- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- FMC Site-to-Site VPN Troubleshooting
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 11-23-2022 09:46 AM
We are setting up two Firepower 1010s, with FTD, version 7.0.4. These are controlled by Firepower Management Center.
I'm trying to setup a Site-to-Site VPN, IKEv2, with a third party VPN device.
I need to troubleshoot why it is not working. I'm not sure where to look for errors.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
First step to verify :
is the public IP you using to tunnel peer reachable ?
both the FW FTD and other side internet facing and reachable
- is the agreed config both the side matches ?
check below guide :
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
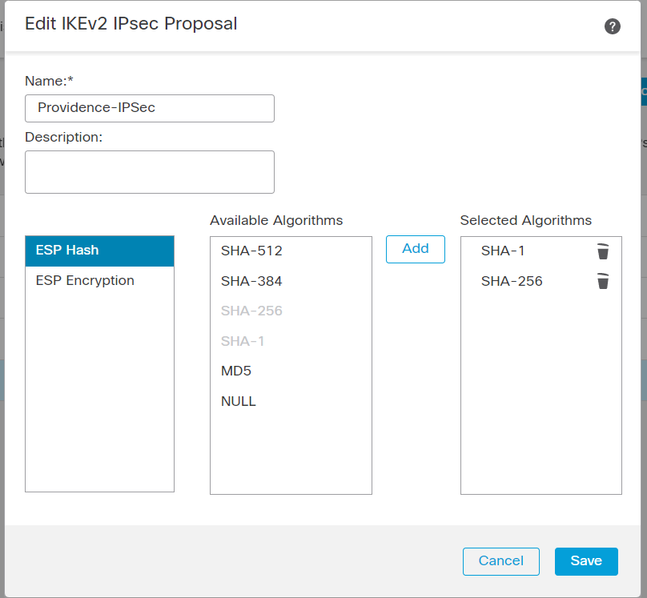
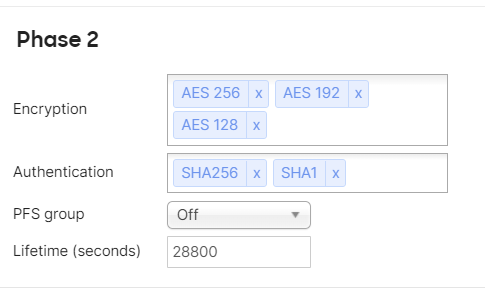
I got phase 1 connected, but not phase 2. I have the configuration as follows. I can't see a missmatch.
The FTD shows the following:
> show crypto ikev2 sa detail
IKEv2 SAs:
Session-id:6, Status:UP-IDLE, IKE count:1, CHILD count:0
Tunnel-id Local Remote Status Role
843825709 199.59.217.8/4500 166.137.148.169/39763 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/6494 sec
Session-id: 6
Status Description: Negotiation done
Local spi: F83AE1FE9C636591 Remote spi: 6121AC8923B4782A
Local id: 199.59.217.8
Remote id: 166.137.171.22
Local req mess id: 0 Remote req mess id: 780
Local next mess id: 0 Remote next mess id: 780
Local req queued: 0 Remote req queued: 780
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is detected outside
IKEv2 Fragmentation Configured MTU: 576 bytes, Overhead: 28 bytes, Effective MTU: 548 bytes
Parent SA Extended Status:
Delete in progress: FALSE
Marked for delete: FALSE
Error code: Failed to find a matching policy
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Error code: Failed to find a matching policy
run the debug using below guide on FTD, (third-party VPN device -what is the other device ?)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
PFS need to enable for Phase2 of IKEv2, this will build the child SA for connection.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: