- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA Phone Proxy In Mixed Mode sample configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-10-2009 04:33 AM - edited 03-08-2019 05:59 PM
Overview
This document is designed as a supplement to ASA Phone Proxy sample configuration in 8.0 article. Please review that parent document to familiarize yourself with the feature first. The rest of this guide will present a Phone Proxy configuration example where the CallManager cluster is operating in Mixed Mode and the remote phone is natively configured for encryption. The screenshots are taken from a CallManager running 6.x software, so you may need to adjust these steps based on the particular version that you're running.
Limitations
In order for the remote phone to be able to call inside users who are registered to the CallManager in encrypted mode, the firewall must be running 8.2 or higher software. Otherwise, either all phones need to be registered through Phone Proxy or all inside phones must be configured in non-encrypted mode.
Configuration Steps
This is the topology of the installation:
- The outside interface is meant to represent the Internet in this example.
- To ensure proper reachability and avoid making the ASA to be the default gateway for the entire network, inside and outside devices will use different Media Termination Addresses (MTAs). The inside devices will use the MTA IP of 172.16.152.219 and the outside phone will use the MTA IP of 192.0.2.2.
- The TFTP server resides on the CallManager which is at 172.16.97.80. The firewall is statically translating this inside ip to the outside with a global address of 192.0.2.10.
- The remote phone has a Locally Signed Certificate (LSC) that was pre-provisioned from the CallManager before moving it to the outside. The local phone has a Manufacturer Installed Certificate (MIC).
- The CallManager is running in Mixed (secure) mode. Both phones are natively configured as Encrypted on the CallManager. Therefore, all communication between the involved parties (ASA, CallManager, inside and outside phones) is encrypted.
- It is assumed that all the basic interface and IP configuration of the firewall is complete. The firewall should be able to reach the CallManager as well as all of the voice endpoints on the inside and the remote phones on the outside. The inside voice devices should be able to reach the inside MTA of the ASA through the inside interface and outside phones should be able to reach the outside MTA of the firewall through the outside interface.
1. If not done yet, we need to set the host and domain names of the ASA. These will be used to generate RSA keys for various Phone Proxy related tasks:
ciscoasa(config)# hostname phone-proxy
phone-proxy(config)# domain-name cisco.com
2. Create RSA keys used for various certificates that Phone Proxy uses. While you can use a single RSA key for all of the relevant trustpoints, we will use a separate key for each one for illustrative purposes. This is the most secure recommended practice. The first keypair will be linked to the "server" trustpoint that the firewall will use to respond to any incoming connections (secure Skinny from the remote phone, TFTP configuration transfer, and so on):
phone-proxy(config)# crypto key generate rsa label phoneproxy-main modulus 1024
INFO: The name for the keys will be: phoneproxy-main
Keypair generation process begin. Please wait...
When the ASA itself needs to create a secure connection on behalf of a remote client (in this case, the outside phone), it will have to generate a dynamic locally signed certificate. The following keypair will be used by the "signer" trustpoint performing this task:
phone-proxy(config)# crypto key generate rsa label phoneproxy-ldc-signer modulus 1024
INFO: The name for the keys will be: phoneproxy-ldc-signer
Keypair generation process begin. Please wait...
Finally, this keypair will be used to generate each individual dynamically generated certificate on behalf of remote phones:
phone-proxy(config)# crypto key generate rsa label phoneproxy-ldc-clients modulus 1024
INFO: The name for the keys will be: phoneproxy-ldc-clients
Keypair generation process begin. Please wait...
3. Once the keypairs are created, we'll define the actual trustpoints and generate the associated certificates. First, we'll create the "server" trustpoint used by the firewall to respond to secure connections as outline above and generate the self-signed certificate. We'll reference 'phoneproxy-main' keypair:
phone-proxy(config)# crypto ca trustpoint phoneproxy-main
phone-proxy(config-ca-trustpoint)# enrollment self
phone-proxy(config-ca-trustpoint)# keypair phoneproxy-main
phone-proxy(config-ca-trustpoint)# exit
phone-proxy(config)# crypto ca enroll phoneproxy-main
% The fully-qualified domain name in the certificate will be: phone-proxy.cisco.com
% Include the device serial number in the subject name? [yes/no]: no
Generate Self-Signed Certificate? [yes/no]: yes
Similarly, we'll create the "signer" trustpoint and the respective certificate used as the root for dynamically generated client certificates. We'll use 'phoneproxy-ldc-signer' keypair:
phone-proxy(config)# crypto ca trustpoint phoneproxy-ldc-signer
phone-proxy(config-ca-trustpoint)# enrollment self
phone-proxy(config-ca-trustpoint)# keypair phoneproxy-ldc-signer
phone-proxy(config-ca-trustpoint)# proxy-ldc-issuer
phone-proxy(config-ca-trustpoint)# exit
phone-proxy(config)# crypto ca enroll phoneproxy-ldc-signer
% The fully-qualified domain name in the certificate will be: phone-proxy.cisco.com
% Include the device serial number in the subject name? [yes/no]: no
Generate Self-Signed Certificate? [yes/no]: yes
Note that even though the names of the trustpoints match the respective names of the keypairs, it is not a requirement.
4. At this point, we will need to exchange some certificate information between the ASA and the CallManager. Since the firewall will be generating dynamic certificates on behalf of the remote phones that are connecting to the CallManager, we need to import the "signer" root certificate to the CallManager's certificate trust list. First, we export the certificate from the respective trustpoint of the ASA:
phone-proxy(config)# crypto ca export phoneproxy-ldc-signer identity-certificate
The PEM encoded identity certificate follows:
-----BEGIN CERTIFICATE-----
MIIBwzCCASygAwIBAgIE9zznSTANBgkqhkiG9w0BAGQFADAmMSQwIgYJKoZ33vcN
AQkCFhVwa39uZS1wcm94eS5jaXNjby5jb20wHhcNMDkwNDE2MTQxMzExWhcNMTkw
NDE0MTQxMzExWjAmMSQwIgYJKoZIhvcNAQkCFhVwaG9uZS1wcm94eS5jaXNjby5j
b20wgZ8wDQYJKoZIh444AQEBAQADgY0AMIGJAoGBAMw84wGRZWZw6XZGDPzqI/JB
t2XHHGSrwsGP+LIPaoEstjF/QTYQCMm2sskkCWxZEPlfDmXZaMwYo6z9+CEXLSS4
0EEKl5CKmToy5+8Mibp3iGVFOv07m4GkP6C2UBsNKS01GAPvi6Wch9nOa4kVBti9
tsuw4dR3Gvtn7NzrCT7F22MBAAEwDQYJKoZIhvcNAQEEBQADgYEAfj9bWLzaT77z
Fg4VpeDUDGYeMEpDUe6653ZqgcRxRVW4Sxz1oztjhqzMboilFm88txq4Ump/uZfg
SJoLaPTk6qXNRLeultNWuF0Q3WDqnC4HqBCoPm8552K1f52k2AA+kFM4b5R55nNd
VliesHizS6fRIdEcX0LrUGvx/NpxzfI=
-----END CERTIFICATE-----
Copy the portion of the output highlighted in bold above into a text file and save it on the local computer. We will now use it to import the certificate to the CallManager.
5. Go to the CallManager web interface, select "Cisco Unified OS Administration" on the navigation pulldown menu in the upper right corner, and click "Go." Log into the OS administration interface:
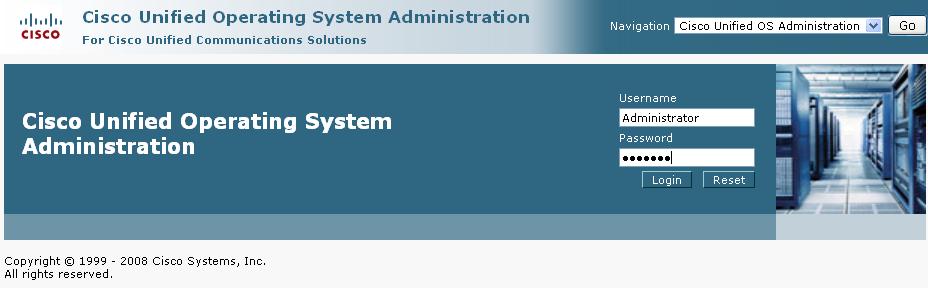
Once logged in, go to "Security -> Certificate Management" screen. In there, click on "Upload Certificate" to import the firewall's "signer" certificate into the CallManager. In the popup window, select "CallManager-trust" as the Certificate Name and click "Browse" to point to the certificate file that you saved in the previous step. At the end, click "Upload File" to finish the import process:
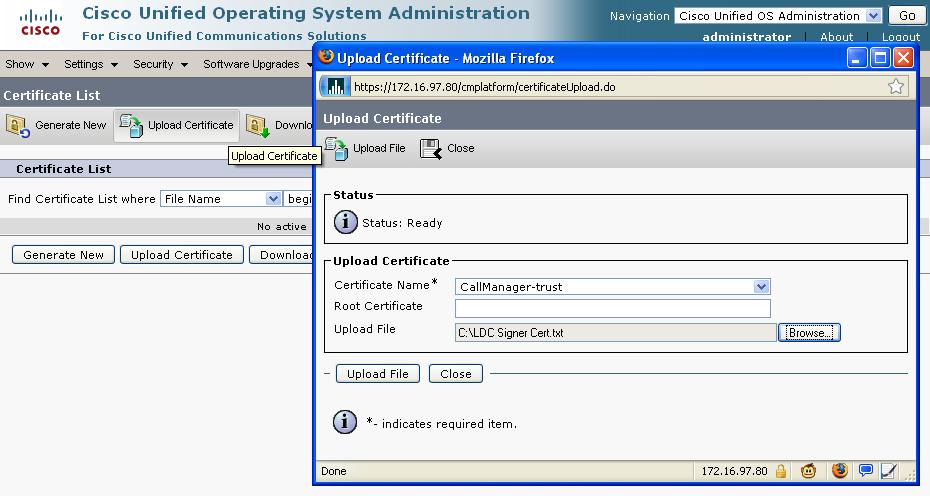
If you get an error saying that the certificate is not in the X.509 format, make sure that you did answer this question in step 3 with a "no:"
% Include the device serial number in the subject name? [yes/no]: no
If necessary, repeat the certificate enrollment process in step 3 and export the certificate again as shown in step 4.
Once the certificate is successfully uploaded, you can close the popup window. However, do not log out of the CallManager or navigate away from the "Certificate List" screen just yet.
6. Now that the CallManager has the ASA's certificate in its trust list, we'll need to export some or all of the following items from the CallManager to import them back to the firewall later on:
- Cluster CTL file (only if some of the remote phones use LSCs -- refer to step 6a)
- Cisco_Manufacturing_CA, CAP-RTP-001, and CAP-RTP-002 trust certificates as well as CallManager indentity certificate (only if some of the remote phones use MICs -- refer to step 6b).
a. Perform this substep only if you plan to use LSCs on some of the remote phones connecting through Phone Proxy. If you're not planning on using LSCs on the remote phones, skip to step 6b.
Under the same "Security -> Security Management" screen on the CallManager interface, click "Download CTL" button and and save the file to a TFTP, FTP, or HTTP server accessible from the ASA that is being configured for Phone Proxy:
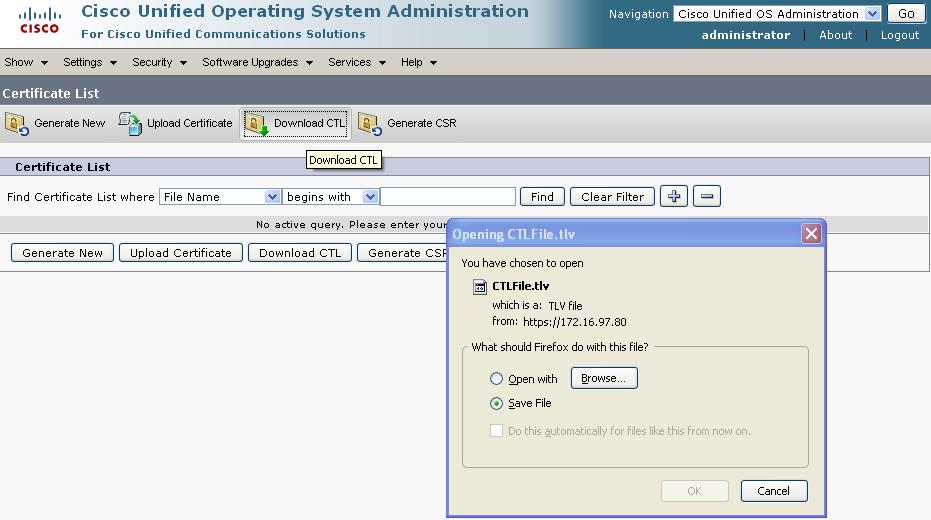
b. Perform this sub step only if you plan to use MICs on some of the remote phones connecting through Phone Proxy. Bear in mind that if a remote phone has an LSC installed, it will have priority over MIC. Otherwise, skip to step 7.
Under the same "Security -> Security Management" screen on the CallManager interface, click "Find" button on the "Certificate List" page to display all of the certificates used by the CallManager. As indicated above, you need to export the following File Names under "CallManager-trust" Certificate Name:
- Cisco_Manufacturing_CA
- CAP-RTP-001
- CAP-RTP-002
You would also need to export the following File Name under "CallManager" Certificate Name:
- CallManager
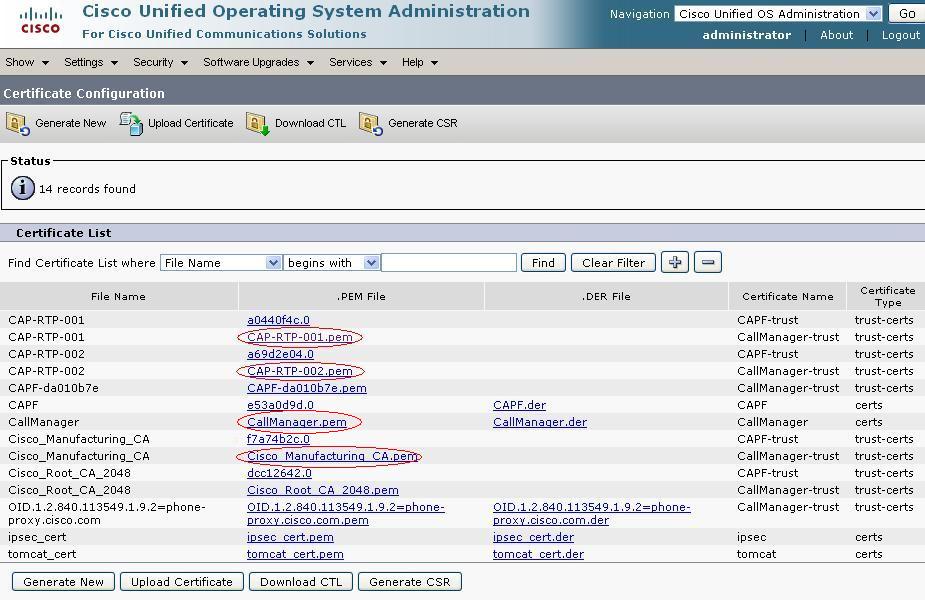
For each of the certificates circled above, click on the corresponding link and download it as a PEM file:
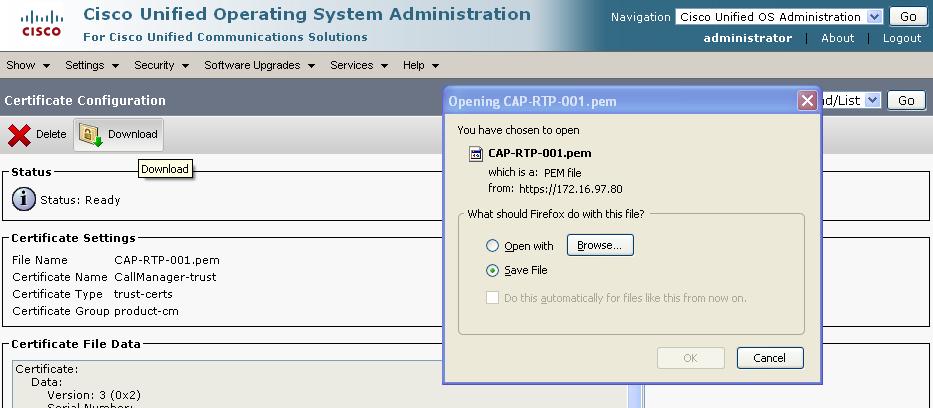
At this point, we're done with the CallManager side of the configuration, so you can log out of the interface and move back to the firewall.
7. Now, we need to import the information exported from the CallManager in the previous step to the ASA. Once again, you may need to only perform one of the sub stems here depending on whether your remote phones will be using LSCs, MICs, or both.
a. Perform this sub step only if you plan to use LSCs on some of the remote phones connecting through Phone Proxy. If it's the case, make sure you performed step 6a. If you're not planning on using LSCs on the remote phones (just MICs), skip to step 7b.
We'll upload the previously exported CallManager cluster's CTL file to the flash. If you have a failover pair of ASAs, make sure to upload it to both devices under the same name. You can use TFTP, FTP, or HTTP; we'll use TFTP in this case:
phone-proxy# copy tftp://172.16.171.125/CTLFile.tlv flash:
Address or name of remote host [172.16.171.125]?
Source filename [CTLFile.tlv]?
Destination filename [CTLFile.tlv]?
Accessing tftp://172.16.171.125/CTLFile.tlv...!!
Writing file disk0:/CTLFile.tlv...
!!
5312 bytes copied in 0.110 secs
phone-proxy#
b. Perform this sub step only if you plan to use MICs on some of the remote phones connecting through Phone Proxy. If it's the case, make sure you followed step 6b. If LSCs will be used on the remote phones, skip to step 8.
Here we will import the four certificates that we exported from the CallManager earlier. This will ensure that the remote phones that only have MICs installed will be able to authenticate with the ASA for Phone Proxy. First, we'll create the respective trustpoints:
phone-proxy(config)# crypto ca trustpoint CiscoManufacturing
phone-proxy(config-ca-trustpoint)# enrollment terminal
phone-proxy(config-ca-trustpoint)# exit
phone-proxy(config)# crypto ca trustpoint CAP-RTP-001
phone-proxy(config-ca-trustpoint)# enrollment terminal
phone-proxy(config-ca-trustpoint)# exit
phone-proxy(config)# crypto ca trustpoint CAP-RTP-002
phone-proxy(config-ca-trustpoint)# enrollment terminal
phone-proxy(config-ca-trustpoint)# exit
phone-proxy(config)# crypto ca trustpoint CallManager
phone-proxy(config-ca-trustpoint)# enrollment terminal
phone-proxy(config-ca-trustpoint)# exit
Second, we'll authenticate the endpoints and paste the actual certificates saved in step 6b:
phone-proxy(config)# crypto ca authenticate CiscoManufacturing
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIE2TCCA8GgAwIBAgIKamlnswAAAAAAAzANBgkqhkiG9w0BAQUFADA1MRYwFAYD
VQQKEw1DaXNjbyBTeXN0ZW1zMRswGQYDVQQDExJDaXNjbyBSb290IENBIDIwNDgw
HhcNMDUwNjEwMjIxNjAxWhcNMjkwNTE0MjAyNTQyWjA5MRYwFAYDVQQKEw1DaXNj
byBTeXN0ZW1zMR8wHQYDVQQDExZDaXNjbyBNYW51ZmFjdHVyaW5nIENBMIIBIDAN
BgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKCAQEAoMX33JaUNRXx9JlOu5tB4X3beRaR
u/NU8kFKlDJiYskj95rnu5t56AcpTjD1rhvFIVZGsPj05o6BuBbMqJuF0kKB23zL
lKkRYRIcXOozIByaFqd925kGauI2r+z4Cv+YZwf0MO6l+IgaqujHPBzO7kj9zVw3
8YaTnj1xdX007ksUqcApewUQ74eeaTEw9Ug2P9irzhXi6FifPmJxBIcmpBViASWq
1d/JyVu4yaEHe75okpOTIKhsvRV100RdRUvsqNpgx9jI1cjtQeH1X1eOUzKTSdXZ
D/g2qgfEMkHFp68dGf/2c5k5WnNnYhM0DR9elXBSZBcG7FNcXNtq6jUAQQIBA6OC
AecwggHjMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFNDFIiarT0Zg7K4F
kcfcWtGwR/dsMAsGA1UdDwQEAwIBhjAQBgkrBgEEAYI3FQEEAwIBADAZBgkrBgEE
AYI3FAIEDB4KAFMAdQBiAEMAQTAfBgNVHSMEGDAWgBQn88gVHm6aAgkWrSugiWBf
2nsvqjBDBgNVHR8EPDA6MDigNqA0hjJodHRwOi8vd3d3LmNpc2NvLmNvbS9zZWN1
cml0eS9wa2kvY3JsL2NyY2EyMDQ4LmNybDBQBggrBgEFBQcBAQREMEIwQAYIKwYB
BQUHMAKGNGh0dHA6Ly93d3cuY2lzY28uY29tL3NlY3VyaXR5L3BraS9jZXJ0cy9j
cmNhMjA0OC5jZXIwXAYDVR0gBFUwUzBRBgorBgEEAQkVAQIAMEMwQQYIKwYBBQUH
AgEWNWh0dHA6Ly93d3cuY2lzY28uY29tL3NlY3VyaXR5L3BraS9wb2xpY2llcy9p
bmRleC5odG1sMF4GA1UdJQRXMFUGCCsGAQUFBwMBBggrBgEFBQcDAgYIKwYBBQUH
AwUGCCsGAQUFBwMGBggrBgEFBQcDBwYKKwYBBAGCNwoDAQYKKwYBBAGCNxQCAQYJ
KwYBBAGCNxUGMA0GCSqGSIb3DQEBBQUAA4IBAQAw8zAtjPLKN0pkmSQpCvKGqkLV
I+ii6itvaSN6go4cTAnPpE+rhC836WVg0ZrG2PML9d7QJwBcbx2RvdFOWFEdyeP3
OOfTC9Fovo4ipUsG4eakqjN9GnW6JvNwxmEApcN5JlunGdGTjaubEBEpH6GC/f08
S25l3JNFBemvM2tnIwcGhiLa69yHz1khQhrpz3B1iOAkPV19TpY4gJfVb/Cbcdi6
YBmlsGGGrd1lZva5J6LuL2GbuqEwYf2+rDUU+bgtlwavw+9tzD0865XpgdOKXrbO
+nmka9eiV2TEP0zJ2+iC7AFm1BCIolblPFft6QKoSJFjB6thJksaE5/k3Npf
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: 6ea241f5 ac9a1148 cc8b4b43 c7c13025
Do you accept this certificate? [yes/no]: yes
Trustpoint 'CiscoManufacturing' is a subordinate CA and holds a non self-signed
certificate.
Trustpoint CA certificate accepted.
% Certificate successfully imported
phone-proxy(config)# crypto ca authenticate CAP-RTP-001
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDqDCCApCgAwIBAgIQdhL5YBU9b59OQiAgMrcjVjANBgkqhkiG9w0BAQUFADAu
MRYwFAYDVQQKEw1DaXNjbyBTeXN0ZW1zMRQwEgYDVQQDEwtDQVAtUlRQLTAwMTAe
Fw0wMzAyMDYyMzI3MTNaFw0yMzAyMDYyMzM2MzRaMC4xFjAUBgNVBAoTDUNpc2Nv
IFN5c3RlbXMxFDASBgNVBAMTC0NBUC1SVFAtMDAxMIIBIDANBgkqhkiG9w0BAQEF
AAOCAQ0AMIIBCAKCAQEArFW77Rjem4cJ/7yPLVCauDohwZZ/3qf0sJaWlLeAzBlq
Rj2lFlSij0ddkDtfEEo9VKmBOJsvx6xJlWJiuBwUMDhTRbsuJz+npkaGBXPOXJmN
Vd54qlpc/hQDfWlbrIFkCcYhHws7vwnPsLuy1Kw2L2cP0UXxYghSsx8H4vGqdPFQ
NnYy7aKJ43SvDFt4zn37n8jrvlRuz0x3mdbcBEdHbA825Yo7a8sk12tshMJ/YdMm
vny0pmDNZXmeHjqEgVO3UFUn6GVCO+K1y1dUU1qpYJNYtqLkqj7wgccGjsHdHr3a
U+bw1uLgSGsQnxMWeMaWo8+6hMxwlANPweufgZMaywIBA6OBwzCBwDALBgNVHQ8E
BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQU6Rexgscfz6ypG270qSac
cK4FoJowbwYDVR0fBGgwZjBkoGKgYIYtaHR0cDovL2NhcC1ydHAtMDAxL0NlcnRF
bnJvbGwvQ0FQLVJUUC0wMDEuY3Jshi9maWxlOi8vXFxjYXAtcnRwLTAwMVxDZXJ0
RW5yb2xsXENBUC1SVFAtMDAxLmNybDAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG
9w0BAQUFAAOCAQEAq2T96/YMMtw2Dw4QX+F1+g1XSrUCrNyjx7vtFaRDHyB+kobw
dwkpohfkzfTyYpJELzV1r+kMRoyuZ7oIqqccEroMDnnmeApc+BRGbDJqS1Zzk4OA
c6Ea7fm53nQRlcSPmUVLjDBzKYDNbnEjizptaIC5fgB/S9S6C1q0YpTZFn5tjUjy
WXzeYSXPrcxb0UH7IQJ1ogpONAAUKLoPaZU7tVDSH3hD4+VjmLyysaLUhksGFrrN
phzZrsVVilK17qpqCPllKLGAS4fSbkruq3r/6S/SpXS6/gAoljBKixP7ZW2PxgCU
1aU9cURLPO95NDOFN3jBk3Sips7cVidcogowPQ==
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: 233c8e33 8632ea4e 76d79feb ffb061c6
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
phone-proxy(config)# crypto ca authenticate CAP-RTP-002
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDqDCCApCgAwIBAgIQNT+yS9cPFKNGwfOprHJWdTANBgkqhkiG9w0BAQUFADAu
MRYwFAYDVQQKEw1DaXNjbyBTeXN0ZW1zMRQwEgYDVQQDEwtDQVAtUlRQLTAwMjAe
Fw0wMzEwMTAyMDE4NDlaFw0yMzEwMTAyMDI3MzdaMC4xFjAUBgNVBAoTDUNpc2Nv
IFN5c3RlbXMxFDASBgNVBAMTC0NBUC1SVFAtMDAyMIIBIDANBgkqhkiG9w0BAQEF
AAOCAQ0AMIIBCAKCAQEAxCZlBK19w/2NZVVvpjCPrpW1cCY7V1q9lhzI85RZZdnQ
2M4CufgIzNa3zYxGJIAYeFfcRECnMB3f5A+x7xNiEuzE87UPvK+7S80uWCY0Uhtl
AVVf5NQgZ3YDNoNXg5MmONb8lT86F55EZyVac0XGne77TSIbIdejrTgYQXGP2MJx
Qhg+ZQlGFDRzbHfM84Duv2Msez+l+SqmqO80kIckqE9Nr3/XCSj1hXZNNVg8D+mv
Hth2P6KZqAKXAAStGRLSZX3jNbS8tveJ3Gi5+sj9+F6KKK2PD0iDwHcRKkcUHb7g
lI++U/5nswjUDIAph715Ds2rn9ehkMGipGLF8kpuCwIBA6OBwzCBwDALBgNVHQ8E
BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUUpIr4ojuLgmKTn5wLFal
mrTUm5YwbwYDVR0fBGgwZjBkoGKgYIYtaHR0cDovL2NhcC1ydHAtMDAyL0NlcnRF
bnJvbGwvQ0FQLVJUUC0wMDIuY3Jshi9maWxlOi8vXFxjYXAtcnRwLTAwMlxDZXJ0
RW5yb2xsXENBUC1SVFAtMDAyLmNybDAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG
9w0BAQUFAAOCAQEAVoOM78TaOtHqj7sVL/5u5VChlyvU168f0piJLNWip2vDRihm
E+DlXdwMS5JaqUtuaSd/m/xzxpcRJm4ZRRwPq6VeaiiQGkjFuZEe5jSKiSAK7eHg
tup4HP/ZfKSwPA40DlsGSYsKNMm3OmVOCQUMH02lPkS/eEQ9sIw6QS7uuHN4y4CJ
NPnRbpFRLw06hnStCZHtGpKEHnY213QOy3h/EWhbnp0MZ+hdr20FujSI6G1+L39l
aRjeD708f2fYoz9wnEpZbtn2Kzse3uhU1Ygq1D1x9yuPq388C18HWdmCj4OVTXux
V6Y47H1yv/GJM8FvdgvKlExbGTFnlHpPiaG9tQ==
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: f7e150ea 5e6e3ac5 615fc696 66415c9f
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
phone-proxy(config)# crypto ca authenticate CallManager
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDqDCCApCgAwIBAgIQNT+yS9cPFKNGwfOprHJWdTANBgkqhkiG9w0BAQUFADAu
MRYwFAYDVQQKEw1DaXNjbyBTeXN0ZW1zMRQwEgYDVQQDEwtDQVAtUlRQLTAwMjAe
Fw0wMzEwMTAyMDE4NDlaFw0yMzEwMTAyMDI3MzdaMC4xFjAUBgNVBAoTDUNpc2Nv
IFN5c3RlbXMxFDASBgNVBAMTC0NBUC1SVFAtMDAyMIIBIDANBgkqhkiG9w0BAQEF
AAOCAQ0AMIIBCAKCAQEAxCZlBK19w/2NZVVvpjCPrpW1cCY7V1q9lhzI85RZZdnQ
2M4CufgIzNa3zYxGJIAYeFfcRECnMB3f5A+x7xNiEuzE87UPvK+7S80uWCY0Uhtl
AVVf5NQgZ3YDDDDDDDDDDDD8lT86F55EZyVac0dddddddSIbIdejrTgYQXGP2MJx
Qhg+ZQlGFDRzbHfM84Duv2Msez+l+SqmqO80kIckqE9Nr3/XCSj1hXZNNVg8D+mv
Hth2P6KZqAKXAAStGRLSZX3jNbS8tveJ3Gi5+sj9+F6KKK2PD0iDwHcRKkcUHb7g
lI++U/5nswjUDIAph715Ds2rn9ehkMGipGLF8kpuCwIBA6OBwzCBwDALBgNVHQ8E
BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUUpIr4ojuLgmKTn5wLFal
mrTUm5YwbwYDVR0fBGgwZjBkoGKgYIYtaHR0cDovL2NhcC1ydHAtMDAyL0NlcnRF
bnJvbGwvQ0FQLVJaaaaaaaaaaaaaaaaaaaaaaaaaaaxjYXAtcnRwLTAwMlxDZXJ0
RW5yb2xsXENBUC1SVFAtMDAyLmNybDAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG
9w0BAQUFAAOCAQEAVoOM78TaOtHqj7sVL/5u5VChlyvU168f0piJLNWip2vDRihm
E+DlXdwMS5JaqUtuaSd/m/xzxpcRJm4ZRRwPq6VeaiiQGkjFuZEe5jSKiSAK7eHg
tup4HP/ZfKSwPA40DlsGSYsKNMm3OmVOCQUMH02lPkS/eEQ9sIw6QS7uuHN4y4CJ
NPnRbpFRLw06hnStCZHtGpKEHnY213QOy3h/EWhbnp0MZ+hdr20FujSI6G1+L39l
aRjeD708f2fYoz9wnEpZbtn2Kzse3uhU1Ygq1D1x9yuPq388C18HWdmCj4OVTXux
V6Y47H1yv/GJM8FvdgvKlExbGTFnlHpPiaG9tQ==
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: f7e150ea 5e6e3ac5 615ddc96 66415c9f
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
8. Now that all of the certificate information has been exchanged between the CallManager and the firewall, we can proceed to configuring the actual Phone Proxy feature. First, we will create a CTL file instance to be used by Phone Proxy.
phone-proxy(config)#ctl-file phone-proxy-ctl
a. Perform this sub step only if you plan to use LSCs on some of the remote phones connecting through Phone Proxy. If it's the case, make sure you performed sub steps 6a and 7a. If you're not planning on using LSCs on the remote phones (just MICs), proceed directly to step 8b.
Now we will reference the CallManager cluster's CTL file that we loaded to the flash before:
phone-proxy(config-ctl-file)#cluster-ctl-file disk0:/CTLFile.tlv
INFO: Read 5312 bytes of data from CTL file
At this point, we still need to continue on to sub step 8b.
b. We will use the same ASA's "server" trustpoint for both the TFTP configuration transfer and Secure Skinny connection from the remote phone (the mapped address is used):
phone-proxy(config-ctl-file)#record-entry cucm-tftp trustpoint phoneproxy-main address 192.0.2.100
phone-proxy(config-ctl-file)# no shutdown
Trustpoint '_internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4c4914' is a subordinate CA and holds a non self-signed certificate.
Trustpoint '_internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4c4914' is a subordinate CA.
but certificate is not a CA certificate.
Manual verification required
Trustpoint CA certificate accepted.
Trustpoint '_internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4e2114' is a subordinate CA and holds a non self-signed certificate.
Trustpoint '_internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4e2114' is a subordinate CA.
but certificate is not a CA certificate.
Manual verification required
Trustpoint CA certificate accepted.
Trustpoint CA certificate accepted.
Trustpoint CA certificate accepted.
Trustpoint CA certificate accepted.
INFO: Signature on cluster CTL file validated
Keypair generation process begin. Please wait...
% The fully-qualified domain name will not be included in the certificate
Keypair generation process begin. Please wait...
% The fully-qualified domain name will not be included in the certificate
Keypair generation process begin. Please wait...
% The fully-qualified domain name will not be included in the certificate
INFO: Total CTL File length 5770
INFO: Writing CTL file disk0:/phone-proxy-ctl.tlv to flash...
9. Perform this step only if some remote phones will be using LSCs to connect through Phone Proxy. If so, make sure you had followed substeps 6a, 7a and 8a. If none of the remote phones will have LSCs installed, skip to step 10.
In this step, we'll need to create an entry for the CallManager CAPF certificate under the Phone Proxy CTL file configuration section. This will allow the firewall to correctly authenticate LSC-provisioned phones for both signaling and media sessions as well as facilitate new LSC provisioning for remote phones. We can reference the CAPF certificate from the CallManager cluster's CTL file that had already been imported to the ASA. First, we will issue the following command to determine the internal reference name:
phone-proxy(config)# show run crypto ca trustpoint | include CAPF
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn=CAPF-da010b7e;ou=SJ-CUCM;o=Cisc
Now, we'll create the CAPF record under the CTL file configuration (we'll have to shut down the instance first):
phone-proxy(config)#ctl-file phone-proxy-ctl
phone-proxy(config-ctl-file)#shutdown
phone-proxy(config-ctl-file)#record-entry capf trustpoint _internal_CTL_phone-proxy-ctl_cn=CAPF-da010b7e;ou=SJ-CUCM;o=Cisc address 192.0.2.100
phone-proxy(config-ctl-file)#no shutdown
10. In this step, we will configure the TLS Proxy instance used for transit signaling and media sessions. We will use the internal pre-generated trustpoints from the earlier CTL file configuration and the "signer" trustpoint for outgoing connections on behalf of the remote phones as well as the appropriate keypair dedicated to the dynamically issued certificates:
phone-proxy(config)# tls-proxy phone-proxy-tls
phone-proxy(config-tlsp)# server trust-point _internal_PP_phone-proxy-ctl
phone-proxy(config-tlsp)# client ldc issuer phoneproxy-ldc-signer
phone-proxy(config-tlsp)# client ldc key-pair phoneproxy-ldc-clients
11. At this time, we will configure the appropriate MTA IPs for the inside and outside interfaces. As per the earlier description, the inside devices will use the MTA IP of 172.16.152.219 and the outside phones will use the MTA IP of 192.0.2.2:
phone-proxy(config)# media-termination phone-proxy-media
phone-proxy(config-media-termination)# address 192.0.2.2 interface outside
phone-proxy(config-media-termination)# address 172.16.152.219 interface inside
12. Now, it's time to bring everything together under the main Phone Proxy configuration instance. Notice that the CallManager cluster is configured in Mixed mode:
phone-proxy(config)# phone-proxy asa-phone-proxy
phone-proxy(config-phone-proxy)# media-termination phone-proxy-media
phone-proxy(config-phone-proxy)# tftp-server address 172.16.97.80 interface inside
phone-proxy(config-phone-proxy)# tls-proxy phone-proxy-tls
phone-proxy(config-phone-proxy)# cluster-mode mixed
phone-proxy(config-phone-proxy)# ctl-file phone-proxy-ctl
phone-proxy(config-phone-proxy)# no disable service-settings
13. Now that everything is set up, we enable Phone Proxy on transit TCP/2443 traffic. For simplicity, we will apply it to the global Modular Policy Framework (MPF) policy:
phone-proxy(config)# class-map SECURE_SCCP
phone-proxy(config-cmap)# match port tcp eq 2443
phone-proxy(config)# policy-map global_policy
phone-proxy(config-pmap)# class SECURE_SCCP
phone-proxy(config-pmap-c)# inspect skinny phone-proxy asa-phone-proxy
phone-proxy(config-pmap)# service-policy global_policy global
14. The last step is to permit inbound TFTP (UDP/69) and optional CAPF (TCP/3804) traffic on the outside interface:
access-list INBOUND extended permit udp any host 192.0.2.10 eq 69
access-list INBOUND extended permit tcp any host 192.0.2.10 eq 3804
access-group INBOUND in interface outside
Verifying Phone Proxy Operation
Now that everything is configured, we can point the remote phone proxy phone at the mapped address of the CallManager cluster's TFTP server (192.0.2.100 in this example) and test. First, we check and make sure that the phone has successfully registered:
phone-proxy(config)# show phone-proxy secure-phones
asa-phone-proxy: 1 in use, 1 most used
Interface IP Address Port MAC Timeout Idle
outside 192.0.2.10 41297 001b.2a89.e35c 0:05:00 0:00:00
We also need to confirm that the Secure SCCP session to the CallManager is established through Phone Proxy:
phone-proxy(config)# show phone-proxy signaling-sessions
outside 192.0.2.100:41297 inside 172.16.97.80:2443
Now, let's make a phone call. Once it's connected, we can check the signaling session:
phone-proxy(config)# show phone-proxy signaling-sessions
outside 192.0.2.100:41297 inside 172.16.97.80:2443
Local Media (audio) conn: 192.0.2.100/20138 to 192.0.2.2/29996
Local SRTP key set : Remote SRTP key set
Remote Media (audio) conn: 172.16.152.199/29736 to 172.16.152.219/23306
Notice that both media connection above (on the inside and outside) are using SRTP and hence are encrypted. We can also see that both of these SRTP sessions are actively receiving and transmitting packets which indicates that the call is flowing:
phone-proxy(config)# show phone-proxy media-sessions
2 in use, 2 most used
Media-session: 172.16.152.219/23306 :: client ip 192.0.2.100/20138
Lcl SRTP conn 172.16.152.219/23306 to 172.16.152.199/29736 tx_pkts 4647 rx_pkts 4647
Media-session: 192.0.2.2/29996 :: client ip 172.16.152.199/29736
Lcl SRTP conn 192.0.2.2/29996 to 192.0.2.100/20138 tx_pkts 4646 rx_pkts 4647
Complete Sample Configuration
ASA Version 8.2(0)207
!
hostname phone-proxy
domain-name cisco.com
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.0.2.1 255.255.255.0 standby 192.0.2.10
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 172.16.152.216 255.255.255.0 standby 172.16.152.217
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
description LAN/STATE Failover Interface
!
ftp mode passive
dns domain-lookup outside
dns server-group DefaultDNS
name-server 171.70.168.183
domain-name cisco.com
access-list INBOUND extended permit udp any host 192.0.2.10 eq 69
access-list INBOUND extended permit tcp any host 192.0.2.10 eq 3804
no pager
logging enable
logging timestamp
logging monitor debugging
logging buffered debugging
mtu outside 1500
mtu inside 1500
failover
failover lan unit primary
failover lan interface failover Management0/0
failover link failover Management0/0
failover interface ip failover 1.0.3.1 255.255.255.0 standby 1.0.3.2
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 192.0.2.10 172.16.97.80 netmask 255.255.255.255
access-group INBOUND in interface outside
route outside 0.0.0.0 0.0.0.0 192.0.2.253 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto ca trustpoint phoneproxy-main
enrollment self
keypair phoneproxy-main
crl configure
crypto ca trustpoint phoneproxy-ldc-signer
enrollment self
serial-number
keypair phoneproxy-ldc-signer
proxy-ldc-issuer
crl configure
crypto ca trustpoint _internal_phone-proxy-ctl_SAST_0
enrollment self
fqdn none
subject-name cn="_internal_phone-proxy-ctl_SAST_0";ou="STG";o="Cisco Inc"
keypair _internal_phone-proxy-ctl_SAST_0
crl configure
crypto ca trustpoint _internal_phone-proxy-ctl_SAST_1
enrollment self
fqdn none
subject-name cn="_internal_phone-proxy-ctl_SAST_1";ou="STG";o="Cisco Inc"
keypair _internal_phone-proxy-ctl_SAST_1
crl configure
crypto ca trustpoint _internal_PP_phone-proxy-ctl
enrollment self
fqdn none
subject-name cn="_internal_PP_phone-proxy-ctl";ou="STG";o="Cisco Inc"
keypair _internal_PP_phone-proxy-ctl
crl configure
crypto ca trustpoint CiscoManufacturing
enrollment terminal
crl configure
crypto ca trustpoint CAP-RTP-001
enrollment terminal
crl configure
crypto ca trustpoint CAP-RTP-002
enrollment terminal
crl configure
crypto ca trustpoint CallManager
enrollment terminal
crl configure
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn=CAPF-da010b7e;ou=SJ-CUCM;o=Cisc
enrollment terminal
crl configure
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4c4914
enrollment terminal
crl configure
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4e2114
enrollment terminal
crl configure
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn=parshah-cm6-1.par-shah.com
enrollment terminal
crl configure
crypto ca trustpoint _internal_CTL_phone-proxy-ctl_cn=parshah-cm6-2.par-shah.com
enrollment terminal
crl configure
crypto ca certificate chain phoneproxy-main
certificate 4c3ce749
308201c3 3082012c a0030201 0202044c 3ce74930 0d06092a 864886f7 0d010104
05003026 31243022 06092a86 4886f70d 01090216 1570686f 6e652d70 726f7879
2e636973 636f2e63 6f6d301e 170d3039 30343136 31111210 32305a17 0d313930
34313431 34313032 305a3026 31243022 06092a86 4886f70d 01090216 1570686f
6e652d70 726f7879 21111173 636f2e63 6f6d3081 9f300d06 092a8648 86f70d01
01090216 1570686f 6e652d70 726f7879 2e636973 636f2e63 6f6d3081 9f300d06
092a8648 86f70d01 01010500 03818d00 30818902 818100cc 3ce30191 656670e9
76460cfc ea23f241 b765c71c 64abc2c1 8ff8b20f 6a812cb6 317f4136 1008c9b6
b2c92409 6c5910f9 5f0e65d9 68cc18a3 acfdf821 172d24b8 d0410a97 908a993a
9af6ab6e b639f16e fd0842e0 ee042502 03010001 30111109 2a864886 f70d0101
04050003 8181007f 00856857 6299b07c e194e123 547286c3 a254df3d fe990b5e
e84c1063 276d4cd0 358badd0 4449550e 528f1342 0afa764a 58aba026 a9092c51
5ce8044a 4df41a32 aebd4598 e2a041fa 2d1b1977 1c5b6452 49fa9822 6383e59f
64ad5c8b 84dab241 132a2500 95bdd424 b9ef8979 6e25747a 6ef16c17 6d7668d3
268c72df e7dd75
quit
crypto ca certificate chain phoneproxy-ldc-signer
certificate ac7bf849
308201eb 30820154 a0030201 020204ac 7bf84930 0d06092a 864886f7 0d010104
0500303a 31383012 06035504 05130b4a 4d583130 34354b30 54463022 06092a86
4886f70d 01090216 1570686f 6e652d70 726f7879 2e636973 636f2e63 6f6d301e
6e652d70 726f7879 21111173 636f2e63 6f6d3081 9f300d06 092a8648 86f70d01
01090216 1570686f 6e652d70 726f7879 2e636973 636f2e63 6f6d3081 9f300d06
092a8648 86f70d01 01010500 03818d00 30818902 818100cc 3ce30191 656670e9
76460cfc ea23f241 b765c71c 64abc2c1 8ff8b20f 6a812cb6 317f4136 1008c9b6
b2c92409 6c5910f9 5f0e65d9 68cc18a3 acfdf821 172d24b8 d0410a97 908a993a
9af6ab6e b639f16e fd0842e0 ee042502 03010001 30111109 2a864886 f70d0101
04050003 8181007f 00856857 6299b07c e194e123 547286c3 a254df3d fe990b5e
e84c1063 276d4cd0 358badd0 4449550e 528f1342 0afa764a 58aba026 a9092c51
5ce8044a 4df41a32 aebd4598 e2a041fa 2d1b1977 1c5b6452 49fa9822 6383e59f
7e85e36b 28bc5ca5 3ab461d3 47ac8654 06fc5f75 ff936753 8a21e9ef 9b779d6e
8f1bbeb3 006590a2 3be39ffb bc109e68 0f13205c ba28373f 6726c025 c7a281c1
f8a9dd74 369416c7 f8120901 209a0a
quit
crypto ca certificate chain _internal_phone-proxy-ctl_SAST_0
certificate 3a64f849
30820211 3082017a a0030201 0202043a 64f84930 0d06092a 864886f7 0d010104
0500304d 31123010 06035504 0a130943 6973636f 20496e63 310c300a 06035504
0b130353 54473129 30270603 55040314 205f696e 7465726e 616c5f70 686f6e65
2d70726f 78792d63 746c5f53 4153545f 30301e17 0d303930 34323931 34323931
01090216 1570686f 6e652d70 726f7879 2e636973 636f2e63 6f6d3081 9f300d06
092a8648 86f70d01 01010500 03818d00 30818902 818100cc 3ce30191 656670e9
76460cfc ea23f241 b765c71c 64abc2c1 8ff8b20f 6a812cb6 317f4136 1008c9b6
b2c92409 6c5910f9 5f0e65d9 68cc18a3 acfdf821 172d24b8 d0410a97 908a993a
9af6ab6e b639f16e fd0842e0 ee042502 03010001 30111109 2a864886 f70d0101
04050003 8181007f 00856857 6299b07c e194e123 547286c3 a254df3d fe990b5e
e84c1063 276d4cd0 358badd0 4449550e 528f1342 0afa764a 58aba026 a9092c51
5ce8044a 4df41a32 aebd4598 e2a041fa 2d1b1977 1c5b6452 49fa9822 6383e59f
2c27fbbd bd65d19a 28bfa45c d570b5d4 86916e04 1ccb97d2 538ccf08 7eaeb5f4
04ff84fa bfb2f3c6 b1833f71 f37ac620 4fac7626 4376baa0 25dc1014 50d76178
a0cdf1e7 a3cecd60 4a0f9ed9 732d41b0 b0585cc1 1c
quit
crypto ca certificate chain _internal_phone-proxy-ctl_SAST_1
certificate 3b64f849
30820211 3082017a a0030201 0202043b 64f84930 0d06092a 864886f7 0d010104
0500304d 31123010 06035504 0a130943 6973636f 20496e63 310c300a 06035504
0b130353 54473129 30270603 55040314 205f696e 7465726e 616c5f70 686f6e65
04050003 8181007f 00856857 6299b07c e194e123 547286c3 a254df3d fe990b5e
e84c1063 276d4cd0 358badd0 4449550e 528f1342 0afa764a 58aba026 a9092c51
5ce8044a 4df41a32 aebd4598 e2a041fa 2d1b1977 1c5b6452 49fa9822 6383e59f
5f696e74 65726e61 6c5f7068 6f6e652d 70726f78 792d6374 6c5f5341 53545f31
30819f30 0d06092a 864886f7 0d010101 05000381 8d003081 89028181 00ab2065
74337684 7039bd4c bd24c109 4261079e a223b482 0ca25c7b 5a04f0ef 5edb2607
796a396b e814e7ba 07336fa1 8285e48d 7f72576d 314bff9c 3ca5cea5 5f020301
0001300d 06092a86 4886f70d 01010405 00038181 0095a109 44c56370 cb014358
9d96cfa1 02c3384e 370ba564 956ef325 681281ca 7a6b9ea9 7ac6b0e0 9d884b8b
a993fed7 4fac37c8 f5b00945 592c4ff2 c4f210ec 0410c1b2 f1ba21e5 05a9e80f
5d8329c8 6f4f6d5b 5a5caf1b c693db0f 12cda102 c1efffee 1882fd05 36e82e75
42c9a183 99205d0b a8799c8f 0bda2884 2891ff0b 5a
quit
crypto ca certificate chain _internal_PP_phone-proxy-ctl
certificate 3d64f849
30820209 30820172 a0030201 0202043d 64f84930 0d06092a 864886f7 0d010104
05003049 31123010 06035504 0a130943 6973636f 20496e63 310c300a 06035504
0b130353 54473125 30230603 55040314 1c5f696e 7465726e 616c5f50 505f7068
6f6e652d 70726f78 792d6374 6c301e17 0d303930 34323931 34323931 375a170d
31393034 32373134 32393137 5a304931 12301006 0355040a 13094369 73636f20
496e6331 0c300a06 0355040b 13035354 47312530 23060355 0403141c 5f696e74
65726e61 6c5f5050 5f70686f 6e652d70 726f7879 2d63746c 30819f30 0d06092a
864886f7 0d010101 05000381 8d003081 89028181 00a8e852 64556748 a6d2f701
04050003 8181007f 00856857 6299b07c e194e123 547286c3 a254df3d fe990b5e
e84c1063 276d4cd0 358badd0 4449550e 528f1342 0afa764a 58aba026 a9092c51
5ce8044a 4df41a32 aebd4598 e2a041fa 2d1b1977 1c5b6452 49fa9822 6383e59f
04b1e7bd d70326cd 5720576f 9d8ae3a1 920c85c4 73020301 0001300d 06092a86
4886f70d 01010405 00038181 0056999d 4e0af92a 89325a83 f1fda6cf f5c592e0
b58d0d73 dd7377b3 4da2340e 04b0912c ece2ea7c 497fcd76 2d4618c9 51449e91
d56a6a38 67f16066 0553bd3b 1dfa2259 b97e7196 8af8f4e1 9fd35423 db87ee6d
fb3dbcfd 6f01304c 7d493bc8 62242964 38223bd5 41ab28ae f1103d72 c87bb81d
352367ab 0ae354aa cf4b4b9b f9
quit
crypto ca certificate chain CiscoManufacturing
certificate ca 6a6967b3000000000003
308204d9 308203c1 a0030201 02020a6a 6967b300 00000000 03300d06 092a8648
86f70d01 01050500 30353116 30140603 55040a13 0d436973 636f2053 79737465
6d73311b 30190603 55040313 12436973 636f2052 6f6f7420 43412032 30343830
1e170d30 35303631 30323231 3630315a 170d3239 30353134 32303235 34325a30
39311630 14060355 040a130d 43697363 6f205379 7374656d 73311f30 1d060355
04031316 43697363 6f204d61 6e756661 63747572 696e6720 43413082 0120300d
06092a86 4886f70d 01010105 00038201 0d003082 01080282 010100a0 c5f7dc96
943515f1 f4994ebb 9b41e17d db791691 bbf354f2 414a9432 6262c923 f79ae7bb
9b79e807 294e30f5 ae1bc521 5646b0f8 f4e68e81 b816cca8 9b85d242 81db7ccb
94a91161 121c5cea 33201c9a 16a77ddb 99066ae2 36afecf8 0aff9867 07f430ee
a5f8881a aae8c73c 1cceee48 fdcd5c37 f186939e 3d71757d 34ee4b14 a9c0297b
0510ef87 9e693130 f548363f d8abce15 e2e8589f 3e627104 8726a415 620125aa
d5dfc9c9 5bb8c9a1 077bbe68 92939320 a86cbd15 75d3445d 454beca8 da60c7d8
c8d5c8ed 41e1f55f 578e5332 9349d5d9 0ff836aa 07c43241 c5a7af1d 19fff673
99395a73 67621334 0d1f5e95 70526417 06ec535c 5cdb6aea 35004102 0103a382
01e73082 01e33012 0603551d 130101ff 04083006 0101ff02 0100301d 0603551d
6973636f 2e636f6d 2f736563 75726974 792f706b 692f706f 6c696369 65732f69
6e646578 2e68746d 6c305e06 03551d25 04573055 06082b06 01050507 03010608
2b060105 05070302 06082b06 01050507 03050608 2b060105 05070306 06082b06
01050507 0307060a 2b060104 0182370a 0301060a 2b060104 01823714 02010609
2b060104 01823715 06300d06 092a8648 86f70d01 01050500 03820101 0030f330
2d8cf2ca 374a6499 24290af2 86aa42d5 23e8a2ea 2b6f6923 7a828e1c 4c09cfa4
4fab842f 37e96560 d19ac6d8 f30bf5de d027005c 6f1d91bd d14e5851 1dc9e3f7
38e7d30b d168be8e 22a54b06 e1e6a4aa 337d1a75 ba26f370 c66100a5 c379265b
0e041604 14d0c522 26ab4f46 60ecae05 91c7dc5a d1b047f7 6c300b06 03551d0f
04040302 01863010 06092b06 01040182 37150104 03020100 30190609 2b060104
01823714 02040c1e 0a005300 75006200 43004130 1f060355 1d230418 30168014
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
22daebdc 87cf5921 421ae9cf 707588e0 243d5d7d 4e963880 97d56ff0 9b71d8ba
6019a5b0 6186addd 6566f6b9 27a2ee2f 619bbaa1 3061fdbe ac3514f9 b82d9706
afc3ef6d cc3d3ceb 95e981d3 8a5eb6ce fa79a46b d7a25764 c43f4cc9 dbe882ec
0166d410 88a256e5 3c57ede9 02a84891 6307ab61 264b1a13 9fe4dcda 5f
quit
crypto ca certificate chain CAP-RTP-001
certificate ca 7612f960153d6f9f4e42202032b72356
308203a8 30820290 a0030201 02021076 12f96015 3d6f9f4e 42202032 b7235630
0d06092a 864886f7 0d010105 0500302e 31163014 06035504 0a130d43 6973636f
20537973 74656d73 31143012 06035504 03130b43 41502d52 54502d30 3031301e
170d3033 30323036 32333237 31335a17 0d323330 32303632 33333633 345a302e
31163014 06035504 0a130d43 6973636f 20537973 74656d73 31143012 06035504
03130b43 41502d52 54502d30 30313082 0120300d 06092a86 4886f70d 01010105
00038201 0d003082 01080282 010100ac 55bbed18 de9b8709 ffbc8f2d 509ab83a
21c1967f dea7f4b0 969694b7 80cc196a 463da516 54a28f47 5d903b5f 104a3d54
a981389b 2fc7ac49 956262b8 1c143038 5345bb2e 273fa7a6 46860573 ce5c998d
55de78aa 5a5cfe14 037d695b ac816409 c6211f0b 3bbf09cf b0bbb2d4 ac362f67
0fd145f1 620852b3 1f07e2f1 aa74f150 367632ed a289e374 af0c5b78 ce7dfb9f
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
30312e63 726c3010 06092b06 01040182 37150104 03020100 300d0609 2a864886
f70d0101 05050003 82010100 ab64fdeb f60c32dc 360f0e10 5fe175fa 0d574ab5
02acdca3 c7bbed15 a4431f20 7e9286f0 770929a2 17e4cdf4 f2629244 2f3575af
e90c468c ae67ba08 aaa71c12 ba0c0e79 e6780a5c f814466c 326a4b56 73938380
73a11aed f9b9de74 1195c48f 99454b8c 30732980 cd6e7123 8b3a6d68 80b97e00
7f4bd4ba 0b5ab462 94d9167e 6d8d48f2 597cde61 25cfadcc 5bd141fb 210275a2
0a4e3400 1428ba0f 69953bb5 50d21f78 43e3e563 98bcb2b1 a2d4864b 0616bacd
a61cd9ae c5558a52 b5eeaa6a 08f96528 b1804b87 d26e4aee ab7affe9 2fd2a574
bafe0028 96304a8b 13fb656d 8fc60094 d5a53d71 444b3cef 79343385 3778c193
74a2a6ce dc56275c a20a303d
quit
crypto ca certificate chain CAP-RTP-002
certificate ca 353fb24bd70f14a346c1f3a9ac725675
308203a8 30820290 a0030201 02021035 3fb24bd7 0f14a346 c1f3a9ac 72567530
0d06092a 864886f7 0d010105 0500302e 31163014 06035504 0a130d43 6973636f
20537973 74656d73 31143012 06035504 03130b43 41502d52 54502d30 3032301e
170d3033 31303130 32303138 34395a17 0d323331 30313032 30323733 375a302e
31163014 06035504 0a130d43 6973636f 20537973 74656d73 31143012 06035504
03130b43 41502d52 54502d30 30323082 0120300d 06092a86 4886f70d 01010105
00038201 0d003082 01080282 010100c4 266504ad 7dc3fd8d 65556fa6 308fae95
b570263b 575abd96 1cc8f394 5965d9d0 d8ce02b9 f808ccd6 b7cd8c46 24801878
57dc4440 a7301ddf e40fb1ef 136212ec c4f3b50f bcafbb4b cd2e5826 34521b65
01555fe4 d4206776 03368357 83932638 d6fc953f 3a179e44 67255a73 45c69dee
fb4d221b 21d7a3ad 38184171 8fd8c271 42183e65 09461434 736c77cc f380eebf
632c7b3f a5f92aa6 a8ef3490 8724a84f 4daf7fd7 0928f585 764d3558 3c0fe9af
1ed8763f a299a802 970004ad 1912d265 7de335b4 bcb6f789 dc68b9fa c8fdf85e
8a28ad8f 0f4883c0 77112a47 141dbee0 948fbe53 fe67b308 d40c8029 87bd790e
cdab9fd7 a190c1a2 a462c5f2 4a6e0b02 0103a381 c33081c0 300b0603 551d0f04
04030201 86300f06 03551d13 0101ff04 05300301 01ff301d 0603551d 0e041604
1452922b e288ee2e 098a4e7e 702c56a5 9ab4d49b 96306f06 03551d1f 04683066
3064a062 a060862d 68747470 3a2f2f63 61702d72 74702d30 30322f43 65727445
6e726f6c 6c2f4341 502d5254 502d3030 322e6372 6c862f66 696c653a 2f2f5c5c
6361702d 7274702d 3030325c 43657274 456e726f 6c6c5c43 41502d52 54502d30
30322e63 726c3010 06092b06 01040182 37150104 03020100 300d0609 2a864886
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
4c5b1931 67947a4f 89a1bdb5
quit
crypto ca certificate chain CallManager
certificate ca 353fb24bd70f14a322c1f3aaac725675
30820298 30820201 a0030201 02020820 b7befb53 ee129030 0d06092a 864886f7
0d010105 05003067 310e300c 06035504 0a130543 6973636f 310b3009 06035504
08130243 41311130 0f060355 04071308 53616e20 4a6f7365 310b3009 06035504
06130255 53311630 14060355 0403130d 43415046 2d646130 31306237 65311030
0e060355 040b1307 534a2d43 55434d30 1e170d30 38303731 33323235 3735365a
170d3133 30373133 32323537 35aaaa30 67310e30 0c060355 040a1305 43697363
6f310b30 09060355 04081302 43413111 300f0603 55040713 0853616e 204a6f73
65310b30 09060355 04061302 55533116 30140603 55040313 0d434150 462d6461
30313062 37653110 300e0603 55040b13 07534a2d 4355434d 30819f30 0d06092a
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c3dddd6 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 0ccccc06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
ef62574d 3e8b5415 dde20702 168ba9c8 71e4bb3e b28caf31 11611762 311fbe2c
1d0d9d32 e468a036 b170e60d 6415e9da 244262c9 f0aab496 bb52f3c3 dc6ed2cc
69678b5e 56cfc2c5 b11236a5 34ac8ef0 d6ecf85e 5c57d6b1 b6c264f1
quit
crypto ca certificate chain _internal_CTL_phone-proxy-ctl_cn=CAPF-da010b7e;ou=SJ-CUCM;o=Cisc
certificate ca 20b7befb53ee1290
30820298 30820201 a0030201 02020820 b7befb53 ee129030 0d06092a 864886f7
0d010105 05003067 310e300c 06035504 0a130543 6973636f 310b3009 06035504
08130243 41311130 0f060355 04071308 53616e20 4a6f7365 310b3009 06035504
06130255 53311630 14060355 0403130d 43415046 2d646130 31306237 65311030
0e060355 040b1307 534a2d43 55434d30 1e170d30 38303731 33323235 3735365a
170d3133 30373133 32323537 35365a30 67310e30 0c060355 040a1305 43697363
6f310b30 09060355 04081302 43413111 300f0603 55040713 0853616e 204a6f73
65310b30 09060355 04061302 55533116 30140603 55040313 0d434150 462d6461
30313062 37653110 300e0603 55040b13 07534a2d 4355434d 30819f30 0d06092a
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
ef62574d 3e8b5415 dde20702 168ba9c8 71e4bb3e b28caf31 11611762 311fbe2c
1d0d9d32 e468a036 b170e60d 6415e9da 244262c9 f0aab496 bb52f3c3 dc6ed2cc
69678b5e 56cfc2c5 b11236a5 34ac8ef0 d6ecf85e 5c57d6b1 b6c264f1
quit
crypto ca certificate chain _internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4c4914
certificate ca 29978cf30000001a7f25
30820382 3082026a a0030201 02020a29 978cf300 00001a7f 25300d06 092a8648
86f70d01 01050500 30393116 30140603 55040a13 0d436973 636f2053 79737465
6d73311f 301d0603 55040313 16436973 636f204d 616e7566 61637475 72696e67
20434130 1e170d30 37303630 36313633 3335375a 170d3137 30363036 31363433
35375a30 51311c30 1a060355 040a1313 43697363 6f205379 7374656d 732c2049
6e632e31 0e300c06 0355040b 13054950 43425531 21301f06 03550403 13185341
53542d41 444e3465 34633439 31342020 20202020 20203081 9f300d06 092a8648
86f70d01 01010500 03818d00 30818902 818100ad 64bf26d5 c0a873ec b74a068a
0165f8dc 00aa874b 8265fd9e dbcd1cea b862fd72 a73f244e 56f524f8 0c31db21
73e45e22 050bdfca 4fbc3683 69565388 4e755ad5 971d1189 e3d1aa50 4d896dbe
70984e4c d8119fdf 809e051e d8072619 00e83623 6f8db64f 4e6984d9 36b6b31d
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
706b692f 63657274 732f636d 63612e63 6572300d 06092a86 4886f70d 01010505
00038201 01009d43 eae9546a cba0bee0 ffdcdfad e1db28d4 868a3d72 71e2189c
0f3ca81e 3963bde2 1a0c1881 cde94633 b9b95be4 d960ff09 07e15e1b bce57499
a9fbb7e8 89bcda8a 3bf5c1b2 9c31e477 3d84f3b8 62ed499c 29a267af 7531542c
7f65db1b 9ddc994b 005620ff 00686781 1b3daab8 92c2b378 0d5daaa7 48826590
69bd3a63 2cccc259 906eb13e ae257c26 bd42b04a 39aac2f5 d6fa7a9f d77dbd8c
71382d76 8b15354b 5a8de336 2d367781 c70c14b6 c3a9808d f5d6f29a 724ea4a9
6a44c857 39650cc3 790cddaa a1a01ddc ae63799e ee7a6b24 8d23fb9d a68adb36
adceda53 7af578bf 965895aa 3d48921e aa350fdb e074eb03 7e62500f 1635236c
7172dc3c 2065
quit
crypto ca certificate chain _internal_CTL_phone-proxy-ctl_cn="SAST-ADN4e4e2114
certificate ca 299919400000001a7f2a
30820382 3082026a a0030201 02020a29 99194000 00001a7f 2a300d06 092a8648
86f70d01 01050500 30393116 30140603 55040a13 0d436973 636f2053 79737465
6d73311f 301d0603 55040313 16436973 636f204d 616e7566 61637475 72696e67
20434130 1e170d30 37303630 36313633 3533385a 170d3137 30363036 31363435
33385a30 51311c30 1a060355 040a1313 43697363 6f205379 7374656d 732c2049
6e632e31 0e300c06 0355040b 13054950 43425531 21301f06 03550403 13185341
53542d41 444e3465 34653231 31342020 20202020 20203081 9f300d06 092a8648
86f70d01 01010500 03818d00 30818902 818100b0 b5568e22 a636be97 686a7087
1d892b3e be907414 60a3199b d89fe051 62d006f5 2501ebf7 86db0532 724247c3
c27ab378 185e5ad5 11175783 e055e44b 5833837b 644fb3c0 f1365be7 da7dc448
9e794718 b1f7ab64 38a8d809 29dbcd84 4fd7c1de 03f6d276 ce5d7498 68ecb0d4
1685f1c3 aa2ec749 f1ddabc7 050411cc cfe6ad02 034c0c79 a381f730 81f4300e
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
9e416f8e ba289a06 4599de3f a14775f7 acf24dc7 d7923d69 8f9e64d2 b7646835
87086d39 56479cf0 abbb1174 d8534475 d3aeec7e 0433c2f6 0c61b396 dd5c5801
60efbb61 da93f8b7 bb16ddbd 2b869463 67983f64 188c9720 9acce942 173fedc1
8b3838c5 cfa06f94 139aec89 119d17ef 7f7f3c28 60545610 8ae29641 6a6ebb37
a853bffd 0562f023 340aa5ab 8fc81981 5c9a36fc 2affa096 30728d19 2e3ba723
655ede4c c7b2aea8 8b402425 cfeb506b 9c5caaec bb5cdc06 8d82fbbe 725c300f
8076c5e9 ec5c53fb 2a134728 36918db7 bf256f0f 979190f6 db53a751 d14bb59f
80f59218 3d33
quit
crypto ca certificate chain _internal_CTL_phone-proxy-ctl_cn=parshah-cm6-1.par-shah.com
certificate ca 5e4bd888b2b05a3a
3082024e 308201b7 a0030201 0202085e 4bd888b2 b05a3a30 0d06092a 864886f7
0d010105 05003025 31233021 06035504 03131a70 61727368 61682d63 6d362d31
2e706172 2d736861 682e636f 6d301e17 0d303830 37313332 32353735 345a170d
31333037 31333232 35373534 5a302531 23302106 03550403 131a7061 72736861
682d636d 362d312e 7061722d 73686168 2e636f6d 30819f30 0d06092a 864886f7
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
301d0603 551d0e04 16041410 fc6aac00 ce0bfb51 355f39f4 10a119ac 1932a330
0d06092a 864886f7 0d010105 05000381 8100bbbb 20958c9a 893f800a 4eb52f18
9149033d 7265ad86 88a9db61 83e09dc6 d0b6d398 ddc9cfb5 413c13b4 689ebf91
7a12e807 373d8831 d882b1a2 bbd4794b 872332de 403ed5d0 e80df429 016aab18
f4fe812f 8c5a7a1d cbad66fc 19dbf265 d010b97f 1946100c d4e9d94b a68000eb
b56d2498 31ec2381 89d12b1c e9d729d0 81fd
quit
crypto ca certificate chain _internal_CTL_phone-proxy-ctl_cn=parshah-cm6-2.par-shah.com
certificate ca 72282522f77bbba2
3082024e 308201b7 a0030201 02020872 282522f7 7bbba230 0d06092a 864886f7
0d010105 05003025 31233021 06035504 03131a70 61727368 61682d63 6d362d32
2e706172 2d736861 682e636f 6d301e17 0d303830 37313430 30303031 365a170d
31333037 31343030 30303136 5a302531 23302106 03550403 131a7061 72736861
682d636d 362d322e 7061722d 73686168 2e636f6d 30819f30 0d06092a 864886f7
0d010101 05000381 8d003081 89028181 00a36017 300f8503 f0aceca4 ebc746a1
df5baebf 1eb1a928 053f2a64 7010eb4d 3cac96de 280b3d60 54562c4c 9d44d641
27f3c815 1e6e9a02 0916ad2b a089605f da7b2faa 30430603 551d1f04 3c303a30
38a036a0 34863268 7474703a 2f2f7777 772e6369 73636f2e 636f6d2f 73656375
72697479 2f706b69 2f63726c 2f637263 61323034 382e6372 6c305006 082b0601
05050701 01044430 42304006 082b0601 05050730 02863468 7474703a 2f2f7777
772e6369 73636f2e 636f6d2f 73656375 72697479 2f706b69 2f636572 74732f63
72636132 3034382e 63657230 5c060355 1d200455 30533051 060a2b06 01040109
15010200 30433041 06082b06 01050507 02011635 68747470 3a2f2f77 77772e63
a719d193 8dab9b10 11291fa1 82fdfd3c 4b6e65dc 934505e9 af336b67 23070686
0d06092a 864886f7 0d010105 05000381 810056c7 c9b6e085 f1d18193 0e210bdb
861a8ae7 fc1d7838 b889f92b 7b6e159d 019610b5 e1b28fef 013ff99b af67b23b
695d7693 0b7a411f c0c68d71 aa94bbbb ee6d01c4 04cdc5af b3191e8b fc54f58f
9fd15b8d c62c0412 96ffcba7 be30a810 bd2ca7f0 a1f1b266 5309f993 14ad92b7
122c1b13 04ab0eba adbb2c9d fe504025 d454
quit
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 5
console timeout 0
!
tls-proxy phone-proxy-tls
server trust-point _internal_PP_phone-proxy-ctl
client ldc issuer phoneproxy-ldc-signer
client ldc key-pair phoneproxy-ldc-clients
ctl-file phone-proxy-ctl
cluster-ctl-file disk0:/CTLFile.tlv
record-entry capf trustpoint _internal_CTL_phone-proxy-ctl_cn=CAPF-da010b7e;ou=SJ-CUCM;o=Cisc address 192.0.2.100
record-entry cucm-tftp trustpoint phoneproxy-main address 192.0.2.100
no shutdown
!
media-termination phone-proxy-media
address 192.0.2.2 interface outside
address 172.16.152.219 interface inside
!
phone-proxy asa-phone-proxy
media-termination phone-proxy-media
tftp-server address 172.16.97.80 interface inside
tls-proxy phone-proxy-tls
cluster-mode mixed
ctl-file phone-proxy-ctl
no disable service-settings
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
class-map SECURE_SCCP
match port tcp eq 2443
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect sip
inspect ftp
inspect h323 h225
inspect skinny
inspect h323 ras
inspect sunrpc
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect xdmcp
inspect netbios
inspect tftp
inspect dns preset_dns_map
inspect http
class SECURE_SCCP
inspect skinny phone-proxy asa-phone-proxy
!
service-policy global_policy global
prompt hostname context
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Would highly recommend adding an additional section regarding phone services/corporate directory. With the configuration above the services/corporate directory doesn't work on the phone.
With the following configuration update as outlined below. The ASA will insert a value for "Proxy Server" on a 7900 series phone. You can check this on the phone pressing Settings | Device Configuration | HTTP Configuration | Proxy server. The ASA will insert the global address for the CUCM server and dynamically update the access-list for a registered phone.
You can correct this issue through ASDM or through CLI.
Open ASDM
Expand Firewall | Advanced | Encrypted Traffic Inspection | Phone Proxy
Click "Configure a http-proxy which would be written into the phone's config file so that phone URLs are directed for services on the phone.
Insert the IP address of your CUCM server, port 8080, interface "Inside" (normally).
CLI:
phone-proxy asdm_phone-proxy
proxy-server address X.X.X.X interface inside (where X.X.X.X = your CUCM server)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there any other was of registering remote phone to the CUCM without the expensive ASA phone proxy ?
Thanks
Tim
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is a very good point, but one has to keep in mind that this is more of a workaround (since the Proxy Server URL parameter is not the same as the Directory URL) that has certain limitations when different phone profiles point to different Directory servers. Additionally, the HTTP services traffic will not be encrypted when traversing the Internet, which presents a security concern. GIven these considerations, this example focuses more on the configuration implications when working with Mixed Mode CUCM clusters and phones natively in Encrypted mode.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Unfortunately, there's not alternative solution that offers the same level of security and flexibility. The obvious other choice would be to build a VPN tunnel to the central office. Another option is to configure the CUCM cluster in Mixed Mode and register the phone in Encrypted mode natively, but this presents issues with permitting secondary SRTP traffic through the firewall (since we can't inspect the encrypted control connections). The easiest but least secure option is to register the phone with the CUCM with no encryption.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Andrew,
The security is not a concern (as its a test environment), however the remote phones are only able to register on the CUCM, but there is no media, since they're located in behind NATing in remote locations...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Tim,
You should check remote NAT devices for Skinny (I presume that is what you use) inspection capabilities. If your ASA has Skinny Inspection enabled, you should have no problem with secondary voice connections through it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Well the remote devices are remote users using their Linksys or whatever routes to get to the Internet, only CUCM is behind a ASA..
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Tim,
During the call setup process, the remote phone will embed its local (in this case, private) IP address into a message to the CUCM. This IP address will be used to open the voice connection with the other party. If the Linksys device is not configured to inspect Skinny, the embedded private IP address of the phone will not rewritten and the other side will not know how to route voice traffic to it. The ASA will do its part rewriting the respective private IP addresses in the outbound messages from the inside, but it has no control over how the remote side (Linksys) does NAT IP rewrites.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I guess the only solutions would be having the phone proxy on the ASA..
Thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You're welcome, Tim! You can also review this document that specifically describes what you can try on the remote router to make it work:
http://www.cisco.com/en/US/docs/security/asa/asa80/configuration/guide/unified_comm.html#wp1194487
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

