- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Common issues of ISE 1.2 & 1.3 installations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-18-2014 06:20 AM - edited 02-21-2020 10:00 PM
- Introduction
- Prerequisite
- Scenario 1:ISE - WiFi Access only to Authorized Devices rest BYOD blocked
- Scenario 2:File transfer problem during ISE 1.3 upgrade
- Scenario 3:Cisco ISE 1.3 internal CA
- Source Discussion
Introduction
This document describes 3 scenarios of ISE troubleshooting.
Prerequisite
- ISE 1.3
- ISE 1.2
- WLC HA (Code 8.0.100.0)
Scenario 1: ISE - WiFi Access only to Authorized Devices rest BYOD blocked
Problem:
What is MDM?
Mobile device management (MDM) is a security software which is used by an IT department to monitor, manage and secure employees' mobile devices that are deployed across multiple mobile service providers and across multiple mobile operating systems being used in the organization. Mobile device management software is often combined with additional security services and tools to create a complete mobile device and security Enterprise Mobility Management solution.The widespread proliferation of consumerisation of IT means more personal consumer computing devices — such as smartphones, laptops and tablets — are brought to the workplace by employees for use and connectivity on the corporate network. The phrase BYOD (bring your own device) has become widely adopted to refer to these employees. Today's category of mobile device management software is one way that an organization can deliver secure mobile solutions to its BYOD workforce.
You can import all of the mac addresses in ISE and perform mac filtering along with a PEAP-User based authentication. However, keep in mind that using this method is not the most secure one since a mac address can be very easily be spoofed and it is send in clear text. With that being said, a better solution would be to get an MDM (MobileIron, Airwatch, etc), integrate it with ISE and on-board all of the corporate owned devices.
Scenario 2: File transfer problem during ISE 1.3 upgrade
Problem:
User have problem running the upgrade command:
iseadm01/admin# application upgrade cleanup
Application upgrade preparation directory cleanup successful
iseadm01/admin# application upgrade prepare ise-upgradebundle-1.2.x-to-1.3.0.876.x86_64.tar.gz FTP
Getting bundle to local machine...
% File transfer error
iseadm01/admin#
The sniffertrace shows that the ISE 1.2 is sending TCP RST after about 30MB file transfer. If we run the command serveral times, it stops exactly after the same amount of transferred bytes.
The disk utilazation looks OK:
iseadm01/admin# dir
Directory of disk:/
16384 Sep 18 2014 15:55:48 lost+found/
Usage for disk: filesystem
172761088 bytes total used
14275047424 bytes free
15234142208 bytes available
iseadm01/admin#
iseadm01/admin# dir
Directory of disk:/
16384 Sep 18 2014 15:55:48 lost+found/
Usage for disk: filesystem
172761088 bytes total used
14275047424 bytes free
15234142208 bytes available
iseadm01/admin#
User have Another ISE (monitor node) and the problem is exact the same on that node.
Solution:
You can use FileZila for transfering the file.On FileZila click on the User Accounts Icon. The dialog box will show you defined users. By default only anonymous is created.So you need to create a local ftp username and passowrd. Then assign it a home directory under shared folders. This will be the dfault location a remote clietn will look for files and where you would find the ISE upgrade package, for example.
See following screenshot
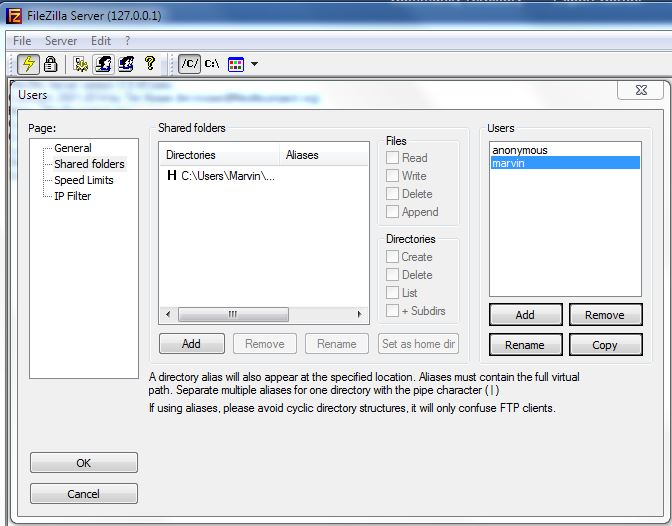
You can upgrade two deployments now - one on VMs and another on ISE 3400 series appliances. Both transferred the images OK. I found it easier to transfer the files separately via FTP. I then created a repository pointing at the disk and referenced that in the upgrade command. I have seen reports of ftp servers on Windows (with WS-FTP and/or IIS) limiting transfers to 30 MB. I used the Filezilla ftp server on windows laptop and it worked very nicely.
Scenario 3: Cisco ISE 1.3 internal CA
Problem:
User is deploying the 1.3 version of ISE(new), he have a distribute environment, with two machines for admin/log personas and two machines for psn's. The problem that he need to solve is about the internal CA, he installed one ISE 1.1 one year ago and used an external CA certificate based to do the authentication via eap and gui admin console with no problems, on this new instalation he would like to use the internal CA, but the documentation is very poor and he don't found how he can initiate this setup using the internal CA.
He know that the CA is the admin primary machine, but he don't know what he need to do(using the gui) to generate the certs of the other machines and register the nodes using the certificates generated by this internal CA.
Solution:
The internal ca is positioned as a ca for byod device on-boarding and not an enterprise ca replacement (for example getting certs onto customer servers or for managed assets such as corporate pcs) again this is for byod use case
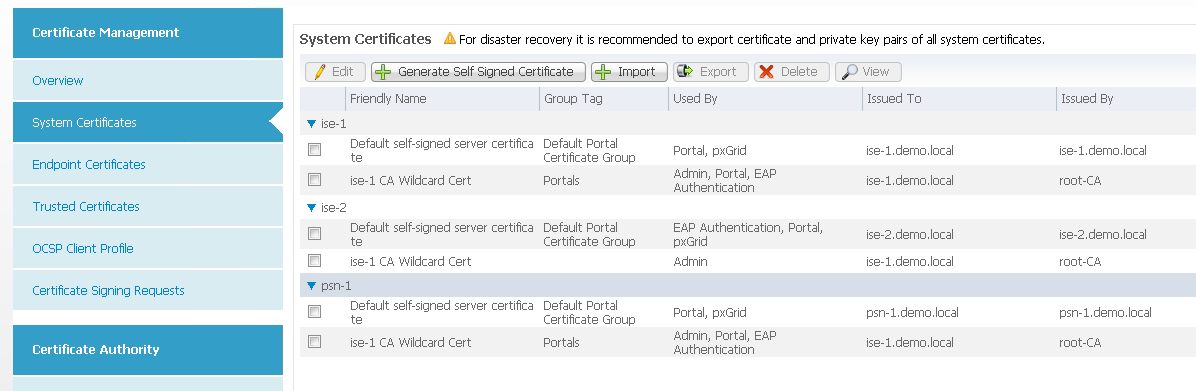
For the other ISE Nodes, create a self-signed cert on that node (this must be done prior to registering it to the Primary Admin Node or it fails) and export the cert. Import the node Self-Signed Cert into the Trusted Certificates store on the Admin Node. You can then register the node.
Do this for all node types. The IPN is vastly different, and the ISE 1.2 Installation guide details those steps. (ISE 1.3 uses the ISE 1.2 IPN). You bind the CSR from your Admin node to the External Root CA. Once the other nodes are registered, the bound cert is copied down to that other node. The bound cert is normally a wildcard cert.
Notice that I have three nodes in this deployment with a single wildcard cert to the nodes that are in my Trusted Certificates store. The wildcard cert is transferred automatically.
Source Discussion
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For scenario#2 it would be helpful to understand what the problem is with the FTP - why it is stopping at 30MB?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: