- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA: IDFW (Identity Firewall) Step by Step configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-14-2011 07:42 PM - edited 03-08-2019 06:43 PM
- Goal
- Documentation
- Prerequisite
- Limitations
- Scenarios
- Licensing for IDFW
- Topology
- Step by Step Configuration
- Show commands
- Debugs
- Syslogs
- Common Problems
Goal
With Identity firewall, we can configure access-list and allow/restrict permission based on users and/or groups that exist in the Active Directory Domain.
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here:
Prerequisite
The ASA must be running minimum 8.4.2 code to be able to configure IDFW feature.
The AD Agent must be installed on a Windows server that is accessible to the ASA. Additionally, you must configure the AD Agent to obtain information from the Active Directory servers. Configure the AD Agent to communicate with the ASA.
Supported Windows servers include Windows 2003, Windows 2008, and Windows 2008 R2.
![]()
Windows 2003 R2 is not supported for the AD Agent server.
ASA sends encrypted log in information to the Active Directory server by using SSL enabled over LDAP. SSL must be enabled on the Active Directory server.
Limitations
•![]() A full URL as a destination address is not supported.
A full URL as a destination address is not supported.
• MAC address checking by the Identity Firewall does not work when intervening routers are present.
•![]() The following ASA features do not support using the identity-based object and FQDN:
The following ASA features do not support using the identity-based object and FQDN:
–![]() route-map
route-map
–![]() Crypto map
Crypto map
–![]() WCCP
WCCP
–![]() NAT
NAT
–![]() group-policy (except VPN filter)
group-policy (except VPN filter)
–![]() DAP
DAP
Scenarios
Feature is supported in all models of ASAs.
Feature is supported in all modes of ASAs - transparent, routed, single and multiple-context mode.
Total users supported - ASA5505 (1024 users), Other model ASAs support 64K users
Total groups supported - 256 groups
Total number of IPs per user in a domain - 8 IP addresses
AD Agent can support up to 100 client devices and 30 domain controller machines, and can internally cache up to 64,000 IP-to-user-identity mappings.
ASA - The Identity Firewall supports defining only two AD-Agent hosts. This applies to single as well as multiple contexts. Each context can support only 2 AD-Agents.
Description Topology
DC and AD-Agent Co-loated on the same box. No redundancy. The step by step configuration below is based off of this topology. | 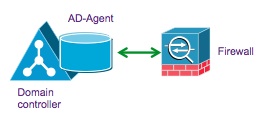 |
DC and AD-Agent on different boxes. No redundancy. | 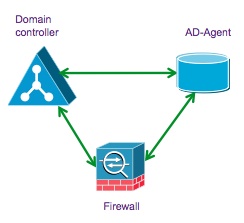 |
Multiple DCs and Single AD-Agent - all on separate boxes. Offers redundancy. |  |
Multiple DCs and multiple AD-Agent - all on separate boxes. Offers redundancy. For example if you have 30 domain controllers, you would need 2 AD-Agent boxes. Each AD-Agent will have all 30 DCs configured on it to receive login/logoff events from. You would configure both the AD-Agents on the ASA. ASA will talk to only one AD-Agent at a time and use the other as backup.
If you have more than 30 domain controllers, then consider multiple context. Each context follows the same IDFW rules. Each context can support only 2 AD-Agents. | 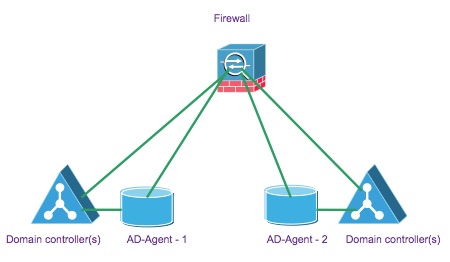 |
Licensing for IDFW
Base License - All Models
Topology
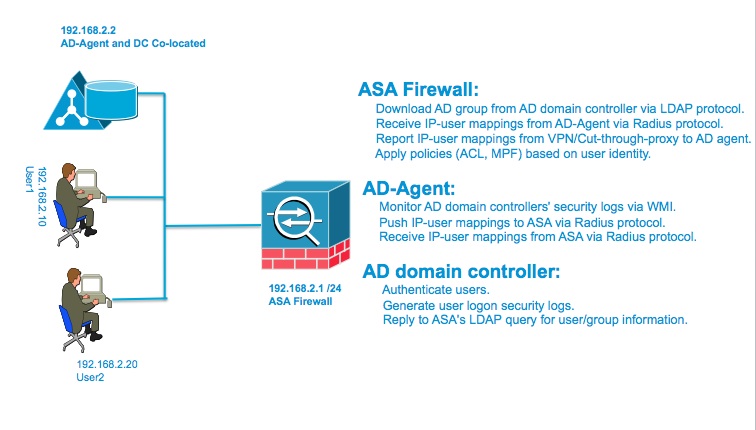
Step by Step Configuration
1. Configure the Active Directory Domain (on the ASA)
Gather the following information:
a. AD Domain Controller Server IP address
b. Distinguished Name for LDAP base dn
c. Create a UserID and password on the DC that the ASA/IDFW will use to connect to the DC (Domain Controller)
The DC's name is kurelisankar.DC1.SAMPLE.com. By configuring the ldap-base-dn,
AD server will know where it should begin searching when it receives an authorization request.
KUSANKAR-ASA-5505(config)# aaa-server AD1 protocol ldap
KUSANKAR-ASA-5505(config-aaa-server-group)#aaa-server AD1 (inside) host 192.168.2.2
KUSANKAR-ASA-5505(config-aaa-server-host)# ldap-base-dn DC=DC1,DC=SAMPLE,DC=com
KUSANKAR-ASA-5505(config-aaa-server-host)# ldap-scope subtree
KUSANKAR-ASA-5505(config-aaa-server-host)# server-type microsoft
KUSANKAR-ASA-5505(config-aaa-server-host)# server-port 389
By default the ASA talks to the DC using port tcp 389. If SSL is enabled on the DC then we need to enable ldap-over-ssl on the ASA as well, and also configure server-port 636 so the ASA can talk to the DC using port 636. This is optional.
KUSANKAR-ASA-5505(config-aaa-server-host)# ldap-over-ssl enable
KUSANKAR-ASA-5505(config-aaa-server-host)# server-port 636
Configure the userID (kusankar) and password on the AD Server for the ASA to be able to log into the AD Domain.

hostname(config-aaa-server-host)# ldap-login-dn DC1\kusankar ("ldap-login-dn kusankar" is also correct)
hostname(config-aaa-server-host)# ldap-login-password cisco123
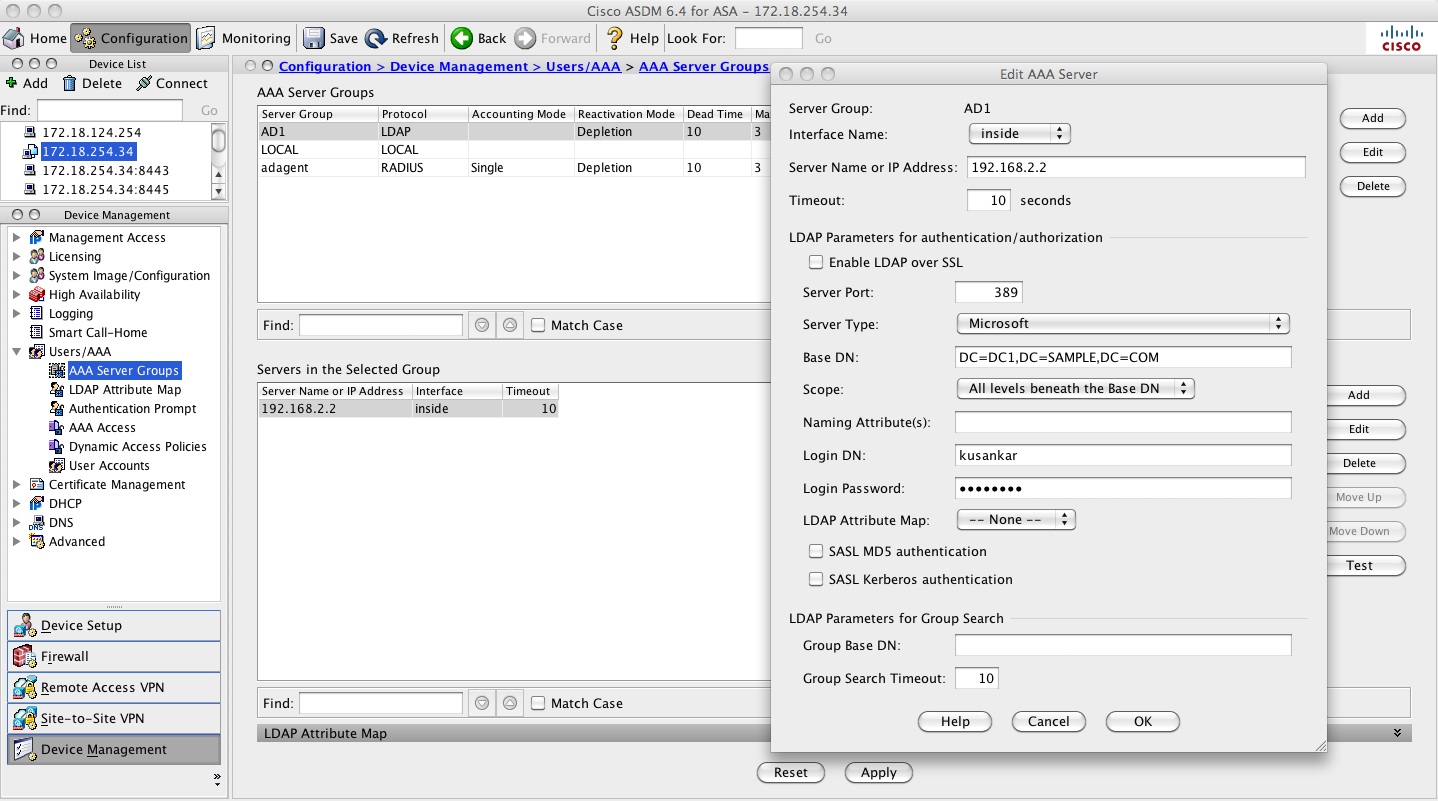
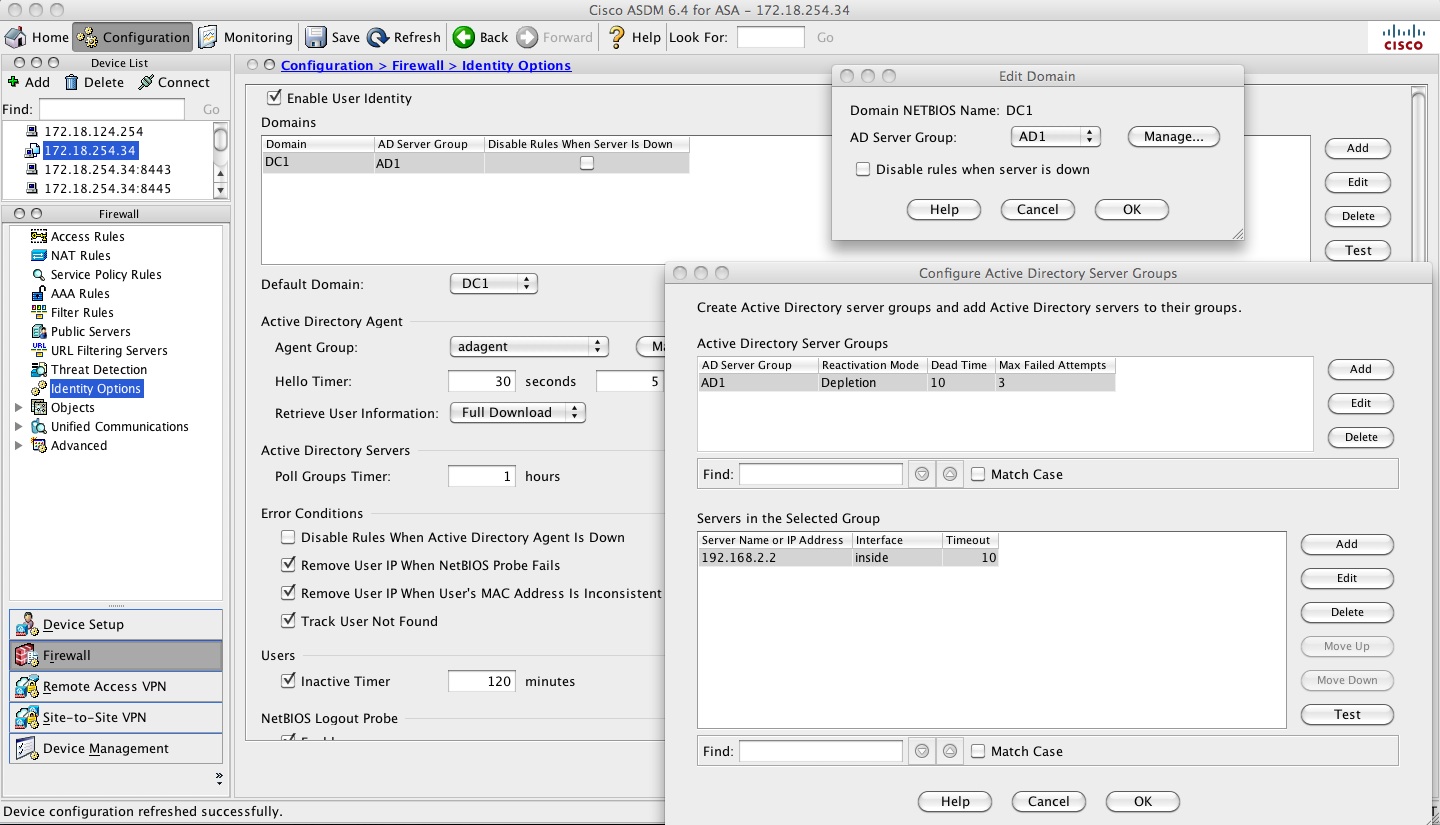
If configuring via ADSM watch the screen shot below to create the AAA server group:
2. Configure the AD Agent either on the DC or on a member server in the domain
Download AD Agent installer from here: http://tools.cisco.com/squish/930d9 File Name: AD_Agent-v1.0.0.32-build-539-Installer.exe
In this example the AD Agent is installed on the Domain Controller. The AD Agent as the folloiwng components.
