- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA Bi-directional (overlapping) NAT example configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-11-2010 01:42 PM - edited 03-08-2019 06:37 PM
In some network situations (usually due to two different networks becoming interconnected) there might be a situation where there are overlapping IP subnets. If the ip duplication cannot be resolved by re-numbering one of the subnets, NAT is required to provide connectivity between them.
Consider the following example where the 10.10.10.0/24 network exists on both the inside and the outside interfaces of the firewall. The 10.10.10.0/24 network on the outside of the firewall is reachable via an IPSEC Lan-to-Lan tunnel:
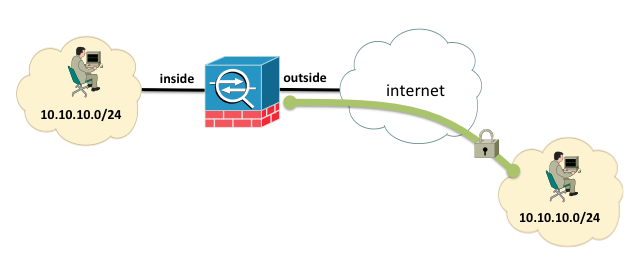
In ASA version 8.3 and later, connectivity between the two subnets can be established by having the inside subnet reach the outside subnet by sending packets to the 10.10.30.0/24 network, and the outside subnet connect to the inside subnet by sending packets to the 10.10.20.0/24 subnet.
object network insideReal
subnet 10.10.10.0 255.255.255.0
object network insideMapped
subnet 10.10.20.0 255.255.255.0
object network outsideReal
subnet 10.10.10.0 255.255.255.0
object network outsideMapped
subnet 10.10.30.0 255.255.255.0
Note that the ASA will need to have a route to not only the local LAN segment, but the remote LAN segment, and the ASA does not allow duplicate routing entries. To add this duplicate route, increase the metric for the route facing out the outside interface, which will satisfy the ASA requirement that the routes be different:
route inside 10.10.10.0 255.255.255.0 10.0.0.2 1
route outside 10.10.10.0 255.255.255.0 192.168.2.5 2
Both routes are valid and operational; remember, the ASA has the concept of routes applied on a particular interface (that is why you specify the interface nameif when you add the route statement). Also, the NAT translations can override the routing table, which is key in this example.
With a NAT configuration like this, the NAT translations override the global routing table, and will virtually forward the packets destined to 10.10.20.x or 10.10.30.x to the egress interface first, without consulting the global routing table. Then, only the routes associated with that interface the packet was forwarded to are used to find the next hop.
If packets don't match these translations, (when a "global" routing decision is needed) for a packet destined to the 10.10.10.x network (a packet sourced from a DMZ for example, that does not match either of these translations), the global routing table is consulted and the route with the lower metric will always win, and in this case it will be routed to the inside interface.
This "route-override" behavior of translations can be modified with the 'route-override' argument to manual NAT rules, see this documentation for more information (find in page for 'route-override'):
http://www.cisco.com/en/US/docs/security/asa/asa84/configuration/guide/nat_rules.html
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Could you please provide the run-config of above asa. I tried the above configuration but no go. I don't know where i did a mistake. So to clarify i need the run-config of asa. thanku.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The example given here contradicts the example givin in the CCNP Security FIREWALL study guide by Cisco Press. I did not yet have the time to fully test both examples so I can not yet say which is correct. I did however e-mail the author of the Cisco Press book and he claims his example is the correct one.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I found this page because I also thought the example in the Cisco Press book was wrong. How would matching 10.0.0.0/24 real to 10.0.0.0/24 real ever hit the translation rule in the firewall when it's the same network and thus would not even go out to their default gateway to begin with?
I believe the example on this page is the correct way to do it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I forgot about my comment here. As I got a new job where we don't use Cisco ASA, I never got around to fully testing both examples. Did you test both, Zach? This one sure looks to be the correct one, but I assume the author really (should at least) know what he is talking about. I'll try to fire up some virtual ASAs in GNS3 and test it out.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The ciscopress.com web site page for the CCNP Security FIREWALL study guide book has corrections on this topic. I've noticed that the update for the twice-NAT configuration is almost a full rewrite.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: