- Cisco Community
- Technology and Support
- Networking
- Routing
- redirect one ip to an other
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
redirect one ip to an other
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2023 03:45 PM
equipment
c1111 ipbase
4x lan ports (i think l2 ports ?? you cant create sub interfaces on them cant do no switch port and so on)
2x wan ports can create subintarfaces on them and seems to have a larger comand set then the prvios 4
c2960x ipbase (yes its a l2 switch BUT it hase limited L3 capabilities!!!)
24 ports
what i ultimatly try to acomplis is having multiple servers with the same service running use asl and in case the main one isnt responding redirect to the secondary
an exaple for such a service would be home assitant
HA 1 is 10.0.0.1 VLAN 10
HA 2 is 10.0.0.2 VLAN 10
both are connectred to the 2960x
a desktop from where i need to reach them 20.0.0.1 also connectred to the 2960x VLAN 20
the c1111 is connected to the 2960x with one of his lan ports (trunk port)
interface GigabitEthernet0/1/1
description CON-c1111-c2961
switchport mode trunk
interface Vlan123
description Vlan123
ip address 10.123.0.1 255.255.255.0
ip nat inside
on the 2960x it looks like this
interface GigabitEthernet1/0/1
description C1111
switchport mode trunk
interface Vlan123
ip address 10.123.0.2 255.255.255.0
they are also connected in the folowing way
c1111
interface GigabitEthernet0/0/1
description WAN1 (on this port i can create subintarfaces in contrast to the others)
ip address 10.21.0.1 255.255.255.0
ip nat outside
on the 2960x
interface GigabitEthernet1/0/4
no switchport
ip address 10.21.0.2 255.255.255.0
on the c1111 i have
ip nat inside source static tcp 10.2.12.10 80 10.21.0.1 80 extendable
c1111#sh ip nat t
Pro Inside global Inside local Outside local Outside global
tcp redacted
tcp 10.21.0.1:80 10.2.12.10:80 --- ---
tcp 10.21.0.1:80 10.2.12.10:80 10.2.10.10:50557 10.2.10.10:50557
tcp 10.21.0.1:80 10.2.12.10:80 10.2.10.10:50558 10.2.10.10:50558
tcp 10.21.0.1:80 10.2.12.10:80 10.2.10.10:50556 10.2.10.10:50556
Total number of translations: 5
i assume the problem i am facing in the moment is the back chanel
on 10.2.12.10 i can see requests coming from 10.2.10.10 but on the way back eg. when
10.2.12.10 sends them to 10.2.10.10 they will be routed by the 2960x and the requester
will expect the response from 10.21.0.1 and not from 10.2.12.10
i am a bit lost in the moment any help would be apriciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 11:33 AM
A bit confuse what you are trying to accomplish. I advise you to put all this idea in a simple diagram. That would be easier to anyone undestand. Also, if you want to load balance service, you may need a load balancer in between. Another good idea is run this setup in a lab like Packet Tracer, even though you can not test service you can validate connectivity at least.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 12:15 PM
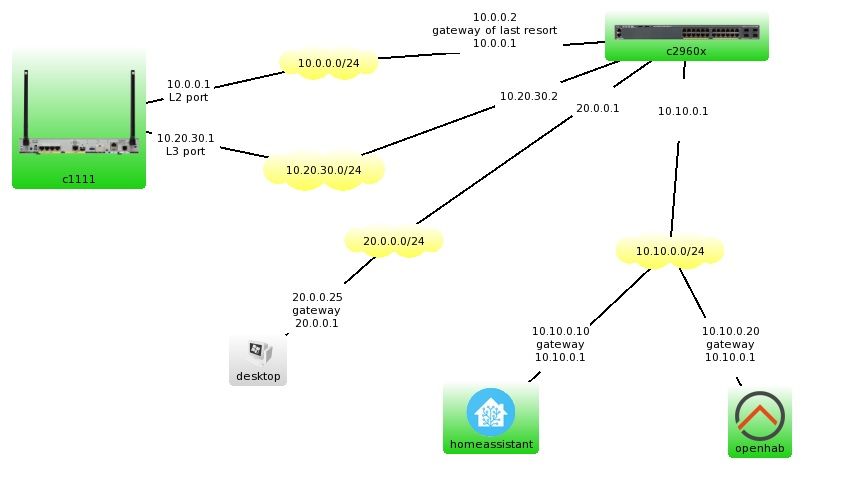
routing between 10.10.0.0 and 20.0.0.0 is done by the c2960x
so accessing 10.10.0.10 or 10.10.0.20 from 20.0.0.25 will go
desktop --> c2960 --> homeassistant
what i try to acomplis is
10.20.30.1 should bring me to 10.10.0.10 OR 10.10.0.20
depending on if 10.10.0.10 is reachable or not (sla icmp or http probing)
so it should be routed to the second ip just in case the first is unreachable
as a failover (not loadbalancing) this should be done by the c1111
hope this way its a bit more clear what my target is
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 02:34 PM
Much better. But I dont see any 10.20.30.x on your first post. Can you share the show running-config from both switch and router?
Just to make sure I understood correctly. From the desktop you will call 10.30.0.1 and you want to pass through the router and reach 10.10.0.x by using NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 06:07 PM
no service pad
service timestamps debug datetime msec localtime show-timezone year
service timestamps log datetime msec localtime show-timezone year
service password-encryption
service internal
service sequence-numbers
!
hostname c2961
!
boot-start-marker
boot-end-marker
!
logging buffered 163840
logging persistent url flash:/logs/ size 819200 filesize 16384 batch 8192
enable secret 9 ------------
!
username --- secret 9 ----------
username --- privilege 15 secret 9 ------------
no aaa new-model
clock timezone --- 1 0
switch 1 provision ws-c2960x-24ts-l
!
!
!
!
ip routing
no ip cef optimize neighbor resolution
!
ip dhcp pool 2961-DOMAIN
network 10.2.10.0 255.255.255.0
default-router 10.2.10.1
dns-server 10.10.10.10
lease 0 0 3
!
!
ip domain-name ----.com
ip name-server 10.2.12.10
ip name-server 10.2.12.11
ip accounting-threshold 500
ip accounting-list 0.0.0.0 255.255.255.0
login on-failure log
login on-success log
vtp interface abc
!
!
mls qos
!
crypto pki trustpoint ------
enrollment mode ra
enrollment url http://ca.-------.com:80/certsrv/mscep/mscep.dll
fqdn c2961.------.com
subject-name CN=c2961.-------.com,O=-----,OU=CORE DEVICE
subject-alt-name c2961.--------.com
revocation-check none
rsakeypair c2961
!
!
crypto pki certificate chain -----ROOT
certificate 6B00000029BB5D07----------
---- 665591
quit
certificate ca 57974CA27C57-----------
------- D9
quit
archive
path flash:/ConfBack/
maximum 13
write-memory
time-period 1440
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
errdisable recovery cause psecure-violation
errdisable recovery interval 30
!
vlan internal allocation policy ascending
!
class-map match-all dns-kill
!
policy-map policy1
class class-default
set ip dscp af33
!
interface FastEthernet0
description OFF
no ip address
no ip route-cache
shutdown
!
interface GigabitEthernet1/0/1
description C1111
switchport mode trunk
switchport port-security maximum 100
switchport port-security violation restrict
!
interface GigabitEthernet1/0/2
description MIKROTIK SXT 2
switchport access vlan 80
switchport mode access
!
interface GigabitEthernet1/0/3
description apis
switchport access vlan 20
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
spanning-tree portfast edge
service-policy input policy1
!
interface GigabitEthernet1/0/4
no switchport
ip address 10.21.0.2 255.255.255.0
!
interface GigabitEthernet1/0/5
description E1-1
switchport access vlan 20
switchport trunk allowed vlan 20
switchport mode trunk
switchport port-security maximum 9
switchport port-security violation restrict
!
interface GigabitEthernet1/0/6
description E1-2
switchport mode trunk
!
interface GigabitEthernet1/0/7
description OFF
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/8
description OFF
no switchport
no ip address
!
interface GigabitEthernet1/0/9
description E2-1
switchport access vlan 20
switchport trunk allowed vlan 20
switchport mode trunk
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/10
description Apep 2
switchport mode trunk
!
interface GigabitEthernet1/0/11
description OFF
!
interface GigabitEthernet1/0/12
description HSwitch
switchport access vlan 7
switchport trunk allowed vlan 7,1920-1930
switchport trunk native vlan 7
switchport mode trunk
switchport port-security maximum 15
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/13
description HSwitch
switchport access vlan 50
switchport trunk native vlan 50
switchport mode trunk
switchport port-security maximum 15
switchport port-security violation restrict
!
interface GigabitEthernet1/0/14
description POE Switch
switchport access vlan 255
switchport trunk native vlan 7
switchport mode access
switchport port-security maximum 15
switchport port-security violation restrict
!
interface GigabitEthernet1/0/15
description OFF
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/16
description OFF
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/17
description OFF
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/18
description OFF
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/19
description OFF
switchport access vlan 255
switchport mode access
switchport port-security maximum 9
switchport port-security violation restrict
!
interface GigabitEthernet1/0/20
description laptop
switchport access vlan 7
switchport mode trunk
switchport port-security maximum 9
switchport port-security violation restrict
switchport port-security
!
interface GigabitEthernet1/0/21
description Nic 1/3 domain, adg
switchport mode trunk
switchport port-security maximum 50
switchport port-security violation shutdown vlan
!
interface GigabitEthernet1/0/22
description Nic 1/2 wlc
switchport mode trunk
switchport port-security maximum 9
switchport port-security violation shutdown vlan
!
interface GigabitEthernet1/0/23
description Nic 1/3 vision
switchport mode trunk
switchport port-security maximum 9
switchport port-security violation shutdown vlan
!
interface GigabitEthernet1/0/24
description Ra Nic 1/4 grafana, prometheus, influx, sql, scraperw
switchport access vlan 12
switchport mode trunk
!
interface GigabitEthernet1/0/25
description OFF
shutdown
!
interface GigabitEthernet1/0/26
description OFF
shutdown
!
interface GigabitEthernet1/0/27
description OFF
shutdown
!
interface GigabitEthernet1/0/28
description OFF
shutdown
!
interface Vlan1
description OFF
no ip address
!
interface Vlan5
ip address 10.250.250.1 255.255.255.0
!
interface Vlan7
ip address 10.0.0.2 255.255.255.0
!
interface Vlan20
description 2961-MAIN
ip address 10.2.0.1 255.255.255.0
!
interface Vlan50
ip address 10.5.0.10 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan60
ip address 10.6.0.10 255.255.255.0
!
interface Vlan80
ip address 10.8.0.10 255.255.255.0
!
interface Vlan90
ip address 10.9.0.10 255.255.255.0
!
interface Vlan210
description 2961-DOMAIN
ip address 10.2.10.1 255.255.255.0
!
interface Vlan212
description 2961-DNS
ip address 10.2.12.1 255.255.255.0
!
interface Vlan220
ip address 10.2.20.1 255.255.255.0
!
interface Vlan230
description 2961-OPENHAB
ip address 10.2.30.1 255.255.255.0
!
interface Vlan250
description 2961-VISION
ip address 10.2.50.1 255.255.255.0
!
interface Vlan255
ip address 10.2.55.1 255.255.255.0
!
interface Vlan290
ip address 10.2.90.1 255.255.255.0
!
interface Vlan1505
description WLAN-------
ip address 192.168.5.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1510
description WLAN-B
ip address 192.168.10.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1520
description WLAN-S
ip address 192.168.20.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1530
description WLAN-W
ip address 192.168.30.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1540
description WLAN-WC
ip address 192.168.40.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1920
description Vlan1920
ip address 192.168.0.1 255.255.255.0
ip helper-address 10.0.0.1
!
interface Vlan1921
description Vlan1921
ip address 192.168.1.1 255.255.255.0
ip helper-address 10.0.0.1
!
router ospf 1
router-id 10.2.0.1
redistribute connected subnets
redistribute static subnets
network 10.0.0.0 0.0.0.255 area 0
network 10.2.0.0 0.0.255.255 area 0
network 10.5.0.0 0.0.255.255 area 0
network 10.6.0.0 0.0.255.255 area 0
network 10.8.0.0 0.0.255.255 area 0
network 10.9.0.0 0.0.255.255 area 0
network 192.168.0.0 0.0.255.255 area 0
!
ip default-gateway 10.0.0.1
!
no ip ftp passive
ip ftp username c2961
ip ftp password 7 -----------
no ip http server
ip http banner
ip http authentication local
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 10.0.0.1
ip ssh client algorithm encryption aes128-cbc aes128-ctr aes192-cbc aes192-ctr aes256-cbc aes256-ctr
!
ip access-list standard LogIn
-------
!
ip access-list extended LTE-M-1
permit ip host 10.0.0.66 any
ip access-list extended TEST
permit ip any host 10.0.10.10
ip access-list extended dns-block
deny tcp any any eq domain
deny udp any any eq domain
permit ip any any
ip access-list extended test
permit ip host 10.2.12.10 any
logging source-interface Vlan20
logging host 10.9.0.1
!
!
route-map test permit 5
match ip address test
set ip next-hop 10.21.0.1
!
route-map test permit 10
match ip address test
set ip next-hop 10.0.0.8
!
route-map LTE-MAP permit 5
match ip address LTE-M-1
set ip next-hop 10.0.0.9
!
snmp-server group grp1 v3 priv read ViewDefault
snmp-server view ViewDefault iso included
snmp mib flash cache
banner login authorized users only, violaters will be remote electrocuted!!!
banner motd authorized users only, violaters will be shot on sight!
alias exec xwr copy run ftp://10.0.0.6/c2960x/
!
line con 0
exec-timeout 30 0
logging synchronous
login
length 50
stopbits 1
line vty 0 4
access-class LogIn in
exec-timeout 30 0
logging synchronous
login local
length 50
transport input ssh
line vty 5 15
login
transport input ssh
!
!
monitor session 1 source vlan 1621 , 1624
monitor session 1 destination interface Gi1/0/28
ntp server 10.1.1.1
event manager environment _email_to ----------
event manager environment _email_from admin@-----.com
event manager environment _email_server apikey:-------
event manager applet ssh-login
event syslog pattern "SEC_LOGIN.*"
action 1.0 mail server "$_email_server" to "$_email_to" from "$_email_from" subject "$_event_pub_time: c2960x Login via SSH" body "$_syslog_msg"
action 1.5 syslog priority notifications msg "SSH LOGIN - Mail Sent"
!
end- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 06:20 PM
version 16.9
no service pad
service timestamps debug datetime msec localtime show-timezone year
service timestamps log datetime msec localtime show-timezone year
service password-encryption
service internal
service sequence-numbers
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform hardware throughput crypto 150000
!
hostname c1111
!
boot-start-marker
boot system flash bootflash:c1100-universalk9_ias.16.09.06.SPA.bin
boot-end-marker
!
!
logging buffered 163840
logging persistent url bootflash:/logs/ size 819200 filesize 16384 batch 8192
enable secret 9 ----------
!
aaa new-model
!
!
aaa authorization network IKEv2_GROUP_AUTHZ local
!
aaa session-id common
clock timezone ---- 1 0
!
ip name-server 10.2.12.10 10.2.12.11
ip domain name -----.com
ip ddns update method control
HTTP
add http:----------
interval maximum 0 0 5 0
!
ip ddns update method -----com
HTTP
add http:----------
interval maximum 0 0 5 0
!
ip dhcp subscriber-id interface-name
ip dhcp excluded-address 192.168.0.1 192.168.0.80
!
login on-failure log
login on-success log
!
subscriber templating
!
multilink bundle-name authenticated
!
crypto pki server VPN_CA
no database archive
grant auto
eku server-auth client-auth
!
crypto pki trustpoint VPN_CA
revocation-check crl
rsakeypair VPN_CA
!
crypto pki trustpoint VPNSERVERCERT
enrollment url http://10.0.0.1:80
subject-name CN=-----------.buzz
revocation-check none
rsakeypair VPNSERVERCERT
!
crypto pki trustpoint -----ROOT
enrollment mode ra
enrollment url http://ca.----.com:80/certsrv/mscep/mscep.dll
fqdn c1111.-----.com
subject-name CN=c1111.----.com,O=------,OU=CORE DEVICE
subject-alt-name c1111.-----.com
revocation-check none
rsakeypair c1111
!
!
!
crypto pki certificate map CERT_MAP 10
name co -----
issuer-name co -----
!
crypto pki certificate chain VPN_CA
certificate ca 01
------ 8FDF3C09
quit
crypto pki certificate chain VPNSERVERCERT
certificate 02
------ E74DCF78
quit
certificate ca 01
------8FDF3C09
quit
crypto pki certificate chain -----ROOT
certificate ca 57974CA27C5------
------ D9
quit
!
archive
path flash:/ConfBack/
maximum 13
write-memory
time-period 1440
!
diagnostic bootup level complete
!
spanning-tree extend system-id
mac address-table aging-time 0
errdisable recovery cause psecure-violation
errdisable recovery interval 30
!
username --- secret 9 -------------
username --- privilege 15 secret 9 -----------
!
redundancy
mode none
!
crypto ikev2 authorization policy IKEv2_AUTHZ_POLICY
pool VPNPOOL
dns 10.2.12.10 10.2.12.11
netmask 255.255.255.0
def-domain -------
route set access-list split_tunel
!
crypto ikev2 proposal default
encryption aes-cbc-256 aes-cbc-192 aes-cbc-128
integrity sha512 sha384 sha256
group 21 20 14 19
!
crypto ikev2 policy default
match fvrf any
proposal default
!
!
crypto ikev2 profile IKEv2_PROFILE
match certificate CERT_MAP
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint VPNSERVERCERT
pki trustpoint ------ROOT
aaa authorization group cert list IKEv2_GROUP_AUTHZ IKEv2_AUTHZ_POLICY
virtual-template 1
reconnect timeout 900
!
no crypto ikev2 http-url cert
!
controller Cellular 0/2/0
no lte gps enable
lte modem link-recovery rssi onset-threshold -110
lte modem link-recovery monitor-timer 20
lte modem link-recovery wait-timer 10
lte modem link-recovery debounce-count 6
!
!
vlan internal allocation policy ascending
!
track 1 ip sla 1 reachability
!
!
class-map match-all LTE_Priority_Traffic
match access-group 101
class-map match-all test_match
!
policy-map LTE_Child
class LTE_Priority_Traffic
priority 10240
class class-default
fair-queue
policy-map LTE-Yettel-Primery
class class-default
fair-queue
fair-queue queue-limit 5
policy-map LTE_Parent
class class-default
shape average 10240000
service-policy LTE_Child
policy-map test_mark
class test_match
set ip dscp 1
!
!
!
crypto logging session
crypto logging ezvpn
crypto logging ikev2
!
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEv2_PROFILE
!
interface Loopback0
description NTP
ip address 10.1.1.1 255.255.255.255
ntp broadcast
!
interface Loopback1
description VPN
ip address 172.16.0.1 255.255.255.255
!
interface GigabitEthernet0/0/0
description WAN0
ip ddns update -----com
ip address dhcp
ip access-group VPN in
negotiation auto
!
interface GigabitEthernet0/0/1
ip address 10.21.0.1 255.255.255.0
no ip redirects
ip nat outside
negotiation auto
!
interface GigabitEthernet0/1/0
description -----
switchport access vlan 7
switchport mode access
!
interface GigabitEthernet0/1/1
description CON-c1111-c2961
switchport mode trunk
switchport port-security maximum 100
switchport port-security violation restrict
!
interface GigabitEthernet0/1/2
description -----
switchport access vlan 7
switchport mode access
switchport port-security maximum 25
switchport port-security violation restrict
!
interface GigabitEthernet0/1/3
description SXT01
switchport access vlan 70
switchport mode access
!
interface Cellular0/2/0
description LTE
ip ddns update control
ip address negotiated
ip nat outside
ip access-group VPN in
load-interval 30
history BPS all
dialer in-band
dialer watch-group 1
pulse-time 1
ip virtual-reassembly
ip virtual-reassembly-out
!
interface Cellular0/2/1
description LTE 2
no ip address
!
interface Virtual-Template1 type tunnel
description Cisco AnyConnect IKEv2
ip unnumbered Loopback1
ip mtu 1400
ip tcp adjust-mss 1360
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
!
interface Vlan1
description OFF
no ip address
ip nat inside
!
interface Vlan7
description Vlan7
ip address 10.0.0.1 255.255.255.0
ip nat inside
ip policy route-map LTE-MAP
!
interface Vlan11
ip address 10.0.1.2 255.255.255.0
ip nat inside
!
interface Vlan70
ip address 10.7.0.10 255.255.255.0
ip nat inside
!
interface Vlan80
ip address 10.8.0.254 255.255.255.0
ip nat inside
!
interface Vlan123
ip address 10.123.0.1 255.255.255.0
ip nat outside
!
interface Vlan666
no ip address
!
router ospf 1
router-id 10.0.0.1
redistribute connected subnets
redistribute static subnets
network 10.0.0.0 0.0.0.0 area 0
network 10.0.1.2 0.0.0.0 area 0
network 10.0.1.0 0.0.0.255 area 0
network 10.0.0.0 0.0.255.255 area 0
network 10.1.1.1 0.0.0.0 area 0
network 10.7.0.10 0.0.0.0 area 0
network 10.7.0.0 0.0.0.255 area 0
network 10.99.2.1 0.0.0.0 area 0
network 10.99.99.1 0.0.0.0 area 0
!
ip local policy route-map router_local
ip local pool VPNPOOL 172.16.0.101 172.16.0.103
ip forward-protocol nd
no ip ftp passive
ip ftp username -----
ip ftp password 7 -----
no ip http server
ip http authentication local
no ip http secure-server
ip dns server
ip nat translation timeout 300
ip nat translation tcp-timeout 300
ip nat translation udp-timeout 300
ip nat translation finrst-timeout 60
ip nat translation syn-timeout 60
ip nat translation dns-timeout 60
ip nat translation icmp-timeout 60
ip nat inside source static tcp 172.16.200.200 2222 interface Cellular0/2/0 22
ip nat outside source static 10.2.12.10 10.21.0.10 add-route
ip nat outside source static 10.2.12.15 10.21.0.20 add-route
ip route 0.0.0.0 0.0.0.0 Cellular0/2/0
ip ssh version 2
ip ssh client algorithm encryption aes128-cbc aes128-ctr aes192-cbc aes192-ctr aes256-cbc aes256-ctr
!
!
ip access-list standard LogIn
-----
ip access-list standard split_tunel
permit 10.0.0.0 0.255.255.255
permit 172.16.0.0 0.0.255.255
permit 192.168.0.0 0.0.255.255
!
ip access-list extended LTE-M-1
permit ip 192.168.5.0 0.0.0.255 any
deny ip 10.12.34.0 0.0.0.255 any
deny ip host 10.2.0.10 any
deny ip host 10.2.0.20 any
deny ip host 10.2.0.100 any
deny ip any 192.168.0.0 0.0.255.255
deny ip any 172.16.0.0 0.15.255.255
deny ip any 10.0.0.0 0.255.255.255
permit ip 10.0.0.0 0.255.255.255 any
ip access-list extended LTE-M-2
permit ip host 10.2.90.10 any
ip access-list extended NAT-L
deny ip any any
ip access-list extended VPN
permit object-group PORT_VPN any any log-input
permit ip any any
ip access-list extended router_local
permit ip host 10.7.0.10 host 1.1.1.1
!
ip sla 1
icmp-echo 1.1.1.1 source-interface Vlan70
ip sla schedule 1 life forever start-time now
ip sla 2
icmp-echo 10.2.0.1
ip sla schedule 2 life forever start-time now
ip sla 7
icmp-echo 10.7.0.1
ip sla schedule 7 life forever start-time now
ip sla 8
icmp-echo 10.8.0.1
ip sla schedule 8 life forever start-time now
logging source-interface Vlan7
logging host 10.9.0.1
dialer watch-list 1 ip 8.8.8.8 0.0.0.0
dialer watch-list 1 delay route-check initial 60
dialer watch-list 1 delay connect 1
dialer-list 1 protocol ip permit
!
!
!
menu Base text 1. .LTE Radio.
menu Base command 1. show cellular 0/2/0 radio
menu Base options 1. pause
menu Base text 2. .View SMS.
menu Base command 2. cellular 0/2/0 lte sms view summary
menu Base options 2. pause
menu Base text 3. .Interface Brief.
menu Base command 3. show ip interface brief
menu Base options 3. pause
menu Base text 4. .DHCP Bindings.
menu Base command 4. show ip dhcp binding
menu Base options 4. pause
menu Base text 5. .Show Run.
menu Base command 5. show run
menu Base options 5. pause
menu Base text 6. .ping.
menu Base command 6. ping 8.8.8.8
menu Base options 6. pause
menu Base text 7. .pingggg.
menu Base command 7. ping 8.8.8.8 rep 250
menu Base options 7. pause
menu Base text 8. policy
menu Base command 8. sh policy-map interface
menu Base options 8. pause
menu Base text 9. lte RESET
menu Base command 9. test cellu 0/2/0 modem-power-cycle
menu Base options 9. pause
menu Base text q .End Menu.
menu Base command q menu-exit
menu Base default q
route-map LTE-MAP permit 1
match ip address LTE-M-2
set ip next-hop 10.8.0.1
!
route-map LTE-MAP permit 5
match ip address LTE-M-1
set ip next-hop 10.7.0.1
!
route-map router_local permit 10
match ip address router_local
set ip next-hop 10.7.0.1
!
snmp-server group grp1 v3 priv read ViewDefault
snmp-server view ViewDefault iso included
!
!
!
!
control-plane
!
banner login authorized users only, violaters will be remote electrocuted!!!
banner motd authorized users only, violaters will be shot on sight!
alias exec xsms cellular 0/2/0 lte sms view summary
alias exec x menu Base
alias exec xib show ip interface brief
alias exec xr show cellular 0/2/0 radio
alias exec xd show ip dhcp binding
alias exec xwr copy run ftp://10.0.0.6/c1111/
default-value special-character-bits 8
!
line con 0
exec-timeout 30 0
password 7 ---------
logging synchronous
length 50
width 250
transport input none
stopbits 1
line vty 0 4
access-class LogIn in
exec-timeout 30 0
length 50
width 250
transport input ssh
line vty 5 20
access-class LogIn in
exec-timeout 30 0
length 50
width 250
transport input ssh
!
ntp master
ntp server 0.europe.pool.ntp.org
!
end- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 06:26 PM
this is the ip i want to redirect or some other from this subnet
interface GigabitEthernet0/0/1 ip address 10.21.0.1 255.255.255.0 no ip redirects ip nat outside negotiation auto
and here it connects to the 2960
interface GigabitEthernet1/0/4 no switchport ip address 10.21.0.2 255.255.255.0
this is just testing i tryed whit inside / outside swaping the ips ....
ip nat outside source static 10.2.12.10 10.21.0.10 add-route ip nat outside source static 10.2.12.15 10.21.0.20 add-route
the ip to wich i want to redirect is connected to the 2960
chuse any you like
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide