- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: VRRP with re-routing inter-vlan traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VRRP with re-routing inter-vlan traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020 08:59 AM
Hi
My scenario is that I have two switches in DC configured with VRRP. Those two switches provide resilient connection to another switch in another building.
I also have two firewalls above the two VRRP switches.
routing
I would like to still make use of the VRRP feature and somehow stop inter-vlan routing on VRRP switches and re-route all traffic to firewalls to apply policies and then come back down.
I understand I introduce extra hops with this and I can achieve this by only using L2 or VPC or even using ACLs at the switch level but I was wondering if there is a way to still use VRRP feature but send all traffic up to the firewall to control the traffic and come back down.
Thanks
- Labels:
-
LAN Switching
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020 09:43 AM - edited 05-15-2020 09:43 AM
Hi,
I have the exactly same trouble in my previous environment. ACL is so hard to manage and we would like to migrate the access control to firewall instead.
But technically, we could not do it like what you say. All VLANs are sharing the same routing domain (or VRF), your core switch should have exactly 1 exit point (the directly connected route) to either VLAN. If you force it to route to firewall, then firewall route it back to core switch. It will introduce a routing loop.
To migrate the access control to firewall, you still have some options to choose:
Option 1. Migrate the SVI/gateway to the firewall
Simple solution, but you got to check out if your firewall could provide enough throughput for your business operation.
Option 2. Separate VLANs on Core Switch into different VRFs. In each VRFs, route the traffic to firewall.
Extremely complex when there are large number of VLANs. Not recommended, but it's still a solution.
Option 3. Configure your firewall into a transparent mode, so that it could inspect all layer 2 traffic.
This is the simplest solution, but not scalable. It's might not compatible to your existing design.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020 10:02 AM - edited 05-15-2020 10:03 AM
Option 4 (Just for FUN). Make use of DSCP to identify whether the packet had inspected by firewall or not. Then use PBR to route it to either Firewall or to VLAN directly.
Logic is simple:
a. DSCP for all incoming packet from VLANs are reset to 0
b. DSCP for all packet passing to Firewall are set to non-zero (e.g. AF31)
c. PBR - If DSCP = 0, pass to Firewall.
interface Ethernet0/1 description To Firewall ip address 192.168.254.254 255.255.255.252 service-policy output DSCP-AF31 end interface Ethernet0/2 description To VLAN ip address 192.168.1.1 255.255.255.0 ip policy route-map ROUTE-TO-FIREWALL service-policy input RESET-DSCP interface Ethernet0/0 description To VLAN ip address 192.168.0.1 255.255.255.0 ip policy route-map ROUTE-TO-FIREWALL service-policy input RESET-DSCP route-map ROUTE-TO-FIREWALL permit 10 match ip address DSCP-0 set ip next-hop 192.168.254.253 policy-map DSCP-AF31 class class-default set dscp af31 policy-map RESET-DSCP class class-default set dscp default
ip access-list extended DSCP-0
permit ip any any dscp 0
I have tested it on GNS3 and it works. But again, this is just for fun, and not recommended to use it on production.
No body would like to manage a network like this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 05:23 AM
I'm glad I'm not the only one with this issue.
Trouble is I have around 50 buildings and want them to have two connections (one to each DC) using VRRP for failover.
I was thinking just using VPC across the DCs and then VPC each building (one connection to each DC). That way I can have the gateways on the firewalls which are 40g beasts.
However not sure if VPC is a good approach for that number of buildings/switches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 06:28 AM
Hi,
Centralizing 50 building's network gateway into firewall will introduce much loading to your firewall. Imagine the inter-vlan traffic originally handled by your Nexus switch (depend on model, usually can handle over 100 Gbps), now migrate to firewall which usually have much lower throughput (depend on model, and if NGFW feature enabled, it will be even slower) might downgrade your overall network throughput.
For your second question, I can't comment tat much as I don't know what model you have got, how many of them you have.
But in general, vPC is a not a bad solution, make sure you have enough resilience & throughput of the across DCs circuit. For example, at least 2 across DC circuits with 1G/10G CIR.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 01:48 PM
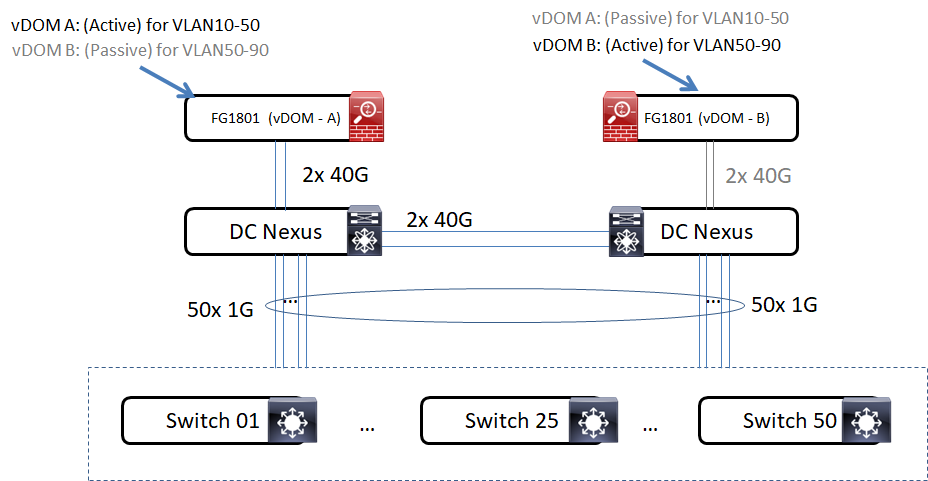
@ngkin2010 they are Fortis 1800 so 2 x 40g bond down to switches per DC and then 2 x 40g VPC between DCs/switches. Then 1g VPC from each DC to a building switch. That should do it right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 07:55 PM
Hi,
Not sure if you are meaning FortiGate 1800f at the top, and you are planning to migrate SVI to the FortiGate 1800.
Are they 2 in HA (active-passive) mode? or standalone mode?
You have got 2x 40G across DC fibers for vPC, are they used as peer link? how about the keepalive link?
And it's hard to comment without these information, and better draw it out on a network diagram for further discussion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2020 05:00 AM
2 x HA Active-Pasive FG 1801e at top with two 40g downlinks to one nexus in each DC.
Then 2 x VPC 40g peer links and 2 x 1g keep alives between DCs.
Was thinking two nexuses per DC but not sure how that would work with VPC as in two VPC'ed nexuses in each DC and then another VPC between DCs. Guess that is asking for loops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2020 06:32 AM - edited 05-17-2020 06:37 AM
Was thinking two nexuses per DC but not sure how that would work with VPC as in two VPC'ed nexuses in each DC and then another VPC between DCs. Guess that is asking for loops.
You may read about the document which describe DCI for 2 Nexus in each DC.
2 x HA Active-Pasive FG 1801e at top with two 40g downlinks to one nexus in each DC.
Then 2 x VPC 40g peer links and 2 x 1g keep alives between DCs.
I assume you are talking about FortiGate 1801F. According to the official datasheet, the throughput is around 140Gbps to 190 Gbps. Make sure you don't enable NGFW feature for inter-vlan taffic, otherwise the throughput will dramatically drop to 11 Gbps or even slower.
You have got a high-end ForitGate device, I think it could handle the inter-vlan traffic well.
Depending on the actual loading (as well as you upstream network design), you may also consider to load share your gateways to both FortiGate by separated vDOM. However, the traffic across vDOM may have longer forwarding path (FG -> NX -> NX -> FG). That's the trade off.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2020 10:28 AM
@ngkin2010 you were a great help buddy. Thank you.
The Forti active active only gives an advantage for the UTM stuff. I'm happy with active passive for Fortis and have primary VPC switch where active Forti is so 40g inter-vlan traffic is plenty.
I believe the passive Forti still passes traffic to active in case the primary nexus goes. But I'm going to have to test that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2020 11:44 AM
Hello
We dont know at this time how your network is setup, it sounds like the FW is performing the inter-vlan routing or traffic s getting routed up-towards the fw for some policy inspection etc...
Can you post a topology diagram and maybe elaborate a bit more on your network
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2020 05:14 AM
Hi Paul
Currently the inter-vlan routing is done at the switch level where all the SVIs are configured. What I'm trying to get to is to make use of VRRP using SVIs across two DCs but I want to control the policies at the firewall level.
With the current set up all the routing is done on switches and all traffic is allowed between SVIs at switch level.
Basically I would like the VRRP gateways on the switches but then traffic between vlans to be routed up via firewall then back down to control the policies. Hope that makes sense.
DC1 DC2
Firewall1 <----> Firewall2
| |
| |
Switch1 <--VRRP--> Switch2
\ /
\ /
\ /
SwitchN
Thanks @paul driver
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide