- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Maximise usage of Cisco Secure Endpoint through connector deployment
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-08-2022 09:10 PM - edited 06-16-2022 07:45 AM
This article explains recommended step-by-step Cisco deployment strategies in four phases to best optimise the deployment of Cisco Secure Endpoint.
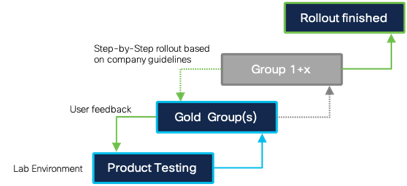
After base features have been enabled, we move on to the deployment stage where we rollout the software. As with any large-scale software deployment, it is always a good practice to deploy in a slow, methodical way. Staged deployments ensure that as we deploy to any environment, if we encounter issues, we are able to resolve them while only impacting a relatively small percentage of endpoints.
Cisco recognises that each customer environment is unique, therefore, the following framework should serve as a recommendation as it may need to be adjusted accordingly to each customer’s use case.
Here's a video that explains the stages involved in the deployment. The goal is that you're able to deploy close to 50% of the licensed endpoint connectors by the end of the video and this blog post.
Phase 1: LAB Environment – Testing and Rollout |
|
|
Step 1 Download the Connector from Secure Endpoint console. |
Best Practice: Set the defined connector version for your environment in the AMP console under Accounts → Organization Settings, so everyone is installing the same version. Otherwise generate a download URL under Management → Download Connector for any admin which has no access rights to AMP console. |
|
Step 2 Install the Connector to the machines in your LAB. Start with your standard company image, so you are getting a test result for a high amount of company endpoints. If possible, try to install as much as possible software components. |
Best Practices: Always test with your existing Deployment Architecture (e.g., Microsoft SCCM, Altiris and others). The Deployment Architecture already provides many Software Packages for testing. During Software Installation and upgrades, there are many files changed on your system by the installer, which will be scanned by Secure Endpoint. Monitor the System Performance during the Software Installation and Upgrade Process. Review the Windows Installer Exit Codes if there is any issue when installing Secure Endpoint. Software Deployment Agents should be excluded from scanning by process. In secure areas also add the SHA-256 hash to the exclusion. |
Phase 2: Gold user Group |
|
|
Step 3 Define the Gold User Group to test with business-critical applications. There can be situations, where specific application features are generating new files on the disk. Application testing cannot be done by IT.
|
Best Practices
|
Phase 3: Deployment Preparation |
|
|
Step 4: Generate the deployment packages for the Deployment. |
Cisco recommends using an existing Deployment Architecture e.g., Microsoft SCCM, Altiris, or others.
Best Practice: Review available installer command line switches for the Secure Endpoint connector: http://cs.co/AMP4E_Connector_Install_Switches. |
Phase 4: Rollout |
|
|
Step 5: Start the rollout in your Environment based on your internal guidelines, policies and the defined Step-by-Step rollout. Add new exclusions as needed during the Rollout Phase. |
For business-critical systems, you may start in Audit mode when deploying Secure Endpoint to observe impact. Best Practice: There can always be an issue when installing new software to endpoints, regardless of if you are installing Secure Endpoint or any other software package. In a Worst-Case-Scenario a stepwise rollout helps you to lower the impact on your infrastructure. |
Phase 2 and 4 will include iterative testing and feedback so be comfortable in going back and implementing those changes for a successful outcome roll out for both gold and general user groups.
For an in-depth guide, refer to Secure Endpoint Best Practices Guide.
If you want to join a live Q&A session, register for the following Ask the Experts Session:
- Installation / Implementation Best Practices: Endpoint Protection
Review Schedule and Register
Comment on this post if you have any questions
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: