- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IOS Zone Based Firewall Step-by-Step Basic Configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-21-2012 02:13 AM - edited 03-08-2019 06:46 PM
Introduction
The Cisco IOS Zone Based Firewall is one of the most advanced form of Stateful firewall used in the Cisco IOS devices. The zone based firewall (ZBFW) is the successor of Classic IOS firewall or CBAC (Context-Based Access Control). Cisco first implemented the router-based stateful firewall in CBAC where it used ip inspect command to inspect the traffic in layer 4 and layer 7.
Even though ASA devices are considered as the dedicated firewall devices, Cisco integrated the firewall functionality in the router which in fact will make the firewall a cost effective device. The zone based firewall came up with many more features that is not available in CBAC. The ZBFW mainly deals with the security zones, where we can assign the router interfaces to various security zones and control the traffic between the zones. Also the traffic will be dynamically inspected as it passes through the zones. In addition to all the features which is available in classic IOS firewall, Zone based firewall will support Application inspection and control for HTTP, POP3, Sun RPC, IM Applications and P2P File sharing.
For advanced configuration of IOS Zone Based Firewall refer http://yadhutony.blogspot.in/2013/08/zone-based-firewall-advanced_4036.html
Zone Based Firewall Vs CBAC
| CBAC | Zone Based Firewall |
|---|---|
| Interface Based Configuration | Zone Based Configuration |
| Controls Inbound and Outbound access on an interface | Controls Bidirectional access between zones. |
| Uses inspect statements and stateful ACLs | Uses Class-Based Policy language |
| -Not supported- | Support Application Inspection and Control |
| Support from IOS Release 11.2 | Support from IOS Release 12.4 (6) T |
- This document will guide you to configure a basic Zone Based Policy Firewall in an IOS router. Here I am going to divide the entire configuration into logical sets and finally will combine them to the get the full configuration.
ZBFW Configuration Procedure
The below are the configuration tasks that you need to follow:
- Configure Zones
- Assign Router Interfaces to zones
- Create Zone Pairs
- Configure Interzone Access Policy (Class Maps & Policy Maps)
- Apply Policy Maps to Zone Pairs
Configuration Scenario
Figure 1.
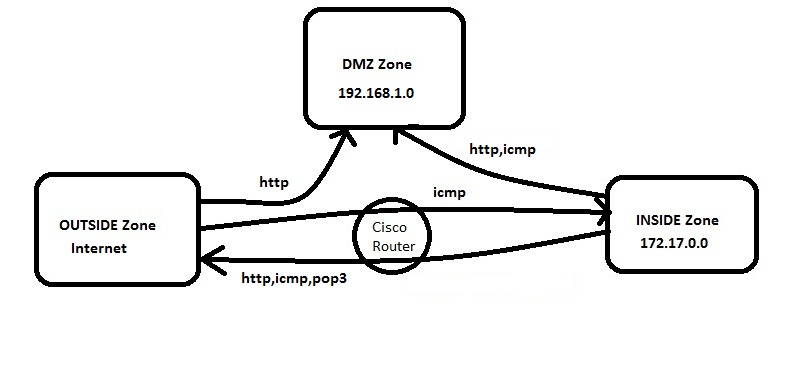
In this example we have three zones.
- Inside Zone - Private LAN
- DMZ Zone - DMZ hosts
- Outside Zone - Internet
Here I am defining a rule set for our ZBFW:
1. From Inside to Outside -http,icmp and pop3 is allowed
2. From Outside to Inside -icmp is allowed
3. From Inside to DMZ -http and icmp is allowed
4. From Outside to DMZ -http is allowed
Default Rules of Zone Based Firewall
- Interzone communication is Denied, traffic will be denied among the interfaces that are in the different zones unless we specify a firewall policy.
- Intrazone communication is Allowed, traffic will flow implicitly among the interfaces that are in the same zone.
- All traffic to Self zone is Allowed
Self Zone is created automatically by the router while we create the other zones in a Zone Based Firewall.
Task 1 : Configure Zones
In this example (refer Figure 1) we have three zones. Inside ,Outside, DMZ.
To configure zones in a router, connect the router via putty or console, switch to the global configuration mode and type the command as below:
Router(config)#zone security INSIDE
Router(config)#zone security OUTSIDE
Router(config)#zone security DMZ
Task 2 : Assign Router Interfaces to Zones
We have to assign the router interface to a particular zone. Here I am going to assign Gigabyte Ethernet 0/0 to INSIDE zone , Ge0/1 to OUTSIDE zone and Ge0/2 to DMZ zone.
To achieve this we have to go to the particular interface and attach that interface to the zone.Type the command as below:
Router(config)#interface gigabitEthernet 0/0
Router(config-if)#zone-member security INSIDE
Router(config)#interface gigabitEthernet 0/1
Router(config-if)#zone-member security OUTSIDE
Router(config)#interface gigabitEthernet 0/2
Router(config-if)#zone-member security DMZ
Now if you try to ping a zone from another zone the traffic will be denied because of the default firewall policy.
Task 3 : Create Zone Pairs
Zone pairs are created to connect the zones. If you want to make two zones to communicate you have to create Zone pairs. DO NOT create zone pairs for non-communicating zones. In our scenario the traffic flows between :
- INSIDE to OUTSIDE
- OUTSIDE to INSIDE
- OUTSIDE to DMZ
- INSIDE to DMZ
So we need to create four zone pairs. To create zone pairs the command is as follows.
Router(config)#zone-pair security IN-TO-OUT source INSIDE destination OUTSIDE
Router(config)#zone-pair security OUT-TO-IN source OUTSIDE destination INSIDE
Router(config)#zone-pair security OUT-TO-DMZ source OUTSIDE destination DMZ
Router(config)#zone-pair security IN-TO-DMZ source INSIDE destination DMZ
Task 4 : Configure Interzone Access Policy
Interzone Access policy is the key part of a Zone based firewall where we classify the traffic and apply the firewall policies. Class map and Policy map configurations are carried out during this task.
Class Maps : This will classify the traffic
Policy Maps : This will decide the 'fate' of the traffic
Class Map Configuration
Class map sort the traffic based on the following criteria 1.) Access-group 2.) Protocol 3.) A subordinate class map. In our scenario I am sorting the traffic based on access group. So first we need to create an ACL and associate it with the class map.
a.) Class Map for INSIDE-TO-OUTSIDE
Router(config)#ip access-list extended INSIDE-TO-OUTSIDE
Router(config-ext-nacl)#permit tcp 172.17.0.0 0.0.255.255 any eq www
Router(config-ext-nacl)#permit tcp 172.17.0.0 0.0.255.255 any eq pop3
Router(config-ext-nacl)#permit icmp 172.17.0.0 0.0.255.255 any
Router(config)#class-map type inspect match-all INSIDE-TO-OUTSIDE-CLASS
Router(config-cmap)#match access-group name INSIDE-TO-OUTSIDE
or
[ you can group the protocols as below:
class-map type inspect match-any INSIDE-TO-OUTSIDE-CLASS
description Allowed_Protocol_From_INSIDE_to_OUTSIDE
match protocol https
match protocol dns
match protocol udp
match protocol tcp
match protocol pop3
match protocol smtp
match protocol icmp ]
b.) Class Map for OUTSIDE-TO-INSIDE
Router(config)ip access-list extended OUTSIDE-TO-INSIDE
Router(config-ext-nacl)#permit icmp any 172.17.0.0 0.0.255.255
Router(config)#class-map type inspect match-all OUTSIDE-TO-INSIDE-CLASS
Router(config)#match access-group name OUTSIDE-TO-INSIDE
c.) Class Map for OUTSIDE-TO-DMZ
Router(config)#ip access-list extended OUTSIDE-TO-DMZ
Router(config-ext-nacl)#permit tcp any 192.168.1.0 0.0.0.255 eq www
Router(config)#class-map type inspect match-all OUTSIDE-TO-DMZ-CLASS
Router(config)#match access-group name OUTSIDE-TO-DMZ
d.) Class Map for INSIDE-TO-DMZ
Router(config)#ip access-list extended INSIDE-TO-DMZ
Router(config-ext-nacl)#permit tcp 172.17.0.0 0.0.255.255 192.168.1.0 0.0.0.255 eq www
Router(config-ext-nacl)#permit icmp 172.17.0.0 0.0.255.255 192.168.1.0 0.0.0.255
Router(config)#class-map type inspect match-all INSIDE-TO-DMZ-CLASS
Router(config-cmap)#match access-group name INSIDE-TO-DMZ
Policy-Map Configuration
Policy-Maps will apply the firewall policy to the class map that is configured previously. Three actions can be taken aganist the traffic with the policy-map configuration:
- Inspect : Dynamically inspect the traffic.
- Drop : Drop the traffic
- Pass : Simply forward the traffic.
There will be a drop policy, by default, at the end of all policy maps.
a.) Policy-map for INSIDE-TO-OUTSIDE
Router(config)#policy-map type inspect INSIDE-TO-OUTSIDE-POLICY
Router(config-pmap)#class type inspect INSIDE-TO-OUTSIDE-CLASS
Router(config-pmap)#inspect
Router(config-pmap)#class class-default
Router(config-pmap)#drop log
b.) Policy-map for OUTSIDE-TO-INSIDE
Router(config)#policy-map type inspect OUTSIDE-TO-INSIDE-POLICY
Router(config-pmap)#class type inspect OUTSIDE-TO-INSIDE-CLASS
Router(config-pmap)#pass
Router(config-pmap)#class class-default
Router(config-pmap)#drop log
c.) Policy-map for OUTSIDE-TO-DMZ
Router(config)#policy-map type inspect OUTSIDE-TO-DMZ-POLICY
Router(config-pmap)#class type inspect OUTSIDE-TO-DMZ-CLASS
Router(config-pmap)#inspect
Router(config-pmap)#class class-default
Router(config-pmap)#drop log
d.) Policy-map for INSIDE-TO-DMZ
Router(config)#policy-map type inspect INSIDE-TO-DMZ-POLICY
Router(config-pmap)#class type inspect INDISE-TO-DMZ-CLASS
Router(config-pmap)#pass
Router(config-pmap)#class class-default
Router(config-pmap)#drop log
Task 5 : Apply policy maps to zone pairs
Now we have to attach the policy maps to the zone pairs that we have already created. The command is as follows:
Router(config)#zone-pair security IN-TO-OUT source INSIDE destination OUTSIDE
Router(config-sec-zone-pair)#service-policy type inspect INSIDE-TO-OUTSIDE-POLICY
Router(config)#zone-pair security OUT-TO-IN source OUTSIDE destination INSIDE
Router(config-sec-zone-pair)#service-policy type inspect OUTSIDE-TO-INSIDE-POLICY
Router(config)#zone-pair security OUT-TO-DMZ source OUTSIDE destination DMZ
Router(config-sec-zone-pair)#service-policy type inspect OUTSIDE-TO-DMZ-POLICY
Router(config)#zone-pair security IN-TO-DMZ source INSIDE destination DMZ
Router(config-sec-zone-pair)#service-policy type inspect INSIDE-TO-DMZ-POLICY
There we finish the basic configuration of a zone based firewall.
Troubleshooting
You can use the below commands to perform some basic troubleshooting and verification.
a.) Show commands
show class-map type inspect
show policy-map type inspect
show zone-pair security
b.) Debug Commands
debug policy-firewall detail
debug policy-firewall events
debug policy-firewall protocol tcp
debug policy-firewall protocol udp
Advanced Zone Based Firewall Configuration
Here you can find some examples of advanced Zone Based Firewall configuration.
1. Advanced Zone Based Firewall Configuration : http://yadhutony.blogspot.in/2013/08/zone-based-firewall-advanced_4036.html
2. IOS Content Filtering : http://yadhutony.blogspot.in/2013/02/cisco-ios-local-content-filtering.html
3. P2P and IM Application control : http://yadhutony.blogspot.in/2012/11/how-to-block-p2p-traffic-on-cisco-router.html
You can visit http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_zbf/configuration/15-1s/sec-zone-pol-fw.html for more details.
Thank you for viewing this document.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank You Very Much (Yadhu Tony) .. ^___^ ..
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You are welcome.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very good tutorial. Thanks for sharing your knowledge with us!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Brilliant tutorial..thank you very much for taking the time to do it....very clear and concise
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you Niall
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice doc - I was going to print it when I noticed a couple of typos (INDISE vs INSIDE) so I corrected them.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the clear explanation!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have a question here.
That is how to block website like facebook using zone-based firewall.??I have done as follows..Pls correct me if I am wrong.
parameter-map type regex DENY_SITES
pattern .*facebook.com
class-map type inspect http match-all CLASS_DENY_SITES
match request header host regex DENY_SITES
!
!
policy-map type inspect http POLICY_DENY_SITES
class type inspect http CLASS_DENY_SITES
reset
zone security INSIDE
zone security OUTSIDE
zone-pair security IN_OUT source INSIDE destination OUTSIDE
But when i am going to apply this policy ,getting the following error.....................
Router(config-sec-zone-pair)#service-policy type inspect POLICY_DENY_SITES
Inspect service-policy attachment failed
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for your question. I would recommend you to go through the below link to configure local url filtering
(using 'urlf-glob') http://yadhutony.blogspot.in/2013/02/cisco-ios-local-content-filtering.html .
If you want to specifically block using 'regex' then follow http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00808bc994.shtml and search for 'Configuring HTTP Application Inspection Enhancements'. Let me know if you have any more clarification.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you! But correct me if i wrong. According to initial requirements:
"1. From Inside to Outside - http, tcp, udp, icmp and pop3 is allowed"
but there are none of icmp-aware rules. You allowed echo service, 7/tcp, but not ICMP. Also you didn't specify rule for udp and tcp, only subset of tcp: http and pop3.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
I have my zone firewall working but when I added the access-list to existing policy as configured below , I loose internet connection.
Can you help please?
Kind Regards
Hamid
ip access-list extended PermitViber
permit tcp any any eq 4244
permit tcp any any eq 1147
permit tcp any any eq 5242
permit udp any any eq 1148
permit udp any any eq 5243
permit udp any any eq 9785
permit ip any any
end
class-map type inspect match-any Viber_class
match access-group name PermitViber
Policy-Map type inspect InsideToOutside
class type inspect Viber_class
inspect
class class-default
drop
end
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Hamid,
Thank you for reading the document.
Now about your question,basically from INSIDE to OUTSIDE you need to allow the below protocols to get Internet access:
tcp
udp
http
https
dns
If you could share the entire ZBFW configuration by removing all critical information I can better guide you forward.
Best Regards,
Tony
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Denis,
Yes, you are absolutely right. I have changed the doc accordingly. Thank you for pointing this out
Best Regards,
Tony
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Tony for your reply.
my existing configration as below, what i want is to added the above configration.
Kind regrds
Hamid
version 12.4
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime
service password-encryption
service sequence-numbers
!
hostname Router
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 8 log
security passwords min-length 6
logging buffered 51200 warnings
enable secret 5 $1$c6/s$x226Qy8iD3Zkad6dXmKUK.
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
aaa session-id common
clock summer-time london recurring
!
crypto pki trustpoint TP-self-signed-4161185151
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4161185151
revocation-check none
rsakeypair TP-self-signed-4161185151
!
!
crypto pki certificate chain TP-self-signed-4161185151
certificate self-signed 01
3082023E 308201A7 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34313631 31383531 3531301E 170D3133 30313139 31323035
31375A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 31363131
38353135 3130819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A5AA 992BBAE8 7541EF9F DDEBF5D8 911D2374 A411A541 BBCD8B0D A5489E64
35D878EE 3054B7F2 D80F9E9A C642B5F8 42A2055D A75CD215 33539B85 77C9A21B
28C980D2 32917513 A6A82387 86E794C5 DBCFBCEE 9992548A 885C3C65 6C6517EE
4A2441E0 25A00DBF F43EEFB8 D9F7524E 7AE0ECF3 A198274C 24F5FBE3 DD648409
50550203 010001A3 66306430 0F060355 1D130101 FF040530 030101FF 30110603
551D1104 0A300882 06526F75 74657230 1F060355 1D230418 30168014 5E3FEDFE
F46A1F9A 7AEFFC1B 9C59052F 7D578F87 301D0603 551D0E04 1604145E 3FEDFEF4
6A1F9A7A EFFC1B9C 59052F7D 578F8730 0D06092A 864886F7 0D010104 05000381
81007307 ED236D2D 0CD3B0DB DBD3C525 F73115C1 736446E2 2F34DAE8 749A9BED
B80460C3 DE17D01A 2A7316EF 0277A45E 3C0DF176 D7598EAC DFEBDAE8 270FE233
64393741 6FA673A2 459FDAF0 A2667866 4C4E8A3C 663FB940 DBA0C610 11FB5BDF
37207C40 76DC95FF F74FCB09 64F63AF9 7B8C0F39 F2A81151 58A7FA9B 6B6EE8E7 9062
quit
!
dot11 ssid cisco
authentication open
authentication network-eap eap_methods
!
no ip source-route
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 10.10.10.254
!
ip dhcp pool lan-pool
import all
network 10.10.10.0 255.255.255.0
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
lease 0 12
!
ip dhcp pool dreambox
host 10.10.10.1 255.255.255.0
client-identifier 0100.0934.1044.b2
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
!
ip dhcp pool linksys-kiss1600
host 10.10.10.2 255.255.255.0
client-identifier 0100.d0e0.9509.78
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
!
ip dhcp pool linksys-spa942
host 10.10.10.3 255.255.255.0
client-identifier 0100.0e08.dcd4.80
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
!
ip dhcp pool agnieszka
host 10.10.10.4 255.255.255.0
client-identifier 0100.1302.7b92.b6
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
!
ip dhcp pool dariusz
host 10.10.10.5 255.255.255.0
client-identifier 0100.15af.01c7.a4
dns-server 87.194.0.51 87.194.0.66
default-router 10.10.10.254
!
!
no ip bootp server
ip name-server 87.194.0.51
ip name-server 87.194.0.66
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
multilink bundle-name authenticated
!
archive
log config
hidekeys
!
!
ip tcp synwait-time 10
!
class-map type inspect match-any ping
match access-group name ICMPEcho
class-map type inspect match-any RouterManagement
match access-group name ManagementProtocols
class-map type inspect match-any InternetTraffic
match protocol http
match protocol ftp
match protocol icmp
match protocol https
match protocol dns
match protocol smtp
match protocol pop3
match protocol tcp
match protocol udp
!
!
policy-map type inspect InsideToRouter
class type inspect RouterManagement
inspect
class class-default
policy-map type inspect RouterToInside
class class-default
inspect
policy-map type inspect OutsideToRouter
class type inspect ping
inspect
class class-default
drop log
policy-map type inspect InsideToOutside
class type inspect InternetTraffic
inspect
class class-default
drop
!
zone security Inside
description Inside network
zone security Outside
description Outside network
zone-pair security InsideToOutside source Inside destination Outside
service-policy type inspect InsideToOutside
zone-pair security OutsideToRouter source Outside destination self
service-policy type inspect OutsideToRouter
zone-pair security InsideToRouter source Inside destination self
service-policy type inspect InsideToRouter
zone-pair security RouterToInside source self destination Inside
service-policy type inspect RouterToInside
!
bridge irb
!
!
interface Loopback1
ip address 1.1.1.1 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
ip route-cache flow
!
interface Null0
no ip unreachables
!
interface ATM0
no ip address
ip access-group 101 in
ip access-group 101 out
no ip redirects
no ip unreachables
no ip proxy-arp
ip virtual-reassembly
ip route-cache flow
no atm ilmi-keepalive
dsl operating-mode auto
!
interface ATM0.1 point-to-point
description Link_To_Outside$FW_OUTSIDE$
ip address dhcp
ip access-group 101 out
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly
zone-member security Outside
logging event subif-link-status
atm route-bridged ip
pvc 0/101
oam-pvc manage
encapsulation aal5snap
!
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface Dot11Radio0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
ip route-cache flow
!
encryption vlan 1 key 1 size 40bit 7 F6003767BE9C transmit-key
encryption vlan 1 mode ciphers wep40
!
ssid Shireen@1955
!
ssid cisco
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role root
!
interface Dot11Radio0.1
description Cisco open
encapsulation dot1Q 1 native
no cdp enable
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface Vlan1
no ip address
ip access-group 101 in
ip access-group 101 out
ip tcp adjust-mss 1452
bridge-group 1
bridge-group 1 spanning-disabled
!
interface BVI1
description $FW_INSIDE$
ip address 10.10.10.254 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly
zone-member security Inside
ip route-cache flow
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 93.96.32.1
!
!
ip http server
ip http access-class 1
ip http authentication local
ip http secure-server
ip http timeout-policy idle 600 life 86400 requests 10000
ip nat inside source list 102 interface ATM0.1 overload
!
ip access-list extended ICMPEcho
permit icmp any any echo
ip access-list extended ManagementProtocols
permit tcp any any eq telnet
permit tcp any any eq 22
permit tcp any any eq www
permit tcp any any eq 443
permit icmp any any echo
ip access-list extended strict
!
access-list 1 remark HTTP Access-class list
access-list 1 remark CCP_ACL Category=1
access-list 1 permit 10.10.10.0 0.0.0.255
access-list 1 deny any
access-list 102 permit ip 10.10.10.0 0.0.0.255 any
no cdp run
!
!
!
!
control-plane
!
bridge 1 protocol ieee
bridge 1 route ip
banner login ^CThis is Hamid computer^C
!
line con 0
no modem enable
transport output telnet
line aux 0
transport output telnet
line vty 0 4
transport input telnet ssh
!
scheduler max-task-time 5000
scheduler allocate 4000 1000
scheduler interval 500
ntp master
ntp server 109.169.89.48
ntp server 178.79.160.57
time-range NOTRAFFIC
periodic daily 0:10 to 7:00
!
end
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Hamid,
Hope you are getting Internet access using the existing configuration. Now could you change the config as below and let me know if you can connect to Internet.
ip access-list extended PermitViber
permit tcp any any eq 4244
permit tcp any any eq 1147
permit tcp any any eq 5242
permit udp any any eq 1148
permit udp any any eq 5243
permit udp any any eq 9785
permit ip any any
class-map type inspect match-any InternetTraffic
match protocol http
match protocol ftp
match protocol icmp
match protocol https
match protocol dns
match protocol smtp
match protocol pop3
class-map type inspect match-all UDP
match access-group name PermitViber
match protocol udp
class-map type inspect match-all TCP
match access-group name PermitViber
match protocol tcp
policy-map type inspect InsideToOutside
class type inspect InternetTraffic
inspect
class type inspect UDP
inspect
class type inspect TCP
inspect
class class-default
drop log
zone-pair security InsideToOutside source Inside destination Outside
service-policy type inspect InsideToOutside
Let me know if you are still facing issues.
Best Regards,
Tony
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: