network, but it does not work. I use external network only for mapping tunnel IP with external IP of HeadOffice in Branch Tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2021 02:42 PM
the issue here that there is IPSec under the Physical Interface and not under the tunnel "IPSec profile".
this is why the OSPF and IPSec issue appear.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 07:43 AM
Hello,
In tunnel there is OSPF.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 09:21 AM
Freind as i mnetion before if you not solve ipsec then ospf issue appear becuase message is not deencryprt right and peer will assume the other peer is dead and ospf is flap.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 01:43 PM
My suggestion would be start from the ground up. Remove all IPSEC configuration so it is not active. Does the DMVPN tunnel go UP & has the OSPF adj formed if not focus on that.
Once that is working then you can add IPSEC and best to add in the following way:
{ global config }
crypto isakmp policy 1
encryption aes
authentication pre-share
group 14
crypto isakmp key cisco47 address 0.0.0.0 0.0.0.0
!
crypto IPsec transform-set trans2 esp-aes esp-sha-hmac
mode transport
!
crypto IPsec profile vpnprof
set transform-set trans2
{under tunnel interface}
tunnel protection IPsec profile vpnprof
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 08:28 PM
Thank you so much.But I can not remove IPsec config because one other side, 1 router should be connected through IPsec VPN and on other side, one router is connected through DMVPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2021 07:32 AM
As me mention before and as My friend send to you
we here not remove the IPSec but change the config
instead of config IPSec Map under the physical Interface
we config IPSec Profile under the Tunnel Interface
this the solution here.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide