- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Notes on Okta as SAML IdP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 08-19-2016 03:32 PM
MyDevices
- [Okta admin] We create one application in Okta for each of the ISE user portals for SSO.
- To create an application for ISE MyDevices, follow the instructions @ Setting up a SAML application in Okta
- Download the resulting meta data file and save it with the extension .xml
- [ISE admin] Create a new identity provider (IdP) for Okta MyDevices app
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Click [ Add ]
- General > Id Provider Name: [Give a name to id it] (e.g. IdP_oktaMyDevices)
- Identity Provider Config: Click on [ Browse... ] next to import Identity Provider Config File. Select the meta data file from Okta
- Click [ Submit ]
- [ISE admin] Create a new MyDevices Portal to use the new IdP
- Navigate to Administration -> Device Portal Management -> My Devices
- Click [ Create ]
- Portal Settings and Customization -> Portal Name: [Give a name for this new portal]
- Portal Behavior and Flow Settings - Portal & Page Settings -> Portal Settings (Expand)
- Fully qualified domain name (FQDN): [fill in this with a DNS FQDN, which is usually a CNAME to one of the ISE PSN]
- Authentication method (drop-down): Select the IdP name from the previous step.
- Click [ Save ]
- [ISE admin] Obtain Service Provider Info for the MyDevices
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Select the previous added IdP and drill-in the hyperlink or click on [ Edit ]
- Tab [ Service Provider Info. ] and click on [ Export ] next to Export Service Provider Info.
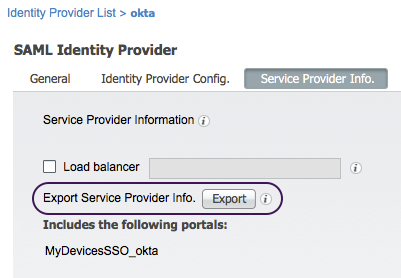
- Save the resulting zip file to the local file system. This zip file contains XML files for each portal configured to authenticate with this IdP instance.
- Unzip the zip file and open the XML file with the MyDevices portal name. Below is an example:
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID
="http://CiscoISE/f8eddd30-d418-11e5-8b92-00505693df29">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data><ds:X509Certificate>MIIDNDCCAhygAwIBAgIQVsIelAAAAAD1mMuiboHY2jANBgkqhkiG9w0BAQsFADAeMRwwGgYDVQQD...</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor>
<md:SingleLogoutService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="
https://mydevices.demo.local:8443/mydevicesportal/SSOLogoutRequest.action?portal=f8eddd30-d418-11e5-8b92-00505693df29" ResponseLocation="
https://mydevices.demo.local:8443/mydevicesportal/SSOLogoutResponse.action"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:AssertionConsumerService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://mydevices.demo.local:8443/mydevicesportal/SSOLoginResponse.action"
index="0"/><md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.1.100.21:8443/mydevicesportal/SSOLoginResponse.action"
index="1"/><md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise.demo.local:8443/mydevicesportal/SSOLoginResponse.action"
index="2"/>
</md:SPSSODescriptor></md:EntityDescriptor>
The main info we needing are the values associated with:
- entityID -- e.g. (from the above sample XML) http://CiscoISE/f8eddd30-d418-11e5-8b92-00505693df29
- SingleLogoutService -- e.g. (from the above sample XML) https://mydevices.demo.local:8443/mydevicesportal/SSOLogoutResponse.action
- AssertionConsumerService -- e.g. (from the above sample XML) https://mydevices.demo.local:8443/mydevicesportal/SSOLoginResponse.action
- [ISE admin] Obtain SAML certificate
- Navigate to Administration -> System-> Certificates -> System Certificates
- Select the certificate designated to be used by SAML. By default, it is the [Default self-signed saml server certificate - CN=SAML_ise.demo.local]
- Click [ Export ]
- Export Certificate Only and click [ Export ]. Then, save the resulting file to the local file system and, if needed, rename it so that it's easier to identify it later.
- [Okta admin] Update the application settings
- Back to the application created for ISE MyDevices
- Tab to [ General ]
- SAML Settings and click [ Edit ]
- General Settings, tick for both App visibility options and then click [ Next ]
- SAML Settings
- GENERAL
- Single sign on URL: Update this with the Location URL for AssertionConsumerService Binding of the MyDevices XML from the above.
- Audience URI (SP Entity ID): Update this to the value for the entityID of the MyDevices XML.
- Click on [ Show Advanced Settings ]
- Enable Single Logout: tick the checkbox next to it
- Single Logout URL: Update this with the Location URL for SingleLogoutService ResponseLocation of the MyDevices XML
- SP Issuer: Copy the value from Audience URI (SP Entity ID).
- Signature Certificate: Click [ Browse... ] and locate the ISE SAML certificate that we exported from ISE previously. Then, click on [ Upload Certificate ]
- Scroll down and click on [ Next ]
- Click on [ Finish ]
- GENERAL
- Ensure the application is assigned to the test user directly or to one of the groups it belongs to.
- [ISE admin] Update IdP for Logout Settings
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Select the previous added IdP for Okta MyDevices app and drill-in the hyperlink or click on [ Edit ]
- Tab to [ Advanced Settings ]
- Logout Settings: Tick [ Sign Logout request ]
- Click [ Save ].
- Test MyDevices SSO
- Option 1 -- Use "Portal test URL" in the MyDevices portal configuration page in [ISE admin]
- Navigate to Administration -> Device Portal Management -> My Devices
- Click on the hyperlink of the MyDevices portal previously created with SSO
- Click on [ Portal test URL ] hyperlink, which will usually open a new browser tab.
- Option 2 -- Use the portal FQDN
- Option 1 -- Use "Portal test URL" in the MyDevices portal configuration page in [ISE admin]
Sponsor
- [Okta admin] Create a new application for the sponsor portal the same way as the MyDevices.
- [ISE admin] Create a new identity provider (IdP) for Okta's ISE Sponsor app.
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Click [ Add ]
- General > Id Provider Name: [Give a name to id it] (e.g. IdP_oktaSponsor)
- Identity Provider Config: Click on [ Browse... ] next to import Identity Provider Config File. Select the meta data file from Okta
- Click [ Submit ]
- [ISE admin] Create a new Sponsor Portal to use the SAML IdP
- Navigate to Work Centers -> Guest Access -> Configure -> Sponsor Portals
- Click [ Create ]
- Portal Settings and Customization -> Portal Name: [Give a name for this new portal]
- Portal Behavior and Flow Settings - Portal & Page Settings -> Portal Settings (Expand)
- Fully qualified domain name (FQDN): [fill in this with a DNS FQDN, which is usually a CNAME to one of the ISE PSN]
- Authentication method (drop-down): Select the IdP name.
- Click [ Save ]
- [ISE admin] Obtain Service Provider Info for the Sponsor
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Select the previous added IdP and drill-in the hyperlink or click on [ Edit ]
- Tab [ Service Provider Info. ] and click on [ Export ] next to Export Service Provider Info.
- Save the resulting zip file to the local file system. This zip file contains XML files for each portal configured to authenticate with this IdP instance.
- Unzip the zip file and open the XML file with the sponsor portal name. Similar to MyDevices, the main info we needing are the values associated with:
- entityID
- SingleLogoutService
- AssertionConsumerService
- [Okta admin] Update the application settings
- Back to the application created for ISE Sponsor
- Tab to [ General ]
- SAML Settings and click [ Edit ]
- General Settings, tick for both App visibility options and then click [ Next ]
- SAML Settings
- GENERAL
- Single sign on URL: Update this with the Location URL for AssertionConsumerService Binding of the Sponsor XML from the above.
- Audience URI (SP Entity ID): Update this to the value for the entityID of the Sponsor XML.
- Click on [ Show Advanced Settings ]
- Enable Single Logout: tick the checkbox next to it
- Single Logout URL: Update this with the Location URL for SingleLogoutService Binding of the Sponsor XML
- SP Issuer: Copy the value from Audience URI (SP Entity ID).
- Signature Certificate: Click [ Browse... ] and locate the ISE SAML certificate that we exported from ISE previously. Then, click on [ Upload Certificate ]
- GROUP ATTRIBUTE STATMENTS (OPTIONAL)
Name | Name format (optional) | Filter | |
groups | Unspecified | Regex | .* |
Note: The attribute name "groups" is what we choose here but it can be any non-reserved attribute names but meaningful.
- Scroll down and click on [ Next ]
- Click on [ Finish ]
- Ensure the application is assigned to the test user directly or to one of the groups it belongs to.
- [ISE admin] Update IdP for Groups, Attributes, and Logout Settings
- Navigate to Administration -> Identity Management -> External Identity Sources -> SAML Id Providers
- Select the IdP for Okta Sponsor App and drill-in the hyperlink or click on [ Edit ]
- Tab to [ Groups ]
- Group Membership Attribute: Use the attribute name configured in Okta group attribute statements; i.e. "groups" in our example.
- Add each group from Okta and the name in ISE can be the same or simpler one.
- Tab to [ Attributes ]
- Add all the attributes -- FirstName, LastName, and Email -- configured in Okta
- Tab to [ Advanced Settings ]
- Email attribute (drop-down): Email
- Logout Settings: Tick [ Sign Logout request ]
- Click [ Save ].
- [ISE admin] Update Sponsor Group membership
- Navigate to Work Centers -> Guest Access -> Configure -> Sponsor Groups
- Click on one of the existing sponsor groups (e.g. ALL_ACCOUNTS (default))
- Click on [ Members... ]
- Use [ > ] and [ < ] to move between [ Available User Groups ] and [ Selected User Groups ]
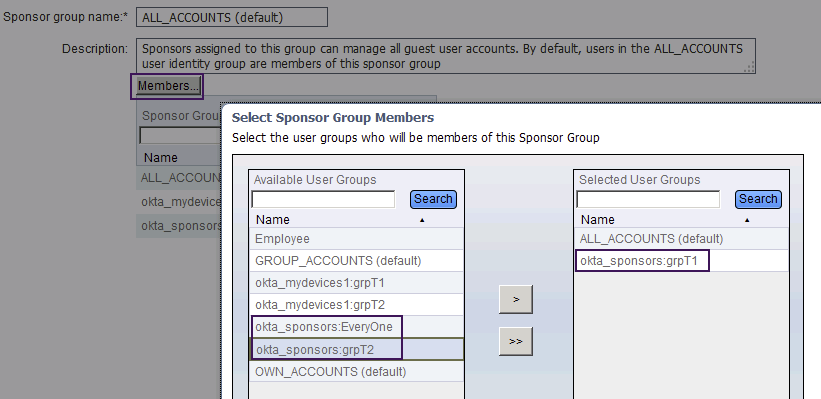
- Click [ OK ]
- Click [ Save ]
- Test Sponsor SSO
- Option 1 -- Use "Portal test URL" in the sponsor portal configuration page in [ISE admin]
- Navigate to Work Centers -> Guest Access -> Configure -> Sponsor Portals
- Click on the hyperlink of the sponsor portal previously created with SSO
- Click on [ Portal test URL ] hyperlink, which will usually open a new browser tab.
- Option 2 -- Use the portal FQDN
- Option 1 -- Use "Portal test URL" in the sponsor portal configuration page in [ISE admin]
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent instructions, thank you very much for posting!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent document. Do you have any document for the BYOD/Guest portal with OKTA ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
ISE BYOD and Guest portals would follow the similar steps in designating the IdP as the authentication method and exporting the XML files to obtain the values for the entityID and AssertionConsumerService. No SingleLogoutService, since they do not support logout. The group attribute, if configured, then can be used as an authorization condition.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can these instructions be used to integrate OKTA and ISE for Device Administration?
I am working on using MFA for device administration for when we access our network devices.
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No, the notes here are specific to Okta as a SAML Identity Provider and ISE end-user facing portals as Service Provider.
For device administration, Okta may serve as a RADIUS Token Identity Source for ISE. The flow is similar to
Okta RADIUS Server Agent Deployment Best Practices with ISE replacing ASA but I have no personal experience with it.
.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great document!
Do you have anything to suggest for Okta and ACS server for authenticating WLC admin access? A 2-factor authentication.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Roberto.Carmona please open a tac case
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



