- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Azure AD SSO with multiple ISE Portals
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 05-11-2021 04:11 PM
Introduction
With the enhancements in ISE 3.0 for integrating with Azure AD via SAML IdP, it is now possible to leverage Microsoft Single Sign-On for multiple ISE Portals (for example Sponsor and Guest/BYOD Portals).
At the time of this writing, ISE cannot create more than one SAML Id Provider with the same Azure tenant ID. As such, one cannot create separate Azure AD Enterprise Applications for the different use cases and map them to separate SAML Id Providers in ISE.
In addition, using separate Azure Enterprise Applications mapped to a single SAML IdP results in an error after redirection and login stating “There was a problem accessing the site. Please contact help desk for assistance"
The current workaround is to use a single Azure AD Enterprise Application for both use cases that maps to a single SAML IdP in ISE.
This document provides an example configuration for using Azure AD for SSO login on both the Sponsor and Guest/BYOD Portals.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco ISE 3.0
- Basic knowledge about SAML SSO deployments
- Azure AD
References
The configuration described in this document is based on Sponsor and BYOD use cases and configurations described in the following documents.
Configure ISE 3.0 Sponsor Portal with Azure AD SAML SSO
Assumptions
This document assumes that ISE and Azure AD have been configured and validated as per the Configure ISE 3.0 Sponsor Portal with Azure AD SAML SSO document.
The following naming conventions are used within this configuration example:
- Sponsor Portal = AzureAD Sponsor Portal
- SAML Id Provider = AAD_ISELAB
- Azure AD Enterprise Application = ISE_SSO
Configuration
Portal Configuration
Step 1 – Configure the BYOD Portal
Navigate to Work Centers > Guest Access > Portals & Components > Guest Portals. Create a new Sponsored Guest Portal or select an existing one.
Input the Portal Name and optional Description:

*** Note: There is currently a bug that requires manually disabling the ‘Require guest to change password…’ option before changing the Authentication method to use the SAML IdP.

Bug reference - https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvy23380
In the Portal Settings section, select the SAML IdP from the ‘Authentication method’ drop-down list and the Guest Type from the ‘Employees using this portal as guests…’ drop-down list.
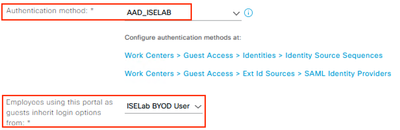
Configure all other preferred settings and click Save.
Azure AD SAML SSO Configuration
Step 2 – Export the updated SAML IdP info from ISE
Navigate to Administration > Identity Management > External Identity Sources > SAML Id Providers and Edit the IdP.
You will notice that both portals are now listed under the ‘Includes the following portals:’ section.
Select the Service Provider Info tab and click Export.
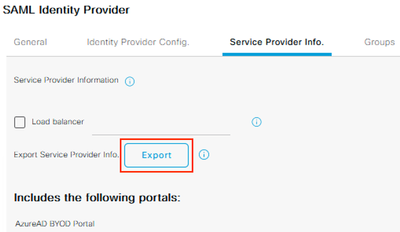
Save and extract the zip file, which includes two separate XML files.

Open the XML file for the new BYOD Portal in a text editor. Record the following attribute values:
- entityID
- AssertionConsumerService Locations
<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://CiscoISE/655019f2-fa19-4517-a5f6-b59d3110830b"><md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate>MIIF6jCCA9KgAwIBAgIQYH/
…
snip
…
</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat><md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://192.168.120.180:8443/portal/SSOLoginResponse.action" index="0"/><md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-sa.ise.xxx.local:8443/portal/SSOLoginResponse.action" index="1"/></md:SPSSODescriptor></md:EntityDescriptor>
Step 3 – Create a BYOD Security Group in Azure AD
Login to the Azure AD Portal and navigate to Azure Active Directory > Manage > Groups
Click New Group

Configure the desired Group name, click the No members selected link and select the associated BYOD user accounts. Click Create.

Record the Object ID for the new group

Step 4 – Update the Enterprise Application
Navigate to Azure Active Directory > Manage > Enterprise applications
Locate and select the Enterprise Application previously created.

Navigate to Manage > Users and groups

Click on Add user/group
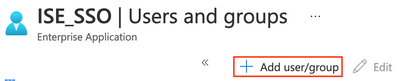
Under Users and groups, click on the link for None selected. Click the BYOD group created earlier and click Select.
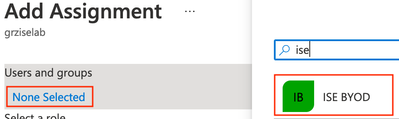
There should now be two groups associated with the Application; one for each use case.
Navigate to Manage > Single sign-on

In the Basic SAML Configuration section, click Edit.
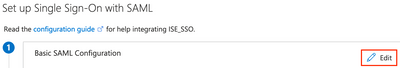
Paste the new entityID and Location values recorded from the XML file earlier in Step 2. This should result in two Entity IDs and multiple Reply URLs. Click Save.

*** Note: There is no need to re-import Azure's metadata into ISE after updating the SAML SSO settings for the Enterprise Application.
Complete the SAML Configuration in ISE
Complete the ISE and WLC configuration as per the ISE BYOD Flow using Azure AD configuration guide and verify that SSO is working for both Portals.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Greg,
Thank you for this document. I have two questions:
1) You mention that this is a new enhancement on ISE 3.0 to support multiple Portals with Azure AD SAML SSO. Does that mean it's not possible to setup for ISE 2.7?
2) Logout URL: in your example, the Azure AD side is configured with the Sponsor Portal Entity ID and URLs (Reply and Logout), and you add the BYOD Portal's Entity ID and Reply URL. But there can only be one Logout URL so that one uses the Sponsor Portal Logout URL. So if a user signs on to the BYOD Portal and then signs out, he/she will be redirected to the Sponsor Portal. Is there a way around that?
Thanks,
Luke
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


