- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SDWAN lab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2021 06:59 PM
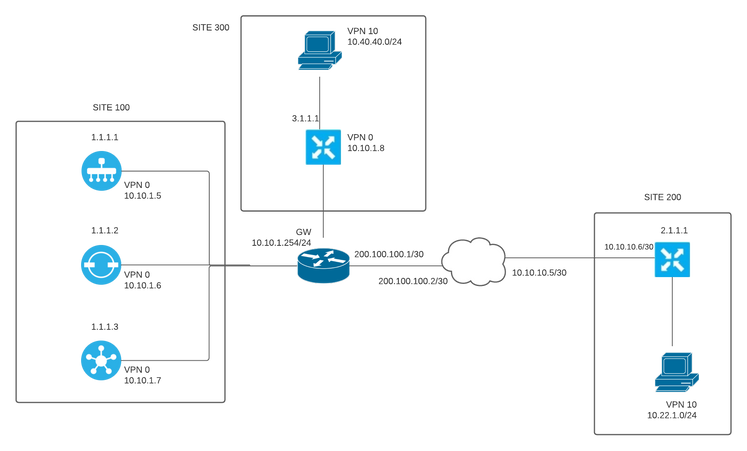
I have been playing with sdwan in eve-ng with the topology below. I already bring up the tunnels and can see both sites up to vpn0 from each other. still getting use to and practicing with templates but i really having difficulties in how to send the service vpn through the overlay, for ex. connecting site 300 service vpn 10 with site 200 service vpn 10
- Labels:
-
SD-WAN Infrastructure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 07:35 AM
Hi!
Can you share the next outputs from both edges?
#show control connections
#show control local properties
#show bfd sessions
#show omp peers
#show omp tlocs
#show omp routes
#show bfd tloc-summary-list
Customer Success Specialist (SD-WAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 07:49 AM
Well I was able to do it with an extranet policy in vsmart but is this the correct way ?
policy
lists
vpn-list client_vpn
vpn 10
!
vpn-list transport_vpn
vpn 0
!
site-list all_sites
site-id 100
site-id 200
site-id 300
!
!
control-policy extranet
sequence 10
match route
vpn-list client_vpn
!
action accept
export-to
vpn-list transport_vpn
!
!
!
sequence 20
match route
vpn-list transport_vpn
!
action accept
export-to
vpn-list client_vpn
!
!
!
default-action accept
!
!
apply-policy
site-list all_sites
control-policy extranet inthis is the output but the policy is in place already
show omp peers
R -> routes received
I -> routes installed
S -> routes sent
DOMAIN OVERLAY SITE
PEER TYPE ID ID ID STATE UPTIME R/I/S
------------------------------------------------------------------------------------------
1.1.1.2 vsmart 1 1 100 up 1:22:02:26 3/1/1 show control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT LOCAL COLOR PROXY STATE UPTIME ID
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.1.2 100 1 10.10.1.7 12446 10.10.1.7 12446 public-internet No up 0:22:31:14 0
vbond dtls 0.0.0.0 0 0 10.10.1.6 12346 10.10.1.6 12346 public-internet - up 0:22:31:32 0
vmanage dtls 1.1.1.1 100 0 10.10.1.5 12446 10.10.1.5 12446 public-internet No up 0:22:31:32 0show bfd sessions
SOURCE TLOC REMOTE TLOC DST PUBLIC DST PUBLIC DETECT TX
SYSTEM IP SITE ID STATE COLOR COLOR SOURCE IP IP PORT ENCAP MULTIPLIER INTERVAL(msec) UPTIME TRANSITIONS
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
3.1.1.1 300 up public-internet public-internet 10.10.10.6 10.10.1.8 12346 ipsec 7 1000 0:22:24:58 0show omp routes
Code:
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Inv -> invalid
Stg -> staged
IA -> On-demand inactive
U -> TLOC unresolved
PATH ATTRIBUTE
VPN PREFIX FROM PEER ID LABEL STATUS TYPE TLOC IP COLOR ENCAP PREFERENCE
--------------------------------------------------------------------------------------------------------------------------------------
0 10.22.1.0/24 1.1.1.2 3 1006 C,R installed 2.1.1.1 public-internet ipsec -
0 10.40.40.0/24 1.1.1.2 4 1003 C,R installed 3.1.1.1 public-internet ipsec -
10 10.22.1.0/24 0.0.0.0 69 1006 C,Red,R installed 2.1.1.1 public-internet ipsec -
10 10.40.40.0/24 1.1.1.2 2 1003 C,I,R installed 3.1.1.1 public-internet ipsec -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 07:59 AM
By default whenever there's no policy SD-WAN creates a full mesh fabric between all edges. Now your 2 sites have the same VPN 10 so there's no need to do route leaking with that inbound control policy. Plase remove the policy and gather the same outputs.
Regards
Customer Success Specialist (SD-WAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 09:45 AM
ok, there you go
show control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT LOCAL COLOR PROXY STATE UPTIME ID
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.1.2 100 1 10.10.1.7 12446 10.10.1.7 12446 public-internet No up 1:00:31:11 0
vbond dtls 0.0.0.0 0 0 10.10.1.6 12346 10.10.1.6 12346 public-internet - up 1:00:31:30 0
vmanage dtls 1.1.1.1 100 0 10.10.1.5 12446 10.10.1.5
12446 public-internet No up 1:00:31:30 0 show control local-properties
personality vedge
sp-organization-name MSI
organization-name MSI
root-ca-chain-status Installed
certificate-status Installed
certificate-validity Valid
certificate-not-valid-before Jan 11 15:14:39 2021 GMT
certificate-not-valid-after Jan 09 15:14:39 2031 GMT
dns-name 10.10.1.6
site-id 200
domain-id 1
protocol dtls
tls-port 0
system-ip 2.1.1.1
chassis-num/unique-id 553dd379-f093-2c2d-405d-83555f250481
serial-num EA45ED56
subject-serial-num N/A
token Invalid
keygen-interval 1:00:00:00
retry-interval 0:00:00:18
no-activity-exp-interval 0:00:00:20
dns-cache-ttl 0:00:02:00
port-hopped TRUE
time-since-last-port-hop 1:00:32:22
pairwise-keying Disabled
embargo-check success
cdb-locked false
number-vbond-peers 1
INDEX IP PORT
-----------------------------------------------------
0 10.10.1.6 12346
number-active-wan-interfaces 1
NAT TYPE: E -- indicates End-point independent mapping
A -- indicates Address-port dependent mapping
N -- indicates Not learned
Note: Requires minimum two vbonds to learn the NAT type
RESTRICT/ LAST VM
PUBLIC PUBLIC PRIVATE PRIVATE PRIVATE MAX CONTROL/ LAST SPI TIME NAT CON
INTERFACE IPv4 PORT IPv4 IPv6 PORT VS/VM COLOR STATE CNTRL STUN LR/LB CONNECTION REMAINING TYPE PRF
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
ge0/0 10.10.10.6 12386 10.10.10.6 :: 12386 1/1 public-internet up 2 no/yes/no No/No 0:00:00:08 0:11:27:37 N 5 show bfd sessions
SOURCE TLOC REMOTE TLOC DST PUBLIC DST PUBLIC DETECT TX
SYSTEM IP SITE ID STATE COLOR COLOR SOURCE IP IP PORT ENCAP MULTIPLIER INTERVAL(msec) UPTIME TRANSITIONS
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
3.1.1.1 300 up public-internet public-internet 10.10.10.6 10.10.1.8 12346 ipsec 7 1000 1:00:25:36 0 show omp peers
R -> routes received
I -> routes installed
S -> routes sent
DOMAIN OVERLAY SITE
PEER TYPE ID ID ID STATE UPTIME R/I/S
------------------------------------------------------------------------------------------
1.1.1.2 vsmart 1 1 100 up 2:00:05:51 1/1/1show omp tlocs
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Stg -> staged
IA -> On-demand inactive
Inv -> invalid
PUBLIC PRIVATE
ADDRESS PSEUDO PUBLIC PRIVATE PUBLIC IPV6 PRIVATE IPV6 BFD
FAMILY TLOC IP COLOR ENCAP FROM PEER STATUS KEY PUBLIC IP PORT PRIVATE IP PORT IPV6 PORT IPV6 PORT STATUS
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
ipv4 2.1.1.1 public-internet ipsec 0.0.0.0 C,Red,R 1 10.10.10.6 12386 10.10.10.6 12386 :: 0 :: 0 up
3.1.1.1 public-internet ipsec 1.1.1.2 C,I,R 1 10.10.1.8 12346 10.10.1.8 12346 :: 0 :: 0 up show omp routes
Code:
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Inv -> invalid
Stg -> staged
IA -> On-demand inactive
U -> TLOC unresolved
PATH ATTRIBUTE
VPN PREFIX FROM PEER ID LABEL STATUS TYPE TLOC IP COLOR ENCAP PREFERENCE
--------------------------------------------------------------------------------------------------------------------------------------
10 10.22.1.0/24 0.0.0.0 69 1006 C,Red,R installed 2.1.1.1 public-internet ipsec -
10 10.40.40.0/24 1.1.1.2 2 1003 C,I,R installed 3.1.1.1 public-internet ipsec -show bfd tloc-summary-list IF SESSIONS SESSIONS SESSIONS NAME ENCAP TOTAL UP FLAP -------------------------------------------- ge0/0 ipsec 1 1 4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 10:45 AM
I case see a couple of things here...
From the output below that the edge 2.1.1.1 has an IPsec tunnel UP with edge 3.1.1.1, so here we can assume that there's data plane active
show bfd sessions
SOURCE TLOC REMOTE TLOC DST PUBLIC DST PUBLIC DETECT TX
SYSTEM IP SITE ID STATE COLOR COLOR SOURCE IP IP PORT ENCAP MULTIPLIER INTERVAL(msec) UPTIME TRANSITIONS
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
3.1.1.1 300 up public-internet public-internet 10.10.10.6 10.10.1.8 12346 ipsec 7 1000 1:00:25:36 0
Can you gather the same outputs from the other edge?
Customer Success Specialist (SD-WAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 11:01 AM
yes, but weirdly enough after removing the policy from vsmart I still have access between sites. Maybe the policy insert routes and leave it there even when I already removed the policy I even restarted the vsmart and vEdges ?
show control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT LOCAL COLOR PROXY STATE UPTIME ID
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.1.2 100 1 10.10.1.7 12346 10.10.1.7 12346 public-internet No up 0:00:31:37 0
vbond dtls 0.0.0.0 0 0 10.10.1.6 12346 10.10.1.6 12346 public-internet - up 0:00:51:04 0
vmanage dtls 1.1.1.1 100 0 10.10.1.5 12346 10.10.1.5 12346 public-internet No up 0:00:51:03 0show control local-properties
personality vedge
sp-organization-name MSI
organization-name MSI
root-ca-chain-status Installed
certificate-status Installed
certificate-validity Valid
certificate-not-valid-before Jan 12 21:04:18 2021 GMT
certificate-not-valid-after Jan 10 21:04:18 2031 GMT
dns-name 10.10.1.6
site-id 300
domain-id 1
protocol dtls
tls-port 0
system-ip 3.1.1.1
chassis-num/unique-id 4bcae5f0-fd3d-d801-4065-602863ccbf93
serial-num EDF456A2
subject-serial-num N/A
token Invalid
keygen-interval 1:00:00:00
retry-interval 0:00:00:18
no-activity-exp-interval 0:00:00:20
dns-cache-ttl 0:00:02:00
port-hopped TRUE
time-since-last-port-hop 0:00:51:24
pairwise-keying Disabled
embargo-check success
cdb-locked false
number-vbond-peers 1
INDEX IP PORT
-----------------------------------------------------
0 10.10.1.6 12346
number-active-wan-interfaces 1
NAT TYPE: E -- indicates End-point independent mapping
A -- indicates Address-port dependent mapping
N -- indicates Not learned
Note: Requires minimum two vbonds to learn the NAT type
RESTRICT/ LAST VM
PUBLIC PUBLIC PRIVATE PRIVATE PRIVATE MAX CONTROL/ LAST SPI TIME NAT CON
INTERFACE IPv4 PORT IPv4 IPv6 PORT VS/VM COLOR STATE CNTRL STUN LR/LB CONNECTION REMAINING TYPE PRF
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
ge0/0 10.10.1.8 12366 10.10.1.8 :: 12366 1/1 public-internet up 2 no/yes/no No/No 0:00:00:16 0:11:28:01 N 5
show bfd sessions
SOURCE TLOC REMOTE TLOC DST PUBLIC DST PUBLIC DETECT TX
SYSTEM IP SITE ID STATE COLOR COLOR SOURCE IP IP PORT ENCAP MULTIPLIER INTERVAL(msec) UPTIME TRANSITIONS
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
2.1.1.1 200 up public-internet public-internet 10.10.1.8 10.10.10.6 12346 ipsec 7 1000 0:00:50:17 0show omp peers
R -> routes received
I -> routes installed
S -> routes sent
DOMAIN OVERLAY SITE
PEER TYPE ID ID ID STATE UPTIME R/I/S
------------------------------------------------------------------------------------------
1.1.1.2 vsmart 1 1 100 up 0:00:32:43 1/1/1 show omp tloc
Possible completions:
tloc-paths Display TLOC paths
tlocs Display TLOCs
vEdge-HQ# show omp tlocs
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Stg -> staged
IA -> On-demand inactive
Inv -> invalid
PUBLIC PRIVATE
ADDRESS PSEUDO PUBLIC PRIVATE PUBLIC IPV6 PRIVATE IPV6 BFD
FAMILY TLOC IP COLOR ENCAP FROM PEER STATUS KEY PUBLIC IP PORT PRIVATE IP PORT IPV6 PORT IPV6 PORT STATUS
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
ipv4 2.1.1.1 public-internet ipsec 1.1.1.2 C,I,R 1 10.10.10.6 12346 10.10.10.6 12346 :: 0 :: 0 up
3.1.1.1 public-internet ipsec 0.0.0.0 C,Red,R 1 10.10.1.8 12366 10.10.1.8 12366 :: 0 :: 0 up show omp routes
Code:
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Inv -> invalid
Stg -> staged
IA -> On-demand inactive
U -> TLOC unresolved
PATH ATTRIBUTE
VPN PREFIX FROM PEER ID LABEL STATUS TYPE TLOC IP COLOR ENCAP PREFERENCE
--------------------------------------------------------------------------------------------------------------------------------------
10 10.22.1.0/24 1.1.1.2 1 1003 C,I,R installed 2.1.1.1 public-internet ipsec -
10 10.40.40.0/24 0.0.0.0 69 1003 C,Red,R installed 3.1.1.1 public-internet ipsec -show bfd tloc-summary-list IF SESSIONS SESSIONS SESSIONS NAME ENCAP TOTAL UP FLAP -------------------------------------------- ge0/0 ipsec 1 1 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 11:44 AM
Can you gather these outputs on both edges?
#show ip route vpn 10
or #show ip route vrf 10 in case you are using cEdges
Customer Success Specialist (SD-WAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2021 10:24 AM
since there is no route leak, i am suppose to get to each other from vpn 10 ?
Ex. ping 10.40.40.x vpn 10
site 200
show ip routes vpn 10
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive, L -> import
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
---------------------------------------------------------------------------------------------------------------------------------------------
10 10.22.1.0/24 connected - ge0/1 - - - - - F,S
10 10.40.40.0/24 omp - - - - 3.1.1.1 default ipsec F,Ssite 300
show ip routes vpn 10
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive, L -> import
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
---------------------------------------------------------------------------------------------------------------------------------------------
10 10.22.1.0/24 omp - - - - 2.1.1.1 default ipsec F,S
10 10.40.40.0/24 connected - ge0/1 - - - - - F,S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2021 10:40 AM
Correct with the current outputs you should be able to reach one site from the other since you have an IPsec tunnel UP between both sites and both sides in the service VPN 10 have a correct route.
Try this from site 200
ping vpn 10 10.40.40.X (host)
Customer Success Specialist (SD-WAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 05:17 AM
Hi Team
As I have SD-WAN LAB setup. I have issue Alarms, I am not getting BFD_SITE_UP and BDF_SITE_DOWN alarm in vManage for vEDGE devices.
all the control connection is showing UP.
please support.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide