- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IP Phone SSL VPN to ASA using AnyConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-05-2010 08:06 AM - edited 08-28-2017 10:14 PM
- Purpose
- Functional Overview
- CUCM Places ASA Certificate Hash and VPN URL in Phone Config
- Phone Connects to ASA
- Software Versions
- Phone Models
- CUCM Configuration
- Phone Configuration
- ASA Configuration
- Additional Requirements:
- Troubleshooting Steps
- Common Issues
Purpose
Starting in CUCM 8.0.1 and IP Phone Firmware 9.X, IP Phones are now able to directly connect to an ASA using the AnyConnect VPN. This document will help address some common issues encountered during intial configuration. This guide will act as a supplement to the Official IP Phone VPN Documentation.
Functional Overview
Before we get into versions and model numbers let's look at how the feature works.
CUCM Places ASA Certificate Hash and VPN URL in Phone Config
Before the phone is ready for VPN, it must first be provisioned using the internal network. This requires direct access to the CUCM TFTP server.
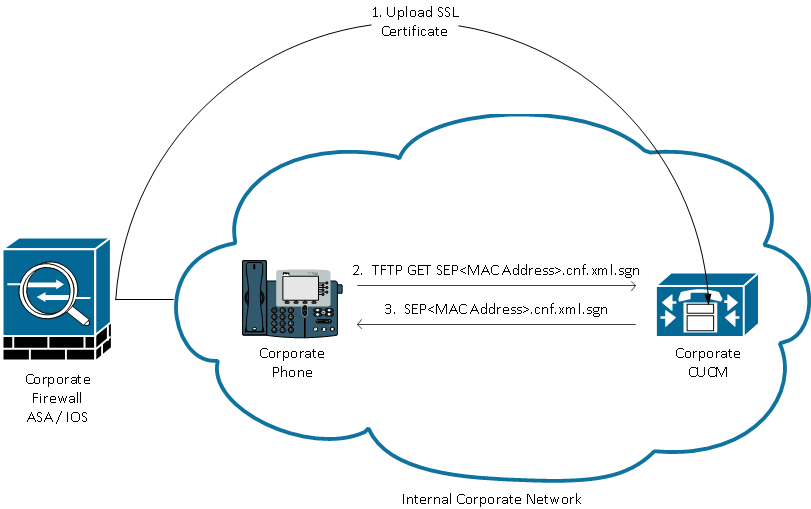
The first step after the ASA is fully configured is to take the ASA HTTPS Certificate and upload it to the CUCM server. This allows the CUCM server to build an IP phone config file that tells the phone how to get to the ASA. The CUCM requires some additional configuration to associate the uploaded certificate with a VPN Profile that can be assigned to the phone.
Here is an example of the IP Phone VPN section of a phone's config file after performing the required configuration:
jasburns@jasburns-gentoo /home/jasburns $ tftp 14.48.44.80 tftp> get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /home/jasburns $ cat SEP0011215A1AE3.cnf.xml.sgn .......... <vpnGroup> [Some Lines Omitted] <addresses> <url1>https://X.X.X.X/PhoneVPN</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>
Note that the URL is printed exactly as entered on the VPN Gateway Configuration page in CUCM. Make sure the IP Phone can resolve this address.
Even more interesting is the Cert Hash. The IP phone configuration does not contain the entire certificate, merely a SHA1 Base64 encoded hash of the certificate.
