- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE BYOD Endpoint notes
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-28-2020 01:08 PM - edited 01-19-2021 09:11 AM
- Before Anything...
- Android devices
- General
- Android 11
- Android 10
- Android 9 and above
- Android 6 and above
- iOS devices
- General
- iOS14, iPadOS14
- iPadOS 13
- 12.2+
- 12.1
- macOS
- 10.12 (High Sierra)
- ChromeOS
- Version 76
This document is to provide any changes made to endpoint OS that impacts BYOD flow for end users. The videos shown are normal flows for different OS as a reference.
Before Anything...
Prior to troubleshooting endpoint issues, please follow these steps first:
- If you see support OS issues - Update OS finger printing DB on ISE: This is done by going to Administration > System > Settings, Posture > Updates, then click ‘Update Now’ button. It may take ~ 10 minutes to complete. Although this update is for posture, BYOD flow leverages the same update to identify browser user agent string to get OS information from the client. This menu is available to setup even if the deployment does not have any Apex license.
- For Android, make sure to download latest version of SPW app from the Google play store
- For Windows and macOS, make sure to download latest SPW from Cisco to ISE and update Client Provisioning Policy to reflect the newer version of SPW
Android devices
General
When using mini browser user may get an error when transitioning from mini browser to Play Store when trying to download the Cisco Network Setup Assistant App such as following:
There are two potential workaround, one as an end user and one as an ISE admin
As an end user
User can close the mini browser window and continue with full browser. If the Cisco Network Setup Assistance is already installed, then open Cisco Network Setup Assistance App on step #3 instead of Chrome browser
- Select three dots on the top right-hand corner of the mini browser window
- Select Use this network as is
- Go to home screen and open full Chrome browser
- Refresh the page or enter arbitrary IP such as 192.0.2.123 in the URL bar to force redirect to BYOD page
- Continue with the BYOD flow
Note: On certain model of phones, the Android device may switch to cellular network even when Use this network as is option is selected. User may need to disable cellular connection to force Android device to continue with the BYOD flow
As an ISE admin
The mini browser automatic popup can be suppressed by allowing following FQDN in the URL exception list in the redirected ACL on the WLC. Since mini browser does not popup, users are forced to open the full browser to continue with the BYOD process. However, if the same portal is used for the guest users, guest users will also be forced to open full browser to get Internet access.
- Login to the Cisco WLC
- Select SECURITY > Access Control Lists > Access Control Lists
- Select the down arrow next to the redirect ACL used by ISE BYOD flow
- Select Add-Remove URL
- In the URL String Name enter following and select Add
- connectivitycheck.gstatic.com
- Select Back
Note: There may be additional URL used for captive portal detection based on the phone vendor or version of Android that needs to be added in addition to the ones noted above.
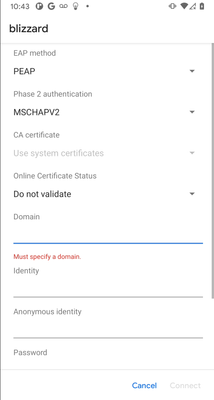
Android 11
Android 11 December 2020 update changed way the certificate trust works for EAP purpose. Once updated, when connecting to a 802.1X secured WLAN for the first time, the Android device will require the RADIUS server EAP certificate to be trusted via installed CA. This means that if the RADIUS server is using a self-signed EAP certificate, the Android 11 device will not trust it. On top of that, when connecting, the user has to specify the domain name that matches the CN and/or SAN of the EAP certificate. Here are few options to address the issue:
- Use EAP certificate that is signed by well known public CA
- Install private root CA certificate that signed ISE EAP certificate on Android 11 devices prior to initial connection to the 802.1X SSID
- Use dual-SSID BYOD flow
Android 10
Android 10 requires network user password 3 times during the BYOD flow. Once for Association or WebAuth, second for EST, third to access private key.
Please make sure to use SPW version 2.2.0.66 which supports Android 10
Android 10 generates random MAC address every time a new connection profile is created. This results in few problems to the ISE BYOD flow
- Dual SSID: You can no longer use MAC in SAN condition or the BYOD registered condition as the MAC address changes between the first connection during Open SSID and 802.1X SSID. Also, the burned-in MAC address is not visible within the My Devices Portal. Please make sure to remove "BYOD_is_Registered" and "MAC_in_SAN" condition from Employee_EAP-TLS flow highlighted below:
- Single SSID: Even if the random MAC is enabled then SPW will capture the random MAC and use it as identity. If user disables random MAC on the SSID at later time, the user will may not be able to connect due to the same reason as the Dual SSID flow. If you want to allow such use case, disable the two conditions show above.
- If you want to deny random MAC or provide differentiated access for random MAC, please review Random MAC Address - How to deal with it using ISE
Android 9 and above
If BYOD profile includes web proxy settings, SPW requires user to establish Android work profile if not already present on the endpointWith single-SSID flow, user has to delete the SSID setting (That was used to connect with PEAP-MSCHAPv2) for EAP-TLS will function. User will be guided via overlay instructions
Android 6 and above
Uses EST instead of SCEP between the endpoint and ISE. Requires additional policies on ISE and also change to redirect ACL to allow EST server access from endpoint. Due to this change end users are required to enter network credential for EST authentication in addition to regular WebAuth/802.1X authentication
iOS devices
General
When non well known certificate is used for BYOD portal, iOS device requires the root CA certificate to be trusted prior to accepting rest of the profile
Dual SSID
- After onboarding from open SSID, user needs to manually go to WiFi settings on the iOS device and connect to secured SSID
iOS14, iPadOS14
iOS14 generates random MAC address every time a new connection profile is created. This results in few problems to the ISE BYOD flow
- Dual SSID: You can no longer use MAC in SAN condition or the BYOD registered condition as the MAC address changes between the first connection during Open SSID and 802.1X SSID. Also, the burned-in MAC address is not visible within the My Devices Portal. Please make sure to remove "BYOD_is_Registered" and "MAC_in_SAN" condition from Employee_EAP-TLS flow as shown for Android 10 devices
- Single SSID: Even if the random MAC is enabled then SPW will capture the random MAC and use it as identity. If user disables random MAC on the SSID at later time, the user will may not be able to connect due to the same reason as the Dual SSID flow. If you want to allow such use case, disable the two conditions show above.
- If you want to deny random MAC or provide differentiated access for random MAC, please review Random MAC Address - How to deal with it using ISE
iPadOS 13
iPadOS defaults to desktop mode on the Safari browser which sends wrong user-agent string to be sent and causes iPads profiled as macOS. To fix ipadOS issue for BYOD, now ISE provides a way to choose your own OS on the BYOD page.
12.2+
Now iOS device requires user to manually go to profile settings whereas before user was able to open profiles within the browserProfile popup for root CA certificate and SCEP/WiFi profile popup happens back to back without user acknowledging
In a single-SSID flow, the iOS device is still connected with PEAP instead of EAP-TLS after CoA. User has to disable Wireless and re-enable it to connect with EAP-TLS
12.1
Now iOS device requires user to trust the root CA if not part of trusted CA store. This can be done by going to 'About' settings and scroll down to trust imported root CA certificate
macOS
10.12 (High Sierra)
When CNA BYOD (mini browser) flow is used, and when user clicks on the hyperlink in the CNA browser, instead of opening up full browser, it opens up within the CNA browser which breaks the BYOD flow.
ChromeOS
If you are planning to provision certificate for both wireless and wired interface, be sure to create separate certificate template that can be differentiated using certification pattern matching with Google Admin Console.
Version 76
BYOD flow is successful, but endpoint cannot connect to the network provisioned by NSP
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For Single SSID Apple iOS 12.2+ do we still have to open safari browser
Do we still face issues with Mini Browsers?
I was in perception that this issue has been fixed in 2.6
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please refer to following flow:
This is only supported on Dual-SSID flow, in the case of Single-SSID flow, it is best to suppress mini browser using captive portal by pass feature on the WLC.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
I hope the dual SSID solution would be applicable to ISE 3.0 version as well..
Pls suggest..
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: