- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco ASA: VPN-Spoke-to-Spoke communication via the Hub
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 11-24-2013 03:03 PM
(Eine deutsche Version dieses Dokumentes gibt es unter http://security-planet.de/2013/11/29/cisco-asa-vpns-spoke-to-spoke-traffic-via-hub/)
The question how to configure spoke-to-spoke VPN traffic on the ASA is quite frequent on the Cisco Support Community.
This document shows how to achieve this on the ASA with version 8.4+ and IKEv1 which is still most common.
If someone reads this document in the planning phase, consider using IOS-routers for this task. They are far more flexible for things like this and should be your first choice for site-to-site VPN-devices.
This Example uses the following topology:
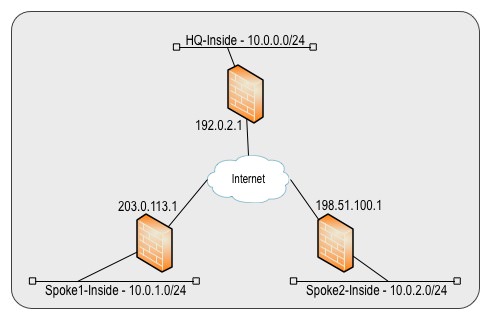
We start with a basic Hub-and-Spoke config that gets extended for Spoke-to-Spoke later on.
On all ASAs we need IPSec Phase1 and Phase2 policies. Use policies that fit your need. These won't change when configuring spoke-to-spoke:
Spoke1, Spoke2, Hub
crypto ikev1 policy 1 authentication pre-share encryption aes 256 hash sha group 5 lifetime 86400 ! crypto ikev1 enable outside ! crypto ipsec ikev1 transform-set ESP-AES256-SHA esp-aes-256 esp-sha-hmac
On all ASAs we configure the needed object-groups, crypto-ACLs, crypto-maps and tunnel-groups for the VPNs. In addition NAT-Exemption is configured:
Spoke1
object-group network SPOKE1-NETWORKS network-object 10.0.1.0 255.255.255.0 object-group network HQ-NETWORKS network-object 10.0.0.0 255.255.255.0 object-group network NAT-EXEMPTION-DESTINATIONS group-object HQ-NETWORKS ! access-list VPN-SPOKE1-TO-HQ extended permit ip object-group SPOKE1-NETWORK object-group HQ-NETWORKS ! crypto map VPN 1 match address VPN-SPOKE1-TO-HQ crypto map VPN 1 set peer 192.0.2.1 crypto map VPN 1 set ikev1 transform-set ESP-AES256-SHA crypto map VPN interface outside ! tunnel-group 192.0.2.1 type ipsec-l2l tunnel-group 192.0.2.1 ipsec-attributes ikev1 pre-shared-key Th!sP$KHQ-Spoke1isN0Tc0mpl3xEnough ! nat (any,outside) source static SPOKE1-NETWORKS SPOKE1-NETWORKS destination static NAT-EXEMPTION-DESTINATIONS NAT-EXEMPTION-DESTINATIONS no-proxy-arp route-lookup description NAT-Exemption for VPN
Spoke2
object-group network SPOKE2-NETWORKS network-object 10.0.2.0 255.255.255.0 object-group network HQ-NETWORKS network-object 10.0.0.0 255.255.255.0 object-group network NAT-EXEMPTION-DESTINATIONS group-object HQ-NETWORKS ! access-list VPN-SPOKE2-TO-HQ extended permit ip object-group SPOKE2-NETWORKS object-group HQ-NETWORKS ! crypto map VPN 1 match address VPN-SPOKE2-TO-HQ crypto map VPN 1 set peer 192.0.2.1 crypto map VPN 1 set ikev1 transform-set ESP-AES256-SHA crypto map VPN interface outside ! tunnel-group 192.0.2.1 type ipsec-l2l tunnel-group 192.0.2.1 ipsec-attributes ikev1 pre-shared-key Th!sP$KHQ-Spoke2isN0Tc0mpl3xEnough ! nat (any,outside) source static SPOKE2-NETWORKS SPOKE2-NETWORKS destination static NAT-EXEMPTION-DESTINATIONS NAT-EXEMPTION-DESTINATIONS no-proxy-arp route-lookup description NAT-Exemption for VPN
Hub
object-group network SPOKE1-NETWORKS
network-object 10.0.1.0 255.255.255.0
object-group network SPOKE2-NETWORKS
network-object 10.0.2.0 255.255.255.0
object-group network HQ-NETWORKS
network-object 10.0.0.0 255.255.255.0
object-group network NAT-EXEMPTION-DESTINATIONS
group-object SPOKE1-NETWORKS
group-object SPOKE2-NETWORKS
!
access-list VPN-HQ-TO-SPOKE1 extended permit ip object-group HQ-NETWORKS object-group SPOKE1-NETWORKS
!
access-list VPN-HQ-TO-SPOKE2 extended permit ip object-group HQ-NETWORKS object-group SPOKE2-NETWORKS
!
crypto map VPN 1 match address VPN-HQ-TO-SPOKE1
crypto map VPN 1 set peer 203.0.113.1
crypto map VPN 1 set ikev1 transform-set ESP-AES256-SHA
crypto map VPN 2 match address VPN-HQ-TO-SPOKE2
crypto map VPN 2 set peer 198.51.100.1
crypto map VPN 2 set ikev1 transform-set ESP-AES256-SHA
crypto map VPN interface outside
!
tunnel-group 203.0.113.1 type ipsec-l2l
tunnel-group 203.0.113.1 ipsec-attributes
ikev1 pre-shared-key Th!sP$KHQ-Spoke1isN0Tc0mpl3xEnough
!
tunnel-group 198.51.100.1 type ipsec-l2l
tunnel-group 198.51.100.1 ipsec-attributes
ikev1 pre-shared-key Th!sP$KHQ-Spoke2isN0Tc0mpl3xEnough
!
nat (any,outside) source static HQ-NETWORKS HQ-NETWORKS destination static NAT-EXEMPTION-DESTINATIONS NAT-EXEMPTION-DESTINATIONS no-proxy-arp route-lookup description NAT-Exemption for VPN
With this setup the Spokes can communicate with the Hub through the VPN. If there are more networks at a site, only the object-groups have to be extended. IKEv1 could also be changed to IKEv2 without any impact on the following spoke-to-spoke communication.
Now the given config is extended for Spoke-to-Spoke communication.
(Only the config changes are shown; the complete VPN-config is attached)
Each Spoke has to send the traffic for the other Spokes through the tunnel that is already established to the Hub. For that, both the existing crypto-ACLs and the NAT-exemption is extended with the Spoke-to-Spoke traffic:
Spoke1
object-group network SPOKE2-NETWORKS network-object 10.0.2.0 255.255.255.0 object-group network NAT-EXEMPTION-DESTINATIONS group-object SPOKE2-NETWORKS ! access-list VPN-SPOKE1-TO-HQ extended permit ip object-group SPOKE1-NETWORKS object-group SPOKE2-NETWORKS
Spoke2
object-group network SPOKE1-NETWORKS network-object 10.0.1.0 255.255.255.0 object-group network NAT-EXEMPTION-DESTINATIONS group-object SPOKE1-NETWORKS ! access-list VPN-SPOKE2-TO-HQ extended permit ip object-group SPOKE2-NETWORKS object-group SPOKE1-NETWORKS
The resulting ACLs now have permit statements to the hub and also to the other spoke. The crypto-ACLs could also be configured with a new object-group that includes all VPN-destinations that are reachable through the Hub. By extending the object-group NAT-EXEMPTION-DESTINATIONS, the traffic to the other spoke won't be NATed, the same way as the traffic to the Hub is exempted.
Hub
On the Hub, two config-changes have to be made. The crypto-ACL for the Hub-to-Spoke1-traffic needs to be extended with Spoke2-to-Spoke1 traffic and the crypto-ACL for the Hub-to-Spoke2-traffic needs to be extended with Spoke1-to-Spoke2 traffic:
access-list VPN-HQ-TO-SPOKE1 extended permit ip object-group SPOKE2-NETWORKS object-group SPOKE1-NETWORKS ! access-list VPN-HQ-TO-SPOKE2 extended permit ip object-group SPOKE1-NETWORKS object-group SPOKE2-NETWORKS
As a last step, the ASA has to allow traffic to enter and leave on the same interface which is not the default:
same-security-traffic permit intra-interface
Attached are the resulting configs from Spoke1, Spoke2 and the Hub.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have two more subnet in HUB LOACTION. Could some one provide me the config to allow the subnets to reach spoke1 and spoke2.
10.10.32.0 255.255.255.0
10.10.40.0 255.255.255.0
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
just add all networks to the corresponding network-objects and you are done.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi ,
I have added one more sopke-2 to the hub and i am getting the below error. Config also attached.
Hub: No crypto map,
HUB CONFIG
ASA Version 9.0(1)
!
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
<--- More --->
!
interface Vlan1
nameif inside
security-level 100
ip address 10.10.30.1 255.255.254.0
!
interface Vlan2
nameif outside
security-level 0
ip address 66.241.104.40 255.255.255.0
!
no ftp mode passive
dns domain-lookup outside
dns server-group DefaultDNS
name-server 8.8.8.8
same-security-traffic permit intra-interface
object network net-local
subnet 10.10.30.0 255.255.254.0
object network net-remote
subnet 10.10.50.0 255.255.254.0
object network net-local-2
subnet 10.10.32.0 255.255.254.0
object network outside_to_in51
host 10.10.31.51
<--- More --->
object network outsidetoWebS
host 10.10.31.40
object network myNatPool
range 66.241.104.41 66.241.104.60
object network PrivNet
subnet 10.10.30.0 255.255.254.0
object network PBXRange
range 66.241.103.193 66.241.103.210
object network MYSQL3121
host 10.10.31.21
object network Mail3150
host 10.10.31.50
object network NOCServer
host 10.10.31.53
object network FSPortal
host 10.10.31.54
object network ftpserver
host 10.10.31.10
object network saltech-vv
host 172.251.29.11
object network outside_to_in80
host 10.10.31.80
object network outside_toin80
object network outside_to_in_81
<--- More --->
host 10.10.31.81
object network outside_to_in_82
host 10.10.31.82
object network outside_to_in_12
host 10.10.31.12
object network net-remote-3
subnet 10.10.29.0 255.255.255.0
access-list vpn-nat0 extended permit ip 10.10.60.0 255.255.254.0 10.10.50.0 255.255.254.0
access-list vpn-nat0 extended permit ip 10.10.30.0 255.255.254.0 10.10.50.0 255.255.254.0
access-list vpn-nat0 extended permit ip 10.10.32.0 255.255.254.0 10.10.50.0 255.255.254.0
access-list vpn-nat0 extended permit ip 10.10.40.0 255.255.254.0 10.10.50.0 255.255.254.0
access-list decepticons3 extended permit ip 10.10.30.0 255.255.254.0 10.10.50.0 255.255.254.0
access-list inbound extended permit icmp any any echo
access-list inbound extended permit tcp any host 10.10.31.51 eq www
access-list inbound extended permit tcp any host 10.10.31.51 eq ssh
access-list inbound extended permit tcp any host 10.10.61.51 eq https
access-list inbound extended permit tcp any host 10.10.31.40 eq www
access-list inbound extended permit tcp any host 10.10.31.40 eq https
access-list inbound extended permit tcp any host 10.10.31.50 eq smtp
access-list inbound extended permit tcp any host 10.10.31.50 eq pop3
access-list inbound extended permit tcp any host 10.10.31.50 eq imap4
access-list inbound extended permit tcp any host 10.10.31.50 eq www
access-list inbound extended permit tcp any host 10.10.31.50 eq https
access-list inbound extended permit tcp object PBXRange host 10.10.31.21
<--- More --->
access-list inbound extended permit tcp any host 10.10.31.53 eq www
access-list inbound extended permit tcp any host 10.10.31.53 eq https
access-list inbound extended permit tcp any host 10.10.31.54 eq www
access-list inbound extended permit tcp any host 10.10.31.54 eq ssh
access-list inbound extended permit tcp any host 10.10.31.54 eq https
access-list inbound extended permit tcp any host 10.10.31.51 eq https
access-list inbound extended permit tcp any host 10.10.31.10 eq ftp
access-list inbound extended permit tcp any host 10.10.31.10 eq 990
access-list inbound extended permit tcp any host 10.10.31.10 eq ssh
access-list inbound extended permit tcp any host 10.10.31.10 eq ftp-data
access-list inbound extended permit tcp any host 10.10.31.10 eq https
access-list inbound extended permit tcp any host 10.10.31.10 eq www
access-list inbound extended permit tcp object PBXRange host 10.10.31.10
access-list inbound extended permit tcp object saltech-vv host 10.10.31.10
access-list inbound extended permit tcp any host 10.10.31.40 eq 3389
access-list inbound extended permit tcp any host 10.10.31.80 eq www
access-list inbound extended permit tcp any host 10.10.31.80 eq sip
access-list inbound extended permit udp any host 10.10.31.80 range 10000 60000
access-list inbound extended permit udp any host 10.10.31.80 range sip 5082
access-list inbound extended permit tcp any host 10.10.31.81 eq ssh
access-list inbound extended permit tcp any host 10.10.31.81 range 10000 20000
access-list inbound extended permit tcp any host 10.10.31.81 eq sip
access-list inbound extended permit udp any host 10.10.31.81 range sip 5082
access-list inbound extended permit tcp any host 10.10.31.82 range 10000 20000
<--- More --->
access-list inbound extended permit tcp any host 10.10.31.82 eq sip
access-list inbound extended permit udp any host 10.10.31.82 range sip 5082
access-list inbound extended permit tcp any host 10.10.31.12 eq www
access-list inbound extended permit tcp any host 10.10.31.12 eq https
access-list decepticons4 extended permit ip 10.10.30.0 255.255.254.0 10.10.29.0 255.255.255.0
access-list decepticons4 extended permit ip 10.10.50.0 255.255.254.0 10.10.29.0 255.255.255.0
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static net-local net-local destination static net-remote net-remote
nat (inside,outside) source static net-local-2 net-local-2 destination static net-remote net-remote
nat (inside,outside) source static net-local net-local destination static net-remote-3 net-remote-3 no-proxy-arp route-lookup description NAT-Exemption for VPN
!
object network outside_to_in51
nat (inside,outside) static 66.241.104.51
object network outsidetoWebS
nat (inside,outside) static 66.241.104.41
object network PrivNet
<--- More --->
nat (inside,outside) dynamic interface
object network MYSQL3121
nat (inside,outside) static 66.241.104.42
object network Mail3150
nat (inside,outside) static 66.241.104.50
object network NOCServer
nat (inside,outside) static 66.241.104.53
object network FSPortal
nat (inside,outside) static 66.241.104.54
object network ftpserver
nat (inside,outside) static 66.241.104.43
object network outside_to_in80
nat (inside,outside) static 66.241.104.52
object network outside_to_in_81
nat (inside,outside) static 66.241.104.55
object network outside_to_in_82
nat (inside,outside) static 66.241.104.56
object network outside_to_in_12
nat (inside,outside) static 66.241.104.57
access-group inbound in interface outside
route outside 0.0.0.0 0.0.0.0 66.241.104.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
<--- More --->
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set autobots-transform-and-roll-out esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map cybertron 29 match address decepticons3
crypto map cybertron 29 set pfs
crypto map cybertron 29 set peer 67.203.13.146
crypto map cybertron 29 set ikev1 transform-set autobots-transform-and-roll-out ESP-3DES-SHA
crypto map cybertron 79 match address decepticons4
crypto map cybertron 79 set peer 76.79.157.179
crypto map cybertron 79 set ikev1 transform-set autobots-transform-and-roll-out ESP-3DES-SHA
crypto map cybertron interface outside
<--- More --->
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 5
lifetime 86400
crypto ikev1 policy 29
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 28800
crypto ikev1 policy 33
authentication pre-share
encryption 3des
hash sha
<--- More --->
group 2
lifetime 86400
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 60
console timeout 0
dhcpd auto_config outside
!
dhcpd address 10.10.30.120-10.10.30.125 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 207.200.81.113 source outside
ntp server 69.25.96.13 source outside
ntp server 64.147.116.229 source outside
ntp server 216.171.124.36 source outside
webvpn
anyconnect-essentials
username cfocusserv password F0DMDG1d1mpcVNyR encrypted
tunnel-group 67.203.13.146 type ipsec-l2l
<--- More --->
tunnel-group 67.203.13.146 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 76.79.157.179 type ipsec-l2l
tunnel-group 76.79.157.179 ipsec-attributes
ikev1 pre-shared-key *****
!
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:7496dca495192b01c900f631a9ea45a6
: end
cfocusASA# SI IPSEC SA
^
ERROR: % Invalid input detected at '^' marker.
cfocusASA# SI IPSEC SA SI IPSEC SA H IPSEC SA
interface: outside
Crypto map tag: cybertron, seq num: 29, local addr: 66.241.104.40
access-list decepticons3 extended permit ip 10.10.30.0 255.255.254.0 10.10.50.0 255.255.254.0
local ident (addr/mask/prot/port): (10.10.30.0/255.255.254.0/0/0)
remote ident (addr/mask/prot/port): (10.10.50.0/255.255.254.0/0/0)
current_peer: 67.203.13.146
#pkts encaps: 2079635, #pkts encrypt: 2079635, #pkts digest: 2079635
#pkts decaps: 3859012, #pkts decrypt: 3859012, #pkts verify: 3859012
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 2079635, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 66.241.104.40/0, remote crypto endpt.: 67.203.13.146/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: DD2B7B72
current inbound spi : F3F50A05
<--- More --->
inbound esp sas:
spi: 0xF3F50A05 (4092922373)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: cybertron
sa timing: remaining key lifetime (kB/sec): (3905565/8536)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xDD2B7B72 (3710614386)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, }
slot: 0, conn_id: 32768, crypto-map: cybertron
sa timing: remaining key lifetime (kB/sec): (3822568/8536)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
cfocusASA# SH IPSEC SA SAKM
cfocusASA# SH ISAKMp SA
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 67.203.13.146
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
cfocusASA#
Spkoe-2: Error.
No IKEV1 SA
H run
: Saved
:
ASA Version 9.1(3)
!
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
<--- More --->
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 10.10.29.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 76.79.157.179 255.255.255.248
!
ftp mode passive
dns domain-lookup outside
dns server-group DefaultDNS
domain-name customerfocusservices.com
dns server-group Google_DNS
dns server-group defaultDNS
name-server 8.8.8.8
same-security-traffic permit intra-interface
object network local_network
subnet 10.10.29.0 255.255.255.0
object network net-local
subnet 10.10.30.0 255.255.254.0
<--- More --->
object network net-remote-3
subnet 10.10.29.0 255.255.255.0
access-list outside_acl extended permit icmp any any echo-reply
access-list outside_acl extended permit icmp any any time-exceeded
access-list decepticons4 extended permit ip 10.10.29.0 255.255.255.0 10.10.30.0 255.255.254.0
access-list decepticons4 extended permit ip 10.10.29.0 255.255.255.0 10.10.50.0 255.255.254.0
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static net-remote-3 net-remote-3 destination static net-local net-local no-proxy-arp route-lookup description NAT-Exemption for VPN
!
object network local_network
nat (inside,outside) dynamic interface
access-group outside_acl in interface outside
route outside 0.0.0.0 0.0.0.0 76.79.157.177 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
<--- More --->
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
http 10.10.29.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set autobots-transform-and-roll-out esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map cybertron 79 match address decepticons4
crypto map cybertron 79 set peer 66.241.104.40
crypto map cybertron 79 set ikev1 transform-set autobots-transform-and-roll-out ESP-3DES-SHA
crypto map cybertron interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 10
<--- More --->
authentication pre-share
encryption aes
hash sha
group 5
lifetime 86400
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 60
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd dns 8.8.8.8
dhcpd auto_config outside
dhcpd option 3 ip 10.10.29.1
!
dhcpd address 10.10.29.5-10.10.29.25 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cfocususa password F0DMDG1d1mpcVNyR encrypted
tunnel-group 66.241.104.40 type ipsec-l2l
<--- More --->
tunnel-group 66.241.104.40 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
<--- More --->
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:181514d043015479e131aed882b93b45
: end
ciscoasa# sh cry
ciscoasa# sh crypto ipse c sa
There are no ipsec sas
ciscoasa# sh ipsec sa isa
ciscoasa# sh isakmp sa
There are no IKEv1 SAs
There are no IKEv2 SAs
ciscoasa# sh isakmp sa cry
ciscoasa# sh crypto ?
accelerator Show accelerator operational data
ca Show certification authority policy
debug-condition Show crypto debug filters
ikev1 Show IKEv1 operational data
ikev2 Show IKEv2 operational data
ipsec Show IPsec operational data
isakmp Show ISAKMP operational data
key Show long term public keys
protocol Show protocol statistics
sockets Show secure socket information
ssl Show ssl information
ciscoasa# sh crypto ips
ciscoasa# sh crypto ipsec ?
df-bit Show IPsec DF policy
fragmentation Show IPsec fragmentation policy
policy Show IPSec SS-API security policies
sa Show IPsec SAs
stats Show IPsec global statistics
ciscoasa# sh crypto ipsec sa
There are no ipsec sas
ciscoasa# sh crypto ipsec sa stat
ciscoasa# sh crypto ipsec stats
IPsec Global Statistics
-----------------------
Active tunnels: 0
Previous tunnels: 0
Inbound
Bytes: 0
Decompressed bytes: 0
Packets: 0
Dropped packets: 0
Replay failures: 0
Authentications: 0
Authentication failures: 0
Decryptions: 0
Decryption failures: 0
TFC Packets: 0
Decapsulated fragments needing reassembly: 0
Valid ICMP Errors rcvd: 0
Invalid ICMP Errors rcvd: 0
Outbound
Bytes: 0
Uncompressed bytes: 0
Packets: 0
Dropped packets: 0
Authentications: 0
<--- More --->
Authentication failures: 0
Encryptions: 0
Encryption failures: 0
TFC Packets: 0
Fragmentation successes: 0
Pre-fragmentation successses: 0
Post-fragmentation successes: 0
Fragmentation failures: 0
Pre-fragmentation failures: 0
Post-fragmentation failures: 0
Fragments created: 0
PMTUs sent: 0
PMTUs rcvd: 0
Protocol failures: 0
Missing SA failures: 0
System capacity failures: 0
ciscoasa#
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Spoke ASA output.
ciscoasa# sh crypto ipsec sa
There are no ipsec sas
ciscoasa# sh ipse
ciscoasa# sh ipsec sa
There are no ipsec sas
ciscoasa# sh crypto isa
ciscoasa# sh crypto isakmp sa
There are no IKEv1 SAs
There are no IKEv2 SAs
ciscoasa#
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
To permit communication SPOKE1 to SPOKE2, you need to add this nat statement on the HUB:
nat (any,outside) source static SPOKE1-NETWORKS SPOKE1-NETWORKS destination static SPOKE2-NETWORKS SPOKE2-NETWORKS no-proxy-arp route-lookup
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
It seems not possible to add the route-lookup when configuring nat with (any,outside)
nat with (inside,outside) is ok
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Sir,
I´m interested to review this case but with a different thing:
HUB has static ip but the remote devices are Contivities and they have Dynamic IP.
Can you please post an example of ASA HUB to create dynamic VPN´s with multiple remote sites?
>>Site A (Dynamic Public IP)
ASA >>> >>Site B (Dynamic Public IP)
>>Site C (Dynamic Public IP)
We need communication in all of them.
Thanks in advance.
Neyton
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
HI Guys i followed the same solution which has been explained above. after done the configuration all three sites phase-1 and Phase-2 comes up but unable to reach from any of sites to destination. i am working on this solution since last three days continuously but there is no luck at the moment.
below is the config of my Hub FW:
ciscoasa(config)# sh run
: Saved
:
ASA Version 8.4(3)
!
hostname ciscoasa
domain-name arborfshosting.com
enable password MvFWWNGobOrbHMPx encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
!
interface Ethernet0/1
shutdown
!
interface Ethernet0/2
shutdown
!
interface Ethernet0/3
shutdown
!
interface Ethernet0/4
shutdown
!
interface Ethernet0/5
shutdown
!
interface Ethernet0/6
shutdown
!
interface Ethernet0/7
switchport access vlan 10
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan10
nameif outside
security-level 0
ip address 11X.19X.36X.11X 255.255.255.248
!
ftp mode passive
dns domain-lookup inside
dns domain-lookup outside
dns server-group DefaultDNS
name-server 8.8.8.8
domain-name arborfshosting.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network Local-Subnet
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_192.168.1.0_24
subnet 192.168.1.0 255.255.255.0
object network Spoke-1
subnet 192.168.10.0 255.255.255.0
object-group network SPOKE1-NETWORKS
network-object 192.168.10.0 255.255.255.0
object-group network SPOKE2-NETWORKS
network-object 172.17.1.0 255.255.255.0
object-group network HQ-NETWORKS
network-object 192.168.1.0 255.255.255.0
object-group network NAT-EXEMPTION-DESTINATIONS
group-object SPOKE1-NETWORKS
group-object SPOKE2-NETWORKS
object-group network HQ_&_BCP
network-object 192.168.10.0 255.255.255.0
network-object object Local-Subnet
object-group network HQ_&_US
network-object 172.17.1.0 255.255.255.0
network-object object Local-Subnet
access-list VPN-HQ-TO-SPOKE1 extended permit ip object-group HQ_&_US object-group SPOKE1-NETWORKS
access-list VPN-HQ-TO-SPOKE1 extended permit ip object-group SPOKE2-NETWORKS object-group SPOKE1-NETWORKS
access-list outside_access_in extended permit ip any any
access-list VPN-HQ-TO-SPOKE2 extended permit ip object-group HQ_&_BCP object-group SPOKE2-NETWORKS
access-list VPN-HQ-TO-SPOKE2 extended permit ip object-group SPOKE1-NETWORKS object-group SPOKE2-NETWORKS
access-list inside_access_in extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (any,outside) source static HQ-NETWORKS HQ-NETWORKS destination static NAT-EXEMPTION-DESTINATIONS NAT-EXEMPTION-DESTINATIONS no-proxy-arp description NAT-Exemption for VPN
!
object network Local-Subnet
nat (any,outside) dynamic interface
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 11X.19X.36X.11X 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 0.0.0.0 0.0.0.0 inside
http 0.0.0.0 0.0.0.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES256-SHA esp-aes esp-sha-hmac
crypto map VPN 1 match address VPN-HQ-TO-SPOKE1
crypto map VPN 1 set pfs
crypto map VPN 1 set peer 83.16X.1XX.2XX
crypto map VPN 1 set ikev1 transform-set ESP-AES256-SHA
crypto map VPN 2 match address VPN-HQ-TO-SPOKE2
crypto map VPN 2 set pfs
crypto map VPN 2 set peer 20X.1XX.3X.1XX
crypto map VPN 2 set ikev1 transform-set ESP-AES256-SHA
crypto map VPN interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 30
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 30
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
group-policy GroupPolicy_83.16X.1XX.2XX internal
group-policy GroupPolicy_83.16X.1XX.2XX attributes
vpn-tunnel-protocol ikev1
username Dgautam password rOnWdRtRxM6.ZLEP encrypted
tunnel-group 83.16X.1XX.2XX type ipsec-l2l
tunnel-group 83.16X.1XX.2XX general-attributes
default-group-policy GroupPolicy_83.16X.1XX.2XX
tunnel-group 83.16X.1XX.2XX ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 20X.1XX.3X.1XX type ipsec-l2l
tunnel-group 20X.1XX.3X.1XX ipsec-attributes
ikev1 pre-shared-key *****
!
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:cbaef0174bd78907da1e06ead8c49e1d
: end
ciscoasa(config)# sh crypto isakmp sa
IKEv1 SAs:
Active SA: 2
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 2
1 IKE Peer: 20X.1XX.3X.1XX
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
2 IKE Peer: 83.16X.1XX.2XX
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
Crypto map tag: VPN, seq num: 1, local addr: 11X.19X.36X.11X
access-list VPN-HQ-TO-SPOKE1 extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
current_peer: 83.16X.1XX.2XX
#pkts encaps: 37, #pkts encrypt: 37, #pkts digest: 37
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 37, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 11X.19X.36X.11X/0, remote crypto endpt.: 83.16X.1XX.2XX/0
path mtu 1500, ipsec overhead 74, media mtu 1500
current outbound spi: EA588D6B
current inbound spi : B5871D74
Crypto map tag: VPN, seq num: 2, local addr: 11X.19X.36X.11X
access-list VPN-HQ-TO-SPOKE2 extended permit ip 192.168.1.0 255.255.255.0 172.17.1.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.17.1.0/255.255.255.0/0/0)
current_peer: 20X.1XX.3X.1XX
#pkts encaps: 40, #pkts encrypt: 40, #pkts digest: 40
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 40, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 11X.19X.36X.11X/0, remote crypto endpt.: 20X.1XX.3X.1XX/0
path mtu 1500, ipsec overhead 74, media mtu 1500
current outbound spi: 02E90B08
current inbound spi : 41C936F6
please help to get this resolve
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
A document is the wrong place for discussing the problem. Please open a forum-thread in the VPN-section for that.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