You can compare the certificate hash in the IP phone configuration file to the cert hash of the actual file on the ASA or CUCM if you copy it to a computer running OpenSSL (either Windows, Linux, or Mac)
$ cat r2800.cisco.com.pem
-----BEGIN CERTIFICATE-----
<Base64 value of the cert omitted>
-----END CERTIFICATE-----
openssl x509 -in r2800.cisco.com.pem -noout -fingerprint
SHA1 Fingerprint=D5:E0:FD:97:75:44:23:D0:C6:59:01:8A:94:D0:46:13:56:D1:85:48
This is the SHA1 Fingerprint in Hexadecimal form. In the configuration file this value is instead printed as the Base64 value. I used the following website to convert from Hex to Base64:
http://tomeko.net/online_tools/hex_to_base64.php
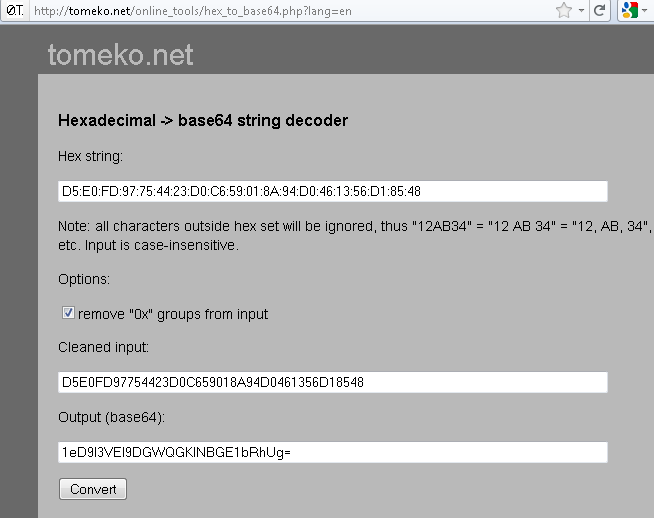
This method can be used to verify the certificate loaded onto and presented by the ASA matches the certificate hash loaded into the phone.
Phone Downloads Configuration
This part is extremely important. The phone must download the configuration (including the certificate hash in Base64) while it is inside the network and has direct access to the CUCM TFTP server.
The phone has to be provisioned inside the network before it can be moved outside the network and use the VPN feature.
Phone Connects to ASA
After internal provisioning has been completed, the phone can be moved to the external network for VPN access. Here the Corporate Phone has been moved to a Home location.
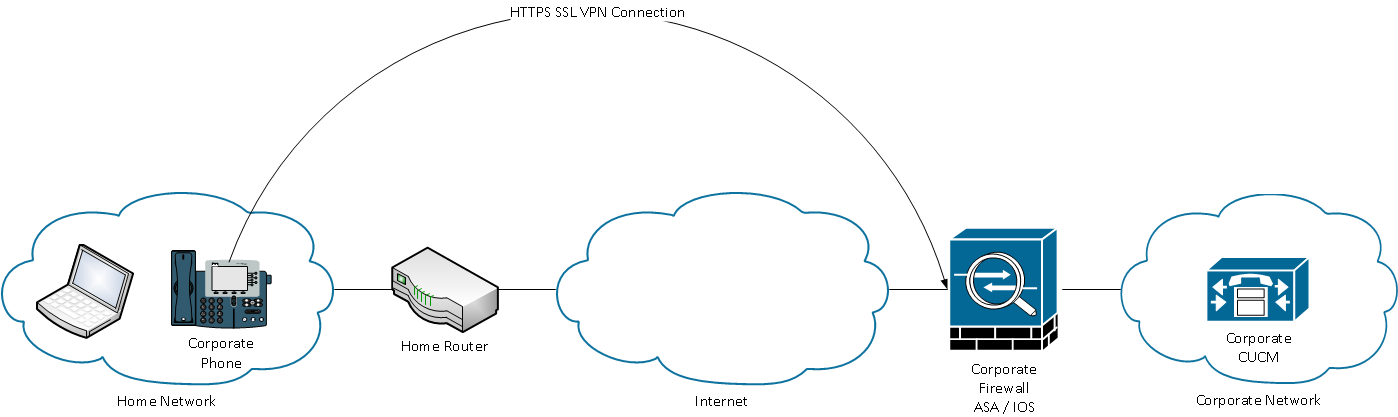
Depending on the phone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once manually initiated. If auto network detect is enabled, the phone will try to ping the TFTP server. If there is no response to this ping request the phone will automatically bring up the VPN process on the phone.
The phone connects on TCP port 443 over HTTPS to the ASA. The ASA responds back with the configured certificate, hopefully the same certificate uploaded to CUCM. In additional TCP 443 (Transport Layer Security, or TLS), the phone will also connect on UDP 443 for DTLS (Datagram Transport Layer Security).
Phone Verifies Presented Certificate
The phone console logs show us the hash of the certificate that the ASA presents in Hex form:
3943: INF 18:10:22.354209 VPNC: vpnc_save_to_file: wrote: </tmp/leaf.crt>, 479 bytes
3944: NOT 18:10:22.355351 VPNC: cert_vfy_cb: peer cert saved: /tmp/leaf.crt
3945: NOT 18:10:22.361892 SECD: Leaf cert hash = D5E0FD97754423D0C659018A94D0461356D18548
3946: NOT 18:10:22.362574 SECD: Hash was found in the trust list
3947: NOT 18:10:22.400294 VPNC: VPN cert chain trusted
These messages show us that the phone was able to validate the certificate that the ASA presented. The cert presented matched the hash in the configuration file.
At this point the phone will establish an SSL session with the ASA and continue setting up the VPN tunnel.
All communication will now flow between the phone and the ASA in an encrypted tunnel. Once the traffic reaches the ASA it will be decrypted and forwarded along to any location in the network that the phone would like to connect to.
The beauty of this solution is that the phone obtains an address on the Internal network that is typically not filtered. The phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Corporate Network. This allows advanced phone services and features to function that might not work through ASA Phone Proxy.
Software Versions
CUCM >= 8.0.1.100000-4
IP Phone >= 9.0(2)SR1S - SCCP
ASA >= 8.0.4
Anyconnect VPN Pkg >= 2.4.1012
Note: A "Premium" license and an "AnyConnect for Cisco VPN Phone" license is required. The part number for the "AnyConnect for Cisco VPN Phone" is L-ASA-AC-PH-55XX= where XX = 05,10,20,40,50,80.
Phone Models
7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete list of supported phones in your CUCM version go to:
https://<CUCM Server IP Address>:8443/cucreports/systemReports.do
Unified CM Phone Feature List
Generate a new report
Feature: Virtual Private Network
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full and correct address to reach the IP Phone VPN tunnel-group on the ASA.
Phone Configuration
- Use a supported phone model per the CUCM Supported Models / Features report.
- Register the phone to the CUCM server on the Internal network
- Configure the IP phone with a TFTP server manually.
- Move the phone to the external network.
ASA Configuration
Configure Anyconnect VPN access on ASA to provide network access.
See http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml for example configuration.
The lateset CUCM Security Guide also provides sample ASA configuration.
Additional Requirements:
- The ASA must have the AnyConnect for Cisco VPN Phone Licensed feature enabled. Licensing info can be found using show version command.
- Group-policy must not be configured with split tunnel or split exclude. Only tunnel all is the supported tunneling policy
- The tunnel-group used can not be the DefaultWEBVPNGroup. Create another tunnel-group and use "group-url https://x.x.x.x/phonevpn enable to map to the correct tunnel-group.
- DTLS must be enabled and negotiated for operation. This requires both tcp/443 and udp/443 to be open and allowed on all devices between the ASA and the phone.
Troubleshooting Steps
- Plug the phone into the internal network. This will test whether the phone's configuration works prior to adding VPN.
- Connect with AnyConnect on a PC from the outside to the ASA. This will confirm that the ASA is configured correctly for Anyconnect
- From the connected PC try to ping the TFTP server and CUCM server. This will test basic ip connectivity to the two servers.
- From the PC try to download the TFTP config file for the phone in question "tftp -i <TFTP Server> GET SEP<Mac Address>.cnf.xml" This will test that the tftp service is reachable and serving files.
- From the PC try to telnet to TCP Port 2000 on the CUCM server "telnet <CUCM IP> 2000". This should immediately come back with a new line and a blank cursor. This will test connectivity to the CUCM SCCP port, for SIP registrations use port 5060 instead.
Common Issues
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints.
- Auto Network Detect does not reliably work in IP Phone Firmware 9.0(2), but does work as expected in 9.2(1).
- Auto Network Detect allows the phone to detect whether it is inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly.
- The phone uses a series of pings to the TFTP server to determine whether it is outside the network. If pings to the TFTP server fail, the VPN GUI will be brought up on the phone and the phone will attempt to access the VPN URL.
- Username and Password authentication from the phone does NOT support the SPACE character in either the username or the password.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
while the ip phone is outside, it can't take the ring tones as the internal ip phones
when putting the tftp ip address manually to point to the cucm, it gives vpn authentication fail
Plz help how to get the ring tones for the ouside phones or what may prevent the phone from getting it
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Could you please advise what is the format of the "VPN gatway url "we should configure on the CUCM? firstly, should we configure this url on the ASA? If yes, what are the procedures for doing this?
Thanks in advance
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Is there any update regarding my above query?
Thanks in advance
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ala Raed Issa,
As mentioned in the article above you will need to configure a url on the ASA like the following:
You will need to do that under the tunnel-group. After that in the CUCM you put the following the phone config file:
<vpnGroup>
[Some Lines Omitted]
<addresses>
<url1>https://X.X.X.X/phonevpn</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jay,
Really, many thanks for your response.
in addtion, could you please provide me with the part number of the required "premium license" ???
Really, thanks in advance for your repsonse.
Best Regards,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
any one got all the ringtones downloaded while the phone is outside ??
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jay and all,
Is there any update regarding the part number of the required "premium license" ???
Thanks in advance
Warmest Regards,
Ala'a Issa
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ala'a Issa,
The license FRU number is: ASA5500-SSL-XXXX
Where XX could be: 10,25,50,100,250,500,750,1000,2500,5000,10K
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
we have 2 questions we wanted to ask you guys about this setup.
1. we currently use Cisco NAC and Cisco ISE for remediation control. Do we need to manually exclude the mac of the phone before sending it to the field, or will NAC/ISE recognize the MAC as a phone?
2. Does the PC Port on the phone ALSO get vpn access? Is the only way to "disable" the pc port is through UCM, then lock the settings so a user can not "piggy back" into the network through the phone?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Don,
1. NAC / ISE - I don't know the answer to this question.
2. Does the PC Port on the phone get VPN Access?
No - the PC port does not have access to the VPN. Only the phone has SSL VPN access. The PC port will have access to the local network where the phone is plugged in.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Don,
I don't believe that the phones have a NAC agent installed on them nor CSD. In addition since the connection is coming over a VPN the MACs of the phone will not be used when being sent out the inside of the ASA.
As a result:
NAC - don't have an agent so can't validate with the CAS.
ISE - The ASA doesn't have any of the endpoint attributes from the phone since CSD won't run. As a result we can't make a policy decision on that info.
The solution for you is to setup another tunnel-group and group-policy specifically for the phones. Setup a separate vlan to have them dumped into and on the CAS allow that vlan to pass.
Hope that helps.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Any one here tried to restore a call manager backup after sending the phone outside, Will the call manager retain the certificate using the restore ? or the outside phones will fail and need to come home again ??
Regards
Haitham
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Haitham,
The CUCM backup and restore should restore the VPN certificate and VPN Gateway and Group configuration as well during a DRS Restore.
Your outside phones wouldn't be affected and should register to the CUCM again once it was restored.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is is possible to use a IOS router at the head end to terminate the phone VPN instead of the ASA ?
Say like a 29xx/39xx series ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

