- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA 8.3 Upgrade - What You Need to Know
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-20-2010 08:53 AM - edited 03-08-2019 06:35 PM
- First Things First
- Pre-Requsites to Upgrading
- How to Determine How Much Memory Your ASA Has
- Why Does the ASA Need a Memory Upgrade?
- Remove nat-control from your ASA Configuration
- How to Upgrade Your ASA to 8.3
- Upgrade Paths
- Examples of Configuration Changes in 8.3
- NAT
- ACL Changes
- What to Do If You Run Into Problems with 8.3
- Additional Information
First Things First
First, let's make sure we get one thing clear, upgrading your ASA from 8.2 to 8.3 is NOT a Minor upgrade! There are significant internal architectural changes around NAT and ACLs in 8.3. And, more importantly to you (the customer) are the following:
- The NAT CLI commands are completely different from all previous version of ASA
- The IP addresses used in the ACLs are different (pre-8.3 versions used the global/translated IPs, whereas 8.3 always uses the real IPs (untranslated)
- A new concept of host-based objects was introduced, to allow singular hosts to be referenced by their names (previously, we had the name command, but that was more of a macro-substitution in the show running-config output).
Pre-Requsites to Upgrading
Many models of the ASA require a memory upgrade prior to upgrading the ASA to version 8.3. Brand new ASAs from the factory (manufactured after Feb 2010) come with the upgraded memory. However, if your ASA was manufactured before February 2010, and is one of the models below requiring a memory upgrade, then you will need to purchase the memory upgrade part prior to installing 8.3 on your ASA.
PlatformLicensePre-8.3 Memory Required8.3 Memory RequiredMemory Upgrade Part Number
| 5505 | Unlimited (inside hosts=Unlimited) | 256 MB | 512 MB | ASA5505-MEM-512= |
| 5505 | Security Plus (failover=enabled) | 256 MB | 512 MB | ASA5505-MEM-512= |
| 5505 | All other licenses | 256 MB | 256 MB | No Memory Upgrade Needed |
| 5510 | All licenses | 256 MB | 1024 MB | ASA5510-MEM-1GB= |
| 5520 | All licenses | 512 MB | 2048 MB * | ASA5520-MEM-2GB= |
| 5540 | All licenses | 1024 MB | 2048 MB * | ASA5540-MEM-2GB= |
| 5550 | All licenses | 4096 MB | 4096 MB | No Memory Upgrade Needed |
| 5580 | All licenses | 8-16 Gb | 8-16 Gb | No Memory Upgrade Needed |
* Note: The maximum memory supported for the ASA-5520 and ASA-5540 is 2 Gb. If you install 4 Gb of memory in these units, they will go into a boot loop.
How to Determine How Much Memory Your ASA Has
From the CLI, you can issue the show version | include RAM command to see how much memory your ASA has. In the following example, it is an ASA-5520, with 512 MB of RAM, and therefore would require a memory upgrade prior to installing 8.3 on it.
ASA#
show version | include RAM
Hardware: ASA5520, 512 MB RAM
, CPU Pentium 4 Celeron 2000 MHz
For ASDM users, you can see the amount of RAM in the ASA from the ASDM Home (Device Dashboard) page.
Why Does the ASA Need a Memory Upgrade?
This seems to be a fairly common question with customers. Why exactly are we requiring a memory upgrade in order to run 8.3? The reason is simple. The memory on the ASAs have not been increased since they were originally introduced, yet as the years have gone by new features have been added which require additional memory at boot. The more memory the base image requires, the less memory there is for things like ACLs, connections, IPSec tunnels, SSL tunnels, etc. Additionally, as we introduce new features and customers adopt those, they consume additional memory.
Remove nat-control from your ASA Configuration
nat-control is a legacy feature which was created to help users migrate from PIX 6.x to PIX/ASA version 7.0 and higher. In PIX 6.x, if you wanted to pass traffic between two interfaces, it was required that you have a NAT configuration which would allow it. PIX/ASA version 7.0 removed this restriction, and made the behavior like routers. Which is, ACLs control if traffic is permitted or not. NAT then becomes optional. However, in order to preserve the behavior for the PIX customers, if a PIX user upgraded from 6.x to 7.0, then the nat-control command was automatically added to the configuration. The same is true of customers using the PIX to ASA migration tool. Thus, there may still be a number of customers with nat-control in their configuration, and who do not need it.
What happens if I remove the nat-control command?
Answer: Not much. Removing the command just means that traffic can flow between interfaces without requiring a nat policy. Therefore, the security policy of what traffic is permitted or denied is defined by your interface ACLs.
What happens if I leave the nat-control command in my configuration?
Answer: Since 8.3 no longer supports the nat-control command, it will add equivalent nat commands to enforce a policy which requires explicit nat rules to allow traffic to pass between interfaces. An example is shown below. Note that the number of these rules increases exponentially with the number of interfaces on your ASA. Thus, it is highly recommended that if your security policy (ie: ACLs) is used to control what traffic is allowed where, then you should issue no nat-control prior to upgrading to ASA version 8.3. This will prevent the following nat rules from being created - which will block traffic between interfaces, until a more specific nat policy is defined for that traffic.
pre-8.3 Configuraiton
8.3 Configuration
| nat-control | object network obj_any subnet 0.0.0.0 0.0.0.0 nat (inside,outside) dynamic obj-0.0.0.0 object network obj-0.0.0.0 host 0.0.0.0 object network obj_any-01 subnet 0.0.0.0 0.0.0.0 nat (inside,mgmt) dynamic obj-0.0.0.0 object network obj_any-02 subnet 0.0.0.0 0.0.0.0 nat (inside,dmz) dynamic obj-0.0.0.0 object network obj_any-03 subnet 0.0.0.0 0.0.0.0 nat (mgmt,outside) dynamic obj-0.0.0.0 object network obj_any-04 subnet 0.0.0.0 0.0.0.0 nat (dmz,outside) dynamic obj-0.0.0.0 object network obj_any-05 subnet 0.0.0.0 0.0.0.0 nat (dmz,mgmt) dynamic obj-0.0.0.0 |
If you forget to issue no nat-control prior to upgrading, then it is safe to remove the all 0's objects with associated nat rules after the fact.
To view your current nat-control configuration, issue the command show run all nat-control.
How to Upgrade Your ASA to 8.3
Upgrading your ASA to 8.3 is the same process as all previous upgrades. Just copy the image over to the flash, specify the file to boot, and then reboot your ASA. Upon first boot, the ASA will auto convert your 8.2 configuration into the new syntax for NAT and ACLs required of 8.3. While your CLI commands will change, your devices security policy will remain the same.
Please note that we only support upgrading to 8.3 from 8.2. Therefore, you need to be running 8.2 on your ASA prior to upgrading to 8.3.
For ASAs in failover set, we do support upgrading from 8.2 to 8.3 with zero-downtime. Follow the same procedure you have in the past.
Note: During the upgrade process, the ASA will save two files on disk.
- The current (pre-upgraded) configuration in a file named <version>_startup_cfg.sav
Example: disk0:/8_2_2_0_startup_cfg.sav
This file will be critical if you need to downgrade your ASA from 8.3 to 8.2 in a future date - Warning messages and Errors encountered during the upgrade process of converting your configuration to 8.3 will be saved in a file named upgrade_startup_errors_<timestamp>.log
Upgrade Paths
Cisco officially supports upgrading to ASA version 8.3 only from ASA version 8.2. Therefore, if you are currently running a version of ASA code prior to 8.2, you will need to perform a stepwise upgrade. Please see the table below:
Current TrainIntermediate UpgradesFinal Train
| 8.2 | none | 8.3 |
| 8.1 | 8.2 | 8.3 |
| 8.0 | 8.2 | 8.3 |
| 7.2 | 8.0 --> 8.2 | 8.3 |
| 7.1 | 7.2 --> 8.0 --> 8.2 | 8.3 |
| 7.0 | 7.2 --> 8.0 --> 8.2 | 8.3 |
Examples of Configuration Changes in 8.3
NAT
The NAT CLI configuration for 8.3 is radically different than anything than you may be used to. Therefore, for CLI users, it is recommended you ease into 8.3 with the expectation that you will have to re-learn NAT. For those who view this as an obstacle, we would recommend that you use ASDM or CSM or some other GUI tool to configure the ASA - as the GUI configuration for 8.3 is largely the same.
That said, for CLI users, please do not upgrade to 8.3 on a Friday night just as you are getting ready to go out of town for the weekend. Instead, it is recommend that you play with it in a lab (if you have one), or read up on the changes (see Additional Information below) before you upgrade. Ok, with that said, let's look at some examples.
pre-8.3 Configuration
8.3 Configuration
| Static NAT | static (inside,outside) 209.165.201.15 10.1.1.6 netmask 255.255.255.255 | Option 1 (Preferred) object network obj-10.1.1.6
Option 2 object network server_real ! nat (inside,outside) source static server_real server_global |
| Dynamic PAT | nat (inside) 1 10.1.1.0 255.255.255.0 global (outside) 1 209.165.201.254 | object network internal_net ! object network internal_netnat (inside,outside) dynamic 209.165.201.254 |
| Dynamic NAT with Interface Overload | nat (inside) 1 10.1.1.0 255.255.255.0 global (outside) 1 interface global (outside) 1 209.165.201.1-209.165.201.2 | object network NAT_Pool ! object network internal_net |
ACL Changes
Although the syntax of the ACLs haven't changed much (just added capabilities for new objects), the significant change is that all IP addresses listed in ACLs which are applied to an interface will be converted (on upgrade) from using global (ie: translated or post-NAT) IP addresses, to using the real IP address. Let's look at an example.
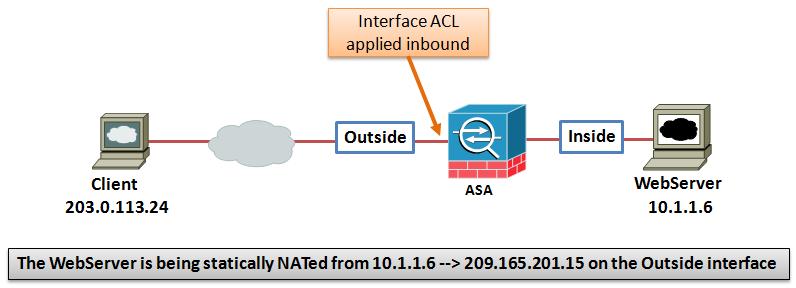
In the above Topology, an internal web server (with IP 10.1.1.6) is being protected by an ASA. Clients on the Internet access this web server by its public IP address: 209.165.201.15 Prior to version 8.3, the interface ACL would permit traffic to the public IP 209.165.201.15. But, starting with 8.3 the real IP 10.1.1.6 is used in the configuration. Please see the configuration examples below.
pre-8.3 Configuration
static (inside,outside) 209.165.201.15 10.1.1.6 netmask 255.255.255.255
!
access-list outside_in extended permit tcp any host 209.165.201.15
access-group outside_in in interface outside
8.3 Configuration
object network obj-10.1.1.6
host 10.1.1.6
nat (inside,outside) static 209.165.201.15
!
access-list outside_in extended permit tcp any host 10.1.1.6
access-group outside_in in interface outside
What to Do If You Run Into Problems with 8.3
- Call in to the TAC, and they can help you
- Check the upgrade_startup_errors_<timestamp>.log on disk0: by using the more disk0:/upgrade_startup_errors_<timestamp>.log
- Downgrade to 8.2 using the downgrade <image> <config> command. This is IMPORTANT! You must use the downgrade command, specifying the config file on disk (which the 8.3 upgrade process saved)
Refer the following video of this document---
https://supportforums.cisco.com/videos/2200
Additional Information
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I inherited an active-standby failover pair that is running 7.2(4). I need to get this pair upgraded to 8.4(5) at least, maybe higher.
Has anyone tried the following?
1. Break a failover pair, taking one offline
2. Performing all the upgrades on the offline ASA
3. Take down the active ASA and bring the upgraded ASA online as the active.
4. Upgrade the remaining ASA by installing the newest code only, no staggered upgrades.
5. Re-create the failover pair and sync the Active to the new Standby.
Seems like it would be faster than doing all the staggered upgrades and failovers on both devices. There would be no redundancy for a period, and a short outage when swapping the active ASA's but that would be doable in my situation.
Anyone have any thoughts about this method?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice document
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Greate, it really helps me a lot. Thanks.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent :-)
Thanks for such a nice sharing!!!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Its a great doc...Great explanation...Thank you..
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great Document!
Regarding "What to Do If You Run Into Problems with 8.3" - I have just one additional recommendation - upgrade configuration in lab, thoroughly analyse configuration, tune everything to your taste and standards (automatic upgrade procedure will automatically name many objects, add lines that you perhaps don't like etc.), and THOROUGHLY TEST NEW CONFIG IN LAB - this will save you so much time, reduce downtimes, avoid issues and reduce chance of rollback when going live.
We use FW123TEST tool for every single software/hardware upgrade and larger configuration change in mission critical environments.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I seem to be having difficulty with the ACL changes. The biggest difficulty is that they do not change. As an example I have an internal Remote Desktop Server that is accessed through our ASA in exactly the same way the web server is outlined in this document. It has an external public ip and an internal private ip. The 8.2(5) configuration is (public ip changed):
name 10.1.31.250 Hehdalrds.best.local-vip description Remote-desktop-server
static (Server,Outside) 3.3.3.3 10.1.31.250 netmask 255.255.255.255
name 3.3.3.3 Remote.academicpartnerships.com description Remote.academicpartnerships.com/32
network-object host 3.3.3.3
access-list Outside_access_in extended permit udp any host 3.3.3.3 object-group RDP_UDP
static (Server,Outside) 3.3.3.3 10.1.31.250 netmask 255.255.255.255
the configuration after the migration to 8.3(1)
name 10.1.31.250 Hehdalrds.best.local-vip description Remote-desktop-server
object network obj-10.1.31.250
host 10.1.31.250
object network obj-10.1.31.250
nat (Server,Outside) static 3.3.3.3
name 3.3.3.3 Remote.academicpartnerships.com description Remote.academicpartnerships.com/32
network-object host 3.3.3.3
access-list Outside_access_in extended permit udp any host 3.3.3.3 object-group RDP_UDP
nat (Server,Outside) static 3.3.3.3
object network obj_any-02
According to the document the post migration ACL should be:
access-list Outside_access_in extended permit udp any host 10.1.31.250 object-group RDP_UDP
None of my ACL's are updated during the migration. Has anyone experienced this? Is there a reason for this? I have a number of ASA’s to upgrade and some of them have significant ACL’s. Are the ACL’s not structured properly to begin with?
BTW great document it has been a great help!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We have to change ACL manually after the migration . ACL's doesn't not get updated after upgradation only Nat get updated .
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: