- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Smart Call Home on the ASA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-01-2010 11:55 AM - edited 03-08-2019 06:36 PM
- What is Smart Call Home?
- What Benefits Does Smart Call Home Provide?
- What Types of Information are Sent from the ASA to Cisco?
- Alert Groups
- How is the Information Transmitted?
- Enabling Smart Call Home on the ASA
- Configuring a DNS Server on the ASA
- Installing and Trusting the CA Certificate
- Configuring the call-home Feature on the ASA
- Example Configuration
- Troubleshooting
- Example
- Success
- No DNS Server Configured
What is Smart Call Home?
Smart Call Home is really a two piece solution. The first of which is the call-home feature on the ASA which is both a time-based and event-based feature which can send information to Cisco and/or yourself. The second is a web portal, where you can view your Smart Call Home registered devices, and see information about their current status.
What Benefits Does Smart Call Home Provide?
Smart Call Home provides several benefits to customers. The most well known is the ability for TAC cases to be automatically opened when a fault is detected. Some examples of this are if a fan fails, or a redundant power supply, or if the temperature of the cpu/power supply/chassis reaches a critical level. In addition, if the ASA crashes, it will also open a TAC case. Since the Cisco TAC is 24x7 they instantly start to work on the problem. Most of the time when TAC reaches out to the customer - it is before the customer is aware of the problem.
How would you like to receive a phone call from TAC letting you know they received a fan failure on a device and they are just letting you know the replacment is being shipped and on its way? Or, that your ASA crashed, and they have identified the software defect, and you may apply a workaround, or upgrade to version X to receive the fix? This proactively reaching out to you - the customer - is a key benefit of Smart Call Home.
Users of Smart Call Home can also log in to the SCH portal to view their current registered devices and their status. The portal will display information about which ASA is Active (in a failover set), and also if you have a time-based license, it will show how much time is remaining before expiration. If you have multiple ASA devices, you can quickly scan through the list to see if they are all running the same version. You can also see if any PSIRT Advisories apply to them.
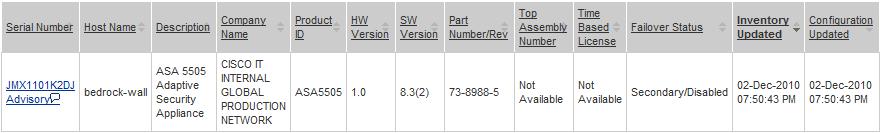
What Types of Information are Sent from the ASA to Cisco?
If you follow the instructions in this document, and acitvate the default CiscoTAC-1 profile, then the following information will be sent in to Cisco:
Diagnostic
If the ASA crashes, it will send in the sanitized output of show crash and show tech-support
Environment
If an environmental alarm is triggered, the ASA will send in the output of show environment. If a high memory or CPU condition is detected, the ASA will send in the output of show memory detail or show cpu usage.
Inventory
By default, every month the output of show inventory, show version, show module, show failover state, and show environment is sent in as part of an Inventory message.
Configuration
By default, every month the output of show call-home registered-module status | include enabled is sent in. Which includes a list of features enabled on the ASA.
Example
ASA# show call-home registered-module status | include enabled
call-home enabled
inspection-dns enabled
inspection-esmtp enabled
inspection-ftp enabled
inspection-hs232 enabled
inspection-netbios enabled
inspection-rsh enabled
inspection-rtsp enabled
inspection-sip enabled
inspection-skinny enabled
. . .
If you want to send in your sanitized configuration for archival purposes, in the CiscoTAC-1 profile, you need to change the default command from
subscribe-to-alert-group configuration periodic monthly
to:
Notice that the export full option was added. Without this, only the list of features is sent in.
Telemetry
By default, the following telemetry information is sent in daily:
show perfmon detail
show traffic
show conn count
show vpn-sessiondb summary
show vpn load-balancing
show local-host
show memory
show access-list | include elements
show interface
show phone-proxy media-sessions count
show phone-proxy secure-phones count
show threat-detection statistics protocol
show xlate count
show perfmon detail
show route
This can be modified by changing the following command:
subscribe-to-alert-group telemetry periodic daily
Alert Groups
All information which can be transmitted to Cisco via Smart Call Home is configured through Alert Groups. Above, we looked at the default information which is sent in based on the default configuration of alert groups. You may customize the default alert group configuration to send in the information at a different frequency, or to disable or enable alert groups. Additionally, some alert groups allow you to indicate what type and how much data is sent in.
The following alert groups can be configured on the ASA.
configuration Configuration Group
diagnostic Diagnostic Group
environment Environmental Group
inventory Inventory Group
snapshot Snapshot Group
syslog System Log Group
telemetry Telemetry Group
threat Threat Group
Alert Group
FrequencyAmount of Data
| configuration | Configurable periodicity: daily, monthly, weekly | full: sends a sanatized version of the full config minimum: only sends the list of features enabled |
| diagnostic | Automatically triggered based on event | Configurable severity: alert, catastrophic, critical, debugging, disaster, emergencies, erors, informational, notifications, warnings. Default is informational |
| environment | Automatically triggered based on event | Configurable severity: alert, catastrophic, critical, debugging, disaster, emergencies, erors, informational, notifications, warnings. Default is informational The following data is sent: show environment |
| inventory | Configurable periodicity: daily, monthly, weekly | The following data is sent: show inventory, show version, show module, show failover state, and show environment |
| threat | Automatically triggered based on even | For Shun, the following data is sent: show threat-detection rate, show threat-detection scanning-threat, show threat-detection statistics, show shunFor dynamic-filter drops, the following data is sent:show dynamic-filter statistics , show dynamic-filter reports top |
| syslog | Automatically triggered based on event | This will send the syslog message. |
| telemetry | Configurable periodicity: daily, monthly, weekly | This will send the following data: show perfmon detail, show traffic, show conn count, show vpn-sessiondb summary, show vpn load-balancing, show local-host, show memory, show access-list | include elements, show interface, show phone-proxy media-sessions count, show phone-proxy secure-phones count, show threat-detection statistics protocol, show xlate count, show perfmon detail, show route |
| snapshot | Configurable periodicity: daily, hourly, interval, monthly, weekl | This will send the output of any command the user has requested in the snapshot |
How is the Information Transmitted?
The ASA can communicate Cisco's Smart Call Home servers via either HTTPS, or SMTP. Ideally, customers should use HTTPS to securely transfer any data from the ASA to Cisco. This document will focus exclusively on configuring the ASA for HTTPS transport.
Also note that a Transport Gateway option is available, which allows SCH capable devices (like the ASA) to send data via HTTP to a customer premise Transport Gateway application. The Transport Gateway then forwards the data on to Cisco via HTTPS. This allows for all SCH data to be aggredated to a central customer premise device, and only have that device communicate to Cisco. For more information on the Transport Gateway, please see the Transport Gateway Q&A. You may also download the Transport Gateway directly from here.
Enabling Smart Call Home on the ASA
Configuring the ASA for Call Home is pretty simple, but it contains three parts:
- Configuring a DNS Server on the ASA
- Installing and trusting the CA certificate
- Configuring the call-home feature on the ASA
Configuring a DNS Server on the ASA
In order for the ASA to contact Cisco's Smart Call Home server via HTTPS, it must be able to resolve the web site: https://tools.cisco.com Therefore, a DNS server must be configured on the ASA for it to resolve the name to an IP address. Follow the steps below to configure a DNS server on the ASA.
- Enable the ASA to perform DNS lookups by adding the dns domain-lookup <interface> command.
- Specify the DNS server for the ASA to use when performing name lookups using the dns name-server <ip> command.
Example
ciscoasa(config)# dns domain-lookup Outside
ciscoasa(config)# dns name-server 203.0.113.43
Installing and Trusting the CA Certificate
Since the ASA will be contacting the Cisco Call Home server over Secure HTTP (HTTPS), the ASA must be able to validate and trust the certificate presented by the Call Home server. In order for this to occur, you must install the CA certificate on the ASA, which signed the certificate that was issued to the Call Home server. Please follow the steps below to accomplish this task.