- Radius Server - Interacts with the ASA
- AD Observer - Monitors AD Domains Controllers and updates the Agent DB.
- WatchDog - Monitors AD Observer and Radius
- CLI - commands to add the ASA as well as the DC on the AD Agent.
a. Install AD Agent on the DC or member server.
The installer will install the AD Agent in the C:\IBF\ (IBF - Identity Based Firewall) directory of the Windows machine.
Clicking on the "show details" button will show the files being copied.
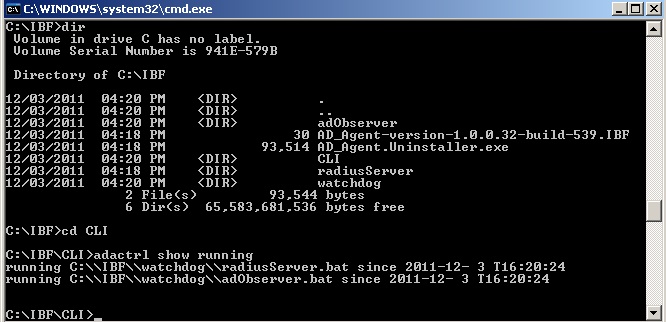
b. Confirm the AD_Agent install
Go to the command prompt on the Windows machine and run "adactrl.exe show running" from the path C:\IBF\CLI.
The output similar to this will be seen.
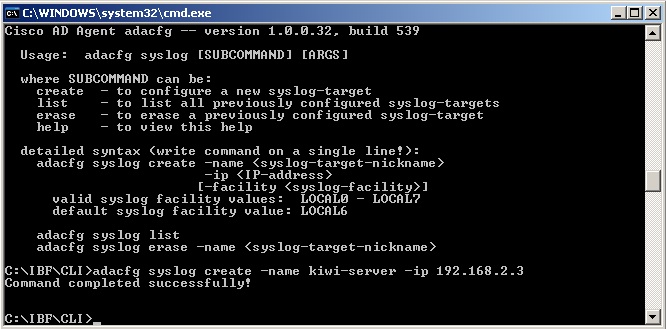
c. Sending logs from the AD Agent to a syslog server (optional)
From the command line prompt, type "cd C:\IBF\CLI" and then enter the command:adacfg syslog create -name kiwi-server -ip 192.168.2.3
If you need help with the options type "adacfg help syslog".
d. Configure the AD Agent to obtain information from all the DCs
- The DCs should run one of the following OS versions and already be a member in the domain.
Windows 2003 R2 is not supported for the AD Agent server.
–![]() Windows Server 2003
Windows Server 2003
–![]() Windows Server 2008
Windows Server 2008
–![]() Windows Server 2008 R2
Windows Server 2008 R2
For 2008 servers should have http://support.microsoft.com/kb/958124 and http://support.microsoft.com/kb/973995 hotfixes installed.
For 2008 R2 either SP1 or http://support.microsoft.com/kb/981314 hotfix should be installed.
- Make sure the windows firewall or other firewall are not enabled on the DCs. If it does't, then make sure the WMI exceptions are allowed per this link http://tools.cisco.com/squish/d3694
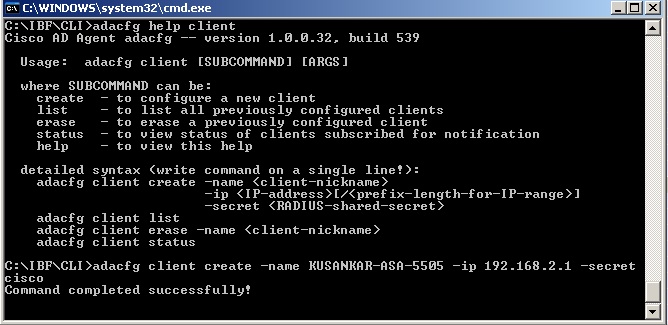
adacfg client create
- From the command line prompt, type cd C:\IBF\CLI (create the ASA as a client on the AD Agent Server). The -secret is the Radius-shared-secret.
adacfg client create –name KUSANKAR-ASA-5505 –ip 192.168.2.1/32 –secret cisco At the command prompt type "adacfg help client" to get the options and sample command syntaxadacfg dc create
- From the command line prompt, type cd C:\IBF\CLI (create all the DCs from which the AD Agent will receive logon logoff events)
Gather the following information
DC - Name
DC - Host name or FQDN
DC - user (must be a member of domain admin group)
Password of the above user-ID
To find the FQDN
- On the Windows Taskbar, click Start > Programs > Administrative Tools > Active Directory Domains and Trusts.
- In the left pane of the Active Directory Domains and Trusts dialog box, look under Active Directory Domains and Trusts. The FQDN for the computer or computers is listed.
adacfg dc create -name KS -host kurelisankar -domain dc1.sample.com -user Administrator -password ww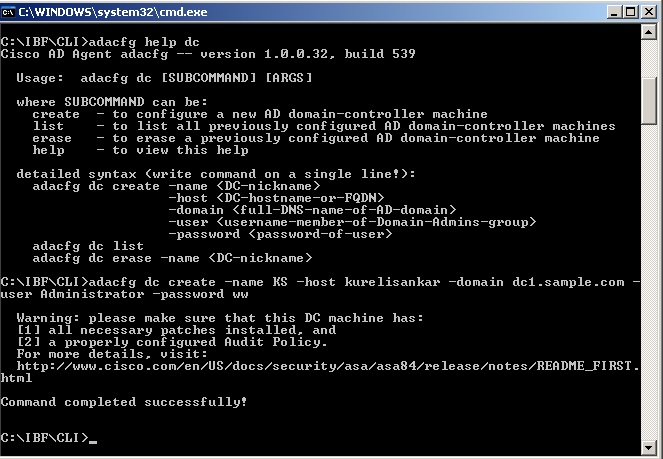
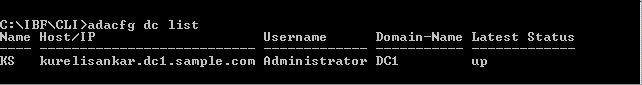
Once the DC has been added via the "adacfg dc create" command, we can verify the status by the "adacfg dc list" command and make sure the DC shows "UP".
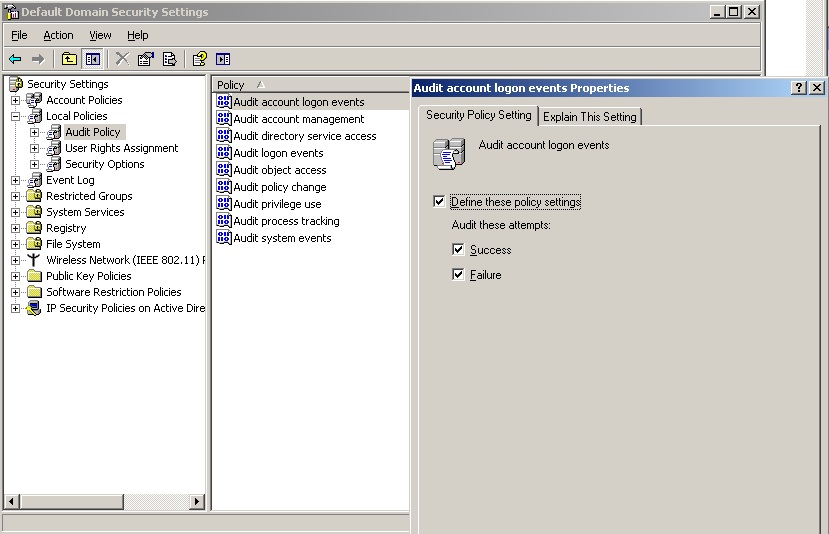
- Make sure the DCs are configured to send logon logoff events to the security event log.
a. To enable 672/673 (or 4768/4769 for Windows 2008 ) logon events in the Domain Controller event log, choose Start > Administrative Tools > Domain Controller Security Policy on each Domain Controller machine.
b. Choose Security Settings > Local Policies > Audit Policy.
c. Define the policy setting for the Audit Account login events policy (audit success). See screen shot below:
- Make sure the WMI (Windows Management Instrumentation) Service is started on the AD Agent and the Domain Controllers and the firewall on both these units are either turned off or are allowing the following ports. The following list does not include the dynamically allocated (random) port numbers that are used by WMI.
1645, 1646, 1812, 1813 - udp
888 - tcp
3. Configure the AD Agent on the ASA
ASA config:
Gather the following information:
a. AD Agent IP address (AD Agent could be installed on the DC)
b. Shared secret between ASA and AD agent (cisco)
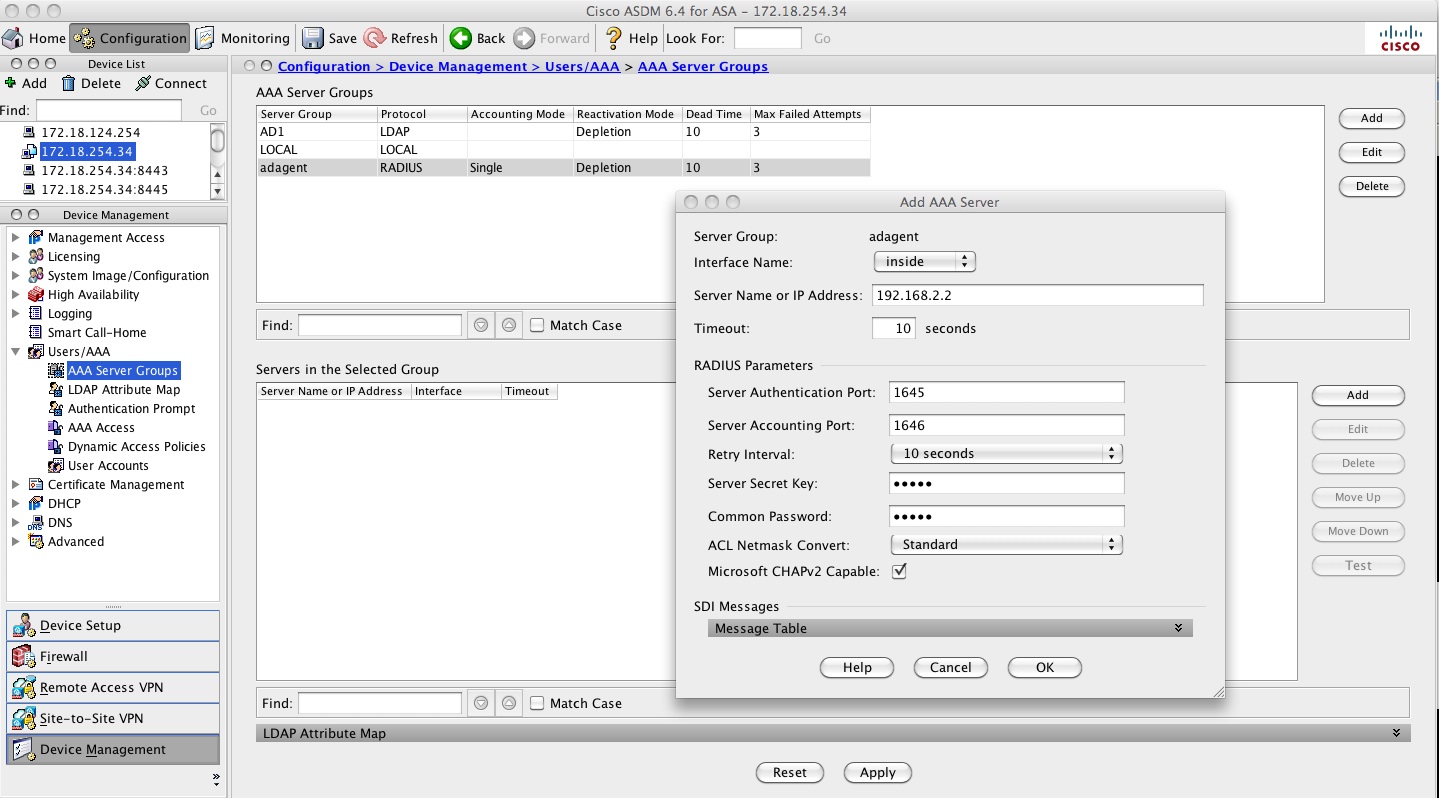
KUSANKAR-ASA-5505(config)# aaa-server adagent protocol radius
KUSANKAR-ASA-5505(config-aaa-server-group)# ad-agent-mode
KUSANKAR-ASA-5505(config-aaa-server-group)#aaa-server adagent (inside) host 192.168.2.2
KUSANKAR-ASA-5505(config-aaa-server-host)# key cisco
KUSANKAR-ASA-5505(config-aaa-server-hos)# user-identity ad-agent aaa-server adagent
Here is the screen shot to configure it from the ASDM side:
Ping and AD-Agent test from the ASA and ping test from AD-Agent:
Test the connectivity between ASA and the adagent with the command "test aaa-server ad-agent adagent". This test will be successful only if the "name" that was used in "adacfg dc create -name KS -host kurelisankar -domain dc1.sample.com -user Administrator -password ww", in this case "KS" can be resolved to the DC's IP address. The netbios name KS here is case sentisive.
From AD-Agent:
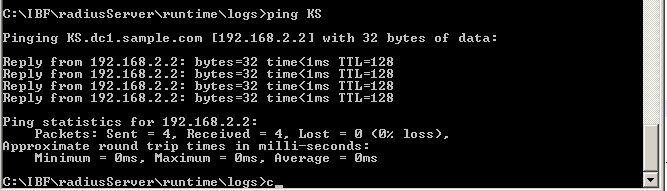
From ASA:
KUSANKAR-ASA-5505# ping KS.dc1.sample.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
KUSANKAR-ASA-5505# test aaa-server ad-agent adagent
Server IP Address or name: 192.168.2.2
INFO: Attempting Ad-agent test to IP address <192.168.2.2> (timeout: 12 seconds)
INFO: Ad-agent Successful
4. Configure Identity Options on the ASA
Configure user-identity config on the ASA. user-identity domain can be different from the e-mail domain of the company or the domain-name configured on the ASA. The domain name comes from the simple NETBIOS name of the Active Directory Domain. How to find the NETBIOS name of the AD domain? Very simple. Look at the screen shot below. NETBIOS name is case sensitive. If this is incorrect then the ASA will not make a query out on port 389 to get the users and groups from the AD Server.
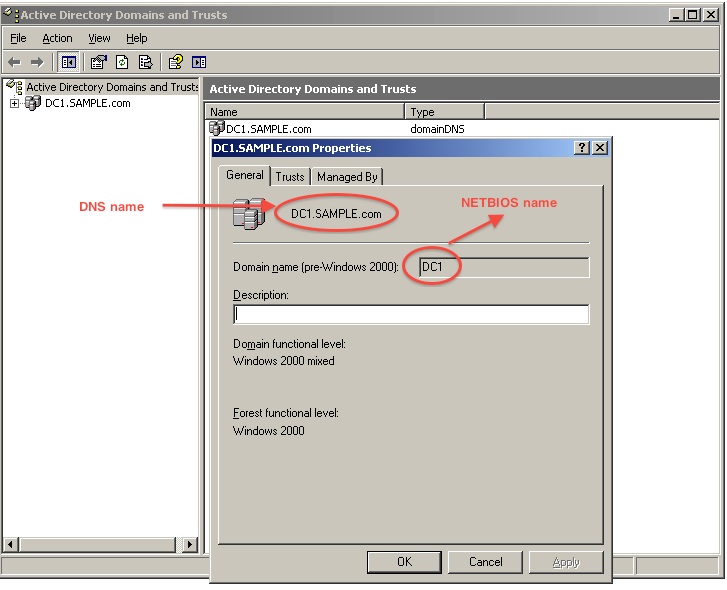
hostname(config)#user-identity domain DC1 aaa-server AD1
hostname(config)#user-identity default-domain DC1
User-identity config on the ASDM side:
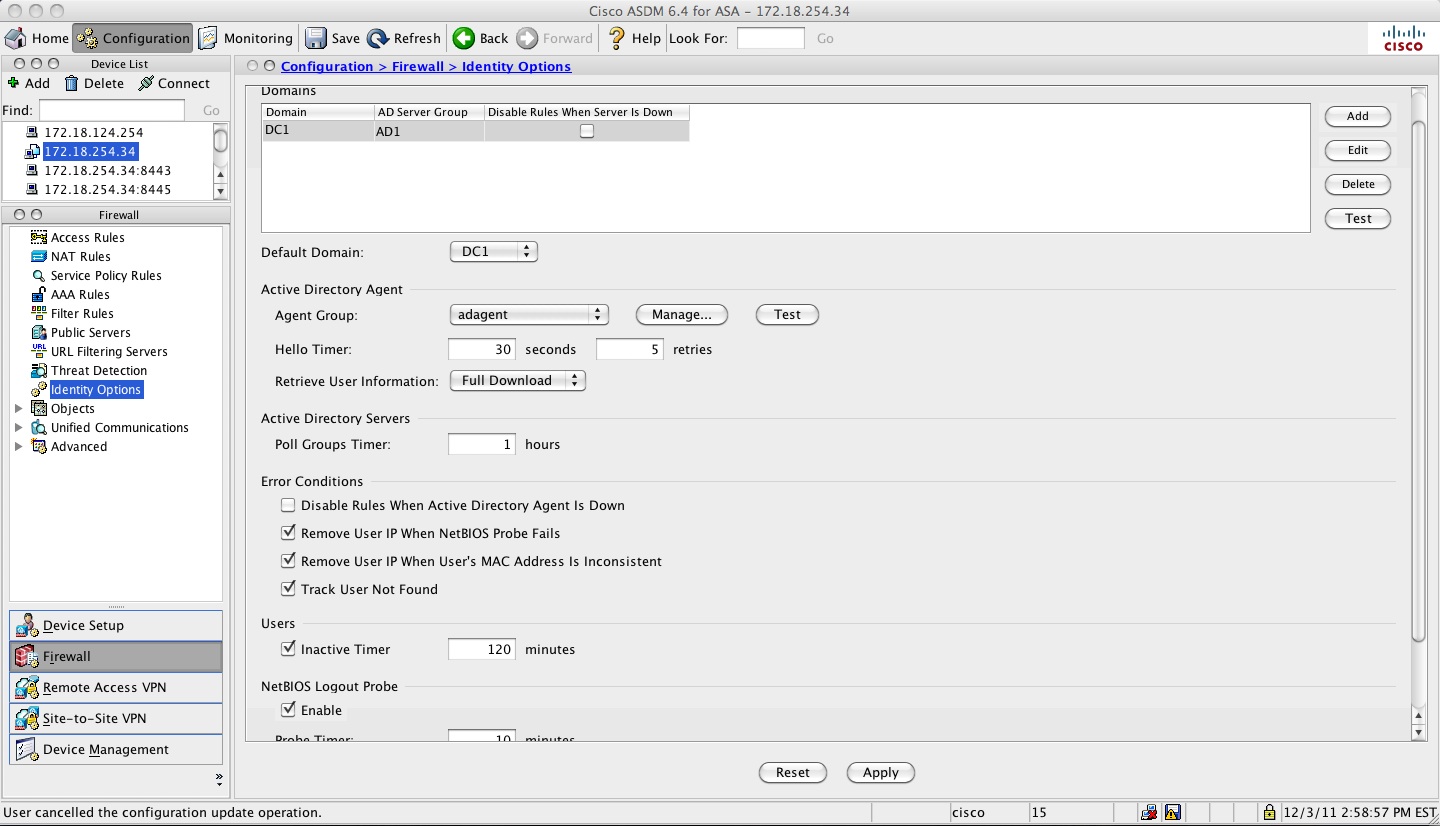
user-identity optional setting:
** The following commands are optional **
hostname(config)# user-identity logout-probe netbios local-system probe-time minutes 10 retry-in seconds 10 retry-count 2 user-not-needed
hostname(config)# user-identity inactive-user-timer minutes 120
hostname(config)# user-identity poll-import-user-group-timer hours 1
hostname(config)# user-identity action netbios-response-fail remove-user-ip
hostname(config)# user-identity user-not-found enable
hostname(config)# user-identity action mac-address-mismatch remove-user-ip
hostname(config)# user-identity ad-agent active-user-database full-download
user-identity optional setting from ASDM that matches the above settings:
5. Configure Identity-based (AD user/group based) Access Rules on the ASA.
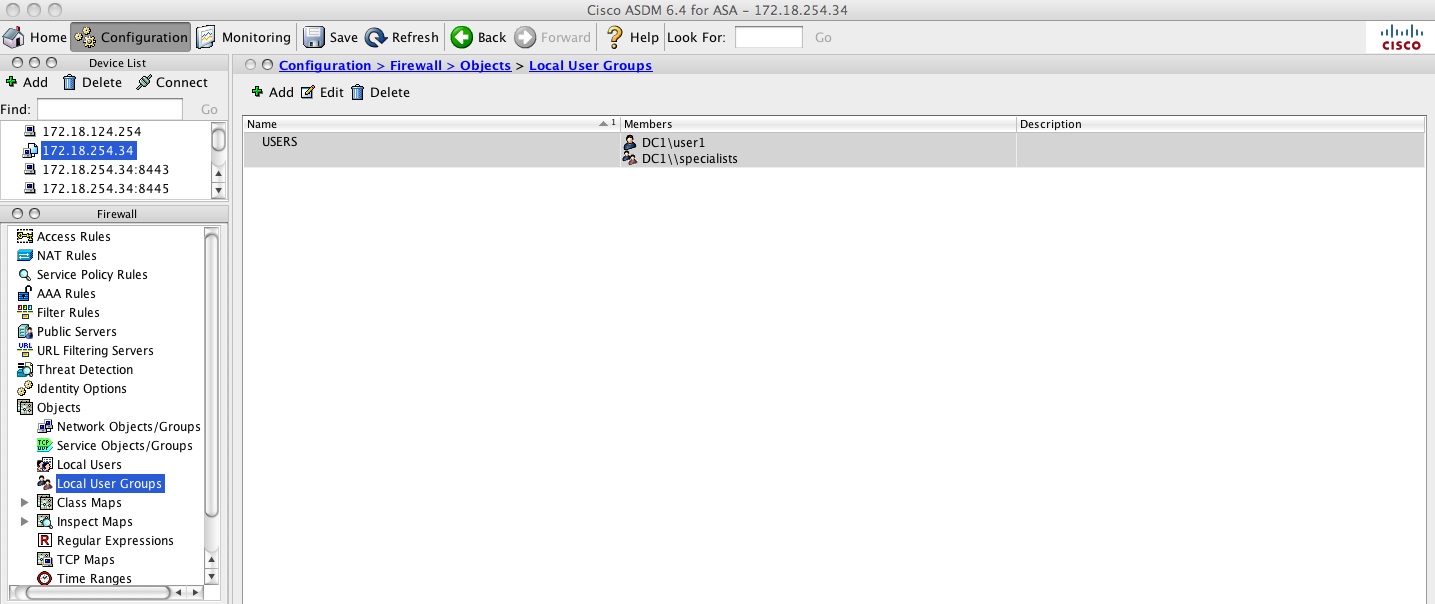
hostname(config)# object-group user USERS
hostname(config-user-object-group)# user DC1\user1
hostname(config-user-object-group)# user-group DC1\\specialists
hostname(config-user-object-group)# exit
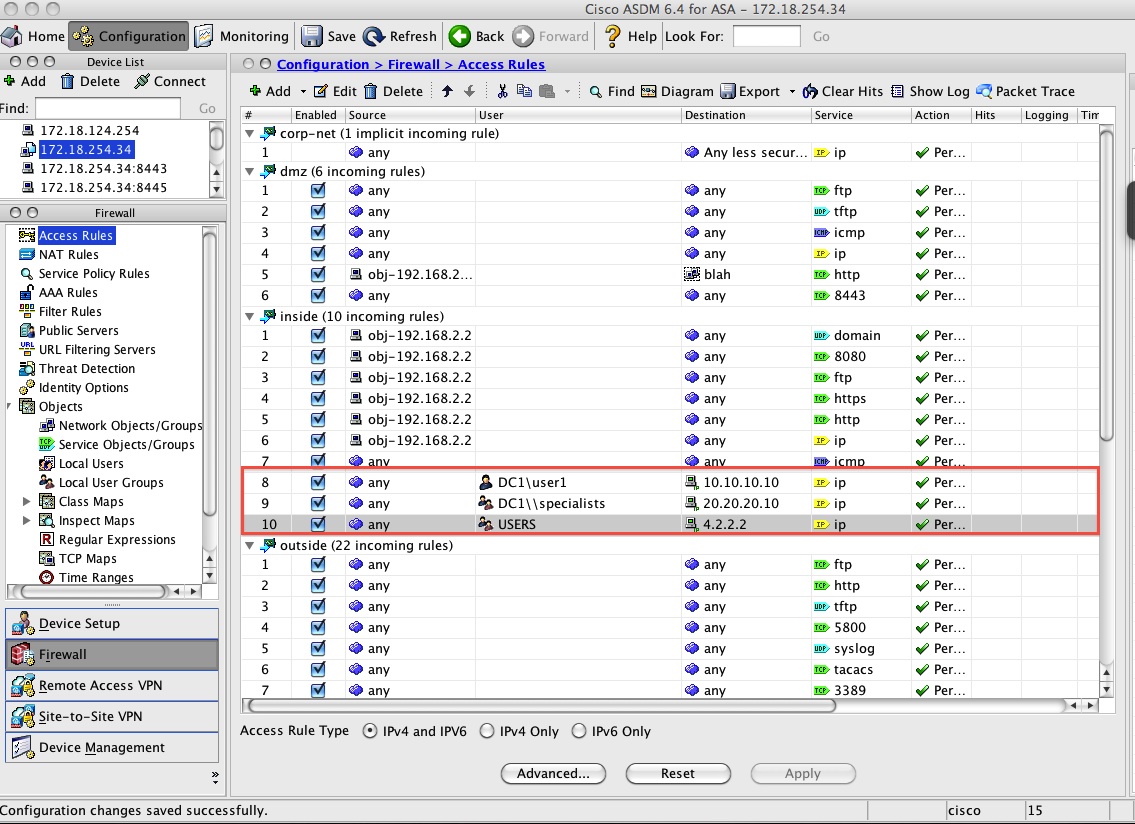
access-list inside-acl extended permit ip user DC1\user1 any host 10.10.10.10
access-list inside-acl extended permit ip user-group DC1\\specialists any host 20.20.20.10
access-list inside-acl extended permit ip object-group-user USERS any host 4.2.2.2
Here is the equivalent of the above from ASDM.
object-group user :
ACL configuration using user, group and object-group-user:
Show commands
show user-identity user active show user-identity user active domain DC1show user-identity user active domain DC1 list
KUSANKAR-ASA-5505# sh user-identity user active domain DC1 list detail
Total active users: 1 Total IP addresses: 1
DC1: 1 users, 1 IP addresses
DC1\Administrator: 0 active conns; idle 0 mins
192.168.2.2: login 99 mins, idle 0 mins, 0 active conns
show user-identity user inactive show user-identity user inactive domain DC1
KUSANKAR-ASA-5505# show user-identity user inactive user-group DC1\\specialists
Total inactive users: 1
DC1\user2
show user-identity user all
show user-identity user all list
KUSANKAR-ASA-5505# show user-identity user all list detail
Total users: 3 Total IP addresses: 1
DC1\Administrator: 2 active conns; idle 0 mins
192.168.2.2: login 114 mins, idle 0 mins, 2 active conns
169.254.218.201: inactive
169.254.25.142: inactive
DC1\user1: 0 active conns
DC1\user2: 0 active conns
This below command shows all the IP addresses for which the ASA hasn't received IP to USER mapping from the AD-Agent.
KUSANKAR-ASA-5505# sh user-identity user-not-found
10.117.14.72
14.36.100.2
14.36.1.106
14.36.109.44
14.36.1.206
14.36.254.80
14.36.1.36
172.18.254.1
This below command shows the groups that have been activation via access-group, policy-map or caputre.
KUSANKAR-ASA-5505# sh user-identity group
Group ID Activated Group Name (Domain\\Group)
-------- ------------------------------------
1 DC1\\specialists
2 LOCAL\\USERS
This below command gives a good status about the Domain from the ad-agent point of view.
show user-identity ad-agent statistics
KUSANKAR-ASA-5505# sh user-identity ad-agent
Primary AD Agent:
Status up (registered)
Mode: full-download
IP address: 192.168.2.2
Authentication port: udp/1645
Accounting port: udp/1646
ASA listening port: udp/3799
Interface: inside
Up time: 17 hours 16 mins
Average RTT: 0 msec
AD Domain Status:
Domain DC1: up
This below command displays all the groups that the ASA has received from the Domain Controller. Output is partial.
KUSANKAR-ASA-5505# show user-identity ad-groups DC1
Domain:DC1 AAA Server Group: AD1
Group list retrieved successfully
Number of Active Directory Groups: 38
dn: CN=DHCP Administrators,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: DHCP Administrators
sAMAccountName: Domain Users
dn: CN=Domain Guests,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: Domain Guests
dn: CN=Group Policy Creator Owners,CN=Users,DC=DC1,DC=SAMPLE,DC=com
dn: CN=Technologists,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: Technologists
dn: CN=Specialists,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: Specialists
If you need to query one particular group then use this command below:
KUSANKAR-ASA-5505# sh user-identity ad-groups DC1 filter specialists
Domain:DC1 AAA Server Group: AD1
Group list retrieved successfully
Number of Active Directory Groups: 1
dn: CN=Specialists,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: Specialists
If you need to filter one particular user then, issue this command below
KUSANKAR-ASA-5505# sh user-identity ad-user DC1 filter user1
Domain:DC1 AAA Server Group: AD1
User list retrieved successfully
Number of Active Directory Users: 1
dn: CN=Ashley Smith,CN=Users,DC=DC1,DC=SAMPLE,DC=com
sAMAccountName: user1
If you need to see the connections opend by user-identity users issue this command below
KUSANKAR-ASA-5505# sh conn user-identity
9 in use, 4379 most used
TCP outside 172.18.109.166:8014 inside 192.168.2.2:3190, idle 0:04:15, bytes 626, flags UO
TCP outside 172.28.128.140:443 dmz 14.36.109.44:4604, idle 0:00:00, bytes 0, flags saA
TCP outside 172.24.180.18:443 dmz 14.36.109.44:4603, idle 0:00:01, bytes 0, flags saA
TCP outside 10.117.14.72:53999 inside (DC1\Administrator) 192.168.2.2:5900, idle 0:00:00, bytes 21614768, flags UIOB
If you need to know the IP mapping of a user you can issue this command below
KUSANKAR-ASA-5505# sh user-identity ip-of-user DC1\Administrator det
DC1\192.168.2.2 (Login) Login time: 150 mins; Idle time: 0 mins; 2 active conns
If you need user maping of an IP then issue this command below
KUSANKAR-ASA-5505# sh user-identity user-of-ip 192.168.2.2
DC1\Administrator (Login)
KUSANKAR-ASA-5505#
KUSANKAR-ASA-5505#
If you need user mapping of a group then issue this commnad below. New users added to an AD group, takes about 8 hours
for the ASA to get the user-group mappings from the AD. We can do that manually on the ASA by "user-identity update import-user"
and make sure they all users that belong in the group show up by issuing "show user-i user-of-gorup CHAS\\monkey" and check the user-group mappings.
KUSANKAR-ASA-5505#show user-i user-of-gorup CHAS\\monkeyOther useful show commands:
show user-identity statistics user
show user-identity statistics top user
sh asp table classify domain user-statistics
Debugs
debug user-identity user
debug user-identity user-group
debug user-identity ad-agent
debug-user-identity ldap
debug user-identity logout-probe
debug user-identity acl
debug user-identity tmatch
debug user-identity fqdn
debug user-identity process
debug user-identity debug
debug user-identity error
debug ldap 255
Syslogs
746001-746019
Common Problems
AD Agent is unable to talk to the DC - ADObserver debug log shows ERROR: Failed to register
How to enable adobserver debug log:
In the AD-Agent computer under the folder IBF\adobserver there is a file named "logconfig.ini". We need to enable debug log in this file by changing LOG_NONE to LOG_DEBUG and restarting the AD Agent service.
[logger]
;this is the logging level
;logging levels are: LOG_VERBOSE, LOG_DEBUG, LOG_INFO, LOG_WARN, LOG_ERROR, LOG_FATAL
;to disable log, set LOG_LEVEL=LOG_NONE, this is the default.
LOG_LEVEL=LOG_DEBUG
Problem: The adObserver debug logs give the following:
Thu Jan 05 10:03:18 2012: ~~~~ Logger Started! Logging Level: LOG_DEBUG ~~~~
Thu Jan 05 10:03:18 2012: INFO: ------------ IBF PIP++ adObserver (version 1.0.0.32, build 539) started ------------
Thu Jan 05 10:03:18 2012: INFO: NOTE: Using real IPs (did not find ADO_RANDOM_IP in environment)
Thu Jan 05 10:03:18 2012: DEBUG: Initializing Winsock
Thu Jan 05 10:03:18 2012: DEBUG: Winsock Initialized
Thu Jan 05 10:03:18 2012: DEBUG: Found local machine FQDN: praprama.praprama1.DC.cisco.com
Thu Jan 05 10:03:18 2012: INFO: Connecting to configuration server
Thu Jan 05 10:03:18 2012: INFO: Configuration loaded successfully from server
Thu Jan 05 10:03:18 2012: DEBUG: EventCallback and DcStatusCallback initialized successfully
Thu Jan 05 10:03:18 2012: DEBUG: Notifier Thread: thread message queue initiated successfully
Thu Jan 05 10:03:18 2012: DEBUG: Notifier thread started successfully
Thu Jan 05 10:03:18 2012: INFO: adding dc: prap with guid: 1325786574-4-436376122
Thu Jan 05 10:03:18 2012: EXCEPTION OCCURED: .\DcMonitor.cpp:373 getDcVersion: Error with ConnectServer for DC: dc name: praprama hostname: praprama domain: praprama1.DC.cisco.com username: Administrator password: <hidden> Error code: 80041064
Thu Jan 05 10:03:18 2012: .\DcMonitor.cpp:373 getDcVersion: Error with ConnectServer for DC: dc name: praprama hostname: praprama domain: praprama1.DC.cisco.com username: Administrator password: <hidden> Error code: 80041064
Thu Jan 05 10:03:18 2012: EXCEPTION OCCURED: .\DcMonitor.cpp:136 Could not find dc version (in addDc) for DC: dc name: praprama hostname: praprama domain: praprama1.DC.cisco.com username: Administrator password: <hidden>
Thu Jan 05 10:03:18 2012: ERROR: Failed to register DC: dc name: prap hostname: praprama domain: praprama1.DC.cisco.com username: Administrator password: <hidden>. Error returned: .\DcMonitor.cpp:136 Could not find dc version (in addDc) for DC: dc name: praprama hostname: praprama domain: praprama1.DC.cisco.com username: Administrator password: <hidden>. Will wait for next DC list update from configuration server
Checking the DC from the AD Agent box may show the following:
C:\IBF\CLI>adacfg dc list Name Host/IP Username Domain-Name Latest Status ---- ------------ ------------- ----------- ------------- prap praprama Administrator down
Solution:
Host name has to be the netbios case sensitive name. If that does not work then add the DC using it FQDN.
So, instead of using this line
C:\IBF\CLI>adacfg dc create -name prap -host praprama -domain praprama1.DC.cisco.com -user Administrator -password Cisco123
change the above line to the following:
C:\IBF\CLI>adacfg dc create -name prap -host praprama.praprama1.DC.cisco.com -domain praprama1.DC.cisco.com -user Administrator -password Cisco123LDAP server test may fail
Problem
Ldap server test may fail with the following message:
Hostname# test aaa-server authentication ADPROFILE username xxxxx password xxxxxx
Server IP Address or name: 172.20.100.10
INFO: Attempting Authentication test to IP address <172.20.100.10> (timeout: 12 seconds)
ERROR: Authentication Server not responding: AAA Server has been removed
Captures taken on the ASA "cap capin int inside match tcp any host 172.20.100.10" may show the following:
indicating strong authentication required - meaning ldap over ssl.
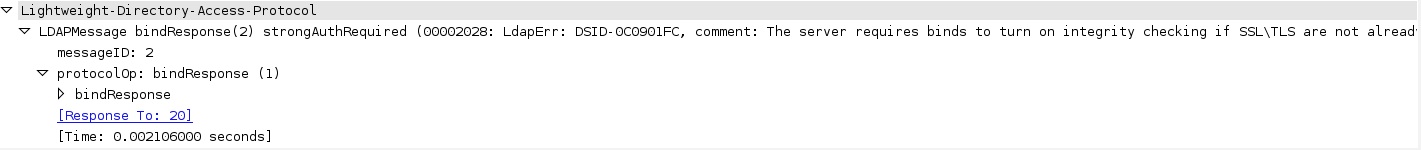
Testing from ASDM may show this error:
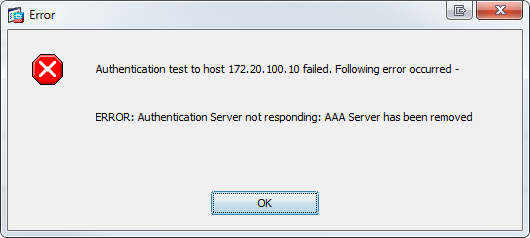
Solution:
adding ldap over ssl in the config will resolve the issue. aaa-server AD1 protocol ldap
aaa-server AD1 (inside) host 172.20.110.10
ldap-over-ssl enable
server-port 636
AD may not send ip address/logon to the ASA
Problem
debugs (debug user-identity ad-agent) may show the following:
idfw_proc[0]: radius query result OK(0), notify caller
idfw_proc[0]: [ADAGENT] radius request STATUS succeeded
idfw_proc[0]: [ADAGENT] domain 'TESTVPN' not configured
ASA config lines show the following:
user-identity domain testvpn.it aaa-server DC01
user-identity default-domain testvpn.it
Solution
Change the config lines on the ASA to reflect the "case" that we see in the debugs
user-identity domain TESTVPN aaa-server DC01
user-identity default-domain TESTVPN
Now the debugs show the following:
idfw_adagent[0]: [ADAGENT] processing RADIUS request from 192.168.2.100/5851
idfw_adagent[0]: [ADAGENT] update 192.168.2.213 <-> TESTVPN\user01 iptype 0 origin 0.0.0.0
idfw_adagent[0]: [ADAGENT] reply CoA-ACK to 192.168.2.100/56086
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi
Somebody solved a problem of several users using one IP address? as a rule at use of Windows terminal servers
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi all.
In Windows 7 clients do not work. in xp everything works fine.
empirically found that I do with service "net send" in windows 7 it is not.
What to do?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am doing some research and looking specifically for wccp redirection to Ironport based on IDFW. It says that feature is not supported but later on you mentioned:
Not that I have heard. We have
- ironport wccp
- botnet - also with ironport
- CSC module for certain models of ASA - for content
Is that functionality now supported?
Thanks,
Oscar Perez
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great job Kureli, it really helped me set this up quickly, although, most of us are trying to set this up with an account that does not have domain admin rights and getting Permissions right in Windows is NOT easy, the way to get permission to read the security event log is really bad and tedious and convoluted. Does anyone have an easy way to setup the Security Event log read permissions to a non Domain Admins user?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am thinking to set up Identity Firewall functionality too for our environment. I had a couple of questions. Is the new version of AD Agent now called CDA (Context Directory Agent)? Also will this support Windows 2012?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello
Does this feature supported on ASA module?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Glad to hear Pete. Sorry just saw these messages on my doc. AD agent has been replaced with CDA now. It is free and runs as a VM. Very easy install. What did you all decide? ASA-CX with CDA is great. Have you tried that out?
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes. It should be.
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I hear you. It is hard if the user isn't a domain admin. If you follow all the steps in our guide then, it just works perfectly. Just takes some time.
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No. We do have an enhancement request filed.
CSCti81922 IDFW: Multiple user login from same ip makes the previous user inactive (enhancement request)
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please note that I had to install KB270537 (http://support.microsoft.com/kb/2705357) on one of my DCs that kept getting status down. After installing the KB and restarting the WMI service we finally got status UP.
Cheers
Rolf
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
thanks for the great description. I have just one simple question. Is it possible two run the native MS radius service and the AD-Agent radius service.
I want to install the AD-Agent on an existing Windows2008 R2 E Server. The server is right now used as AD and Radius Sever.
Can I use MS Radius Server on udp/1811 and udp/1812 and AD-Agent on 1645 and 1646?
Thanks for help!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I realise this is an old post, but I am having a problem registering the DC - and this is the only post on the internet that covers it.
I am getting the error "Error returned: .\DcMonitor.cpp:136 Could not find dc version (in addDc) for DC"
I have tried cases sensitive hostname as we Windows' Computer Porperties dialog (the ADOObserverLog still show lowercase). Not sure where else to look.
What is "addDc" ? Is this an Active Directory property? Something in WMI? I've looked around and can't find references to this so I'm not sure what the ADObserver is actually looking for.
Any help?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Thanks for sharing, this guide is very useful.
I just have one question. Is CDA support VPN with Entrust authentication?
The VPN setting with two-factor authentication. It run OK and CDA receive IP mapping after authenticated from AD. But my issue is ASA doesn't receive IP mapping from CDA. Any advise for this case?
Note: IDFW is running well with other configuration (ACL).
Thanks,
Vo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can I create user identity aware policy if an AD user's workstation is not in domain controller ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: