Cisco Secure Endpoint offers several protection engines which fight against threats like ransomware and zero-day.
Are you an admin looking for protection on a short to mid-term basis or beginning to roll out protection across your organisation? The best place to start is protecting your devices from attacks that are exploiting vulnerabilities of user applications and operating system, commonly known as file-less malware.
File-less malware threats are becoming more common as attackers have learned that traditional file-based malware can be easily detected. Ponemon Institute's 2017 State of Endpoint Security report said that about 77% of malware was file-less and they tend to be 10 times more successful than traditional file-based attacks.
Below are two protection engines you can use to help address these problems and protect your organization:
| Malicious Activity Protection (MAP) |
Enables on-disk run-time detection and blocking of abnormal behaviour on the endpoint by constantly checking for certain changes on the protected system to identify the processes that will be deemed as malicious if they demonstrate a certain set of behaviours or activities laid out in the ruleset.
· Example: If the process reads, writes, and renames a set of files within a short span of time, then the rule can trigger to act on that process. However, the admin can choose that if the process reads and writes the content of a file to a different file and then deletes the original files, then the MAP engine can trigger to take a different action defined in the policy. Legitimate user applications demonstrate this behaviour such as archiving software so process exclusions (and optionally child process) to prevent Cisco Secure Endpoint from monitoring them.
· Common ransomware which MAP can prevent are: SamSam, WannaCry, Jigsaw, Jaffe, Cerber, TeslaCrypt etc.
· MAP also works offline so even when it is not connected to the internet, the connector will detect and respond to such threats.
|
Here's a video walk through that shows how to enable MAP for your connectors:
| Exploit Prevention |
Defend your endpoints from memory injections attacks also commonly known as file-less attacks.
· File-less attacks harness existing vulnerabilities lying in operating systems or apps. In an ideal case, you should be patching and updating these regularly but unfortunately, users typically tend to forgo these updates.
· Examples of such attacks include Java exploits that use shellcode to run payload, malicious Adobe or MS Office files or any attacks on software vulnerabilities that have not been patched yet.
|
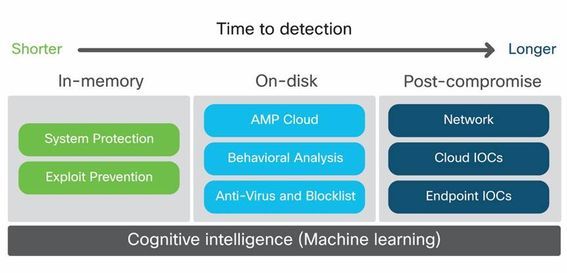
Here’s where Malicious Activity Prevention and Exploit Prevention fall in the protection spectrum:
If you want to dig deeper, you can join a live Q&A session at the following Ask the Experts Sessions:
- Installation / Implementation Best Practices: Endpoint Protection
- Architecture Transformation Planning: Endpoint Protection
Comment on this post if you have any questions