For simplicity, you can just copy and paste in all of the below from enable or config mode:
configure terminal
crypto ca trustpoint Call-Home-CA
enrollment terminal
exit
crypto ca authenticate Call-Home-CA
-----BEGIN CERTIFICATE-----
MIIE0zCCA7ugAwIBAgIQGNrRniZ96LtKIVjNzGs7SjANBgkqhkiG9w0BAQUFADCB
yjELMAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQL
ExZWZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJp
U2lnbiwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxW
ZXJpU2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0
aG9yaXR5IC0gRzUwHhcNMDYxMTA4MDAwMDAwWhcNMzYwNzE2MjM1OTU5WjCByjEL
MAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQLExZW
ZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJpU2ln
biwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxWZXJp
U2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0aG9y
aXR5IC0gRzUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCvJAgIKXo1
nmAMqudLO07cfLw8RRy7K+D+KQL5VwijZIUVJ/XxrcgxiV0i6CqqpkKzj/i5Vbex
t0uz/o9+B1fs70PbZmIVYc9gDaTY3vjgw2IIPVQT60nKWVSFJuUrjxuf6/WhkcIz
SdhDY2pSS9KP6HBRTdGJaXvHcPaz3BJ023tdS1bTlr8Vd6Gw9KIl8q8ckmcY5fQG
BO+QueQA5N06tRn/Arr0PO7gi+s3i+z016zy9vA9r911kTMZHRxAy3QkGSGT2RT+
rCpSx4/VBEnkjWNHiDxpg8v+R70rfk/Fla4OndTRQ8Bnc+MUCH7lP59zuDMKz10/
NIeWiu5T6CUVAgMBAAGjgbIwga8wDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E
BAMCAQYwbQYIKwYBBQUHAQwEYTBfoV2gWzBZMFcwVRYJaW1hZ2UvZ2lmMCEwHzAH
BgUrDgMCGgQUj+XTGoasjY5rw8+AatRIGCx7GS4wJRYjaHR0cDovL2xvZ28udmVy
aXNpZ24uY29tL3ZzbG9nby5naWYwHQYDVR0OBBYEFH/TZafC3ey78DAJ80M5+gKv
MzEzMA0GCSqGSIb3DQEBBQUAA4IBAQCTJEowX2LP2BqYLz3q3JktvXf2pXkiOOzE
p6B4Eq1iDkVwZMXnl2YtmAl+X6/WzChl8gGqCBpH3vn5fJJaCGkgDdk+bW48DW7Y
5gaRQBi5+MHt39tBquCWIMnNZBU4gcmU7qKEKQsTb47bDN0lAtukixlE0kF6BWlK
WE9gyn6CagsCqiUXObXbf+eEZSqVir2G3l6BFoMtEMze/aiCKm0oHw0LxOXnGiYZ
4fQRbxC1lfznQgUy286dUV4otp6F01vvpX1FQHKOtw5rDgb7MzVIcbidJ4vEZV8N
hnacRHr2lVz2XTIIM6RUthg/aFzyQkqFOFSDX9HoLPKsEdao7WNq
-----END CERTIFICATE-----
quit
Example
Create Trustpoint
ciscoasa(config)# crypto ca trustpoint Call-Home-CA
ciscoasa(config-ca-trustpoint)# enrollment terminal
ciscoasa(config-ca-trustpoint)# exit
ciscoasa(config)#
Install Certificate
ciscoasa(config)# crypto ca authenticate Call-Home-CA
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIE0zCCA7ugAwIBAgIQGNrRniZ96LtKIVjNzGs7SjANBgkqhkiG9w0BAQUFADCB
yjELMAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQL
ExZWZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJp
U2lnbiwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxW
ZXJpU2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0
aG9yaXR5IC0gRzUwHhcNMDYxMTA4MDAwMDAwWhcNMzYwNzE2MjM1OTU5WjCByjEL
MAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQLExZW
ZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJpU2ln
biwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxWZXJp
U2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0aG9y
aXR5IC0gRzUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCvJAgIKXo1
nmAMqudLO07cfLw8RRy7K+D+KQL5VwijZIUVJ/XxrcgxiV0i6CqqpkKzj/i5Vbex
t0uz/o9+B1fs70PbZmIVYc9gDaTY3vjgw2IIPVQT60nKWVSFJuUrjxuf6/WhkcIz
SdhDY2pSS9KP6HBRTdGJaXvHcPaz3BJ023tdS1bTlr8Vd6Gw9KIl8q8ckmcY5fQG
BO+QueQA5N06tRn/Arr0PO7gi+s3i+z016zy9vA9r911kTMZHRxAy3QkGSGT2RT+
rCpSx4/VBEnkjWNHiDxpg8v+R70rfk/Fla4OndTRQ8Bnc+MUCH7lP59zuDMKz10/
NIeWiu5T6CUVAgMBAAGjgbIwga8wDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E
BAMCAQYwbQYIKwYBBQUHAQwEYTBfoV2gWzBZMFcwVRYJaW1hZ2UvZ2lmMCEwHzAH
BgUrDgMCGgQUj+XTGoasjY5rw8+AatRIGCx7GS4wJRYjaHR0cDovL2xvZ28udmVy
aXNpZ24uY29tL3ZzbG9nby5naWYwHQYDVR0OBBYEFH/TZafC3ey78DAJ80M5+gKv
MzEzMA0GCSqGSIb3DQEBBQUAA4IBAQCTJEowX2LP2BqYLz3q3JktvXf2pXkiOOzE
p6B4Eq1iDkVwZMXnl2YtmAl+X6/WzChl8gGqCBpH3vn5fJJaCGkgDdk+bW48DW7Y
5gaRQBi5+MHt39tBquCWIMnNZBU4gcmU7qKEKQsTb47bDN0lAtukixlE0kF6BWlK
WE9gyn6CagsCqiUXObXbf+eEZSqVir2G3l6BFoMtEMze/aiCKm0oHw0LxOXnGiYZ
4fQRbxC1lfznQgUy286dUV4otp6F01vvpX1FQHKOtw5rDgb7MzVIcbidJ4vEZV8N
hnacRHr2lVz2XTIIM6RUthg/aFzyQkqFOFSDX9HoLPKsEdao7WNq
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: cb17e431 673ee209 fe455793 f30afa1c
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
Configuring the call-home Feature on the ASA
The simplist way to configure the call-home feature on the ASA is to:
- Enable the service
- Define your contact e-mail address - which is used to send you an email to complete the registration process
- Activate the default CiscoTAC-1 profile
The below commands accomplish these tasks:
service call-home
call-home
contact-email-addr <email-address>
profile CiscoTAC-1
active
After configuring the above, the ASA will send a call-home message to Cisco, which will trigger the registration process and you will receive an e-mail to the contact-email-addr within a few minutes. You must click on the link in the e-mail to complete the registration process and to then view your device on the Smart Call Home portal.
Example Configuration
Below is an Example config mainly using the defaults
service call-home
call-home
contact-email-addr customer@mail.server
profile CiscoTAC-1
active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration export full periodic weekly
subscribe-to-alert-group environment
subscribe-to-alert-group diagnostic
subscribe-to-alert-group telemetry periodic daily
What has been changed is that the command subscribe-to-alert-group configuration export full periodic weekly was added. By default, the configuration export method is 'minimum', in which case the configuration is not sent it. Instead, just a list of features enabled is sent. By changing this option to export full, a scrubbed configuration (passwords and IP addresses removed) of the ASA is then sent to the Cisco Call Home server. Which allows the network administrator to view the configuration of the ASA from the Smart Call Home portal.
Troubleshooting
If you are having problems with the ASA communicating with the Cisco Call Home server, then enable debug call-home all, and then send a test message using call-home test profile <profile_name>
Example
ciscoasa# debug call-home all
call-home all event trace on
Success
What you should see is the following output
ciscoasa# call-home test profile CiscoTAC-1
INFO: Destination callhome@cisco.com skipped. Transport method email is not enabled.
INFO: Sending test message to https://tools.cisco.com/its/service/oddce/services/DDCEService...
ci/console: processing test(Test) SCH Configuration Test
ci/console: [0] dispatching test message to https://tools.cisco.com/its/service/oddce/services/DDCEService
ci/console: upload 2759 bytes
INFO: Succeeded
ci/console: throttle channel input 2759 bytes, output 2759 bytes
ci/console: [0] Successfully dispatch test message(2) to https://tools.cisco.com/its/service/oddce/services/DDCEService
Additionally, within a few minutes, you should receive an e-mail, indicating that your test message was received. If you have not completed the registration process for this ASA, then the e-mail will provide a link to confirm the registration process. By clicking on the link, you tie your CCO user ID to the ASA, so that the ASA appears when you log into the Smart Call Home portal.
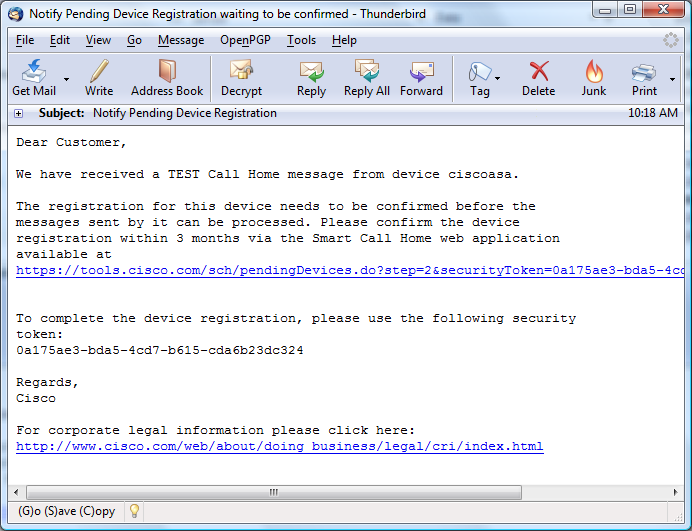
No DNS Server Configured
If you have configured call-home, but the ASA is unable to resolve the IP of tools.cisco.com, (because the DNS server is not configured, or is unreachable), then you will see the following messages in the debugs.
ciscoasa# call-home test profile CiscoTAC-1
INFO: Destination callhome@cisco.com skipped. Transport method email is not enabled.
INFO: Sending test message to https://tools.cisco.com/its/service/oddce/services/DDCEService...
ERROR: Failed: INVALID_ADDRESS(16)
ci/console: processing test(Test) SCH Configuration Test
ci/console: [0] dispatching test message to https://tools.cisco.com/its/service/oddce/services/DDCEService
ci/console: [0] Dispatch message(1) test to https://tools.cisco.com/its/service/oddce/services/DDCEService failed: INVALID_ADDRESS(16)
ci/console: Local error for https://tools.cisco.com/its/service/oddce/services/DDCEService, discarded (error INVALID_ADDRESS(16))
Verifying the DNS Server
To validate that DNS is resolving correctly, just attempt to ping tools.cisco.com. The IP should be resolved, and pings succeed. (Note that tools.cisco.com is load-balanced and therefore the IP my differ from what is shown below.
ciscoasa# ping tools.cisco.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 128.107.242.16, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 70/76/80 ms
show vpn-sessiondb summary
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I know this is an old thread but is there an example of setting up call-home to email out alerts on customer's own email address? Does that allow configuring outbound SMTP on port 587 or 26 since the ISP doesn't allow outbound port 25.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Why yes there is! :-)
Have a look here:
https://supportforums.cisco.com/document/57466/asa-smart-call-home-common-uses-and-periodic-monitoring
However, the ASA does not provide the ability to specify the SMTP server's port number. Do you have another device you can use to port address translate the destination traffic? Or an internal mail server you can use?
Sincerely,
David.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks a lot for prompt response David. Now that most ISPs don't allow port 25 unless its a business class service, would Cisco ever allow call-home feature to use a different port? OR the whole call-home function is very low priority in Cisco's feature list :-)..
http://customer.comcast.com/help-and-support/internet/email-port-25-no-longer-supported/
Thanks,
Sam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Sam,
Ok, I had an idea... and just tested this myself. You can specify the port by following the mail server's IP with a colon and then the port number.
Example:
call-home
mail-server 192.168.1.4:587
The ASA accepts this (even though it isn't documented) and treats it as the destination port to use.
Hope it helps!
David.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks David,
I will test it shortly.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
There needs to be a "What drawbacks does Smart Call-home entail?" section with a warning that your firewall suddenly becomes a brick if the connection to the licensing server stops functioning or there is an issue with CA trust that is out of your control.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi hroi,
Smart Call-home is not tied to licensing. If Smart Call-home is not functioning (or not able to talk to Cisco) it will have zero impact on the operations of the firewall itself.
Sincerely,
David.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi David,
I have configured the call-home for automated scheduled backup. I am successful in sending ASA backup to my email address periodically. But when, i am trying to send the configuration backup to my Web/IIS server using HTTP transport method, it is not successful. trying to resolve it from past one month, but no clue yet. Please help. I tried it using both http/https
Here are the logs.
call-home test profile config_backup
INFO: Sending test message to parveenk@ABC.com...
ssh: processing test(Test) SCH Configuration Test
ssh: [0] dispatching test message to parveenk@ABC.com
ssh: SMTP server: X.X.X.X
ssh: smtp_rewrite channel closed input 2733 bytes, output 2805 bytes
ssh: throttle channel input 2805 bytes, output 2805 bytes
INFO: Succeeded
INFO: Sending test message to http://vwsrv-asabackup/Backup/...
ssh: [0] Successfully dispatch test message(341) to parveenk@ABC.com
ssh: [0] dispatching test message to http://vwsrv-asabackup/Backup/
ssh: Dispatch to destination http://vwsrv-asabackup/Backup/
ssh: Opening dispatch channel: httpc/4/Y.Y.Y.Y/80/
ssh: Opened dispatch channel: httpc/4/Y.Y.Y.Y/80/
ssh: upload 2743 bytes
ssh: http response status 405
ssh: <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org /TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="httssh:
ssh: p://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"/>
<title>405 - HTssh:
ssh: TP verb used to access this page is not allowed.</title>
<style type="text/css">
<!--
body{margin:0;font-size:.7em;font-famissh:
ssh: ly:Verdana, Arial, Helvetica, sans-serif;background:#EEEEEE;}
fieldset{padding:0 15px 10px 15px;}
h1{font-size:2.4em;margin:ssh:
ssh: 0;color:#FFF;}
h2{font-size:1.7em;margin:0;color:#CC0000;}
h3{font-size:1.2em;margin:10px 0 0 0;color:#000000;}
#header{wissh:
ssh: dth:96%;margin:0 0 0 0;padding:6px 2% 6px 2%;font-family:"trebuchet MS", Ve rdana, sans-serif;color:#FFF;
background-color:#555ssh:
ssh: 555;}
#content{margin:0 0 0 2%;position:relative;}
.content-container{background:#FFF;width:96%;margin-top:8px;padding:10px;pssh:
ssh: osition:relative;}
-->
</style>
</head>
<body>
<div id="header"><h1>Server Error</h1></div>
<div id="content">
<div classh:
ssh: ss="content-container"><fieldset>
<h2>405 - HTTP verb used to access this page is not allowed.</h2>
<h3>The page you are ssh:
ssh: looking for cannot be displayed because an invalid method (HTTP verb) was u sed to attempt access.</h3>
</fieldset></div>
</dssh:
ssh: iv>
</body>
</html>
ssh:
ERROR: Failed: HTTP_FAILED(39)
INFO: Sending test message to https://vwsrv-asabackup/backup/...
ssh: throttle channel input 2743 bytes, output 2743 bytes
ssh: [0] Dispatch message(342) test to http://vwsrv-asabackup/Backup/ failed: HT TP_FAILED(39)
ssh: [0] dispatching test message to https://vwsrv-asabackup/backup/
ssh: Dispatch to destination https://vwsrv-asabackup/backup/
ssh: Opening dispatch channel: httpc/4/Y.Y.Y.Y/443/ssl/verify/sch//
ssh: Opened dispatch channel: httpc/4/Y.Y.Y.Y//443/ssl/verify/sch//
ssh: upload 2744 bytes
ERROR: Failed: CONNECT_FAILED(35)
INFO: Sending test message to https://vwsrv-asabackup/Backup/...
ssh: http request to https://vwsrv-asabackup/backup/ failed, rc -1
ssh: [0] Dispatch message(343) test to https://vwsrv-asabackup/backup/ failed: C ONNECT_FAILED(35)
ssh: [0] dispatching test message to https://vwsrv-asabackup/Backup/
ssh: Dispatch to destination https://vwsrv-asabackup/Backup/
ssh: Opening dispatch channel: httpc/4/Y.Y.Y.Y//443/ssl/verify/sch//
ssh: Opened dispatch channel: httpc/4/Y.Y.Y.Y/443/ssl/verify/sch//
ssh: upload 2744 bytes
ERROR: Failed: CONNECT_FAILED(35)
vcadri-vpn#
vcadri-vpn#
vcadri-vpn#
vcadri-vpn#
vcadri-vpn#
vcadri-vpn# ssh:
vcadri-vpn#
vcadri-vpn#
vcadri-vpn# http request to https://vwsrv-asabackup/Backup/ failed, rc -1
ssh: [0] Dispatch message(344) test to https://vwsrv-asabackup/Backup/ failed: C ONNECT_FAILED(35)
$asabackup/Backup/ failed: CONNECT_FAILED(35)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear All
In may case it is related to TLSv1.3 packet cap (TLSv1.3 Record Layer: Alert (Level: Fatal, Description: Handshake Failure) to licensing server
SSL lib error. Function: tls_process_client_certificate Reason: certificate verify failed <==================== (Relegated to bug CSCvw31514 current ver 9.19.1)
https://quickview.cloudapps.cisco.com/quickview/bug/CSCvw31514
changed call-home destination address https to http
Nov 11 2024 08:58:20 ASA : %ASA-7-725013: SSL server management:1.1.1.1/61791 to CSSM/443 chooses cipher TLS_AES_256_GCM_SHA384
Nov 11 2024 08:58:20 ASA : %ASA-7-717025: Validating certificate chain containing 3 certificate(s).
Nov 11 2024 08:58:20 ASA : %ASA-7-717029: Identified client certificate within certificate chain. serial number: 0xxxxx, subject name: O=Cisco,C=US,OU=TC,CN=cissm.
Nov 11 2024 08:58:20 ASA : %ASA-3-717009: Certificate validation failed. serial number: 01, subject name: CN=Cisco Licensing Root CA,O=Cisco.
Nov 11 2024 08:58:20 ASA : %ASA-3-717027: Certificate chain failed validation. Generic validation failure occurred.
Nov 11 2024 08:58:20 ASA : %ASA-7-725014: SSL lib error. Function: tls_process_client_certificate Reason: certificate verify failed <==================== (Relegated to bug CSCvw31514 current ver 9.19.1)
Nov 11 2024 08:58:20 ASA : %ASA-4-120006: Call-Home license message to https://CSSM/Transportgateway/services/DeviceRequestHandler failed. Reason: CONNECT_FAILED <====================
Nov 11 2024 08:58:20 ASA : %ASA-4-120005: Call-Home license message to https://CSSM/Transportgateway/services/DeviceRequestHandler was dropped. Reason: CONNECT_FAILED <====================
Nov 11 2024 08:58:20 ASA : %ASA-3-444303: %SMART_LIC-3-AGENT_REG_FAILED:Smart Agent for Licensing Registration with the Cisco Smart Software Manager (CSSM) failed: Communication message send error
Nov 11 2024 08:58:20 ASA : %ASA-3-444303: %SMART_LIC-3-COMM_FAILED:Communications failure with the Cisco Smart Software Manager (CSSM) : Communication message send error
Nov 11 2024 08:58:20 ASA : %ASA-6-302014: Teardown TCP connection 1077232250 for management:CSSM/443 to identity:1.1.1.1/61791 duration 0:00:00 bytes 779 TCP FINs from identity
Nov 11 2024 08:58:20 ASA : %ASA-7-609002: Teardown local-host management:CSSM duration 0:00:00
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: