- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- configure two factor authentication on ASA for cisco ANYconnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-21-2018 10:37 PM - edited 03-08-2019 07:03 PM
RADIUS and Symantec VIP.
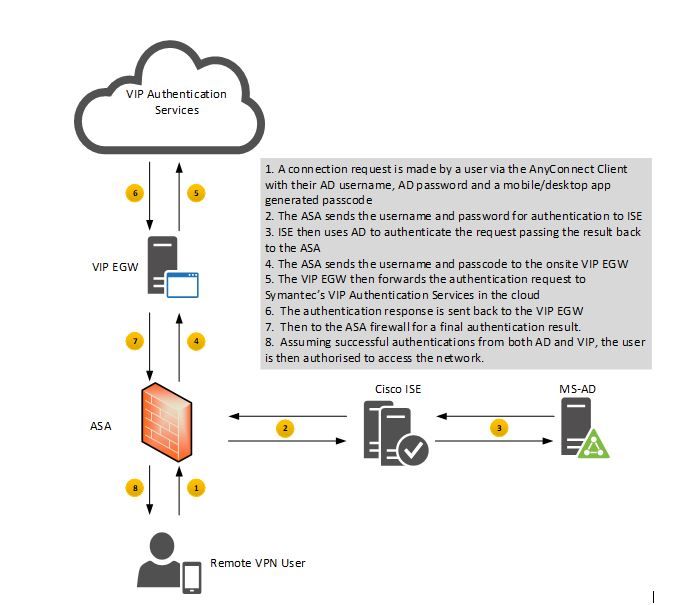
I will use screenshots of ASDM, and at the end I will add the required CLI commands. the diagram below show a diagram of the steps the FW goes through when using 2FA authentication:
As you can see in Fig. 1 the first step in the authentication process is to connect to ISE which then connects to AD, you could configure it to go to AD directly.
Configuration:
Any Connect Connection Profile
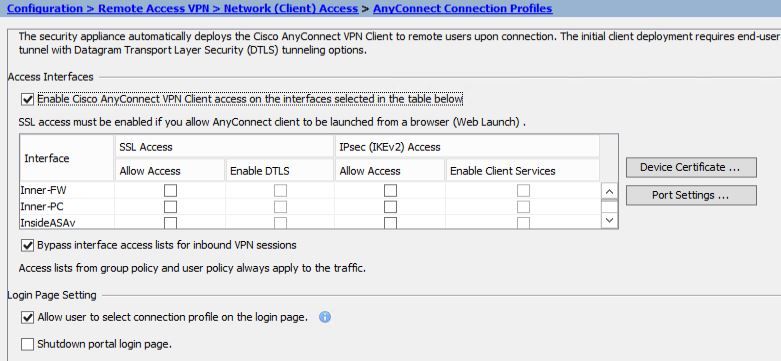
- enable Cisco Anyconnect acces on the outside interface.
- choose to "Bypass interface access lists for inbound VPN sessions
x
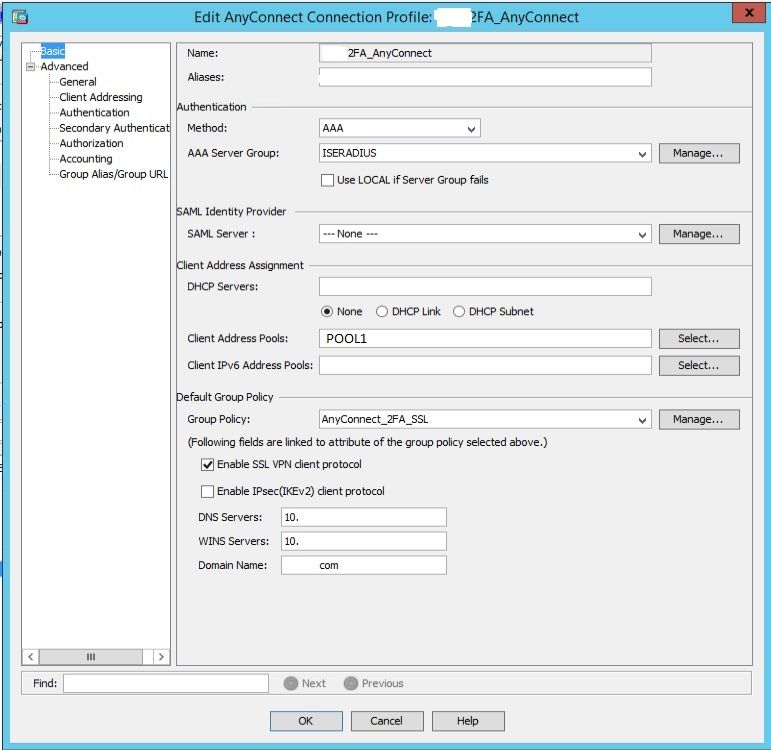
Now drill into the connection profile itself. (Fig.2)
Fig.2. shows that the authentication is set to AAA, which is offloaded to ISE using RADIUS, which authenticates, on (very likely) AD credentials. I will address the ISE configuration part of this in a separate post. So pretty much the first factor is the RADIUS authentication.
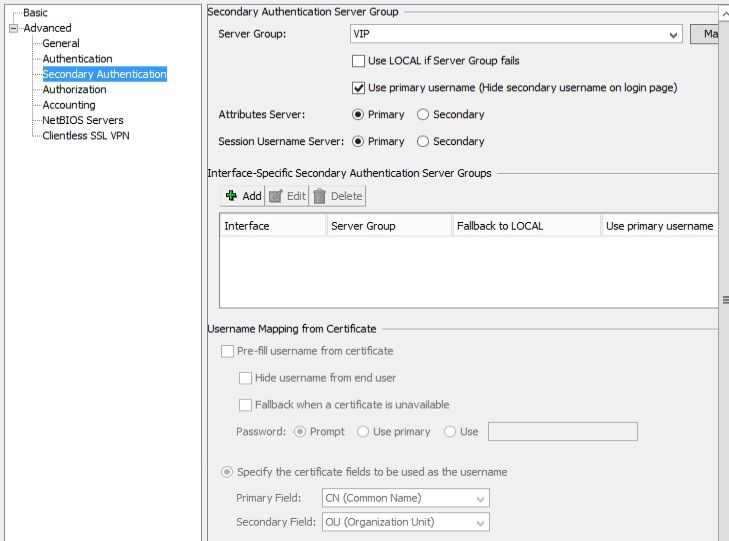
Because 2FA, uses two authentication sources, as the name suggest, you will also need to add a secondary authentication method, this time I have used a server group called VIP (using Symantec's VIP service).
If you are using Symantec or any 3rd party 2FA provider, such as through MS Azure, then you can decide to point your secondary AAA server to either an on premise 2FA gateway or a cloud thingy. Either way, from an ASA point of view you will need a different IP address. Typically, you will connect on ports tcp/1812 for authentication and tcp/1813 for accounting.
Group Policy
Configure a group policy to assign to your connection profile. I prefer to create a separate group policy for each profile, even though I would inherit most of the parameters from the default policy. This makes it easier to make changes that do not impact other connection profiles using the same default values. Assign this group policy to the connection profile in the step above. If you are going to use the Anyconnect client. You would need to select SSL VPN client.
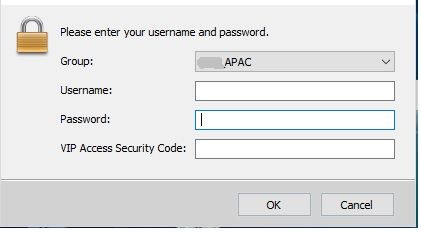
Anyconnect prompt customisation
you might decide to change the anyconnect login prompt to state that the second authentication of a 2FA security code is required. For instance:
To do this, you will need to customize the client's language file:
Config > Remote Access VPN > Network (Client) Access > AnyConnect Customization/Localization > GUI Text and Messages. Edit the language file:
msgid "Second Password"
msgstr "VIP Access Security Code:"
CLI COMMANDS:
group-policy AnyConnect_2FA attributes
vpn-simultaneous-logins 2
vpn-tunnel-protocol ssl-client
webvpn
anyconnect profiles value Test_Client_Profile type user
webvpn
enable Internet
anyconnect image disk0:/anyconnect-win-4.5.01044-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-macos-4.5.01044-webdeploy-k9.pkg 2
anyconnect profiles Test_Client_Profile disk0:/test_client_profile.xml
anyconnect enable
tunnel-group-list enable
tunnel-group 2FA_AnyConnect general-attributes
address-pool Pool1
authentication-server-group ISERADIUS
secondary-authentication-server-group VIP use-primary-username
default-group-policy 2FA_SSL
if you want to use alias for the vpn connection profile:
tunnel-group 2FA_AnyConnect webvpn-attributes
group-alias Test_2FA enable
aaa-server VIPRADIUS (Inside) host 192.168.100.10
timeout 60
key *****
authentication-port 1812
accounting-port 1813
aaa-server VIPRADIUS (Inside) host 192.168.200.10
timeout 60
key *****
authentication-port 1812
accounting-port 1813
Namaste!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice document, comes in real handy as I'll try in in the next couple of weeks.
Is there also documentation/notes/howto towards implementing 2fa on the Firepower devices?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thanks for the feedback
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Pushpendra,
Were you able to achieve it? Please advise on how to do it.
Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Also using
OpenVPN
Palo Alto
Fortinet
Cisco AnyConnect
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please assist if possible, and also, could you provide information on the required configurations for SMS integration on both ends?
Thank you,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: