- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Creating a SHA-2 Certificate Signing Request using ECDSA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-03-2016 12:58 PM
Creating a SHA-2 CSR using ECDSA
Support
In ASA OS 9.0(1), released October 29, 2012, the ASA introduced support for creating ECDSA key pairs. Prior to this version certificates had to be created again RSA key pairs. Now we have the ability to create CSR's that use ECDSA keys.
Be aware however, these certificates can not be used with SSL VPN unless your ASA is running a version of code that supports elliptic curve ciphers.
Testing your CSR
You can test this by creating two keys and testing them against a CSR test site like Symantec or CertLogik
This is how we created RSA Key pairs.
This should NOT be used and is only shown for clarification & comparison.
! Create the keypair
crypto key gen rsa label my.rsa2048.key modulus 2048 noconfirm
!
! Create the CSR
crypto ca trustpoint my-trustpoint.lab-asa.xxxx.com
subject-name CN=lab-asa.xxxx.com,O=My Company Inc,C=US,St=Pennsylvania,L=MyCity
fqdn lab-asa.xxxx.com
enrollment terminal
keypair my.rsa2048.key
exit
!
! Enroll the certificate
crypto ca enroll my-trustpoint.lab-asa.xxxx.com
!
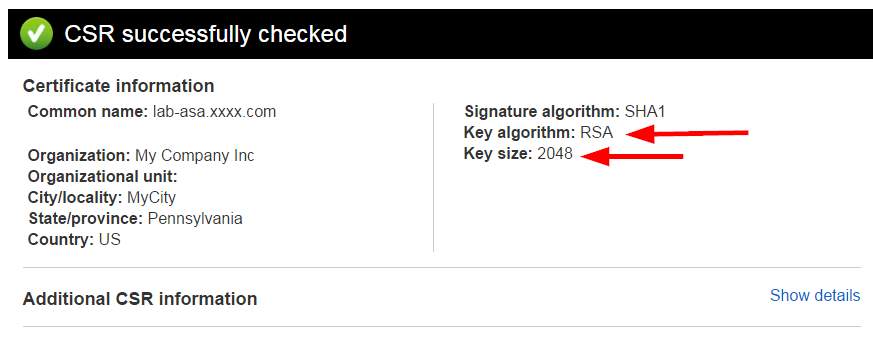
Now go to Symantec's website and paste in the CSR from your ASA. You will see that the Key algorithm is RSA and the Key Size is 2048. Just like we used when we created the key on the ASA.
Create a CSR that has 256 bit ECDSA keypair.
This is the new method and should be used.
! Create the keypair
crypto key gen ecdsa label my.ecdsa.key elliptic-curve 256 noconfirm
!
! Create the CSR
crypto ca trustpoint my-trustpoint.lab-asa.xxxx.com
subject-name CN=lab-asa.xxxx.com,O=My Company Inc,C=US,St=Pennsylvania,L=MyCity
fqdn lab-asa.xxxx.com
enrollment terminal
keypair my.ecdsa.key
exit
!
! Enroll the certificate
crypto ca enroll my-trustpoint.lab-asa.xxxx.com
!
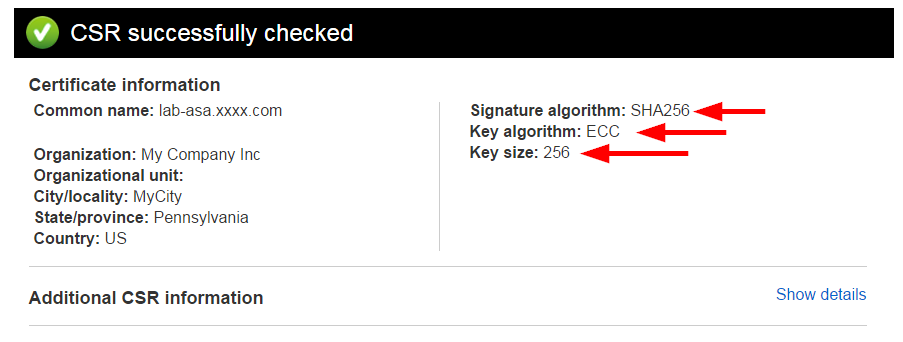
You will notice that the ECDSA Key Size is 256 bits. You may be concerned that it is far less than the 2048 bit RSA key. You should not be concerned because shorter elliptical curve key pairs are as strong or stronger than longer RSA keys.
Create a CSR that has 384 bit ECDSA keypair.
! Create the keypair
crypto key gen ecdsa label my.384ecdsa.key elliptic-curve 384 noconfirm
!
! Create the CSR
crypto ca trustpoint my-trustpoint.lab-asa.xxxx.com
subject-name CN=lab-asa.xxxx.com,O=My Company Inc,C=US,St=Pennsylvania,L=MyCity
fqdn lab-asa.xxxx.com
enrollment terminal
keypair my.384ecdsa.key
exit
!
! Enroll the certificate
crypto ca enroll my-trustpoint.lab-asa.xxxx.com
!
Please comment , rate , reply. Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the information Tim.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In regards on using openssl for a load-balanced VPN solution, do the same as here (openssl.cfg): https://www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/200339-Configure-ASA-SSL-Digital-Certificate-I.html#anc8
Then create a key file with ECDSA-384:
openssl ecparam -name secp384r1 -genkey -noout -out vpn.hostname.ecdsa.key
Then create the CSR:
openssl req -new -nodes -sha256 -key vpn.hostname.ecdsa.key -out vpn.hostname.ecdsa.csr -config openssl.cfg
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

