We recently had a customer that wanted to use ISE for a Wireless Hotspot with the following requirements:
1. Guests could only gain network access during business hours
2. Guests would be required to accept an Acceptable Use Policy (AUP)
3. Guests would be limited to 2 hours of network access per day (similar to common hotel access)
The customer did not want to use either the Sponsored Guest or Self-Registered Guest flows, so we could not leverage the Guest Type settings for Maximum Account Duration or access times.
Using information from jakunst found in the Community post at the link below, we found that we could use the LastAUPAcceptance condition to accomplish this.
https://communities.cisco.com/message/276046#276046
Here are the steps we used to test and validate this scenario with ISE version 2.2:
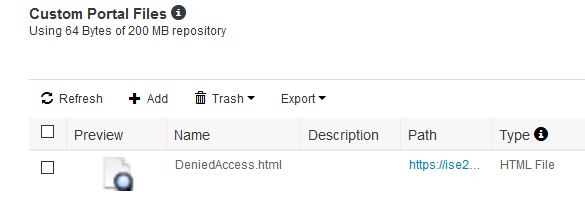
1. Created a basic HTML page that informs the Guest that network access is denied due to either non-business hours or the daily time has been exceeded. Uploaded the page to the Work Centers > Guest Access > Custom Portal Files repository.
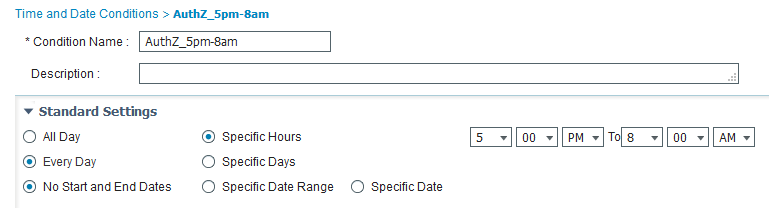
2. Created a Time and Date Condition for the non-business time range of 5pm - 8am.
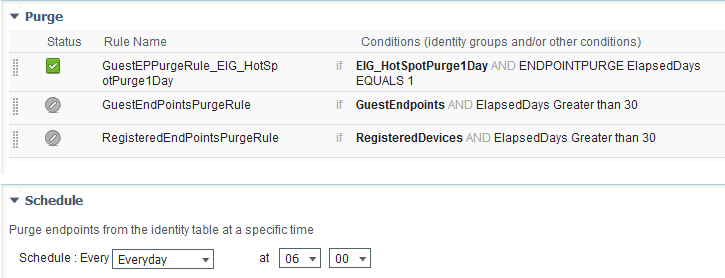
3. Created an Endpoint Identity Group called EIG_HotspotPurge1Day and added an Endpoint Purge Policy rule that is run daily before 8am.
4. Created the Hotspot Portal with the Endpoint ID Group set to EIG_HotspotPurge1Day.
5. Created three Authorization Profiles:
- AuthZ-Wireless-Redirect-Hotspot: Standard Hotspot redirection pointing to the Hotspot Portal.
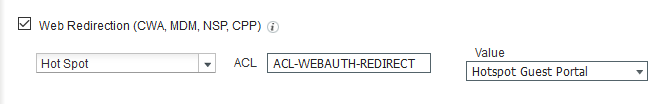
- AuthZ-Wireless-Redirect-BlockPage: Redirect to the custom HTML block page using the Advanced Attributes. The URL for the page is copied from the Custom Portal Files page.
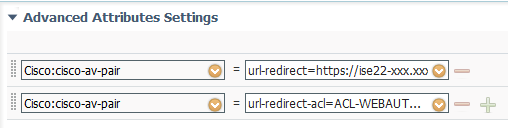
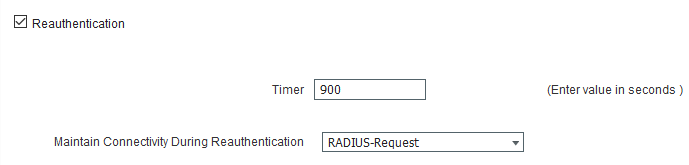
- AuthZ-Wireless-PSK-Guest: Standard ACCESS-ACCEPT response with a Reauthentication timer of 900 seconds sent to the WLC.
6. Created a new Policy Set to match on the SSID name (iselabpsk).
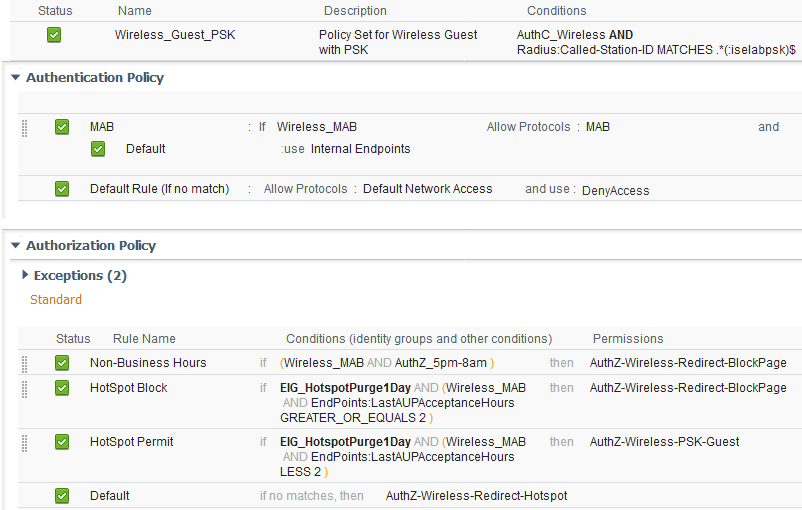
Note: The customer also wanted the SSID to use a Pre-Shared Key, so we used WLC code 8.3.140.0 with the settings from the link below. The same could be done with an open SSID commonly used for wireless Guest.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-3/config-guide/b_cg83/b_cg83_chapter_0100111.html#id_29451
I hope others find this information useful.