- Cisco Community
- Technology and Support
- Networking
- Routing
- Structuring a DMZ into existing network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2011 10:24 AM - edited 03-04-2019 01:49 PM
Hello Community,
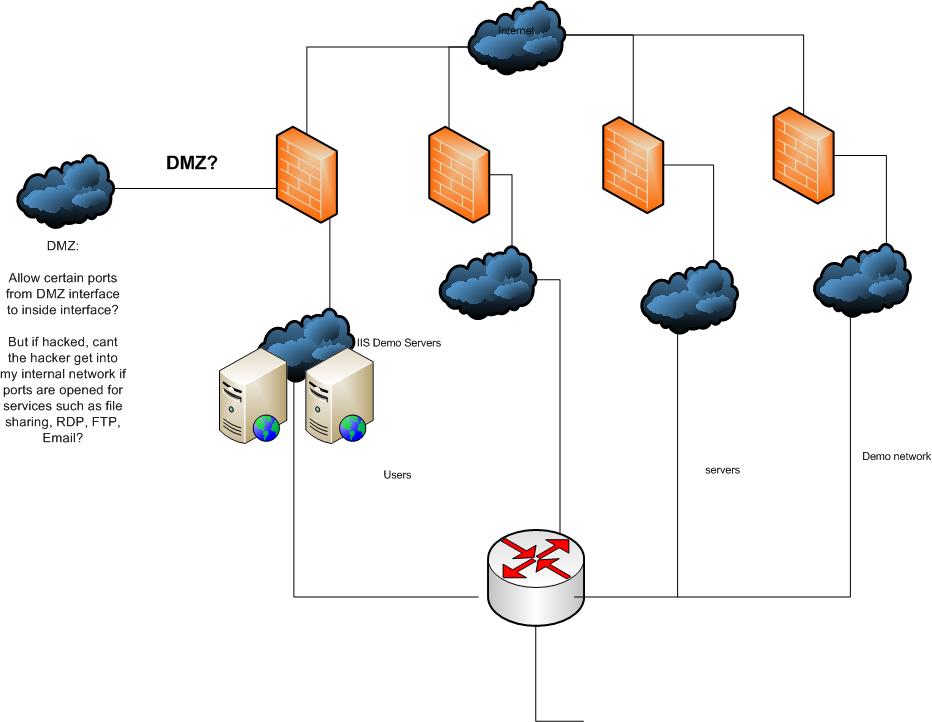
I am thinking of introducing a DMZ to my network.
My current web servers are located behind the firewall using port forwarding. I have about 20 of them. These servers host demo products of software. They are accessed by our internal employees like RDP, file sharing etc.
I was thinking of dedicating a NIC on my Cisco ASA firewall and calling it a DMZ. Then move these 20 web servers to that new network.
What do you think of this? Is this normal? How would users access these servers to work on them? Also some of these servers need communication to internal server such as Exchange, FTP, Domain Controllers and File Shares. How would this traffic be allowed?
Sorry for all the questions on how I should properly (securly) setup my network.
Thanks
Ian
Below is my environment, off to the left side is where I would dedicate a NIC on my ASA firewall to be the DMZ, then regulate the traffic to my other inside NIC. I know I would have to open ports for file sharing, FTP, Domain, Email and RDP. So is it secure if a hacker breaks into a DMZ machine if all these ports are opened? Is this a waste of time for a little added security? I just want to know what is the best for this setup.
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2011 03:15 PM
Hi there
The use of DMZ is a good approach in terms of separation and zoning between different networks and allow only the required traffic to pass through the firewall but this is depends on your network security needs and policies
If hacker got access to server in DMZ with limited number of ports permited better than hacking a server in your internal network with full reachabity so it is relatively more secure way
Also you need to think about nating, acl and other factors fir communications between different interfaces of the firewall
Bellow is a link to several example that you can read and use as a reference
http://www.cisco.com/en/US/products/ps6120/prod_configuration_examples_list.html
Hope this help
If helpful rate
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2011 03:15 PM
Hi there
The use of DMZ is a good approach in terms of separation and zoning between different networks and allow only the required traffic to pass through the firewall but this is depends on your network security needs and policies
If hacker got access to server in DMZ with limited number of ports permited better than hacking a server in your internal network with full reachabity so it is relatively more secure way
Also you need to think about nating, acl and other factors fir communications between different interfaces of the firewall
Bellow is a link to several example that you can read and use as a reference
http://www.cisco.com/en/US/products/ps6120/prod_configuration_examples_list.html
Hope this help
If helpful rate
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2011 01:57 PM
Hello,
Thanks for your thoghts.
I agree that a DMZ is a good approach.
I bought an ASA router and want to use it for a DMZ. I have setup ethernet0/1 as the DMZ and want to transition my Watchguard's subnet over to the ASA router. I would have to make ethernet0/2 the new "watchguard" and slowly transition servers over to it.
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2011 02:34 PM
John
Just as an addition to this. Windows servers that use AD can be difficult to firewall properly. You end up having to open a lot of ports between your DMZ and inside. That doesn't mean you shouldn't do it because it is still good practice but be aware that any server you put in the DMZ that also needs access from internal clients or need to access internal file shares for example can still be vulnerable so just because they are in a DMZ you still need to secure them properly.
In addition the firewall may, and i say may, become a bottleneck in terms of filesharing from internal clients. Just something to keep an eye on. Like i say i think it is a good idea so not trying to put you off.
Also Microsoft do a number of good papers on deploying servers into a DMZ ie. they list the ports you need to open and can recommend more secure configurations where you do not necessarily need to open all the ports you would internally. Worth a look.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2011 02:37 PM
Thanks for the additional info Jon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2011 03:21 PM
In regards to Microsoft AD, Jon is right. Also you would have some antivirus servers that get updates from the internet and send it across internally. The way you can easily do this is by putting some Read Only servers(Antivirus update server, AD,DOM) into a DMZ and call is Services DMZ and then run tunnels from them to the real servers . I have deployed this in an environment and it seems to work perfectlly and its secure too. Let me know if you want more info on this
HTH.
Rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2011 06:06 AM
Sure I would like info on this, I would have to join these servers to the domain. As for the Antivirus, I would have ESET just go out to the internet for its updates. But the AD stuff is the tricky part. RDP, File transfers, POP, SMTP, SNMP I guess would be the easy stuff to open up between DMZ and LAN.
I guess I would need the tunnels from the DMZ to the AD servers? Does this just act a bypass insead of opening up ports using ACLs?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide