- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Loadbalancing DUAL ISP on ASA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-09-2011 08:48 AM - edited 03-08-2019 06:39 PM
Objective
To configure the ASA to send traffic through both ISPs simultaneously.
Problem Description
Usually when a user has two ISPs terminating on the ASA, the ASA is configured for ISP redundancy. However in some cases, the user would like to use both ISPs simutlaneously to send traffic.
Scenario
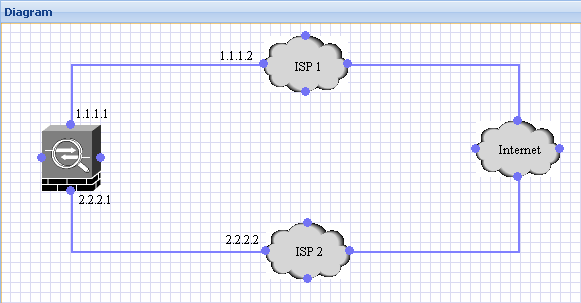
Solution
In such a scenario, the best solution would be to use a router. Using route-maps on the router, one can configure the routing in such a way that only certain kind of traffic uses one ISP while the second ISP is used for other kinds of traffic. Although the ASA supports route-maps, because it wasn't designed to support extensive routing capabilities, there are quite a few features under route-maps like source-based routing, which are not supported by the ASA. If using a router is an option then the network would have to be redesigned as follows:

If however, this is not an option, then it is possible to configure a very crude form of "loadbalancing" on the ASA. The following two scenarios are ways in which both ISPs can be used simultaneously on the ASA:
1. Route traffic based on destination:
As I mentioned aboved, the ASA is not a load-balancer or a packet-shaper. However with the following commands on the ASA, we can route traffic to half the destinations on the internet using ISP1 and the other half using ISP2:
nat (inside) 1 0 0
global (ISP1) 1 interface
global (ISP2) 1 interface
route ISP1 128.0.0.0 128.0.0.0 1.1.1.2 // creates a default route for addresses in the first half of the IPv4 spectrum
route ISP2 0.0.0.0 128.0.0.0 2.2.2.2 // creates a default route for addresses in the second half of the IPv4 sepctrum
2. Route traffic based on destination ports:
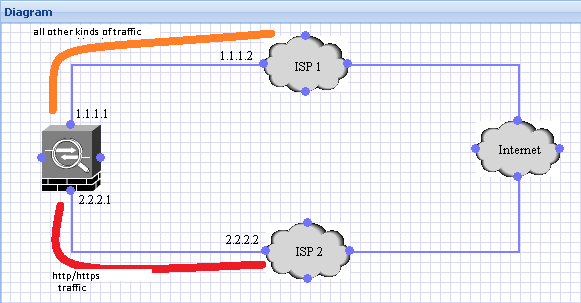
By adding the configuration below, the ASA can be set up to send web traffic(http,https) out through ISP2 and all other traffic is sent through ISP1 as shown above.
route ISP1 0 0 1.1.1.2 // Default route pointing to ISP1
route ISP2 0 0 2.2.2.2 2 // Default route with Metric 2 via ISP2
static (ISP2,inside) tcp 0.0.0.0 80 0.0.0.0 80
static (ISP2,inside) tcp 0.0.0.0 443 0.0.0.0 443
sysopt noproxyarp inside // important, otherwise it will cause routing issues as the ASA will start sending proxy-arps for all hosts on the inside.
nat (inside) 1 0 0
global (ISP1) 1 interface
global (ISP2) 1 interface
Important Note: As I mentioned earlier the ASA is not designed to support load-balancing the above solutions are only workarounds and as such not supported configuration.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Awesome! I love it!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is failover still possible with the second example? In the example, is my web traffic(port 80/443) down if isp2 goes down, or can i still use an SLA monitor or some other method to automatically failover web traffic to isp1 that is still up? Im looking for a way to both send specific destination ports out a particular ISP, but also fail them over should it go down. Asa 5520. Any assistance is appreciated.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
If you're using ASA code above 8.3 the natting becomes very different, and the above set up may no longer work. If the code is below 8.3 then it maybe possible using SLA monitoring, but I haven't tested it and can't be sure how the natting will be affected.Ideally is ISP2 goes down and SLA monitoring removes the second route, then the static NATs shuold also not function properly, so the nat global should work just fine.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi to all.
My goal is to use dual wan (with 2 different ISP):
I would use:
wan1 for all: web, mail, ecc
wan2 only for a vpn l2l connection with HQ.
obviously the wan have to work at the same time.
It's possible with asa 5505? (without a router).
Do yuo know some tutorial for that?
Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
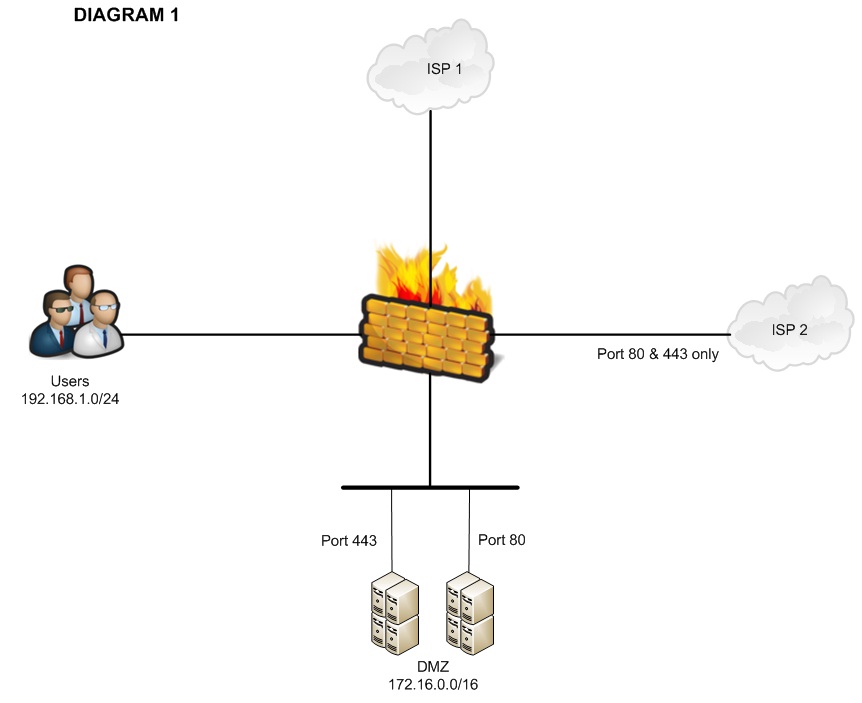
Hello,
Thank you for posting this. It works fine as what the objective is.
BUT I have some problem, USERS cannot access anymore the servers in DMZ using port 80 & 443. Could it be the static NAT? Or do I need to add a new ACL for ISP 2?
I appreciate any feedback. Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Configuring my ASA 5510 according the 2nd scenario works very well. My issue is that my remote users connecting using VPN cannot access the resources on the LAN. I think this is because of "noproxyarp" but is there a way to give access to all resources on the LAN?
Thanks,
Thierry
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
without any doubt , front ending a router is the best solution. However, following is my opinion
1. Route traffic based on destination:
possible caveat:
while this option gives flexibility to load share the outbound traffic initiated behind the ASA, however this option will potentially create trouble for inbound traffic destined for NAT behind either ISP1/2.
Example: if a client on the internet with source 50.67.1.1 trying to access 2.2.2.2 (ISP2 IP) Static NAT for web server, this traffic enters through ISP2 and tries to exit through ISP1 (because of the broad IPv4 spectrum static routes on ASA)
This scenario is also known as asymmetric routing and it also defeats the purpose of ASA stateful inspection.
Note1: Because of its default nature, ICMP will work in this scenario .
Note2:Also ASA is not capable of policy based routing(PBR)
Note3: Outbound traffic in this scenario can also cause problems if ISP1 goes down. The static route towards ISP1 is not going to be removed from route table unless we attach a IP SLA track. However even with the SLA track it is still going to be an issue because it only remove the route from route table but not replace that with 0/0 towards ISP2.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: