- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-18-2018 11:55 AM - edited 01-04-2019 08:13 AM
- Introduction
- Caveats
- Configuration
- ISE & G-Suite: Export ISE EAP identity certificate and import into G-Suite
- G-Suite: Initial Wi-Fi profile
- G-Suite: User Wi-Fi profile
Introduction
On Windows OS native supplicant, there is a setting that reads ‘Automatically use my Windows logon name and password (and domain if any)’. This setting allows OS to reuse PC login credential for 802.1X authentication to gain network access, thus saving user from having to login twice using same credentials for both the PC and the network. This was not possible on Google Chromebook prior to OS v66 so as a workaround SAML was used to gather user identity instead as documented in Google Suite Guest SSO (Single Sign On) with ISE via SAML for Chromebooks. Google Chrome OS v66 introduced a new feature where user can SSO to the network using Google login credentials. Previously, when the network requires 802.1X authentication, the Chromebook user had to sign-in to the Chromebook using Google account and then connect to the network by providing credentials which may or may not be identical to the Chromebook sign-in credential. With the new feature on v66, domain admin can configure enrolled Chromebooks with WiFi settings, where it can reuse Chromebook sign-in credential for network login automatically. This requires the authentication server, typically a RADIUS server to be able to authenticate using the Google account which is not possible with ISE today. As a workaround, customer can synchronize accounts to Google domain from an on-prem AD server that ISE can authenticate with. The setup is shown in the following diagram:
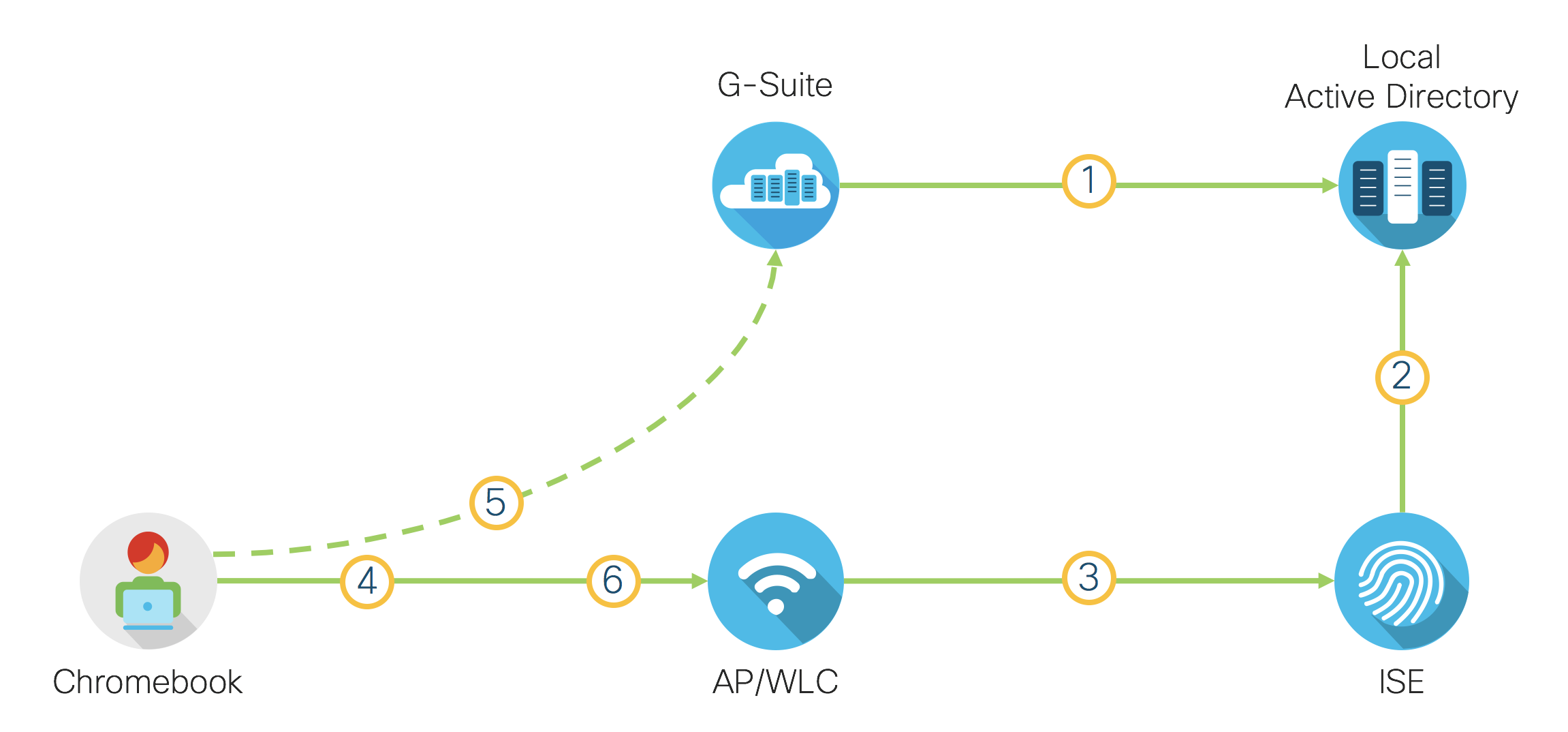
- Google domain account is synchronized with local AD using GCDS (Google Cloud Directory Sync) and subsequently GSPS (G-Suite Password Sync) can be used to synchronize password from AD to Google-Suite
- Since ISE cannot authenticate directly with G-Suite, ISE will interface with local AD
- WLC (NAD) is configured to use ISE as RADIUS server
- Chromebook gets initial network access
- Chromebook is enrolled to the Google Cloud and gets WiFi settings which is configured to use same credential for network access
- Chormebook authenticates using sign-in account which is sent to ISE, ISE authorizes user for full network access
Caveats
- Please note that this document only goes over the necessary settings on G-Suite. The document expects that G-Suite is already setup to synchronize with local AD via GCDS/GSPS. Test Chromebook is already enrolled to the G-Suite. Underlying Wireless network is already configured for 802.1X with ISE.
- Unlike Windows OS, Chromebook supplicant cannot be setup to perform network authentication before login. Which means the Chromebook has to be on the network where it can communicate with G-Suite to authenticate the user prior to user based network access. This can be done by allowing Chromebook to connect to OPEN network (Guest SSID for example) when there are no G-Suite managed user connected. The other option is to use service account that connects to SECURED network prior to user login. In the case of using service account, different ACL can be applied to service account access so it only has access to the Google resources until a valid user logs in. In this document, we will use second example where a service account is used to provide initial access to the network so a subsequent user authentication can occur without issues.
Configuration
ISE & G-Suite: Export ISE EAP identity certificate and import into G-Suite
Note: Steps 1 - 10 is not required if the ISE EAP identity certificate is already generated as 2048 key length and SHA-256 digest.
- Logon to the ISE GUI
- Go to Administration > System > Certificates > Certificate Management > System Certificates
- Click on Generate Self Signed Certificate
- Select DNS Name for ’Subject Alternative Name (SAN)’ and enter the ISE host name in the box
- Select 2048 for Key length and SHA-256 for Digest to Sign With
- Check Portal: Use for Portal
- Select ‘Default Portal Certificate Group’
- Click Submit
- Select Yes when prompted to replace existing certificate
- ISE node will be restarted to use the new certificate
- Once ISE is back up, login to the Admin GUI
- Go to Administration > System > Certificates > Certificate Management > System Certificates
- Check the certificate that is shown as used by ‘Portal’ and click 'Export'
- Leave setting as ‘Export Certificate Only’ and Click Export
- Save it to the local drive. We will import this certificate into the Google Suite
- Logon to the Google Suite account as a google admin user
- Go to Device Management > Device Settings > Network
- Click Certificates
- Click Add Certificate
- Select the one exported from ISE in the step above
- Check 'Use this certificate as an HTTPS certificate authority' check box
- Click Save
G-Suite: Initial Wi-Fi profile
Create Initial Wi-Fi profile so Chromebook is connected to the G-Suite prior to user login. This step can be modified to open SSID instead if such SSID allows access to G-Suite resources.
- Logon to the Google Suite account as a google admin user
- From Home, click on ‘Device Management’
- On the left, click ‘Networks’
- Click ‘Wi-Fi’
- Click ‘Add Wi-Fi’
- Enter Following information:
| Setting | Value |
|---|---|
| Name | SECURED-PRE |
| Service set identifier (SSID) | SECURED |
| Automatically connect | Checked |
| Security type | WPA/WPA2 Enterprise (802.1X) |
| Extensible Authentication Protocol | PEAP |
| Inner Protocol | MS-CHAP v2 |
| Outer identity | PreAuth |
| Username | Service account setup for preauth access. This could be G-Suite account or AD/Internal account |
| Password | Service account password |
| Server Certificate Authority | ISE EAP Identity Certificate previously imported |
| Restrict access to this Wi-Fi network by platform | Chromebooks |
| Apply network | by device |
- Click APPLY
G-Suite: User Wi-Fi profile
- Create user Wi-Fi profile. This will be used for anyone logging in to the Chromebook.
- Click ‘Add Wi-Fi’
- Enter Following information:
| Setting | Value |
|---|---|
| Name | SECURED-USER |
| Service set identifier (SSID) | SECURED |
| Automatically connect | Checked |
| Security Type | WPA/WPA2 Enterprise (802.1X) |
| Extensible Authentication Protocol | PEAP |
| Inner Protocol | MS-CHAP v2 |
| Outer identity | OuterID |
| Username | ${LOGIN_ID} |
| Password | ${PASSWORD} |
| Server Certificate Authority | ISE EAP Identity Certificate previously imported |
| Restrict access to this Wi-Fi network by platform | Chromebooks |
| Apply network | by user |
- Click APPLY then SAVE
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Running into an issue when trying to save the "User WiFi Profile". The Google console throws an error stating "A network with this SSID and security type already exists". Made sure the network is being applied by user. Any ideas? I suppose a work around would be 2 separate SSID's for pre and post logon. According to this doc it should be able to be done on a single SSID.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@michaelpassalacqua Note that one of the two Wi-Fi profiles I've created are applied to the user while the other one is applied to the device.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for providing the guide.
We've encountered an issue when users try to log into the configured SSID, we get the following error on the chromebooks 'Authentication certificate rejected locally'.
Are there any steps we need to take to resolve this message?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
seankin, that generally means the ISE RADIUS/EAP certificate is not trusted by the chromebook. I would double check that ISE RADIUS/EAP certificate has been imported and trusted by the client for the connection.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sorry to dig up an old thread, but the 'Authentication certificate rejected locally' is something we can't get over @howon. I verified by going to the chrome://settings/certificates and seeing the EAP certificate in Others. Plus I even added our corporate Root/Intermediate certificate and I see them under Authority section. But still the 'Authentication certificate rejected locally' appears. These certs are internal only and not publicly signed.
I've verified the certs are valid, they do not expire until 2030 and using SHA256 with RSA other than that there is not much to go on. Any information will help. Thank you.



