- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Trouble Routing VLANs through L2 and L3 Switches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Trouble Routing VLANs through L2 and L3 Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2019 06:44 PM - edited 11-04-2019 06:46 PM
Hello All,
Having trouble trying to figure out how to get VLANs to talk to each other. I have a L2 switches 3750G and a L3 switch 3750G with IP Routing enabled. I have been testing this out in Cisco Packet Tracer, but have been trying things as well with a test environment when I can.
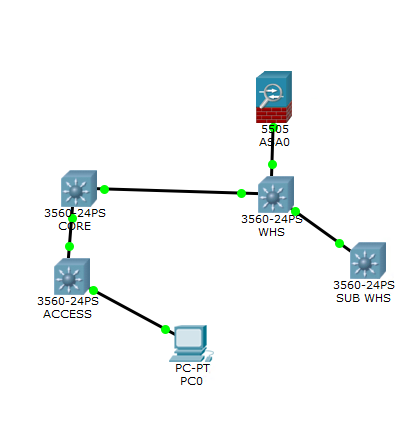
Here is a quick and dirty version of the network I am testing.
There are a couple VLANs
VLAN 1 - 192.168.99.0
VLAN 20 - 192.168.20.0
The PC sits on VLAN 1 and can ping any switch on it's network. The PC can also ping any VLAN on the L2 switch it is connected to. But it cannot ping the next hop on a different VLAN 192.168.20.251. (Can ping VLAN1 on the next hop though). Core is a L3 switch and the WHS under the ASA is a L3. CLI is below
I appreciate any insight.
ACCESS 3560-24PS#show run Building configuration... Current configuration : 1970 bytes ! version 12.2 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname Switch ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! spanning-tree mode pvst ! ! ! ! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 description 2ND FLOOR OFFICE FIBER switchport trunk allowed vlan 1,10,20,30,98 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet0/2 ! interface Vlan1 description User Network ip address 192.168.99.1 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan10 description Internet Peering Network mac-address 000a.4176.dd01 ip address 192.168.10.2 255.255.255.0 ! interface Vlan20 description Server Network mac-address 000a.4176.dd02 ip address 192.168.20.1 255.255.255.0 ! interface Vlan30 description Camera Network mac-address 000a.4176.dd03 ip address 192.168.30.1 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan98 description Guest Network mac-address 000a.4176.dd04 ip address 192.168.98.1 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! ip classless ! ip flow-export version 9 ! ! ! ! ! ! ! line con 0 ! line aux 0 ! line vty 0 4 login ! ! ! end
CORE SWITCH: show run Building configuration... Current configuration : 2527 bytes ! version 12.2 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname Switch ! ! ! ! ! ! ! ip routing ! ! ! ! ! ! ! ! ! ! ! ! ip ssh version 2 ip domain-name airinnovationsllc.local ip name-server 192.168.20.17 ! ! spanning-tree mode pvst ! ! ! ! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 description 2ND FLOOR OFFICE FIBER switchport trunk allowed vlan 1,10,20,30,98 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet0/2 description 2ND FLOOR OFFICE FIBER switchport trunk allowed vlan 1,10,20,30,98 switchport trunk encapsulation dot1q switchport mode trunk ! interface Vlan1 description User Network ip address 192.168.99.5 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan10 description Internet Peering Network mac-address 00d0.bc1c.c601 ip address 192.168.10.3 255.255.255.0 ! interface Vlan20 description Server Network mac-address 00d0.bc1c.c602 ip address 192.168.20.251 255.255.255.0 ! interface Vlan30 description Camera Network mac-address 00d0.bc1c.c603 ip address 192.168.30.5 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan40 description Phone Network mac-address 00d0.bc1c.c604 ip address 192.168.40.2 255.255.255.0 ! interface Vlan98 description Guest Network mac-address 00d0.bc1c.c605 ip address 192.168.98.4 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! ip classless ip route 192.168.20.0 255.255.255.0 192.168.20.254 ip route 192.168.99.0 255.255.255.0 192.168.99.3 ip route 192.168.30.0 255.255.255.0 192.168.30.2 ip route 192.168.98.0 255.255.255.0 192.168.98.3 ! ip flow-export version 9 ! ! ! ! ! ! ! line con 0 ! line aux 0 ! line vty 0 4 login ! ! ! end
WHS 3560#show run Building configuration... Current configuration : 2192 bytes ! version 12.2 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname Switch ! ! ! ! ! ! ! ip routing ! ! ! ! ! ! ! ! ! ! ! ! ip domain-name airinnovationsllc.local ! ! spanning-tree mode pvst ! ! ! ! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 description Fiber Link switchport trunk allowed vlan 1,10,20,30 switchport trunk encapsulation dot1q switchport mode trunk ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 description 2ND FLOOR OFFICE FIBER switchport trunk allowed vlan 1,10,20,30,98 switchport trunk encapsulation dot1q switchport mode trunk ! interface Vlan1 description User Network ip address 192.168.99.3 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan10 description Internet Peering Network mac-address 000c.858e.d201 ip address 192.168.10.254 255.255.255.0 ! interface Vlan20 description Server Network mac-address 000c.858e.d202 ip address 192.168.20.254 255.255.255.0 ! interface Vlan30 description Camera Network mac-address 000c.858e.d203 ip address 192.168.30.2 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! interface Vlan98 description Guest Network mac-address 000c.858e.d204 ip address 192.168.98.3 255.255.255.0 ip helper-address 192.168.20.16 ip helper-address 192.168.20.17 ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.10.1 ! ip flow-export version 9 ! ! ! ! ! ! ! line con 0 ! line aux 0 ! line vty 0 4 login ! ! ! end
- Labels:
-
LAN Switching
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2019 11:39 PM
Hi there,
Is the PC using 192.168.99.1 as its default gateway? If so you need to add:
! ip routing !
..to '3560-24Ps ACCESS', this will allow packets to be forwarded between the local SVIs and then routed towards an SVI on an adjacent switch.
Personally I suggest that if you want this routed access layer design, that you limit the broadcast domain of a the access VLANs to the access switch itself. Create a VLAN with a /30 subnet and use that as a point to point link between the neighbouring switch. Remove the other VLANs from the trunk and either run a dynamic routing protocol between the switches or configure static routes.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 05:22 AM
Can the original poster give us the output of show ip interface brief from each of the switches?
Can the original poster give us the IP address, mask, and default gateway configured on the PC?
I see interfaces configured as trunks with multiple vlans permitted and I see vlan interfaces with IP addresses. But I do not see any access interface assigned to any vlan other than vlan 1. Is that intentional?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 05:50 AM
@Seb Rupik wrote:Personally I suggest that if you want this routed access layer design, that you limit the broadcast domain of a the access VLANs to the access switch itself. Create a VLAN with a /30 subnet and use that as a point to point link between the neighbouring switch. Remove the other VLANs from the trunk and either run a dynamic routing protocol between the switches or configure static routes.
Thanks for the info. I was under the assumption if the Default gateway of the PC was the Layer 2 VLAN on the access, it would route the packet to the next hop and then route to the appropriate vlan it is trying to send a packet to. Adding the Default gateway of the PC to CORE allowed me to route packets to any VLAN like you suggested.
Also, for what your suggesting, the ACCESS switch would need to be in LAYER3 routing mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 05:59 AM
You could use the access switch SVI at the gateway, but you need to enable ip routing on it. That is why using the CORE SVI as the gateway works.
For the routed access layer solution to work, you will need to firstly enable ip routing and then add routes to the routing table either via IGP or statically. Arguably the routed access design would work fine with your current trunked VLAN configuration, but to be correct you will want to remove all existing VLANs from the trunk link and create a new /30 subnet to be used for IGP peering and transit traffic between itself and the upstream switch.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 06:30 AM
@Seb Rupik wrote:
Arguably the routed access design would work fine with your current trunked VLAN configuration, but to be correct you will want to remove all existing VLANs from the trunk link and create a new /30 subnet to be used for IGP peering and transit traffic between itself and the upstream switch.
I want to make sure I understand this correctly. But your suggesting I create a new VLAN and subnet purely for the trunk between the core and access. Then route all traffic through that new vlan? What benefit does this provide? I though having IP Routing enabled (InterVLAN) takes away the need for static and dynamic routing protocols. So that would seem redundant correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 02:26 PM
I only suggested a routed access design as that is what your original configuration appeared to be trying to achieve, ie, you had SVIs for all of the VLANs present on the access switch.
A 'standard' 2/3 tier design keeps the Layer3 boundary off the access layer. This is achieved by not having any SVIs present (with the exception for management), instead VLANs exist only at Layer 2 and all traffic which needs to be routed is sent via Layer2 trunk links upstream to the distribution or core layer.
Regarding the benefits of a routed access layer, take a look at this document:
cheers,
Seb.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide