- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IP Phone SSL VPN to ASA using AnyConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-05-2010 08:06 AM - edited 08-28-2017 10:14 PM
- Purpose
- Functional Overview
- CUCM Places ASA Certificate Hash and VPN URL in Phone Config
- Phone Connects to ASA
- Software Versions
- Phone Models
- CUCM Configuration
- Phone Configuration
- ASA Configuration
- Additional Requirements:
- Troubleshooting Steps
- Common Issues
Purpose
Starting in CUCM 8.0.1 and IP Phone Firmware 9.X, IP Phones are now able to directly connect to an ASA using the AnyConnect VPN. This document will help address some common issues encountered during intial configuration. This guide will act as a supplement to the Official IP Phone VPN Documentation.
Functional Overview
Before we get into versions and model numbers let's look at how the feature works.
CUCM Places ASA Certificate Hash and VPN URL in Phone Config
Before the phone is ready for VPN, it must first be provisioned using the internal network. This requires direct access to the CUCM TFTP server.
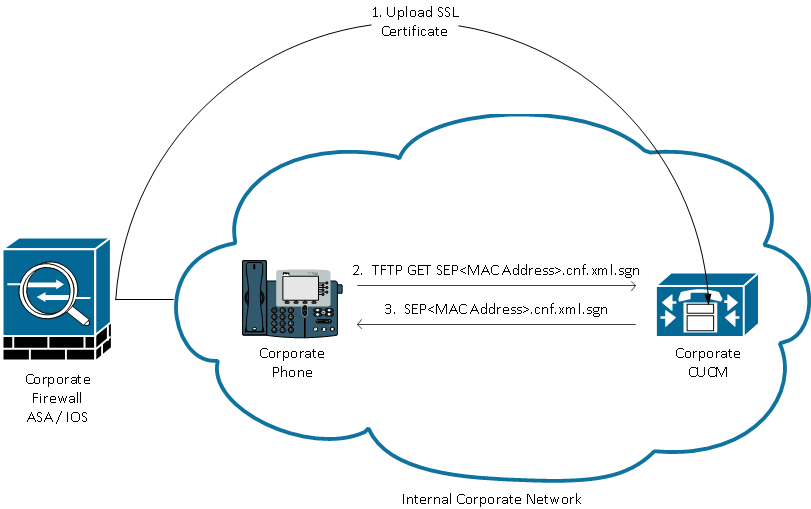
The first step after the ASA is fully configured is to take the ASA HTTPS Certificate and upload it to the CUCM server. This allows the CUCM server to build an IP phone config file that tells the phone how to get to the ASA. The CUCM requires some additional configuration to associate the uploaded certificate with a VPN Profile that can be assigned to the phone.
Here is an example of the IP Phone VPN section of a phone's config file after performing the required configuration:
jasburns@jasburns-gentoo /home/jasburns $ tftp 14.48.44.80 tftp> get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /home/jasburns $ cat SEP0011215A1AE3.cnf.xml.sgn .......... <vpnGroup> [Some Lines Omitted] <addresses> <url1>https://X.X.X.X/PhoneVPN</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>
Note that the URL is printed exactly as entered on the VPN Gateway Configuration page in CUCM. Make sure the IP Phone can resolve this address.
Even more interesting is the Cert Hash. The IP phone configuration does not contain the entire certificate, merely a SHA1 Base64 encoded hash of the certificate.
You can compare the certificate hash in the IP phone configuration file to the cert hash of the actual file on the ASA or CUCM if you copy it to a computer running OpenSSL (either Windows, Linux, or Mac)
$ cat r2800.cisco.com.pem
-----BEGIN CERTIFICATE-----
<Base64 value of the cert omitted>
-----END CERTIFICATE-----
openssl x509 -in r2800.cisco.com.pem -noout -fingerprint
SHA1 Fingerprint=D5:E0:FD:97:75:44:23:D0:C6:59:01:8A:94:D0:46:13:56:D1:85:48
This is the SHA1 Fingerprint in Hexadecimal form. In the configuration file this value is instead printed as the Base64 value. I used the following website to convert from Hex to Base64:
http://tomeko.net/online_tools/hex_to_base64.php
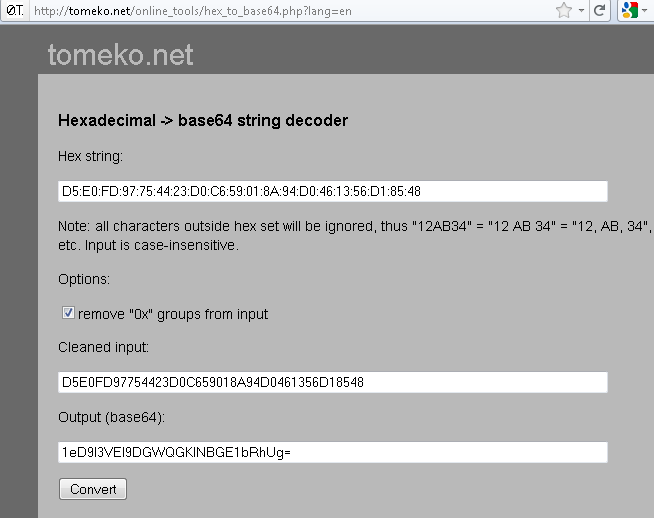
This method can be used to verify the certificate loaded onto and presented by the ASA matches the certificate hash loaded into the phone.
Phone Downloads Configuration
This part is extremely important. The phone must download the configuration (including the certificate hash in Base64) while it is inside the network and has direct access to the CUCM TFTP server.
The phone has to be provisioned inside the network before it can be moved outside the network and use the VPN feature.
Phone Connects to ASA
After internal provisioning has been completed, the phone can be moved to the external network for VPN access. Here the Corporate Phone has been moved to a Home location.
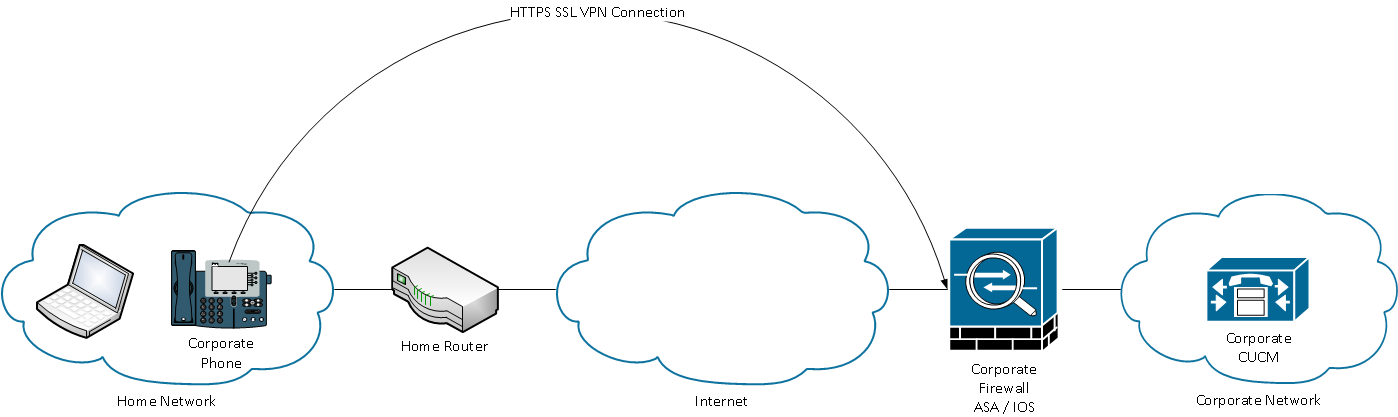
Depending on the phone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once manually initiated. If auto network detect is enabled, the phone will try to ping the TFTP server. If there is no response to this ping request the phone will automatically bring up the VPN process on the phone.
The phone connects on TCP port 443 over HTTPS to the ASA. The ASA responds back with the configured certificate, hopefully the same certificate uploaded to CUCM. In additional TCP 443 (Transport Layer Security, or TLS), the phone will also connect on UDP 443 for DTLS (Datagram Transport Layer Security).
Phone Verifies Presented Certificate
The phone console logs show us the hash of the certificate that the ASA presents in Hex form:
3943: INF 18:10:22.354209 VPNC: vpnc_save_to_file: wrote: </tmp/leaf.crt>, 479 bytes
3944: NOT 18:10:22.355351 VPNC: cert_vfy_cb: peer cert saved: /tmp/leaf.crt
3945: NOT 18:10:22.361892 SECD: Leaf cert hash = D5E0FD97754423D0C659018A94D0461356D18548
3946: NOT 18:10:22.362574 SECD: Hash was found in the trust list
3947: NOT 18:10:22.400294 VPNC: VPN cert chain trusted
These messages show us that the phone was able to validate the certificate that the ASA presented. The cert presented matched the hash in the configuration file.
At this point the phone will establish an SSL session with the ASA and continue setting up the VPN tunnel.
All communication will now flow between the phone and the ASA in an encrypted tunnel. Once the traffic reaches the ASA it will be decrypted and forwarded along to any location in the network that the phone would like to connect to.
The beauty of this solution is that the phone obtains an address on the Internal network that is typically not filtered. The phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Corporate Network. This allows advanced phone services and features to function that might not work through ASA Phone Proxy.
Software Versions
CUCM >= 8.0.1.100000-4
IP Phone >= 9.0(2)SR1S - SCCP
ASA >= 8.0.4
Anyconnect VPN Pkg >= 2.4.1012
Note: A "Premium" license and an "AnyConnect for Cisco VPN Phone" license is required. The part number for the "AnyConnect for Cisco VPN Phone" is L-ASA-AC-PH-55XX= where XX = 05,10,20,40,50,80.
Phone Models
7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete list of supported phones in your CUCM version go to:
https://<CUCM Server IP Address>:8443/cucreports/systemReports.do
Unified CM Phone Feature List
Generate a new report
Feature: Virtual Private Network
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full and correct address to reach the IP Phone VPN tunnel-group on the ASA.
Phone Configuration
- Use a supported phone model per the CUCM Supported Models / Features report.
- Register the phone to the CUCM server on the Internal network
- Configure the IP phone with a TFTP server manually.
- Move the phone to the external network.
ASA Configuration
Configure Anyconnect VPN access on ASA to provide network access.
See http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml for example configuration.
The lateset CUCM Security Guide also provides sample ASA configuration.
Additional Requirements:
- The ASA must have the AnyConnect for Cisco VPN Phone Licensed feature enabled. Licensing info can be found using show version command.
- Group-policy must not be configured with split tunnel or split exclude. Only tunnel all is the supported tunneling policy
- The tunnel-group used can not be the DefaultWEBVPNGroup. Create another tunnel-group and use "group-url https://x.x.x.x/phonevpn enable to map to the correct tunnel-group.
- DTLS must be enabled and negotiated for operation. This requires both tcp/443 and udp/443 to be open and allowed on all devices between the ASA and the phone.
Troubleshooting Steps
- Plug the phone into the internal network. This will test whether the phone's configuration works prior to adding VPN.
- Connect with AnyConnect on a PC from the outside to the ASA. This will confirm that the ASA is configured correctly for Anyconnect
- From the connected PC try to ping the TFTP server and CUCM server. This will test basic ip connectivity to the two servers.
- From the PC try to download the TFTP config file for the phone in question "tftp -i <TFTP Server> GET SEP<Mac Address>.cnf.xml" This will test that the tftp service is reachable and serving files.
- From the PC try to telnet to TCP Port 2000 on the CUCM server "telnet <CUCM IP> 2000". This should immediately come back with a new line and a blank cursor. This will test connectivity to the CUCM SCCP port, for SIP registrations use port 5060 instead.
Common Issues
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints.
- Auto Network Detect does not reliably work in IP Phone Firmware 9.0(2), but does work as expected in 9.2(1).
- Auto Network Detect allows the phone to detect whether it is inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly.
- The phone uses a series of pings to the TFTP server to determine whether it is outside the network. If pings to the TFTP server fail, the VPN GUI will be brought up on the phone and the phone will attempt to access the VPN URL.
- Username and Password authentication from the phone does NOT support the SPACE character in either the username or the password.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Glenn, we ran into these issues and I opened up a support ticket. For the DHCP, I found a workaround by sending the phone an invalid TFTP server via DHCP. TAC took note of the issue and requested a feature enhancement.
For the second issue, we have alot of remote phones that connect this way and there hasnt been a good work around yet. Users just have to hit the reconnect key. Hope this helps.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Eric - thanks for the response. Unfortunately we can't control the other networks -- mostly these are users based in their homes or other environments where we have no administrative privilege for the DHCP services. Instead of fighting this one, we've just been telling users to go into security settings on the phone and enable VPN. This seems to work for us so far.
I would very much like to see the VPN client in the phone reconnect / re-register, especially if using username/password authentication with saved credentials. It's a difficult conversation with management when this happens -- an end-user does not typically watch their phone's display screen constantly, so if a VPN connection is interrupted it may go unnoticed for quite a while ( and the end-user is missing calls the whole time ).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
JC, yes you need to manually setup the TFTP using alternate TFTP on the phone because we cannot trust the ISP/home router to provide an option 150 or option 66 TFTP address that matches the TFTP of the internal CUCM. Put the real TFTP IP address in there also. The auto network detect feature actually uses the TFTP address that is manually configured on the phone. The phone tries to ping the TFTP address, if it gets a response the phone determines it's internal and does not start the VPN, if it does not get a reply it determines the phone is external and starts the VPN client. Catches, if the CUCM TFTP has a common home router IP like 192.168.1.1, the phone will always think it is internal and not automatically start the VPN client.
As for automatically reconnecting to the VPN the best way I've found is to use certificate based authentication. The phone will automatically connect with no user intervention as soon as the connection to the ASA is back up.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So the only thing we should never do is to change the CUCM TFTP server IP or we'll have to manually change settings on each phone outside...
Is there any interest to configure an external ip address in the 2nd alternate TFTP field, so we could activate it on request and put on it an updated phone MAC.cnf.xml file ? It has been previously discussed but I don't see the aim of this trick.
JC
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am unable to get a remote IP Phone to connect using the Cisco VPN Phone.
I am following the below links:
I am running the below versions:
Cisco ASA - System image file is "disk0:/asa861-smp-k8.bin"
CUCM - System version: 8.6.2.22900-9
IP Phone 9971 - sip9971.9-2-4-19
I am licensesd for VPN Use and have followed the troubleshooting docs, but not success. I see in the console logs the below:
919: NOT 03:11:44.129712 SECD: Leaf cert hash = 346FBB4F186F1E303A23378DBF63B3FC5F9E7159
920: NOT 03:11:44.130473 SECD: Hash was found in the trust list
921: NOT 03:11:44.170207 VPNC: VPN cert chain trusted
922: DBG 03:11:44.171394 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
923: NOT 03:11:44.173132 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server certificate A
924: NOT 03:11:44.175588 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server certificate request A
925: NOT 03:11:44.176564 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server done A
926: NOT 03:11:44.179144 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write client certificate A
927: NOT 03:11:44.300654 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write client key exchange A
928: NOT 03:11:49.092573 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write certificate verify A
929: NOT 03:11:49.095174 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write change cipher spec A
930: NOT 03:11:49.097356 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write finished A
931: NOT 03:11:49.099446 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 flush data
932: DBG 03:11:49.106701 VPNU: State AppsUp --> AppsUp
933: DBG 03:11:49.107383 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
934: DBG 03:11:49.108002 VPNU: State AppsUp --> AppsUp
935: NOT 03:11:49.302508 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read finished A
936: NOT 03:11:49.303994 VPNC: create_ssl_connection: SSL setup done
937: NOT 03:11:49.304647 VPNC: do_login: sending (HTTPS) login request...
938: NOT 03:11:49.306559 VPNC: do_login: waiting for login response
939: NOT 03:11:49.308863 VPNC: do_login: got login response
940: NOT 03:11:49.309724 VPNC: process_login: HTTP/1.1 200 OK
941: NOT 03:11:49.310396 VPNC: process_login: login code: 200 (ok)
942: ERR 03:11:49.311099 VPNC: process_login: login failed, 'webvpn=' not found in cookie
943: ERR 03:11:49.311755 VPNC: do_login: process_login failure
944: WRN 03:11:49.313240 VPNC: ssl_state_cb: TLSv1: write: alert: warning:close notify
945: NOT 03:11:49.316531 VPNC: vpn_stop: de-activating vpn
process_login: login failed, 'webvpn=' not found in cookie
919: NOT 03:11:44.129712 SECD: Leaf cert hash = 346FBB4F186F1E303A23378DBF63B3FC5F9E7159
920: NOT 03:11:44.130473 SECD: Hash was found in the trust list
921: NOT 03:11:44.170207 VPNC: VPN cert chain trusted
922: DBG 03:11:44.171394 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
923: NOT 03:11:44.173132 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server certificate A
924: NOT 03:11:44.175588 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server certificate request A
925: NOT 03:11:44.176564 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read server done A
926: NOT 03:11:44.179144 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write client certificate A
927: NOT 03:11:44.300654 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write client key exchange A
928: NOT 03:11:49.092573 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write certificate verify A
929: NOT 03:11:49.095174 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write change cipher spec A
930: NOT 03:11:49.097356 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write finished A
931: NOT 03:11:49.099446 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 flush data
932: DBG 03:11:49.106701 VPNU: State AppsUp --> AppsUp
933: DBG 03:11:49.107383 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
934: DBG 03:11:49.108002 VPNU: State AppsUp --> AppsUp
935: NOT 03:11:49.302508 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read finished A
936: NOT 03:11:49.303994 VPNC: create_ssl_connection: SSL setup done
937: NOT 03:11:49.304647 VPNC: do_login: sending (HTTPS) login request...
938: NOT 03:11:49.306559 VPNC: do_login: waiting for login response
939: NOT 03:11:49.308863 VPNC: do_login: got login response
940: NOT 03:11:49.309724 VPNC: process_login: HTTP/1.1 200 OK
941: NOT 03:11:49.310396 VPNC: process_login: login code: 200 (ok)
942: ERR 03:11:49.311099 VPNC: process_login: login failed, 'webvpn=' not found in cookie
943: ERR 03:11:49.311755 VPNC: do_login: process_login failure
944: WRN 03:11:49.313240 VPNC: ssl_state_cb: TLSv1: write: alert: warning:close notify
945: NOT 03:11:49.316531 VPNC: vpn_stop: de-activating vpn
What does process_login: login failed, 'webvpn=' not found in cookie mean?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Have you checked this one page before?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thanks asp13, but my group-url and my vpn gateway url are identical.
both are https://<DNS ENTRY>
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
cjguinn,
This is normally the URLs don't match.
What is the URL you are using? Also can you provide the VPN section of the IP Phone configuration file and the "tunnel-group" configuration of the ASA
Are you using "Host Id Check" on the CUCM?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
URL's are identical for the group-url in the ASA and VPN Gateway in CUCM.
I am not using "Host ID Check"
Here is the sanitized version of the config. Something look wrong?
Global VPN Config
webvpn
enable OUTSIDE-INTERFACE
no anyconnect-essentials
csd image disk0:/csd_3.6.6203-k9.pkg
csd hostscan image disk0:/hostscan_3.1.02026-k9.pkg
csd enable
anyconnect image disk0:/anyconnect-win-3.1.02040-k9.pkg 2
anyconnect enable
tunnel-group-list enable
Connection Profile
tunnel-group VPN-PHONE type remote-access
tunnel-group VPN-PHONE general-attributes
address-pool VPN_POOL
authentication-server-group LDAP
default-group-policy VPN-PHONE
tunnel-group VPN-PHONE webvpn-attributes
authentication certificate
group-url https://xxx.xxx.com enable
Group Policy
group-policy VPN-PHONE internal
group-policy VPN-PHONE attributes
wins-server none
dns-server value 1.1.1.1
vpn-filter value VPN-PHONE
vpn-tunnel-protocol ssl-client ssl-clientless
default-domain value xxx.com
webvpn
url-list none
Dynamic Access Policy
dynamic-access-policy-record DAP-VPN-PHONE
network-acl VPN-PHONE
priority 238
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The IP Phones don't support CSD/Hostscan.
Please apply this command on the ASA and let us know how it goes:
tunnel-group VPN-PHONE webvpn-attributes
without-csd
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sorry I missed that line. It does have that in there for the WEB-VPN Attributes.
tunnel-group VPN-PHONE webvpn-attributes
authentication certificate
group-url
enable
without-csd
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I think it will be good idea to open a TAC case, this requires more troubleshooting.
Next step is to collect the "debug crypto ca 255" and "debug dap trace" from the ASA when you try to connect the Phone.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So what I had to do to resolve my problem is install the LSC and not use the MIC. We could tell by running the below debugs on the ASA that the phone was attemtpting to use the Manufacturer Installed Certificate.
debug crypto ca messages 255
debug crypto ca 255
debug aaa authentication
We could see the below in the debug:
CRYPTO_PKI: No suitable trustpoints found to validate certificate serial number: 549784970000001EDD4A, subject name: cn=CP-7965G-SEP00229059F06C,ou=EVVBU,o=Cisco Systems Inc., issuer name: cn=Cisco Manufacturing CA,o=Cisco Systems .
So we followed the below link
https://supportforums.cisco.com/docs/DOC-23851
Installed the LSC on the IP Phone
LCS is installed by CUCM locally and hence it is more secure.
+Enable CAPF (Cisco Certificate Authority Proxy Function) service on CUCM .
+Go to the phone page -- > CAPF -- > Install / Upgrade -- > (any option)
+Save and reset the phone.
+Check the phone if LSC is installed (Settings - - > Security)
+Download CAPF Cert from CUCM
OS Admin -- > Security --- > Certificate Managment --- > Find --- > click on CAPF.pem and download it.
+UploadCAPF certificate as CA certificates into ASA.
+ Configure AS tunnel group to authentication by certificate
+Connect phone and Outside and try to use VPN.
RESET the IP Phone internally and then put it on the outside and it worked.
Thanks for your replies.
CJ
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, the was able to connect to VPN but it failed to register. Route is ok and from IP Phone the CUCM is reachable.
The console logs tell me something conn timer expired...
9345: NOT 23:14:15.063163 VPNC: do_dtls_connect: create_dtls_connection
9346: NOT 23:14:15.064097 VPNC: create_dtls_connection: cipher list: AES128-SHA
9347: NOT 23:14:15.065002 VPNC: create_dtls_connection: calling SSL_connect in non-block mode
9348: NOT 23:14:15.067116 VPNC: dtls_state_cb: DTLS: SSL_connect: before/connect initialization
9349: NOT 23:14:15.068937 VPNC: dtls_state_cb: DTLS: SSL_connect: SSLv3 write client hello A
9350: NOT 23:14:15.661334 VPNC: dtls_state_cb: DTLS: SSL_connect: unknown state
9351: NOT 23:14:15.662486 VPNC: dtls_state_cb: DTLS: SSL_connect: SSLv3 write client hello A
9352: NOT 23:14:15.663601 VPNC: dtls_state_cb: DTLS: SSL_connect: SSLv3 flush data
9353: NOT 23:14:16.261076 VPNC: dtls_state_cb: DTLS: SSL_connect: SSLv3 read server hello A
9354: NOT 23:14:17.964424 JVM: Startup Module Loader|cip.sccp.CcApi: - cfgRetryTimer: will try to sync up the configuration..
9355: NOT 23:14:17.965986 JVM: Startup Module Loader|cip.sccp.CcApi: - startCfgRetryTimer: starting cfg retry timer(ms)=76515
9356: NOT 23:15:27.001242 SECD: clpAppSrvrRd: app srvr closed conn to <192.168.10.100> c:10 s:11
9357: NOT 23:15:27.002698 SECD: clpDelTlsSrvrProxyConn: closing conn to <192.168.10.100>, c:10, s:11
9358: ERR 23:15:27.020142 JVM: Calling enable listening for incoming http connections
9359: NOT 23:15:34.435106 JVM: Startup Module Loader|cip.sccp.CcApi: - cfgRetryTimer: will try to sync up the configuration..
9360: NOT 23:15:34.436670 JVM: Startup Module Loader|cip.sccp.CcApi: - startCfgRetryTimer: starting cfg retry timer(ms)=66204
9361: WRN 23:16:12.670117 VPNC: vpnc_control: conn timer expired, abort connect
9362: NOT 23:16:12.670770 VPNC: abort_connect: in dtls setup phase
9363: WRN 23:16:12.671330 VPNC: abort_connect: cancel_dtls_setup
9364: NOT 23:16:12.671846 VPNC: cancel_dtls_setup: marking for cancel
9365: NOT 23:16:12.860115 VPNC: create_dtls_connection: canceling handshake
9366: ERR 23:16:12.860778 VPNC: create_dtls_connection: DTLS setup failure, cleanup
9367: ERR 23:16:12.862251 VPNC: do_dtls_connect: create_dtls_connection failed
9368: ERR 23:16:12.863069 VPNC: protocol_handler: connect: do_dtls_connect failed
9369: WRN 23:16:12.863676 VPNC: protocol_handler: connect : err: SSL success DTLS fail
9370: NOT 23:16:12.864238 VPNC: tunnel_cleanup: cleanup SSL
9371: WRN 23:16:12.865690 VPNC: ssl_state_cb: TLSv1: write: alert: warning:close notify
9372: NOT 23:16:12.867353 VPNC: tunnel_cleanup: cleanup DTLS
9373: NOT 23:16:12.867998 VPNC: tunnel_cleanup: bringing down tun i/f
9374: NOT 23:16:12.868557 VPNC: disconnect: cleanup conn info
9375: NOT 23:16:12.869197 VPNC: vpnc_tun_disconnect: bringing down i/f -> tun0
9376: NOT 23:16:12.870345 VPNC: vpnc_delete_dns_conf: deleting /tmp/vpn_dns.conf
9377: NOT 23:16:12.871762 VPNC: reset_lease_info: values reset
9378: NOT 23:16:12.872407 VPNC: vpn_stop: de-activating vpn
9379: NOT 23:16:12.872969 VPNC: vpn_set_auto: auto -> auto
9380: NOT 23:16:12.873519 VPNC: vpn_set_active: activated -> de-activated
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
9369: WRN 23:16:12.863676 VPNC: protocol_handler: connect : err: SSL success DTLS fail
I think the answer is written in the trace line above. Phone VPN requires both a TLS and a DTLS session to function properly. Make sure that you have TCP and UDP connectivity on port 443 from the phone to the ASA, and that DTLS is enabled.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: